Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "technique"
-
!rant
After over 20 years as a Software Engineer, Architect, and Manager, I want to pass along some unsolicited advice to junior developers either because I grew through it, or I've had to deal with developers who behaved poorly:
1) Your ego will hurt you FAR more than your junior coding skills. Nobody expects you to be the best early in your career, so don't act like you are.
2) Working independently is a must. It's okay to ask questions, but ask sparingly. Remember, mid and senior level guys need to focus just as much as you do, so before interrupting them, exhaust your resources (Google, Stack Overflow, books, etc..)
3) Working code != good code. You are an author. Write your code so that it can be read. Accept criticism that may seem trivial such as renaming a variable or method. If someone is suggesting it, it's because they didn't know what it did without further investigation.
4) Ask for peer reviews and LISTEN to the critique. Even after 20+ years, I send my code to more junior developers and often get good corrections sent back. (remember the ego thing from tip #1?) Even if they have no critiques for me, sometimes they will see a technique I used and learn from that. Peer reviews are win-win-win.
5) When in doubt, do NOT BS your way out. Refer to someone who knows, or offer to get back to them. Often times, persons other than engineers will take what you said as gospel. If that later turns out to be wrong, a bunch of people will have to get involved to clean up the expectations.
6) Slow down in order to speed up. Always start a task by thinking about the very high level use cases, then slowly work through your logic to achieve that. Rushing to complete, even for senior engineers, usually means less-than-ideal code that somebody will have to maintain.
7) Write documentation, always! Even if your company doesn't take documentation seriously, other engineers will remember how well documented your code is, and they will appreciate you for it/think of you next time that sweet job opens up.
8) Good code is important, but good impressions are better. I have code that is the most embarrassing crap ever still in production to this day. People don't think of me as "that shitty developer who wrote that ugly ass code that one time a decade ago," They think of me as "that developer who was fun to work with and busted his ass." Because of that, I've never been unemployed for more than a day. It's critical to have a good network and good references.
9) Don't shy away from the unknown. It's easy to hope somebody else picks up that task that you don't understand, but you wont learn it if they do. The daunting, unknown tasks are the most rewarding to complete (and trust me, other devs will notice.)
10) Learning is up to you. I can't tell you the number of engineers I passed on hiring because their answer to what they know about PHP7 was: "Nothing. I haven't learned it yet because my current company is still using PHP5." This is YOUR craft. It's not up to your employer to keep you relevant in the job market, it's up to YOU. You don't always need to be a pro at the latest and greatest, but at least read the changelog. Stay abreast of current technology, security threats, etc...
These are just a few quick tips from my experience. Others may chime in with theirs, and some may dispute mine. I wish you all fruitful careers!229 -
Programming is like sex because...
- One mistake and you have to support it for the rest of your life.
- Once you get started, you'll only stop because you're exhausted.
- It takes another experienced person to really appreciate what you're doing.
- ...Conversely, there's some odd people who pride themselves on their lack of experience.
- You can do it for money or for fun.
- If you spend more time doing it than watching TV, people think you're some kind of freak.
- It's not really an appropriate topic for dinner conversation.
- Public schools don't do a very good job teaching kids about it.
- It doesn't make any sense at all if you try to explain it in strictly clinical terms.
- Some people are just naturally good at it.
- ...But some people will never realize how bad they are, and you're wasting your time trying to tell them.
- There are a few weirdos with bizarre practices nobody really is comfortable with.
- One little thing going wrong can ruin everything.
- It's a great way to spend a lunch break.
- Everyone acts like they're the first person to come up with a new technique.
- Everyone who's done it pokes fun at those who haven't.
- Beginners do a lot of clumsy fumbling about.
Source and full list : https://push.cx/2006/...1 -
This is simply beautiful. Visualized sorting algorithms using colors.
Just discovered it on twitter (@galka_max)
If you have capped mobile data, search for WiFi first. Could be pretty much data...
Watch them here:
https://m.imgur.com/gallery/voutF
The videos and gifs pretty much disable any compression technique.
Attached is their merge sort example heavily compressed from 16 to 5 megabytes to fit devRant's limits... 2
2 -
!Story
The day I became the 400 pound Chinese hacker 4chan.
I built this front-end solution for a client (but behind a back end login), and we get on the line with some fancy European team who will handle penetration testing for the client as we are nearing dev completion.
They seem... pretty confident in themselves, and pretty disrespectful to the LAMP environment, and make the client worry even though it's behind a login the project is still vulnerable. No idea why the client hired an uppity .NET house to test a LAMP app. I don't even bother asking these questions anymore...
And worse, they insist we allow them to scrape for vulnerabilities BEHIND the server side login. As though a user was already compromised.
So, I know I want to fuck with them. and I sit around and smoke some weed and just let this issue marinate around in my crazy ass brain for a bit. Trying to think of a way I can obfuscate all this localStorage and what it's doing... And then, inspiration strikes.
I know this library for compressing JSON. I only use it when localStorage space gets tight, and this project was only storing a few k to localStorage... so compression was unnecessary, but what the hell. Problem: it would be obvious from exposed source that it was being called.
After a little more thought, I decide to override the addslashes and stripslashes functions and to do the compression/decompression from within those overrides.
I then minify the whole thing and stash it in the minified jquery file.
So, what LOOKS from exposed client side code to be a simple addslashes ends up compressing the JSON before putting it in localStorage. And what LOOKS like a stripslashes decompresses.
Now, the compression does some bit math that frankly is over my head, but the practical result is if you output the data compressed, it looks like mandarin and random characters. As a result, everything that can be seen in dev tools looks like the image.
So we GIVE the penetration team login credentials... they log in and start trying to crack it.
I sit and wait. Grinning as fuck.
Not even an hour goes by and they call an emergency meeting. I can barely contain laughter.
We get my PM and me and then several guys from their team on the line. They share screen and show the dev tools.
"We think you may have been compromised by a Chinese hacker!"
I mute and then die my ass off. Holy shit this is maybe the best thing I've ever done.
My PM, who has seen me use the JSON compression technique before and knows exactly whats up starts telling them about it so they don't freak out. And finally I unmute and manage a, "Guys... I'm standing right here." between gasped laughter.
If only it was more common to use video in these calls because I WISH I could have seen their faces.
Anyway, they calmed their attitude down, we told them how to decompress the localStorage, and then they still didn't find jack shit because i'm a fucking badass and even after we gave them keys to the login and gave them keys to my secret localStorage it only led to AWS Cognito protected async calls.
Anyway, that's the story of how I became a "Chinese hacker" and made a room full of penetration testers look like morons with a (reasonably) simple JS trick. 9
9 -
I hope they make an anime about being a dev and the enemy is the deadline.
Dev: ill use this coding technique number 111
Deadline: impossible
Insert explosion effect here9 -
Manager: Hey Dev I need to do QA on this PR.
Dev: That PR is not finished yet
Manager: Well do QA now anyway, that way when it is finished it can be merged in right away since QA has already been done on it. It’s a project management technique called “fast-tracking” and it improves efficiency.
Dev: …9 -
Be a 17 year old intern with 10 years experience in a language or technique which was invented 6 years ago.5
-
Pomodoro technique, and if nothing works take a break from sitting in front of the computer, and focus on something else, it will get solved easily the next time you touch your pc9
-
Friend : “What’s a devDuck”
Me: “We’ll use it as a problem solving technique. It’s a technique where if you get stuck, you try to explain the problem to a rubber duck.”
Friend: “Because you don't have the people skills to describe it? Autism levels skyrocketing”
Me: T_T4 -
Full stack developer Starter pack:
- Youtube
- Stackoverflow
- Extreme patience
- and a couple of Ninjutsu (cloning technique is recommended)6 -
Story Time:
When I first started working where I currently am, the manager at the time decided to send us off to a conference about one of the products our institution was purchasing at the time. She also thought that it would be a good way for me, the new guy, to bond with the rest of the staff.
During the presentations we found out that the people surrounding us were not exactly developers because of a couple of things:
1. Some examples were done with php and javascript for adding functionality to said product. The product gave you the opportunity to script on top of it (think of some sort of CMS, but it does not use PHP as its backend language) EVERYONE from the "class" in this particular workshop said they were developers. But at the sight of php in a group of 80 people or so, only about 7 recognized it, including myself and my team.
2. When they showed an example with Javascript, in particular jquery, one of the dudes in the workshop said (with extreme senior level confidence might I add) "yeah I never liked Javascript because you really can't connect it to any database in a website" <--- my face went 0.o and one of the actual developers doing the presentation did a Jim from the Office and looked at some out of screen camera.
3. During a conf talk, one PHD dude showed an example in the template language the CMS used (an obscure Java based template language)in which he was proudly calling out a technique he used to include one snippet of code into another one.....at that time, one of my coworkers squinted his eyes in disbelief, got close to me and said "is this man telling everyone in here that he discovered how to include a file? like, as a new thing?" me: "lol yes", him: "this is a waste of time, do the docs for this thing show how to do it or is he doing some sort of strange maneuver for something the platform does not support?" me: "let me check....nope, it is included, for some reason he made a function that takes the...name of the file he wants to include and passes it over to that call inside of the body....which as per the docs it is the include function...." him: ".....fuck, what a waste of time and money, fuck it lets spend a couple of more minutes here and then go get a drink or something"
That last part was my favorite really, the man speaking was not just any phd holder, but a comp sci phd holder. To this day my dude would walk into my office and say shit like "I DISCOVERED HOW TO INCLUDE A FILE WITH PHP!"14 -
The only technique I know.
Get hired straight out of uni. Project architect disappears right at beginning and I am left as a graduate employee to build a travel booking web app. Learning new front end and backend frameworks by coding them constantly for the next 8 months.
We might actually get this project done!5 -
!rant
A rather long(it's 8 hrs long to be precise) story
So I just finished an amazing homework assignment. The goal was to open a new shell on Linux using a C program. We were asked to follow instructions from http://phrack.org/issues/49/14.html . However the instructions given were for 32 bit processors and we had to do same for 64 bit machines. In a nutshell we had to write a 64 bit shell code and use buffer-overflow technique to change the return address if the function to our shell code.
I was able to write my own shellcode within 1hr and was able to confirm that it's working by compiling with nasm and all. Also the "show-off-dev" inside me told me to execute "/bin/bash" instead of "/bin/sh"(which everyone else was going to do). After my assembly code was properly executing shellcode, I was excited to put it in my C code.
For that, I needed opcodes of assembly code in a string. Following again the "show-off-dev" inside me, I wrote a shell script which would extract the exact opcodes out of objdump output. After this I put it in my C code, call my friend and tell him that "hell yeah bro, I did it. Pretty sure sir is gonna give me full marks etc etc etc". I compiled the code and BOOM, IT SEGFAULTS RIGHT IN FRONT OF MY FRIEND. Worst, friend had copied a "/bin/sh" code from shellstorm and already had it working.
Really burned my ego, I sat continuously for 8 hrs in front of my laptop and didn't talk to anyone. I was continuously debugging the code for 8 hrs. Just a few minutes ago, I noticed that the shellcode which I'm actually putting in my C code is actually 2 bytes shorter than actual code length. WHAT THE F. I ran objdump manually and copied the opcodes one by one into the string (like a noob) and VOILA ! IT WORKED !!!
TURNS OUT I DIDN'T CUT THE LAST COLUMN OF OPCODES IN MY SHELL SCRIPT. I FIXED THAT AND IT WORKED !!
THE SINGLE SHITTY NUMBER MADE ME STRUGGLE 8 HRS OF MY LIFE !! SMH
Lessons learnt :
1)Never have such an ego that makes you think you're perfect, cuz you're retarded not perfect
2)Examine your scripts properly before using them
3)Never, I repeat NEVER!! brag about your code before compiling and testing it.
That's it!
If you've read this long story, you might as well press the "++" button.6 -
So, as a programmer, I'm basically the go-to tech support guy for my family (and now my gf's family).
So, my gf's mum updated windows and her computer stopped playing around through headphones, asks me for help.
I've got no fucking idea, I don't even use windows.
She's like "if your computer did this what would you do".
"I'd google the problem and randomly try solutions until it started working again. And hope I didnt break anything else."
She didn't seem happy with my debugging technique...10 -
Bookbinding, it takes time and it gives me an opportunity to slow down. I appreciate the different textures of each paper and technique for each binding/stitching method. Plus this way I never have to buy an expensive notebook 😁3
-
People having sleep deprivation.
If your health is at stake, you may want to aim for maximum healing potential.
Humen always should prefer more natural substances and techniques.
As chemicals mostly alter the status quo but tackle the ultimate reason why.
Military has developed glasses that simulate the sunrise to wake you up / keep you awake.
That technique is like 20 years old. And who is gonna get those glasses for me?
Nowadays, studies published find humen feel more at ease by rising and sleeping with the sun and moon.
Having two weeks of camping once in a while is recommended. At least once a year.
Alternately you can try to regulate your days rhythm.
Start your day with a cup of hot speedwell tea.
Like every freaking day.
Its augmenting your activity thus easing your sleep at night.
Give every technique at least two weeks time to take effect.
And always remember :
Sleep is a thing that can be influenced but never will be controlled.
Good night ;P9 -
I worked on a small project which required selenium for automation! Used the same technique to spam messages to friends in WhatsApp! 😂😂😂2
-
Why is it that everytime, as a back-end developer, I want to dive into a simple front-end topic or technique which can perfectly be done in plain JavaScript, I need 27 different libraries and packages according to nearly all tutorials..
It really crushes my motivation and is just ridiculous.6 -
Working in the embedded systems industry for most of my life, I can tell you methodical testing by the software engineers is significantly lacking. Compared to the higher level language development with unit tests and etc, something i think the higher level abstracted industry actually hit out the of park successfully.
The culture around unit testing and testing in general is far superior in java and the rest.
Down here in embedded all too often I hear “well it worked on my setup... it worked at my desk”.. or Oh I forgot to test that part.. or I didn’t think that perticular value could get passed in... etc I’ve heard it all. Then I’ve also heard, you can’t do TTD or unit tests like high level on embedded... HORSESHIT!
You most definitely can! This book is a great book to prove a point or use as confirmation you are doing things correctly. My history with this book was I gonna as doing my own technique of unit testing based on my experience in the high level. Was it perfect no but I caught much more than if I hadn’t done the testing. THEN I found this book, and was like ohh cool I’m glad I’m on the right thought process because essentially what they were doing in the book is what I was doing just slightly less structured and missing a few things.
I’ve seen coworkers immediately think it’s impossible to utilize host testing .. wrong.
Come to find out most the of problems actually are related to lack of abstraction or for thought out into software system design by many lone wolf embedded developers.. either being alone, or not having to think about repercussions of writing direct register writes in application or creating 1500 line “main functions” because their perception is “main = application”. (Not everyone is like this) but it seems to be related to the EEs writing code ( they don’t know wha the CS knows) and CS writing over abstraction and won’t fit on Embedded... then you have CEs that either get both sides or don’t.. the ones to understand the low level need but also get high level concepts and pariadigms and adapt them to low level requirements BOOM those are the special folks.
ANYway..the book is great because it’s a great beginner book for those embedded folks who don’t understand what TDD is or Unit testing and think they can’t do it because they are embedded. So all they do is AdHoc testing on the fly no recording results no concluding data very quick spot check and done....
If your embedded software engineers say they can’t unit test or do TDD or anything other than AdHoc Testing...Throw the book at them and say you want the unit test results report by next week Friday and walk away.
Lol 7
7 -
So y'all listen to me.
No Software Development methodology or technique is a silver bullet. None!
Every engineer must acquire the ability to know when and where to use different approaches, appropriately.
Well, you wanna read that again.9 -
Scrum is terrible. Is there another agile technique that isn't as bad? Like maybe one that will let us do our "scrum" once a week for like an hour? My current project really doesn't lend itself to once a day scrums. Literally my scrum input is "I worked on what I have been working on, and I'm gonna work on it more today. Impediments are literally the same as they always are because my life is no longer my own."5
-
Pomodoro timers work only when the task at hand is boring. Yesterday, I worked non-stop on some task I greatly enjoyed(Rust embedded) and I would get distracted if there was some disruption because some overrated technique.6
-
Sometime this year(what is left of it) or the next I will be promoted to the senior developer in charge of two schools.....
I already thought that the level of work that me and the current senior do is way too fucking much for two people. Can't really fathom all of it just being me without seeing a substantial increase in salary(there is one in place for it...but shit man I know myself and even then I am going to bitch about it repeatedly)
What sucks the most is that I can't wing it or just not give a fuck(my preferred technique) since I really like my department, my coworkers and specially my manager.
Its her fault. It really is. She is just so likeable and I really can't imagine not giving her anything other than my 100 .
And before everyone states that it should be 100 from the get go. I am not particularly fond of giving my all for a company/institution. Never.
The reason is that I have been fucked with way more times than I can count and normally feel that regardless of how much of a total badass I can be I will never see the full compensation of it. It has happened on every other job. So instead of working for the company I work for my team. If I don't like my team I don't give a fuck.
I am a good worker, was an excellent soldier and I am an even better engineer. But there is always this feeling that I am being taken advantage of that I just can't shake off everywhere that I am working at.
Even now, the reason why the lead is leaving is because of how he was fucked over during the reclassification process. It was a slap to him in the face. Now this glorious institution will lose someone that is really amazing all because they take shit for granted.
Everyone is a number, an id. As irreplaceable as we are they treated him as someone that would just take shit and be fine with it.
And trust me, where I am at, we ARE irreplaceable, this ain't cali where you flip a stone and you get 100 node/php devs. This is 0 man ground where devs are fucking wizards that no one knows exist.
Oh well.3 -
Hey everyone, cozyplanes here with another quick excel prank i thought of.
It is called TEEST, and the technique behind is simple, but interesting. Recommend taking a look, and pranking with your friends.
The following is the README of TEEST (Text in Excel Every Single Time) in Github.
You can check the simple project here ( https://github.com/cozyplanes/teest )
Disclaimer: Do not use or modify neither the program or the source code to make software violating the law.
### How do I use it?
1. Head to https://github.com/cozyplanes/teest and download the latest release `EXE` file.
1. Windows may warn you with the missing signature. The file is a DEBUG file, so there isn't a publisher signature. You can proceed downloading anyway since it has been virus checked by the developer.
2. Type the message you want to display in the textbox.
3. Click `Save text` button.
5. To check the file, click `Cancel` button in the opened popup dialog.
### What happens?
When an MS Excel file (`.xlsx`) has been opened, by using TEEST, two files gets opened.
1. The original file user opened
2. Excel file named `message.txt` with the custom message you have written.
`message.txt` excel file will open every single time a person opens a excel file.
*In some older versions of Excel, the message may overlap with the user opened file.*
### Why does this happen?
When MS Excel program is executed, it is programmed to check the files in the following 2 folders.
- `C:\Program Files\Microsoft Office\Office[versionnumber]\XLSTART`
- `C:\Users\%username%\AppData\Roaming\Microsoft\Excel\XLSTART`
In normal conditions, there is no file in those folders (or the folders doesn't exist at all) but when you use TEEST and click `Save text` button, it saves `message.txt` file in the folders above. From MS Excel is executed again, it will find out there is a file in the folders above, so it will show those text files in Excel.
### Where is this technique used?
There should be a lot of software using this trick, but it is widely known for ransomwares such as `GandCrab` and `TeslaCrypt` displaying decryption methods in MS Excel by this trick.
### How can I disable it?
1. Open TEEST again.
2. Click `Save text` button and click `Cancel` in the following popup.
3. Delete `message.txt` file in the opened explorer.
### LICENSE
This software is under the MIT License. Refer to the `LICENSE` file for more information.
### Contact
<cozyplanes@tuta.io>
Spam/Ads not allowed. Please only send questions or concerns about the software. It may take up to 48 hours to get a reply.13 -
That awkward moment...
... when someone tells you that they have found an amazing technique for a common problem and you are like:
"erhm... I was already using that for years... I thought you knew it too..."1 -
So it's been a while since I've posted as my first few months at the new job have been amazing. But now I'm running into issues with a team member that I need to get off my chest.
So my new job is front end development in React. I'm brand new to it but I was promised time to learn on the job. On my first day the team member I'm now having a conflict with offered me help. He's the most experienced so I gladly took it.
But now several months in I've noticed his teaching style doesn't work for me. He'll go into long theoretical explanations whenever I ask a question and I get overwhelmed with info. And he gets frustrated with my inability to process all that, because he feels I waste his time. So frustrated that at one time he just walked out of work and drove home, which was really upsetting to everyone.
My direct manager and my mentor in the company (our software architect), as well as our scrum master (a consultant) are all aware of the conflict. I've been assigned another colleague to help me out. Things were going ok but he got sick so I had to turn back to the team member with the conflict for assistance. Of course frustrations arose again.
Now yesterday during our sprint planning meeting we had to say what we liked and didn't like about the past sprint. And I brought up I feel I need time for learning and that I don't know where to put that, since we don't have a task for it. I said I also felt past approaches weren't working out and that I'd like to take up the offer to go on training. I was trying to word it very neutral to not upset my colleagues, as they tried their best. But the colleague who I had previous conflicts with took it personal and accused me of not listening and that is why my code is awful. While all I've been doing is rely on his code to learn. Long story short it got very heated and direct manager and scrum master who were present had to shut it down.
I'm thinking of talking to my manager and mentor today. It really hurts when you're accused of maliciousness when all you did was try. I know my code isn't perfect. But I get no help in improving it beyond long winded explanations about theory. If I ask for practical help he says he won't write my code for me. Which isn't what I expect. When I say I followed his example he says I shouldn't copy. But two sentences later he says if I don't know what I am doing I should listen to him. It's really very confused and demotivating as a beginner, but he makes it about how I waste his time and ruin his job for him. I understand he tries his best and that it has to be hard when someone seemingly is as dumb as a bag of bricks. But my manager and mentor told me they support me as long as I continue to show improvement. So I asked for alternatives (training, time to study, or whatever I haven't thought of) and now I feel like the bad person. I'm already someone with crippling low self esteem, and I'm thrown into the deep end. It kinda sucks when someone then tells you from the sideline you can't swim and how swimming works. How about tossing me one of those floaty things and then maybe accept I need to hold on to that for a bit and my technique will need work until I can make it on my own? :(2 -
How did you learn to program ?.
I read E-books to get the basic knowledge and then I would go through a open source PHP project and rebuild it using the look cover right check technique.
Then on top of that I watched YouTube tutorials.
How did you learn ?.
I never went to college or further eduction as I seem to do really well at self teaching plus there is so much info on google nowadays.12 -
“There's one technique that you must use if you want people to listen to you: listen to them.” - The Pragmatic Programmer 📖2
-
Sometimes I just don't know what to say anymore
I'm working on my engine and I really wanna push high triangle counts. I'm doing a pretty cool technique called visibility rendering and it's great because it kind of balances out some known causes of bad performance on GPUs (namely that pixels are always rasterized in quads, which is especially bad for small triangles)
So then I come across this post https://tellusim.com/compute-raster... which shows some fantastic results and just for the fun of it I implement it. Like not optimized or anything just a quick and dirty toy demo to see what sort of performance I can get
... I just don't know what to say. Using actual hardware accelerated rasterization, which GPUs are literally designed to be good at, I render about 37 million triangles in 3.6 ms. Eh, fine but not great. Then I implement this guys unoptimized(!) software rasterizer and I render the same scene in 0.5 ms?!
IT'S LITERALLY A COMPUTE SHADER. I rasterize the triangles manually IN SOFTWARE and write them out with 64-bit atomic image stores. HOW IS THIS FASTER THAN ACTUAL HARDWARE!???
AND BY LIKE A ORDER OF MAGNITUDE AT THAT???
Like I even tried doing some optimizations like backface cone culling on the meshlets, but doing that makes it slower. HOW. Im rendering 37 million triangles without ANY fancy tricks. No hi-z depth culling which a GPU would normally do. No backface culling which a GPU with normally do. Not even damn clipping of triangles. I render ALL of them ALL the time. At 0.5 ms4 -
If you write blogs and tutorials about programming,
Please don't just throw blocks of code at people. Explain what this code does, why you wrote it in this particular way and not the other, when people should use this technique and when they shouldn't. Also don't make your tutorial specific to a particular library/package unless you specify in the title.
Stop making blogs just for the sake of making them. Make blogs that help people become better. Advertise for your proficient and show others why you love it. Put some effort into your craft people!!2 -
I'll give you a few reasons to walk away from a dev's chair:
1. if you want your life to be simple and not challenging, if you just want to go with the flow - choose something else. Dev's life will definitely bring some challenges to your day (and sometimes night, and sometimes - your weekends). Especially if you feel you are a perfectionist, dev life could turn your life into a living hell if not handled with care.
2. If you like to see people smiling, if you love that feeling when you help someone and that someone has a better day thanks to you - choose something else. 1st line SD would probably do, but the further from technology you go - the more smiles (and human faces overall) you'll see.
3. If you prefer person-to-person interaction over to talking to machines - definitely don't be a dev. Go to management, administration or smth else, but development. >90% of the human interaction in this field is arguments and conflicts; ~8% are requests for assistance, and the remaining 2% are shared by saying "hi" to the office administrator and your (semi|)annual reviews with your manager. Not kidding.
4. If you have a personality where you find it difficult to stand your ground and not budge to the pressure/blame game/your managers asking you to stay in late. Like it or not, it happens quite often. Many devs have spoiled the management by budging to their requests/demands to stay for OT/unpaid OT to "fix the mess they have made". That's a blame game right there. And these people stay in and do what the slaves do - work for free because they are yelled at. And then management sees this technique work and (ab|)uses it on other devs. If you can say NO and stick to it, prolly wave with some printed paragraphs of labour law in front that manager's nose - it won't be a problem. But if your consciousness is too troubling - stay away from this field of engineering.
5. If you want to easily "disconnect" from work and go do something else - dev's career might be a problem. Yes, your computer might be shut down/hibernated/suspended after 5pm until 9m the next morning, but your brain will most likely keep trying to solve the problems you were facing. You'll prolly use your own computer to do some research, check some forums, docs, etc. - this is all your free time, this is all your family time donated to your manager (and to your personal knowledge base). Not to mention, all these things you learn will soon enough become obsolete, as new technologies will replace them. So if you'd like to easily "disconnect" after 5pm, doing that as a dev might be too challenging.1 -
!Dev
the fuck...
I'm not very good in remembering numbers. But I have lots to remember: apartment entrance code, maestrocard pin, phone pin, s few pins at work, and so on. So I remember patterns my finger mskes on a numpad instead [if you have played Ingress, you know exactly how it works].
There is a pattern for a bank card. Another one for phone pin, etc.
I've been using this technique for years... It has never failed me. I never could remember my pins, but give me a keypad and I'll enter it right away.
Last week smth happened. I forgot 2 pins from both of my bank cards... Both at the same day. And I did not have them written down anywhere for years...
Shit3 -
Tried pomedoro technique copule of time found that this doesn't work for mE. The only things worked is
1) do 4 hours straight
2) take 1 hour break
3) do another 4 hour straight
works much wetter3 -
today, we're going to learn how to make web dev complicated and how to annoy users with a simple technique. learn by example
 2
2 -
Shower thought:
The anti-procrastination-technique "If it only takes five minutes or less, do it right now" is basically "Shortest Job First" for Real Life3 -
Most successful? Well, this one kinda is...
So I just started working at the company and my manager has a project for me. There are almost no requirements except:
- I want a wireless device that I can put in a box
- I want to be able to know where that device is with enough accuracy to be able to determine in which box the device was put in if multiple boxes were standing together
So, I had to make a real time localization system. RTLS.
A solo project.
Ok, first a lot of experiments. What will the localization technique be? Which radio are we going to use?
How will the communication be structured?
After about two months I had tested a lot, but hadn't found THE solution. So I convinced my manager to try out UWB radio with Time Difference Of Arrival as localization technique. This couldn't be thrown together quickly because it needed more setup.
Two months later I had a working proof of concept. It had a lot of problems because we needed to distribute a clock signal because the radio listeners needed to be sub-nanosecond synchronous to achieve the accuracy my manager wanted. That clock signal wasn't great we later found out.
The results were good enough to continue to work on a prototype.
This time all wired communication would be over ethernet and we'd use PTP to synchronize the time.
Lockdown started.
There was a lot of trouble with getting the radio chip to work on the prototype, ethernet was tricky and the PTP turned out to be not accurate enough. A lot of dev work went into getting everything right.
A year and 5 hardware revisions later I had something that worked pretty well!
All time synchronization was done hybridly on the anchors and server where the best path to the time master was dynamically found.
Everything was synchronized to the subnanosecond. In my bedroom where I had my test setup I achieved an accuracy of about 30cm in 3d. This was awesome!
It was time to order the actual prototype and start testing it for real in one of the factory halls.
The order was made for 40 anchors and an appointment was made for the installation in the hall.
Suddenly my manager is fired.
Oh...
Ehh... That sucks. Well, let's just continue.
The hardware arrives and I prepare everything. Everything is ready and I'm pretty nervous. I've put all my expertise in this project. This is gonna make my career at this company.
Two weeks before the installation was to take place, not even a month after my manager was fired, I hear that my project was shelved.
...
...
Fuck
"We're not prioritizing this project right now" they said.
...
It would've been so great! And they took it away.
Including my salary and hardware dev cost, this project so far has cost them over €120k and they just shelved it.
I was put on other projects and they did try to find me something that suited me.
But I felt so betrayed and the projects we're not to my liking, so after another 2-3 months I quit and went to my current job.
It would've so nice and they ruined it.
Everything was made with Rust. Tags, anchors, RTLS server, web server & web frontend.
So yeah, sorry for the rambling.4 -
Java Server Faces!
Don't get me wrong, I kinda love coding Java, but JSF is just a horrible technique for web development.
Had to do it since my company got to maintain an already existing backend which the customer wanted to have some more Features but the original dev didnt continue to support.
Attached hello world example from good old mykong for those not knowing jsf: http://mkyong.com/jsf2/...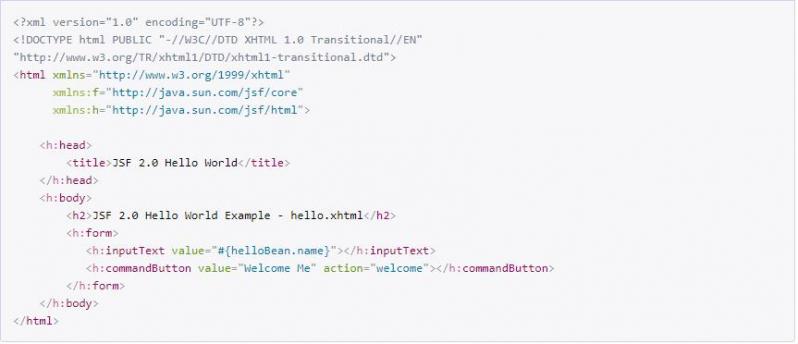 4
4 -
Here’s the second book for today.
Another small 100 page or so book.
It’s called advanced programming techniques, personally I don’t like the title, I don’t consider most of the items in here advanced, I would consider them more “better ways of solving a problem”, they do talk about recursion and linked lists, so I guess that could be a little advanced.
But like table based solutions is not advanced it’s just a technique that allows for simpler, scale able and main table code.. I been doing it for a long time, most easiest way to determine if something can turn into a table solution is look for a function that has a bunch of calls to the same function or something of that nature lots of repeated code with slight changes in a function or range of functions .. those of simplist way of “tablefiying”a solution I will picture the example from the book below.
The book, is all in java except for linked lists Thats in C..
But anyway this book is a great quick reference book, into the pile with programming pearls book, and those like that. 14
14 -
Meme quoting one of our employees who sent in a ticket asking if something was a "phishing technique without the use of email."

-
We code hard in these cubicles
My style’s nerd-chic, I’m a programmin’ freak
We code hard in these cubicles
Only two hours to your deadline?
Don’t sweat my technique.
Sippin’ morning coffee with that JAVA swirl.
Born to code; my first words were “Hello World”
Since 95, been JAVA codin’ stayin’ proud
Started on floppy disks, now we take it to the cloud.
On my desktop, JAVA’s what’s bobbin’ and weavin’
We got another winning app before I get to OddEven.
Blazin’ code like a forest fire, climbin’ a tree
Setting standards like I Triple E….
Boot it on up, I use the force like Luke,
Got so much love for my homeboy Duke.
GNU Public Licensed, it’s open source,
Stop by my desk when you need a crash course
Written once and my script runs anywhere,
Straight thuggin’, mean muggin’ in my Aeron chair.
All the best lines of code, you know I wrote ‘em
I’ll run you out of town on your dial-up modem.
Cause…
We code hard in these cubicles
Me and my crew code hyphy hardcore
We code hard in these cubicles
It’s been more than 10 years since I’ve seen the 404.
Inheriting a project can make me go beeee-serk
Ain’t got four hours to transfer their Framework.
The cleaners killed the lights, Man, that ain’t nice,
Gonna knock this program out, just like Kimbo Slice
I program all night, just like a champ,
Look alive under this IKEA lamp.
I code HARDER in the midnight hour,
E7 on the vending machine fuels my power.
Ps3 to Smartphones, our code use never ends,
JAVA’s there when I beat you in “Words with Friends”.
My developing skills are so fresh please discuss,
You better step your game up on that C++.
We know better than to use Dot N-E-T,
Even Dan Brown can’t code as hard as me.
You know JAVA’s gettin’ bigger, that’s a promise not a threat,
Let me code it on your brain
We code hard in these cubicles,
it’s the core component…of what we implement.
We code hard in these cubicles,
Straight to your JAVA Runtime Environment.
We code hard in these cubicles,
Keep the syntax light and the algorithm tight.
We code hard in these cubicles,
Gotta use JAVA if it’s gonna run right.
We code hard in these cubicles
JAVA keeps adapting, you know it’s built to last.
We code hard in these cubicles,
Robust and secure, so our swag’s on blast
CODE HARD10 -
Working on a bug with the intern. Suggested the "stepping away for a few minutes" technique. Came back and quickly resolved.
Works every time. -
Hated function naming in python, because some functions are like "dothisorthat", some are "do_this_or_that", some are "doThisOrThat", some are, I don't know, what new technique of naming would python devs invent in the near future. Honestly, these naming creeps me out4
-
Noname Russian $17 wireless charger somehow makes less high pitched coil noise than my fancy nomad charger.
Yes it’s ugly. Yes the led is blasting and yes I painted over the led with a black nail polish.
I disassembled the nomad charger and located the coils that were making noise. I’m going to either fill them with epoxy (a common technique used by gpu enthusiasts to get rid of coil noise) or replace them completely.
TL;DR:
nomad — bouba
noname russian charger — kiki 4
4 -
When I used to code I'd use the Pomodoro Technique.
It helps me get tasks done more quickly and efficiently when I know I only have to focus for 45 minutes and then I get a 15 minute break.
It also helps if you're stuck on something, because when you come back to it you have fresh eyes.
Also, music without any lyrics helps me focus better than music where someone is singing. Be it Mozart or dubstep, as long as there are no words I can work with it. 😂 (I highly recommend Instrumental Core)
Finally, my phone would be in a completely different room or in my desk drawer in DND mode. I set it up so that it only rings for certain people (parents, brother and boyfriend), so no-one can bug me while I work. It's fantastic. -
Watching police interrogation videos right now, the channel called “EXPLORE WITH US”. Goddamn, US police/investigator system is _way_ ahead of russia’s. You can remain silent, you can just refuse to testify, and the interrogation will be over, they use REID technique, other tricks to make people talk without resorting to violence. In russia, they either torture you into admission, or straight up put you to jail and that’s it. They don’t want justice, they want to put someone in jail, guilty or not, and call it a day. Case solved, good job guys.
And yes, I realize MKULTRA existed, I realize there is Guantanamo Bay prison where terrible things happen, I realize US system is far from perfect, and accidents happen, there are very bad cops, etc., but in general, US system is a paragon of humanity compared to what happens in russia.
If the US system looks good compared to something, you know that something is truly fucked up.3 -
Been worrying about this for a few weeks now.
As a junior dev, how do I continue to improve (with respect to coding style, technique, etc.) when my seniors are only slightly better than me in a technical regard? I feel like I'm improving at a drastically slower pace than when I first started.
🐢1 -
Ok. I am trying out a new thing. My colleague told me about a technique worth giving a shot. So basically you should ignore the negative things and only focus on the positive ones making your mind shift states and boost your productivity although sometimes really hard. It’s working for me quite well so far, so here’s my two cents on today:
Thank you my dear designer fellow to making all the screens more beautiful than they were already. Big respect for you for not worrying about deadlines and for for inspiring me to be a faster programmer. I knew I can count on you. Being such nice to me leaves me speechless sometimes, but not today. Today I wish you soon get all the anusroses to smell right next to your beautiful face1 -
Today I have created a server application on Python Tornado which can forward TCP Packets directly to HTTP request queue without any intermediate caching.
Our remote IOT devices (microcontrollers with sensors attached) send sensor reading over TCP Socket to our server and all the connected web applications can show the data instantly using long polling and the above mentioned technique.1 -
Managed to derive an inverse to karatsuba's multiplication method, converting it into a factorization technique.
Offers a really elegant reason for why non-trivial semiprimes (square free products) are square free.
For a demonstration of karatsubas method, check out:
https://getpocket.com/explore/item/...
Now for the reverse, like I said something elegant emerges.
So we can start by taking the largest digit in our product. Lets say our product is 697.
We find all the digits that produce 6 when summed, along with their order.
thats (1,5), (5,1), (2,4), (4,2), and (3,3)
That means for one of our factors, its largest digit can ONLY be 1, 5, 2, 4, or 3.
Lets take karatsubas method at step f (in the link) and reverse it. Instead of subtracting, we're adding.
If we assume (3,3)
Then we take our middle digit of our product p, in this case the middle digit of 697. is 9, and we munge it with 3.
Then we add our remaining 3, and our remaining unit digit, to get 3+39+7 = 49.
Now, because karatsuba's method ONLY deals with multiplication in single digits, we only need to consider *at most* two digit products.
And interestingly, the only factors of 49 are 7.
49 is a square!
And the only sums that produce 7, are (2,5), (5,2), (3,4), and (4,3)
These would be the possible digits of the factors of 697 if we initially chose (3,3) as our starting point for calculating karatsubas inverse f step.
But you see, 25 can't be a factor of p=697, because 25 is a square, and ends in a 5, so its clearly not prime. 52 can't be either because it ends in 2, likewise 34 ending in 4.
Only 43 could be our possible factor of p.
And we *only* get one factor because our starting point has two of the same digit. Which would mean p would have to equal 43 (a prime) or 1. And because p DOESNT (it equals 697), we can therefore say (3,3) is the wrong starting point, as are ALL starting points that share only one digit, or end in a square.
Ergo we can say the products of non-squares, are specifically non-prime precisely because if they *were* prime, their only factors would HAVE to be themselves, and 1.
For an even BETTER explanation go try karatsuba's method with any prime as the first factor, and 1 as the second factor (just multiply the tens column by zero). And you can see why the inverse, where you might try a starting point that has two matching digits (like 3,3), would obviously fail, because the values it produces could only have two factors; some prime thats not our product, or the value one, which is also not our product.
It's elegant almost to the level of a tautology. -
!RANT
Oh, the SORROW that is JEST! 😡
Endless days have been swallowed by the abyss in my quest to configure Jest with TypeScript and ECMAScript modules instead of CommonJS. Triumph seemed within my grasp until - BAM! - suddenly the tool forgets what "import" or "export" means. And the kicker? On the CI, it still runs like nothing’s amiss!
Allow me to elucidate for the uninitiated: Jest is supposed to be a testing safeguard, a protective barrier insulating devs from the errors of their peers, ensuring a smooth, uninterrupted coding experience.
But OH, how the tables have turned when the very shield becomes the sword, stabbing me with countless, infuriating errors birthed from Jest’s own design decisions!
The audacity to reinvent the whole module loading process just to facilitate module mocking is mind-boggling! Imagine constructing an entirely new ecosystem just to allow people to pretend modules are something they're not. This is not just overkill; it's a preposterous reinvention of a wheel that insists on being a pentagon!
Sure, if devs want to globally expose their variables, entwining everything in a static context, so be it. BUT, why should we, who walk the righteous path of dependency injection, be subjugated to this configured chaos?!
My blood boils as the jestering Jest thrusts upon me a fragile, perpetually breaking system, punishing ME for its determination to support whole module mocking! A technique, mind you, that I wouldn’t touch with a ten-foot pole, because, you know, DEPENDENCY INJECTION!
Where are the alternatives, you ask? Drowned in the abyss, it seems! Why can’t we embrace snapshots and all the delectable integrations WITHOUT being dragged through this module-mocking mire? Can’t module mocking just be a friendly sidekick, an OPTIONAL add-on, rather than the cruel dictator forcing its agenda upon our code?
Punish those clinging to their static contexts, their global variables – NOT those of us advocating for cleaner, more stable practices!
It’s high time we decouple the goodness of Jest from its built-in bad practices. Must we continue to dance with the devil to delight in the depth of Jest’s capabilities?
WHY, Jest, WHY?! 😭9 -
So here's a random idea: DDoS defence swarm.
Install the daemon on your server, and every time your server gets DDoS'd, all members of the swarm will mobilise to defend you, but the catch is that your server will have to help other members of the swarm too.
The defensive technique in question can be one of many:
1. Automated IP blocking/reporting with a blacklist in distributed form.
2. Other swarm members counterattack and cooperatively DDoS the offending addresses.
3. Flood the ISP with automated emails to force them to pay attention to the problem.
...or a combination of all of the above.
The only issue I can see with this is abuse potential. A clever person can trick the swarm into DDoSing innocents.15 -
I am quiet these days although I had few materials to write about. Like my journey of devdesk. I bought a proper chair. New mouse and got a mechanical keyboard. Work is fine but it is definitely not lack of rant-worthy moments. I had deactivated my Facebook and I wasn't that active on any other social network from the start. So all the more reason for me to be active here.
But turn out I'm not. I was thinking about it and this is my outcomes.
1) I'm focusing more on my tasks after adoption and practicing pomodoros technique. Hence using devrant lesser.
2) My right hand was literally unusable and unmovable for two times in past 5 weeks. Hence using phone lesser.
3) There was that notifications bug period and I thought people were just quiet like me. Hence more reasons to be less active.
4) devRant algo is good but not smart. It knows that I have a relation with PHP. But it doesn't know that I don't hate PHP. >>> How many times a week can you listen/ignore to people saying "Hey your wife is a silicone doll?" Fuck you. I know. But I'm married to my silicone doll. So fuck off. <<< PHP is just an example. I literally close devrant whenever I see "(noun) is (something negative)" posts.
My hand will fully recover soon. (I do hope so). My tasks will not always be super overwhelming. The app's bugs are getting fixed.
However I have a doubt about the last point. -
Okay so for all of you who think that you can't do shit without stackoverflow. I'll tell you this, fuck SO. There's this ancient technique of programmers of old probably just about 20-25 years ago called RTFM. Why bother copy pasting some one else's spaghetti(that you might not fully understand) when you can write your own better code! (said in good faith). When something is behaving strange or you don't know what something requires just hit the docs or manual and read about the api because it is describes not only what it wants and needs but also what it does. So try this because it might have more information that you need than stack overflow might tell you11
-
If you ever try to learn C++, give C Primer Plus 6th edition book a try. This is one of the best books that are prepared to teach, not tell about C++.
I tried Bjarne's boooks, but damn they are hard to understand, with badly formatted non-monnospace font code examples and terrible technique to teach. -
Most of us have scary stories about professors that think that they know about what they are talking about when it comes to teaching comp sci subjects. Shit is so backwards in most parts of the world with teachers showing outdated or completely pointless tech.
A friend called me the other day asking for classic ASP help because it was being used in his web class. Another was asking me about flipping c cgi web scripting. Wtf are schools teaching? Having the drive to LEARN actuall useful topics that are relevant on the market is hard enough as it is...shouldn't schools help at least a little bit? I was lucky, we were thaught Java, Python, cpp, js, sql, html5, css3, php, ruby and we had classes for node (for those interested) and asp.net mvc. Those were RELEVANT and good classes and while some outdated tech was good the rest is just bullshit. Specially since most teachers have 0 market value as develpers...but hey!! Wtf do I know! Of course my word is shit against all them doctorate and master degrees.
Gimme a break. School can be great. But a lot of the leadership there is toxic af for our industry. And while I appreciate the effort in me being thaught modern languages (and thaught is a hard word since I already knew how to program way before going to school) i still remember a teacher taking points away from an assignment for not using switch statements in Python...despite my explaining that there was no such thing (you can go around it by using a lil technique using functions, its pretty cool..pero no mames)
Or what about the time I mentioned to a fellow student how he could use markup for having more control with his windows forms while the very same teacher contradicted me saying that shit was not possible. Or the guy at the school in which I work teaching intro to programming using fucking vba...fk man if you are going the BASIC route at least teach them b4j or something fuuuuck.
I had good teachers, but they were always cast asside by dptmnt heads as if they knew better. I just hate pendejo teachers I really do.
Chinguen a su madre, bola de babosos.rant remembering uni yes asshole gnu linux is a viable alternative i still love coding fuck bad teachers fk the system11 -
Me and the lead developer of my team gave a long and detailed explanation to our manager entailing the current state of a budge program our workplace uses.
This app has been bugging him for a while, he did not write it and has not been given an opportunity to rewrite the damned thing. Its a really...really messy application, and whilst it is a functional one it most certainly is NOT an efficient one since adding or moving things only incites more spaghetti mess.
We were laughing while giving our report, but both of us were crying inside. The main thing is, we both love PHP and the things he has built are very well structured and efficient, he has good technique, but will admit at certain caveats regarding the way he structures his dbs stating that he always has to do changes, which hey, its the nature of the beast, dbs change all the time. But our issue with php is the same: it lets beginners write monstruosities that are harder to do in other environments.
It really is a permissive language. But I reckon thay such lax nature is better left at the hands of the more experieced developers that know what they are doing.
Either way, we will restructure this motherfucker taking advantage of the new standards (which both of us are well versed in) and applying a more structured approach with a nice frontend interface (we be looking at Vue.js and React although we are considering Angular as well)
Gon be some good times. -
Dear Prestashop developers, f**k YOU!
I already hate this shitfuck what you call the best open source e-commerce solution, but your module validation technique sucks.
They use tons of useless rules, but the last addition was the last drop: they force you to use the old (and long) array declaration.
So now I have 500 new errors in this fucking module.
Why the fuck do you want me to force an old syntax?3 -
A remarkably stupid but efficient technique I invented today to measure the latency of an audio feedback channel involving multiple hardware elements that is difficult to synchronize by itself:
1. Knock. Observe the echo in the feedback.
2.Try to knock in such a way that the physical sound more-or-less lines up with the feedback. The human brain is really good at this on average.
3. Once you often only hear one knock (as perfect synchronization as your ear can tell), record several minutes of audio
4. Stop knocking, count the additional knocks in the echo
5. Multiply the average delay between knocks on the recording by the number of additional knocks from step 44 -
When learning something new, say a new language or framework, do you go through the docs or tutorials, or do you just learn by doing and figure it out as you go?
I like to learn by doing and getting a finished project and start modding and changing stuff. what do you guys do?17 -
I hate touchscreens!
Far too often, nothing at all happens when "pressing" a "button", and when something happens, it's not at all what you wanted, it's like touchscreen devices have a will of their own.
Maybe touchscreens will evolve and actually become useful in the future, with a technique for reading input that works for everybody and not just for the majority, and with tactility, i.e. through 3D morphing of buttons, switches and wheels, controls that you can grab, feel and hold on to.
Till then, I'll dismiss touchscreens as the toys they are, no good for anything serious.5 -
I'm not good in doing presentations and I'm not sure if it is a common style or technique that to engage your audience, you need to ask a show of hands if they know about something..
I attended a "meeting/workshop" and the presenter just kept on asking who among us knows blah, have read blah, have seen blah, who doesn't know blah blah blah.
Why ask us to raise our hands? Are u conducting a survey? For those who raised their hands did u feel a sense of belongingness? For that one guy who raised his hand he was bullied.
I don't understand why ask ppl to raise their hands? For what?
If u want to share info then just deliver the message. Full stop. Don't make it embarrassing for the rest of us.3 -
I have sort of an embarrassing question...
I never learned touch typing, hated it as much as I hated my calligraphy lessons in elementary. Forward a couple of years, I'm a developer and trying to dig deeper into vim seems to require learning touch typing... it has been a struggle to say the least and lowered my speed to a frustrating rate. 😥
I know the arguments for putting the work and learning proper technique but, are there any other arguments out there? I mean, as a developer I find myself using a lot of numbers and symbols which are not totally covered in touch typing curricula, together with a bunch of key combinations...
Idk, maybe I'm just asking for encouragement or different perspectives or unknown advantages about learning touch typing even when you feel fast and confident without it... Thank you guys!11 -
Fucking dto hell...
Dear C#/.NET developers or any other developers, do you have a fucking smart approach/technique to handle the fucktons of dto classes throughout your webapi and not having to go to 5 different classes if you change some validation attributes ??
Seriously, that is the only thing I like about JS. It just does not fucking care...
EDIT: This rant came across and just fits perfectly: https://devrant.com/rants/68633811 -
So I promised a post after work last night, discussing the new factorization technique.
As before, I use a method called decon() that takes any number, like 697 for example, and first breaks it down into the respective digits and magnitudes.
697 becomes -> 600, 90, and 7.
It then factors *those* to give a decomposition matrix that looks something like the following when printed out:
offset: 3, exp: [[Decimal('2'), Decimal('3')], [Decimal('3'), Decimal('1')], [Decimal('5'), Decimal('2')]]
offset: 2, exp: [[Decimal('2'), Decimal('1')], [Decimal('3'), Decimal('2')], [Decimal('5'), Decimal('1')]]
offset: 1, exp: [[Decimal('7'), Decimal('1')]]
Each entry is a pair of numbers representing a prime base and an exponent.
Now the idea was that, in theory, at each magnitude of a product, we could actually search through the *range* of the product of these exponents.
So for offset three (600) here, we're looking at
2^3 * 3 ^ 1 * 5 ^ 2.
But actually we're searching
2^3 * 3 ^ 1 * 5 ^ 2.
2^3 * 3 ^ 1 * 5 ^ 1
2^3 * 3 ^ 1 * 5 ^ 0
2^3 * 3 ^ 0 * 5 ^ 2.
2^3 * 3 ^ 1 * 5 ^ 1
etc..
On the basis that whatever it generates may be the digits of another magnitude in one of our target product's factors.
And the first optimization or filter we can apply is to notice that assuming our factors pq=n,
and where p <= q, it will always be more efficient to search for the digits of p (because its under n^0.5 or the square root), than the larger factor q.
So by implication we can filter out any product of this exponent search that is greater than the square root of n.
Writing this code was a bit of a headache because I had to deal with potentially very large lists of bases and exponents, so I couldn't just use loops within loops.
Instead I resorted to writing a three state state machine that 'counted down' across these exponents, and it just works.
And now, in practice this doesn't immediately give us anything useful. And I had hoped this would at least give us *upperbounds* to start our search from, for any particular digit of a product's factors at a given magnitude. So the 12 digit (or pick a magnitude out of a hat) of an example product might give us an upperbound on the 2's exponent for that same digit in our lowest factor q of n.
It didn't work out that way. Sometimes there would be 'inversions', where the exponent of a factor on a magnitude of n, would be *lower* than the exponent of that factor on the same digit of q.
But when I started tearing into examples and generating test data I started to see certain patterns emerge, and immediately I found a way to not just pin down these inversions, but get *tight* bounds on the 2's exponents in the corresponding digit for our product's factor itself. It was like the complications I initially saw actually became a means to *tighten* the bounds.
For example, for one particular semiprime n=pq, this was some of the data:
n - offset: 6, exp: [[Decimal('2'), Decimal('5')], [Decimal('5'), Decimal('5')]]
q - offset: 6, exp: [[Decimal('2'), Decimal('6')], [Decimal('3'), Decimal('1')], [Decimal('5'), Decimal('5')]]
It's almost like the base 3 exponent in [n:7] gives away the presence of 3^1 in [q:6], even
though theres no subsequent presence of 3^n in [n:6] itself.
And I found this rule held each time I tested it.
Other rules, not so much, and other rules still would fail in the presence of yet other rules, almost like a giant switchboard.
I immediately realized the implications: rules had precedence, acted predictable when in isolated instances, and changed in specific instances in combination with other rules.
This was ripe for a decision tree generated through random search.
Another product n=pq, with mroe data
q(4)
offset: 4, exp: [[Decimal('2'), Decimal('4')], [Decimal('5'), Decimal('3')]]
n(4)
offset: 4, exp: [[Decimal('2'), Decimal('3')], [Decimal('3'), Decimal('2')], [Decimal('5'), Decimal('3')]]
Suggesting that a nontrivial base 3 exponent (**2 rather than **1) suggests the exponent on the 2 in the relevant
digit of [n], is one less than the same base 2 digital exponent at the same digit on [q]
And so it was clear from the get go that this approach held promise.
From there I discovered a bunch more rules and made some observations.
The bulk of the patterns, regardless of how large the product grows, should be present in the smaller bases (some bound of primes, say the first dozen), because the bulk of exponents for the factorization of any magnitude of a number, overwhelming lean heavily in the lower prime bases.
It was if the entire vulnerability was hiding in plain sight for four+ years, and we'd been approaching factorization all wrong from the beginning, by trying to factor a number, and all its digits at all its magnitudes, all at once, when like addition or multiplication, factorization could be done piecemeal if we knew the patterns to look for.7 -
So as an IT student I learn new stuff everyday. This is very useful, only not when you find it that the technique that you used in your personal project is not the only way to do it and is super fricking messy.
Whole weekend reworking.
(Not meaning I don't like the coding but just having to remove so many lines and reorganize files and the content of the files sucks sometimes :/) -
Feynman technique is the best tool I have ever used so far. I transform how I read code and doc. Why didnt i realize it early?2
-
I'm doing a new strike technique called sneaky strike.
I'm not doing shit. Not even telling my boss I'm on strike.
Nobody tells him.
C'EST LA LUTTEUH FINALEEEU9 -
So I just found out that GL_MAX as a blend func is supported pretty much universally (~92%). Pretty nice considering I kinda gave up my baricentrics based anti-aliasing technique months ago7
-
Found this in a book and i can tell you that wtfs/min is the most effective code quality measurement technique programmers have known to this day! xD
(Book: Clean code Robert C.Martin) 4
4 -
While the topic is a bit divisive, the statistical technique highlighted in this post is really cool:
https://wattsupwiththat.com/2022/...2 -
Pomodoro technique
Best hack as you choose the "session" length to suit your style and promotes focused effort. -
What are the best practices, which helps you follow "Pomodoro technique" and avoid wasting your time in general?3
-
Just finished a little proof of concept of a reprojected multisample antialiasing technique and daaaaamn it's looking good. First time ever a rendering technique I invented isn't complete shit so that's an improvement
It still has some (pretty big) issues with both spatial and temporal ghosting but I have some ideas in the pipeline
I wish I could show you guys comparison images but as it turns out most anti aliasing techniques look pretty good on still frames but only the good ones stand up under motion and I don't know of a good way right now to capture pixel perfect clips like that4 -
I'm a beginner cs student I'm learning c language now
Should i make note of all content ?
And plz suggest me good technique to learn that language ...plz !!19 -
Java Life Rap Video
https://m.youtube.com/watch/...
SPOKEN:
In the cubicles representin’ for my JAVA homies…
In by nine, out when the deadlines are met, check it.
CHORUS:
We code hard in these cubicles
My style’s nerd-chic, I’m a programmin’ freak
We code hard in these cubicles
Only two hours to your deadline? Don’t sweat my technique.
Sippin’ morning coffee with that JAVA swirl.
Born to code; my first words were “Hello World”
Since 95, been JAVA codin’ stayin’ proud
Started on floppy disks, now we take it to the cloud.
On my desktop, JAVA’s what’s bobbin’ and weavin’
We got another winning app before I get to OddEven.
Blazin’ code like a forest fire, climbin’ a tree
Setting standards like I Triple E….
Boot it on up, I use the force like Luke,
Got so much love for my homeboy Duke.
GNU Public Licensed, it’s open source,
Stop by my desk when you need a crash course
Written once and my script runs anywhere,
Straight thuggin’, mean muggin’ in my Aeron chair.
All the best lines of code, you know I wrote ‘em
I’ll run you out of town on your dial-up modem.
CHORUS:
‘Cause…
We code hard in these cubicles
Me and my crew code hyphy hardcore
We code hard in these cubicles
It’s been more than 10 years since I’ve seen the 404.
Inheriting a project can make me go beeee-serk
Ain’t got four hours to transfer their Framework.
The cleaners killed the lights, Man, that ain’t nice,
Gonna knock this program out, just like Kimbo Slice
I program all night, just like a champ,
Look alive under this IKEA lamp.
I code HARDER in the midnight hour,
E7 on the vending machine fuels my power.
Ps3 to Smartphones, our code use never ends,
JAVA’s there when I beat you in “Words with Friends”.
My developing skills are so fresh please discuss,
You better step your game up on that C++.
We know better than to use Dot N-E-T,
Even Dan Brown can’t code as hard as me.
You know JAVA’s gettin’ bigger, that’s a promise not a threat,
Let me code it on your brain
WHISPERED:
so you’ll never forget.
CHORUS:
We code hard in these cubicles,
it’s the core component…of what we implement.
We code hard in these cubicles,
Straight to your JAVA Runtime Environment.
We code hard in these cubicles,
Keep the syntax light and the algorithm tight.
We code hard in these cubicles,
Gotta use JAVA if it’s gonna run right.
We code hard in these cubicles
JAVA keeps adapting, you know it’s built to last.
We code hard in these cubicles,
Robust and secure, so our swag’s on blast
CODE HARD1 -
Do you always make sure to understand the basics/fundamentals of a technique/solution/tool/.. you're using ?
I don't do it all the time and I feel that it's something I should do more often (or always?).3 -
Use the pomodoro technique.
(im just reposting this since it didnt happen yet)
Serious part:
Asking for help when you get stuck with a problem helps a lot. But also dont ask every small thing because that gets annoying -
Learning to tech to speed up learning.
Using a new cooperative learning technique, AI Lab researchers cut by half the time it took a pair of robot agents to learn to maneuver to opposite sides of a virtual room.
A combination of deep learning and reinforcement learning algorithms are responsible for computers achieving dominance at challenging board games like chess and Go, a growing number of video games, including Ms. Pac-Man, and some card games, including poker. But for all the progress, computers still get stuck the closer a game resembles real life, with hidden information, multiple players, continuous play, and a mix of short and long-term rewards that make computing the optimal move hopelessly complex.
Image: Dong-ki Kim 1
1 -
I want to break my win 10 password which I have forgot . I know one method of breaking the passcode by using bootable Device . Is there any other method to other than using bootable device for breaking the passcode? please suggest some technique9
-
Just a friendly note: If you use the same technique as I i.e. local GIT repositories backed up on cloud, ALWAYS make sure there is still at least as much free space as the largest repo shallow clone.
It may happen that some really really archaic "commits" will disappear and git won't work as usual, but mostly you'll have an access to the branches, which you can diff against the master and make patches. Then just clone, make branches from patches and code happily ever after.
Also... you really really shouldn't push when you discover(git fsck --all) such an issue in your local repo, although I think git won't even allow you to do so. -
Best advice i was given (credit to my aunt), when you're struggling to get into something just do 15 minutes work, then allow 15 minute procrastination as a reward, then 15 mins work again, another 15 min procrastination, keep going until the work's done or you stop needing a break. Usually after the first hour of this I've got my motivation back.
When I was at school I went from a C grade student to an A grade student with this technique.2 -
How does devRant makes their money?
Hypothesis 1: they word count our rants to identify most well known tech terms and sell it to hiring companies and consulting firms.
Hypothesis 2: they aggregate rants on an specific management fad or technique and sell it to management research and consulting firms
Hypothesis 3: currently burning through investor cash and plan on filling the place with ads when that runs off.
Hypothesis 4: something along the lines of "devs of the world, unite!"
Or is there another way?7 -
Does anyone know what technique does Visual Studio IDE uses to open window/dialog when you search for something?
Let's say I want to find github, and I get the exact location, and when I click the list item it opens the screen.
Does anyone has any WPF sample code of similar stuff? It's really cool, and I would like to implement it in my feature projects... 3
3 -
I came across a website today when I was searching for some banking related stuff on Google and this is what happened...
Types search term in Google
Gets the results
Opens a result in a new tab
Finishes reading it and clicks back
Tab refreshes to go the website's home page (What!?)
Clicks back again
Refreshes to the same result page (seriously?)
Back
Home page
Back
Result
Back
.
.
.
.
Back
Google home page (wtf?)
Back
Website home page (again?)
Back
Result page (NO! I'M DONE)
Closes the tab
What sort of wicked loop did I get myself into? Did the website devs ever think how frustrated it will be if they ever open their own page?
And what a clever technique to open Google home page for people who keep on pressing the back button! 👏👏 /s1 -
During my readings of Nim I found a technique known as stropping.
This gives devs the ability to use keywords as identifiers.
Example:
var `var` = "fucking why?"
echo(`var`)
Can anyone tell me WHY would someone subject themselves to such confusion notion? Mind you Nim has large features for macro programming and the creation of dsls, i have not gotten far enough to assess this, but what other use could you highly knowledgeable lads and lasses think of?22 -
I saw few rants about "working in a box". Isn't that legacy technique and we all are now working in open space?I have auto adjusting chair that costs more than my month salary, desk which raises when I push button, console rooms etc etc
Still some thinks that we are slaves of companies working 'in the boxes '. If you are on devrant and you agree with this kind of jokes I must say that you have chosen a bad place to work ;( -
What drop shadow did DevRant use for their UWP app, Microsoft recently released blog theme shadow, but it's work well with the rounded elements. I guess DevRant use different technique.1
-
@LoveBytes inspired this post: What's your favorite coffee brewing technique? Cold brew? French press? Pour over?5
-
Noob question
Is it better to implement a cryptpgraphic algo in a function or in a class? Also how?
More info:
I have a cryptography class and I really enjoy implementing the different techniques that we study in class. At first I was just implementing the techniques in a simple function with 3 parameters; key, message and a bool for encryption or decryption. But as they are getting more complex, it is becoming harder to continue implementing them in a single function block. So I thought of using a class but ran into the problem of how do I even do that? Do I make different methods for key generation, encrypting and decrypting?
P.S. It's really just for learning how the crypto technique works and not for anything serious.12 -
The worst part about trying to come up with an antialiasing technique is running the demo application and thinking "hey that doesn't look too bad" and then reaslizing that the image doesn't have any antialiasing on it whatsoever
I know my technique looks bad right now, thanks for rubbing it in -
Oi, good lads! Here's a question
Do you meditate at work? If you do, would you mind sharing:
- what does it look like? i.e. half an hour of your lunchtime or a task in Jira for that or smth..? are you doing it individually or in groups?
- is it a part of your company culture or just smth you do on your own?
- how often? How long?
- which technique?
- would you recommend?
- which country is this in?
I'm thinking to suggest mindful meditation in my company as I've noticed it's significantly improved my critical thinking and judgement - something others could benefit from as well. And I need some examples, pros/cons, possible ways of implementation, etc.4 -
"What makes great design great is not a trendy technique, but the logic and conceptual aspect that were figured out in the designer’s mind – or on more likely, on paper – before a mouse cursor ever opened Photoshop. " - Kyle Meyer2
-
Note: I had AI rephrase this because apparently it was too full of swearing or smth to be accepted and I was getting a "there was an error posting this rant". Nice that people at devrant's can't even show a clear error of WTF is going on, not even in chrome dev tool console/network requests, so maybe you're able to figure out WTF is going on and fix your post. They must be the same kind of people I'm ranting about.
-----------End of the note.----------------
TL;DR;: My coworkers are smart idiots that learn fast but can't control themselves into turning any project into a trashcan of spaghetti code and I'm burning out and want to switch for couple years to a simpler job.
I'm considering leaving my career in programming, consulting, and project management in favor of a more straightforward, manual labor job—perhaps something like baking or another role that relies on physical effort rather than constant problem solving.
I’ve reached a point where I can no longer tolerate the challenges of my current position, especially due to the dynamics with my coworkers. I long for a day where I can work for eight hours, exhaust myself physically, and then go home without any lingering mental responsibilities or ties to complex problem solving.
Over the past decade, I’ve collaborated with many people, yet I've only had the opportunity to manage an entire project from scratch on my own twice. In those rare instances, everything ran smoothly, issues were quickly resolved, and the code remained stable for years without constant complaints from clients.
Unfortunately, my coworkers, despite their intelligence, tend to overcomplicate even simple tasks. They often fall into the trap of overengineering, chasing the latest technologies and implementing unnecessarily complex paradigms, design patterns, frameworks, and techniques—even when I’ve offered simpler, proven solutions.
For example, I’ve built robust portals that handle everything from national highway finances and warehousing to HR and inventory management for major companies. In contrast, when others attempt similar projects, the resulting code becomes overwhelmingly complex and difficult to manage.
To give a few specific examples:
Example 1: The .NET Portal
We began developing a .NET portal about two months ago, which is now nearing version 1.0. Before we even started, the team had created multiple flowcharts to split the project into components like SaaS deployment, Docker integration, obfuscation, and separate portals for user administration and backend processes. Within a few weeks, they scrutinized and debated numerous authentication technologies—even though we had successfully implemented JWT token solutions in the past. The team continually shifts focus, leaving me uncertain about the final direction.
Example 2: Over-Engineering with Patterns
In another project, the team overused inversion of control (IoC) and mediation patterns, even going so far as to have an AI generate a custom message bus. Navigating this overly decoupled code is challenging; even Visual Studio’s IntelliSense struggles to provide guidance, and the code often feels like a puzzle that changes whenever I return from a break.
Example 3: Complicated Logging Implementation
We needed to add logging functionality, and I proposed a simple solution using custom exceptions that would bubble up to a central logging mechanism. Despite its past success in saving time and reducing frustration, the team decided to implement three different logging methods—one using .NET’s ILogger, another with Serilog, and a third hybrid approach. They even suggested using a rarely seen technique involving stack traces to determine which function threw an error. This approach added unnecessary complexity and only increased my frustration.
Now, even though the project is too far along for me to withdraw, I find myself feeling burned out just a few days back at work. The code has become a tangled mess, and even routine tasks like adding logging are turning into sources of intense frustration due to constantly shifting ideas and overly complicated designs.
On top of all this, I’m also disappointed with the performance of AI tools, which seem to be producing unreliable code that requires further fixes, compounding my frustration.
I’m now seriously contemplating a complete career change—perhaps even moving to a country with a better work environment, such as Denmark or Switzerland—in the hope of finding a job where the work is more straightforward and less mentally taxing and better paying4 -
How do you handle error checking? I always feel sad after I add error checking to a code that was beautifully simple and legible before.
It still remains so but instead of each line meaning something it becomes if( call() == -1 ) return -1; or handleError() or whatever.
Same with try catch if the language supports it.
It's awful to look at.
So awful I end up evading it forever.
"Malloc can't fail right? I mean it's theoetically possible but like nah", "File open? I'm not gonna try catch that! It's a tmp file only my program uses come oooon", all these seemingly reasonable arguments cross my head and makes it hard to check the frigging errors. But then I go to sleep and I KNOW my program is not complete. It's intentionally vulnerable. Fuck.
How do you do it? Is there a magic technique or one has to reach dev nirvana to realise certain ugliness and cluttering is necessary for the greater good sometimes and no design pattern or paradigm can make it clean and complete?15 -
Help me DevRant people, can you suggest any style, technique, tips in making your own personal websites?8
-
Use the Pomodoro technique. 25 min focuc followed by a 5 minute break. After 4 Pomodoros you take 20 min break.
There are several articles about that technique.2 -
I wonder how Saas companies like Zapier, Zendesk, etc...build a lot of common 3rd party integrations that perform the same set of tasks. I mean, do they just brute force in building those market place integrations or do they have an architecture where everything just works if the API keys are configured?
Eg: github, gitlab, Jira apis kind of do the same set of tasks but their APIs are different in structure. Is there a normalisation technique behind the scenes or they just build the same stuff 3 times.3 -
SWIFT 3 sucks! SUCKS I TELL YOU! swift 3 changes the NSError class to its own Error class, now the categories (i.e the extensions) that I have added to the NSError class (like convenience inits and NSDictionary map to my own variables) are ALL LOST !!! MORE THAN 100 LINES OF CODE LOST!! because of this piece of shit mutation of the DATA TYPE ITSELF!!! when objective C code is used in Swift (using the mix-match technique) DONT UPGRADE TO swift 3.0 GUYS DONT DO IT!!! especially if you have legacy code in your project !!2
-
Pomodoro technique but with 52min stretches and 15 min breaks.
For avoiding procrastination: create 2 Todo lists every day before leaving work, one for small tasks to be done first thing in the morning and others throughout the day.1 -
Guys, how frequent do you face distraction while working? Like while coding, I'm always distracted with my phone. I know i can just throw it far away, but I do this habit on browser as well by suddenly opening a new tab to browse fb, for example.
One way to get around this is by using Pomodoro technique. But that only works if I'm not reluctant to do so. Another one is by limiting tabs opened in firefox by using an addon.
ITT: How do you deal with distraction?1 -
!rant
What's the best technique for securely storing all the various credentials used throughout a business?8 -
Anybody using the 52/17 Pomodoro technique? If so what results did it give you till now? I am using it for 2 days and finally I feel like I can focus on something.4
-
Tried pomedoro technique for the first time . Didn't help much other than just telling me how much time I have spent
-
Chef Brandon Rogers, LLC: Elevating Dining to the Next Level
When it comes to exceptional cuisine that transcends the ordinary, Chef Brandon Rogers, LLC is a name that stands out. Known as a Next Level Chef, Brandon Rogers is redefining what it means to experience fine dining with an innovative touch. Whether you're hosting an intimate dinner or planning an unforgettable event, Chef Rogers brings culinary artistry and creativity to every dish, ensuring your dining experience is nothing short of extraordinary.
Located in the heart of Chicago at 1 E Erie St, Suite 525-5584, Chicago, IL 60611, Chef Brandon Rogers, LLC is committed to taking your taste buds on an unforgettable journey. With an eye for detail and a passion for perfection, Chef Rogers is more than just a chef—he's a culinary visionary who takes pride in pushing the boundaries of flavor and presentation.
What Makes Chef Brandon Rogers a Next Level Chef?
Being a Next Level Chef isn't just about cooking—it's about innovation, technique, and creating an experience that goes beyond just the food. Chef Brandon Rogers combines classical training with contemporary methods to craft dishes that are visually stunning and bursting with flavor. His focus on quality ingredients, bold flavors, and beautiful presentations has earned him a reputation as one of Chicago's most sought-after chefs.
Chef Rogers is not afraid to experiment, blending diverse culinary traditions and techniques to create bold new flavors. His approach is always fresh, dynamic, and adaptable, ensuring that each meal is perfectly tailored to his client’s tastes and needs.
Customized Culinary Experiences That Go Above and Beyond
As a Next Level Chef, Chef Brandon Rogers offers more than just a meal—he creates an experience. From private dinners to corporate events, Chef Rogers works closely with his clients to design custom menus that reflect their preferences and dietary needs. Every dish is crafted with care, using the freshest ingredients and the highest standards of quality.
Whether you are planning a lavish wedding reception, an intimate dinner party, or a corporate gala, Chef Rogers ensures that each event is perfectly catered to your vision. His attention to detail extends beyond the food to every aspect of the dining experience, from the table settings to the ambiance. With Chef Brandon Rogers at the helm, your event is guaranteed to be an unforgettable culinary experience.
The Art of Presentation: More Than Just a Meal
Being a Next Level Chef means Chef Brandon Rogers doesn’t just focus on taste—he also brings artistry to the presentation of each dish. He believes that food should not only taste incredible, but also look beautiful and evoke emotion. Each plate is a work of art, designed to delight the eyes as much as the palate. From vibrant colors to unique plating techniques, Chef Rogers ensures that every meal feels like an exclusive, one-of-a-kind creation.
Passion for Excellence
What truly sets Chef Brandon Rogers apart as a Next Level Chef is his unwavering commitment to excellence. For him, cooking is a passion, not just a profession. This passion is evident in every dish he creates. Chef Rogers takes the time to understand the nuances of each ingredient and how to elevate it to its fullest potential, ensuring that every meal is a masterpiece.
His commitment to excellence extends to his business as well. Chef Rogers runs Chef Brandon Rogers, LLC with the utmost professionalism, ensuring that each client receives top-tier service and culinary satisfaction. With a focus on customer satisfaction and a passion for delivering exceptional dining experiences, Chef Rogers consistently exceeds expectations.
Why Choose Chef Brandon Rogers, LLC?
When you choose Chef Brandon Rogers, LLC, you’re not just getting a chef—you’re getting a Next Level Chef who will take your event or dining experience to new heights. Chef Rogers’ creative and personalized approach to cooking guarantees that your menu will be as unique as your event, while his dedication to quality ensures that every bite is flawless.
Chef Brandon Rogers, LLC is perfect for those who want to take their dining experiences to the next level, offering:
Custom Menus: Tailored to your event and preferences, from intimate dinners to large celebrations.
Expert Culinary Techniques: A blend of classic training and modern innovation for flavors that surprise and delight.
Attention to Detail: From the first bite to the last, every element of your meal is crafted with precision.
Unforgettable Dining Experiences: Whether for business or pleasure, Chef Rogers makes sure your event is memorable.
Get in Touch with Chef Brandon Rogers, LLC 1
1 -
Microblading Brows at Laser Body NYC: Perfect Your Look with Precision and Expertise
Are you looking to enhance your natural beauty with perfectly shaped eyebrows? Microblading is the solution you’ve been searching for! At Laser Body NYC, we specialize in offering premium microblading brows services that will leave you with flawless, natural-looking eyebrows that enhance your facial features.
What is Microblading?
Microblading is a semi-permanent eyebrow enhancement technique that involves using a fine blade to deposit pigments into the skin, mimicking the look of natural eyebrow hairs. The result is fuller, more defined brows that suit your face shape and personal style. Whether you're looking to correct sparse eyebrows or simply want a more defined arch, microblading brows can completely transform your look.
Why Choose Laser Body NYC for Microblading?
At Laser Body NYC, located at 99 Madison Ave, Floor 4, Suite 406, New York, NY 10016, we are committed to providing top-notch service and expert care. Our microblading artists are highly trained and experienced in the latest techniques, ensuring that your brows are designed with precision and accuracy. Here’s why you should trust us with your brow transformation:
1. Expert Technicians
Our team of skilled microblading artists uses their expertise to create brows that perfectly complement your natural facial features. We take the time to understand your preferences and ensure that you are happy with the shape, color, and fullness of your new brows.
2. Top-Quality Pigments and Tools
We use only the highest quality pigments and tools to ensure a long-lasting and natural result. Your brows will look amazing from the moment you leave our studio, and they will continue to hold their beautiful shape for months to come.
3. Comfortable and Safe Experience
Your comfort and safety are our top priority. We follow strict hygiene protocols and make sure you feel at ease throughout the entire process. From the initial consultation to the final result, we ensure a smooth and professional experience.
4. Personalized Consultations
Before beginning your microblading procedure, we offer a personalized consultation to understand your desired brow style and shape. Our artists will work with you to design the perfect brows tailored to your face shape and features.
How Long Does Microblading Last?
Microblading typically lasts between 12-18 months, depending on your skin type, lifestyle, and aftercare. Touch-ups are recommended to keep your brows looking fresh and defined.
What to Expect During Your Microblading Appointment?
When you come to Laser Body NYC for your microblading brows procedure, here’s what you can expect:
Consultation: We’ll discuss your brow preferences, desired shape, and color to ensure we achieve the perfect look.
Numbing: A topical numbing cream is applied to ensure that you’re comfortable during the procedure.
Microblading: The artist will use a fine blade to create hair-like strokes, filling in any sparse areas and designing your ideal brow shape.
Aftercare: We provide detailed aftercare instructions to ensure the best results and long-lasting beauty.
Book Your Appointment Today!
Are you ready to achieve the perfect microblading brows that will make you feel confident every day? Visit us at Laser Body NYC in New York City or call us at +1 929-800-7032 to book your consultation today. Our team is ready to help you achieve flawless, natural-looking eyebrows that complement your beauty.
Laser Body NYC is your trusted destination for microblading services in the heart of New York City. Come and experience the magic of expertly crafted brows that will leave you looking and feeling your best!5 -
McCarthy Power Washing Services: Top Roof Cleaning and Concrete Cleaning Services in Humble, TX
At McCarthy Power Washing Services, we specialize in providing high-quality roof cleaning service and concrete cleaning service to homeowners and businesses in Humble, TX, and the surrounding areas. Located at 18810 Summer Anne Drive, Humble, TX 77346, our goal is to restore the beauty and durability of your property’s exterior surfaces, ensuring they remain in excellent condition for years to come.
Why Choose McCarthy Power Washing Services?
With years of experience in the industry, McCarthy Power Washing Services is dedicated to delivering exceptional roof cleaning service and concrete cleaning service. We understand the importance of maintaining the cleanliness and integrity of your property, which is why we use the latest equipment and techniques to deliver outstanding results. Whether you need to clean your roof or restore the look of your concrete surfaces, our team is here to help.
Roof Cleaning Service:
Your roof is one of the most important parts of your property, protecting you from the elements and adding to your home's curb appeal. However, over time, roofs can accumulate dirt, algae, moss, and mold, which not only detract from the appearance of your home but can also cause long-term damage. Regular roof cleaning service is essential to maintain the integrity of your roof and prevent costly repairs.
At McCarthy Power Washing Services, we offer professional roof cleaning service to remove debris, algae, moss, and stains, including:
Algae and Moss Removal: Algae, moss, and lichen can grow on your roof, causing damage and leading to potential leaks. Our soft wash technique safely removes these contaminants without harming your roofing materials.
Stain Removal: We eliminate unsightly stains caused by dirt, leaves, and other debris, restoring the original beauty of your roof.
Protective Cleaning: Regular roof cleaning helps extend the lifespan of your roof by preventing damage and wear from built-up debris and organic growth.
Improved Curb Appeal: A clean roof can significantly enhance the overall appearance of your home or business, boosting curb appeal and property value.
We use a gentle soft wash method to ensure your roof is thoroughly cleaned without risking damage to the materials. Our cleaning solutions are safe and effective, providing lasting results while maintaining the integrity of your roof.
Concrete Cleaning Service:
Concrete surfaces around your property can quickly accumulate dirt, stains, oil spots, and other unsightly contaminants. From driveways and sidewalks to patios and pool decks, concrete cleaning service is essential to keep your hard surfaces looking fresh and well-maintained.
At McCarthy Power Washing Services, we offer comprehensive concrete cleaning service to remove stains and restore the appearance of your concrete surfaces, including:
Driveway Cleaning: We remove oil stains, dirt, and grime from your driveway, giving it a clean and polished look.
Sidewalk Cleaning: Our pressure cleaning removes dirt, algae, and moss from your walkways, ensuring they are safe and inviting.
Patio and Pool Deck Cleaning: We clean and restore outdoor living spaces, removing mold, mildew, and buildup to ensure your patios and pool decks are in excellent condition.
Garage Floor Cleaning: We can clean your garage floors, removing stains from oil, grease, and dirt, leaving them looking like new.
Our concrete cleaning service uses high-pressure washing equipment that effectively removes dirt and stains from concrete surfaces without causing any damage. We also adjust the pressure and cleaning solutions depending on the surface and condition of the concrete, ensuring optimal results every time. 1
1 -
Lounge 483: The Best Hair Treatments, Permanent Makeup, Keratin Treatments, and Lash Extensions Near Me in Brooklyn
At Lounge 483, located at 483 4th Ave, Brooklyn, NY 11215, we offer a wide range of beauty services designed to make you look and feel your absolute best. Whether you're looking for a revitalizing hair treatment near me, want to wake up with flawless makeup with permanent makeup near me, are in need of a smoothing keratin treatment near me, or dream of voluminous lashes with lash extensions near me, our expert team is here to provide you with exceptional service and stunning results.
Hair Treatment Near Me: Restore Your Hair’s Health and Shine
Searching for the perfect hair treatment near me? Look no further than Lounge 483. We offer a variety of treatments designed to repair, nourish, and revitalize your hair, no matter its texture or condition.
Popular Hair Treatments We Offer:
Deep Conditioning Treatments: Restore moisture and vitality to dry, damaged hair with our nourishing deep conditioning treatments. They help improve shine, smoothness, and overall hair health.
Scalp Treatments: If you're struggling with a dry, itchy, or flaky scalp, our scalp treatments can help restore balance and improve the health of your scalp for stronger, healthier hair growth.
Hair Masks: Customizable to suit your unique hair needs, our hair masks target specific concerns such as frizz, breakage, or color damage, leaving your hair feeling rejuvenated and soft.
Hair Repair Treatments: If you’ve recently suffered from damage due to heat styling, coloring, or environmental stress, our repair treatments can help restore strength and vitality to your hair.
No matter your hair type or concern, our hair treatment near me services are designed to give you beautiful, healthy hair that you’ll love to show off.
Permanent Makeup Near Me: Wake Up with Flawless Beauty
Tired of spending time on your daily makeup routine? Lounge 483 offers expert permanent makeup near me services that provide you with long-lasting beauty that stays flawless day in and day out. From eyebrows to eyeliner and lip color, permanent makeup can enhance your natural features without the hassle of applying makeup every day.
Our Permanent Makeup Services Include:
Microblading: Achieve full, natural-looking eyebrows with our microblading service. This semi-permanent technique creates fine, hair-like strokes for a flawless, defined brow.
Eyeliner Tattoo: Say goodbye to smudging eyeliner with our permanent eyeliner tattoo services. Whether you want a subtle lash enhancement or a bold winged look, our permanent eyeliner options are tailored to your style.
Lip Blush Tattoo: Enhance the natural color and shape of your lips with a lip blush tattoo. This semi-permanent procedure gives you fuller, more defined lips with a natural flush of color.
Areola Tattoo: We also offer permanent areola tattoos, which can be a great option for those who have undergone breast surgery and wish to restore their natural look.
With our permanent makeup near me services, you can save time and wake up looking polished, enhancing your natural beauty effortlessly.
Keratin Treatment Near Me: Achieve Smooth, Frizz-Free Hair
If you're tired of battling frizz or dealing with unruly hair, a keratin treatment near me is the solution you've been looking for. At Lounge 483, we specialize in keratin treatments that help smooth, soften, and straighten your hair, leaving it looking glossy, healthy, and frizz-free.
Why Choose Keratin Treatment?
Frizz Reduction: Keratin treatments smooth the hair cuticle, reducing frizz and flyaways, even in the most humid conditions.
Sleek, Smooth Hair: Achieve silky, straight hair without the need for heat styling tools, saving you time and effort.
Long-Lasting Results: The results from a keratin treatment typically last for several months, meaning you can enjoy smooth, manageable hair for an extended period.
Improved Hair Health: The nourishing keratin treatment helps strengthen your hair, adding shine and vitality to dull, lifeless strands.
Whether you're looking for sleek, straight hair or just want to reduce the hassle of styling, our keratin treatment near me service is a game-changer for anyone struggling with frizz or damage.
Lash Extensions Near Me: Enhance Your Eyes with Gorgeous Lashes
At Lounge 483, we offer expert lash extensions near me services to give you voluminous, long lashes that make your eyes pop. Whether you want a natural look or something more dramatic, our lash artists will customize your extensions to suit your style.
Types of Lash Extensions We Offer:
Classic Lashes: For a natural, everyday look, classic lash extensions add length and volume to your natural lashes, giving you a subtle, enhanced appearance. 6
6 -
I started the pomodoro technique recently. Unfortunately when I went to the shop they only had an egg timer.
It's been a frustrating few weeks. -
Hi,
I made a new video.
How to read code with Feynman technique, Pomodoro and Mind map:
https://youtube.com/watch/... -
Melodious Piano Studio: Your Premier Choice for Piano Lessons in Singapore
If you’re looking for quality piano lessons for beginners or piano lessons for adults in Singapore, look no further than Melodious Piano Studio. Located at 131 Jalan Bukit Merah, #01-1565, Singapore 160131, our studio provides a welcoming, professional, and educational environment for piano students of all ages. Whether you’re an adult wanting to learn piano or a beginner looking to start your musical journey, we are here to help!
Why Choose Melodious Piano Studio for Piano Lessons?
At Melodious Piano Studio, we are dedicated to providing the best piano lessons near me for students in the Bukit Merah, Redhill, and Tiong Bahru areas. Here’s why our piano studio stands out:
Experienced Piano Teachers in Singapore: Our skilled and passionate piano teachers in Singapore bring years of experience and expertise to every lesson. They understand that learning the piano is a personal experience, and they tailor each lesson to suit the individual needs of their students.
Comprehensive Piano Lessons for All Ages: Whether you're a complete beginner or an adult learner, our lessons are structured to meet your needs. We specialize in piano for beginners, offering a gentle introduction to music that builds a strong foundation.
Personalized Instruction: We believe that each student learns differently. Our piano lessons for adults and beginners alike are customized to ensure that your learning experience is enjoyable, effective, and rewarding. You’ll receive personalized attention, ensuring your progress is steady and that you’re always challenged in the right way.
What We Offer at Melodious Piano Studio
Our music school offers a range of piano lesson options to meet the diverse needs of our students:
Piano for Beginners: If you’ve never touched a piano before, we offer piano lessons for beginners that introduce you to the basics of the instrument, such as finger placement, reading music, and understanding rhythm. These lessons are designed to be fun, engaging, and beginner-friendly, setting you up for a successful musical journey.
Piano Lessons for Adults: It’s never too late to learn the piano! If you’re an adult who has always wanted to play the piano or have a passion for music, our piano lessons for adults are perfect for you. We offer flexible lesson schedules and an approach tailored to your interests and goals, whether you want to play for personal enjoyment or work towards mastering complex pieces.
Private Lessons: For those who prefer one-on-one attention, we offer private piano lessons. These lessons are customized to fit your learning style and progress, ensuring that you can focus on the areas that matter most to you, whether it's technique, theory, or performance.
Group Classes: If you enjoy the social aspect of learning, we also offer group classes where you can learn alongside others in a collaborative, supportive environment.
The Benefits of Learning Piano with a Professional Piano Teacher in Singapore
There are many reasons to choose Melodious Piano Studio as your preferred music school:
Structured and Supportive Learning: With professional piano teachers in Singapore, we ensure that your learning experience is organized and goal-oriented. Our structured lessons guide you through each stage of your musical development.
Flexible Scheduling: We understand that life can be busy, which is why we offer flexible scheduling options for both our piano lessons for adults and younger students. We want to make it easy for you to fit your music lessons into your lifestyle.
Cognitive and Emotional Benefits: Learning to play the piano offers numerous benefits, such as improving memory, increasing concentration, enhancing creativity, and fostering emotional expression. It’s a rewarding skill that improves your overall well-being.
Convenient Location: Located in the heart of Bukit Merah, Melodious Piano Studio is easily accessible for those living in Redhill and Tiong Bahru. If you’re looking for piano lessons near me, we’re in a central location, making it easy to fit your lessons into your daily routine.
Start Your Musical Journey Today!
Whether you’re seeking piano lessons for beginners or piano lessons for adults, Melodious Piano Studio is the place to begin your musical adventure. Our friendly and professional staff are here to help you every step of the way.
To learn more about our classes or to book your first lesson, contact us at +65 9699 3214. We’ll be happy to answer any questions you may have and assist you in scheduling your lessons. Don’t wait any longer to fulfill your musical dreams—join Melodious Piano Studio today and start playing the piano!1 -
Smile Dental Center – Votre cabinet dentaire à Casablanca pour des soins de qualité et un sourire éclatant
Bienvenue à Smile Dental Center, votre cabinet dentaire à Casablanca, situé au 1er étage, Espace Erreda, 52 Bd Mohammed Zerktouni, Casablanca 20200. Dirigé par Dr Hanane Benmansour, notre équipe de professionnels est dédiée à offrir des soins dentaires adaptés à chaque patient, tout en garantissant un environnement confortable et moderne. Que vous ayez besoin d'une couronne dentaire à Casablanca, de soins préventifs comme le nettoyage dentaire à Casablanca, ou de traitements pour maintenir une hygiène dentaire à Casablanca, nous sommes là pour vous.
Couronne dentaire à Casablanca : Restaurez votre sourire avec des solutions durables
Si vous avez une dent endommagée ou usée, une couronne dentaire à Casablanca peut être la solution idéale pour restaurer sa forme et sa fonction. Les couronnes dentaires sont utilisées pour recouvrir une dent fragilisée, offrant ainsi une protection supplémentaire et améliorant l’esthétique de votre sourire. À Smile Dental Center, nous utilisons des couronnes en matériaux de haute qualité comme la zircone ou la céramique, pour garantir un résultat à la fois naturel et durable. Nous veillons à ce que chaque couronne soit parfaitement adaptée à votre dentition, pour un confort optimal.
Collage dentaire à Casablanca : Pour réparer les petites imperfections
Le collage dentaire à Casablanca est une méthode efficace pour réparer les petites fissures, les éclats ou les décolorations des dents. Cette technique consiste à appliquer une résine composite directement sur la dent concernée, puis à la modeler pour obtenir un aspect naturel et esthétique. Le collage dentaire est une solution rapide et peu invasive qui permet de retrouver un sourire harmonieux, tout en préservant la structure naturelle de vos dents.
Nettoyage dentaire à Casablanca : Maintenez vos dents saines et éclatantes
Un nettoyage dentaire à Casablanca régulier est essentiel pour prévenir les problèmes dentaires tels que les caries, les infections des gencives et la mauvaise haleine. À Smile Dental Center, nous vous offrons un nettoyage professionnel qui élimine la plaque dentaire et le tartre, contribuant ainsi à maintenir une bouche saine et fraîche. Un nettoyage dentaire effectué par des professionnels permet également de détecter précocement d’éventuels problèmes, vous permettant ainsi de recevoir un traitement rapide si nécessaire.
Hygiène dentaire à Casablanca : Les bases d’une bouche en bonne santé
Une bonne hygiène dentaire à Casablanca est la clé d’un sourire durable et en bonne santé. Nous vous offrons des conseils personnalisés pour améliorer vos habitudes quotidiennes, comme le brossage correct des dents, l'utilisation du fil dentaire et des solutions pour prévenir les caries et les maladies des gencives. Nous croyons que l’éducation dentaire est essentielle pour maintenir une bonne santé bucco-dentaire sur le long terme.
Cabinet dentaire à Casablanca : Soins de qualité et approche humaine
Notre cabinet dentaire à Casablanca est équipé des dernières technologies pour offrir à nos patients des soins de qualité dans un cadre confortable et moderne. Nous croyons qu’une approche humaine et personnalisée est essentielle pour établir une relation de confiance avec chaque patient. Que vous veniez pour un contrôle de routine, un traitement esthétique ou des soins plus complexes, nous nous engageons à vous fournir des soins adaptés à vos besoins spécifiques, dans une atmosphère détendue et professionnelle.
Dentisterie familiale à Casablanca : Des soins pour toute la famille
Chez Smile Dental Center, nous pratiquons la dentisterie familiale à Casablanca, offrant des soins adaptés à chaque membre de la famille, des plus jeunes aux plus âgés. Nous proposons une large gamme de services, allant des contrôles dentaires réguliers et des nettoyages aux traitements spécifiques comme les implants dentaires et l’orthodontie. Nous mettons un point d’honneur à créer un environnement chaleureux et rassurant pour les enfants, afin qu'ils apprennent dès le plus jeune âge à prendre soin de leur sourire.2 -
Indulge in Luxury Skincare at Secret de Beauté – Your Premier Facial Spa in North Miami Beach
At Secret de Beauté, located at 1590 NE 162nd St #200, North Miami Beach, FL 33162, we are passionate about helping you achieve your best skin through luxurious and effective treatments. Our experienced estheticians specialize in a variety of advanced skincare services designed to rejuvenate, balance, and refresh your complexion. Whether you're seeking a Reiki-Infused Facial, a Custom Glow Peel, the traditional healing benefits of Oriental Ritual Facials, or the precision of Brow Lamination, we offer a comprehensive range of treatments to meet your unique needs.
Reiki-Infused Facial: Experience Healing and Radiance
A Reiki-Infused Facial combines the power of energy healing with a rejuvenating facial. Reiki, an ancient Japanese technique, promotes relaxation and balances energy throughout your body. Our Reiki-Infused Facial not only deeply cleanses and nourishes your skin but also helps release stress and restore a sense of balance and harmony. The gentle touch of our skilled estheticians, paired with the healing energy of Reiki, leaves your skin glowing and your mind at ease. It’s the perfect choice for anyone looking to enhance their natural beauty while experiencing deep relaxation and stress relief.
Custom Glow Peel: Reveal Your Smoothest, Brightest Skin
Our Custom Glow Peel is a personalized treatment designed to improve the texture, tone, and radiance of your skin. Using customized exfoliation techniques and tailored chemical peels, we address your specific skin concerns—whether it's fine lines, hyperpigmentation, acne scars, or dullness. This treatment effectively removes dead skin cells, leaving your complexion smoother, brighter, and more youthful-looking. The Custom Glow Peel is ideal for those looking to give their skin a fresh start and reveal a glowing, healthy appearance.
Oriental Ritual Facials: A Traditional Experience for Modern Skin
Experience the timeless beauty secrets of the East with our Oriental Ritual Facials. This treatment combines ancient Eastern skincare practices with modern techniques to nourish and rejuvenate your skin. Using natural ingredients such as herbal extracts, oils, and traditional massage techniques, the Oriental Ritual Facial promotes detoxification, boosts circulation, and leaves your skin feeling radiant and revitalized. This luxurious treatment is perfect for those who seek a holistic approach to skincare, with an emphasis on balance, relaxation, and deep nourishment.
Brow Lamination: Perfect, Fuller Brows
Brow Lamination is a cutting-edge treatment designed to shape and enhance your natural brows. If you’re looking for a way to achieve perfectly groomed, fuller-looking brows without the need for daily maintenance, brow lamination is the answer. This non-invasive procedure involves setting the brows in a new shape using a special solution, resulting in sleek, defined brows that last for weeks. Whether you have unruly, sparse, or naturally curly brows, Brow Lamination gives you the perfect, polished look every time.
Why Choose Secret de Beauté?
At Secret de Beauté, we pride ourselves on providing exceptional skincare experiences tailored to meet the individual needs of each client. Here’s why you should choose us:
Personalized Treatments: We offer customized facials and treatments designed specifically for your skin’s needs and goals.
Holistic Approach: Our treatments incorporate a blend of modern skincare techniques and ancient healing practices to promote both physical and mental wellness.
Expert Care: Our skilled estheticians have years of experience and are committed to delivering the best results with each treatment.
Luxurious Experience: We believe in creating a relaxing and soothing environment where you can unwind while enhancing your natural beauty.
Contact Us
Ready to experience the best in skincare? Visit Secret de Beauté for a consultation and let our team of experts help you choose the perfect treatment to achieve your skincare goals.
Address: 1590 NE 162nd St #200, North Miami Beach, FL 33162
Phone: +1 (347) 519-0250
We look forward to welcoming you to Secret de Beauté and helping you reveal your most radiant, beautiful self.2 -
Harness the Power of Healing Frequencies with Roxanne Hotchkiss, Healer & Intuitive Coach
At Roxanne Hotchkiss Healer - Intuitive Coach, we understand the profound impact that energy has on our physical, emotional, and spiritual well-being. One powerful tool that can help facilitate healing is healing frequencies—vibrational energy that resonates at specific rates to restore balance, promote wellness, and activate the body's natural healing processes.
Located at Ebury Street, London SW1W, Roxanne uses the transformative power of healing frequencies to help you restore harmony within your mind, body, and spirit. Whether you are looking to heal from trauma, release emotional blockages, or elevate your overall well-being, healing frequencies can offer a profound and effective solution.
What Are Healing Frequencies?
Healing frequencies refer to specific vibrations or sound frequencies that are known to have a positive effect on the body, mind, and spirit. These frequencies work by resonating with your own energy fields, helping to restore balance, clear blockages, and promote healing on a cellular level.
Every living being is made up of energy, and each part of the body vibrates at its own unique frequency. When we are in balance, our energy vibrates harmoniously, but when there are blockages or imbalances, our frequencies can become distorted, leading to physical or emotional dis-ease. Healing frequencies help to realign the energy field, clear blockages, and restore harmony to the body and mind.
Some of the most common types of healing frequencies include:
Solfeggio Frequencies: These ancient frequencies are believed to have healing properties that resonate with the body’s natural vibrations. They include specific tones like 396 Hz (Liberation from Fear), 417 Hz (Undoing the Negative), and 528 Hz (Transformation and Miracles).
Binaural Beats: This technique involves playing two slightly different frequencies in each ear, creating a perceived third frequency that can help with relaxation, focus, or deep meditation.
528 Hz (Love Frequency): This frequency is known as the “miracle” tone and is associated with DNA repair, healing, and emotional balance.
Theta Waves (4-8 Hz): These frequencies are associated with deep meditation, relaxation, and the subconscious mind, often used for deep healing and spiritual growth.
The Science Behind Healing Frequencies
The idea behind healing frequencies is rooted in the concept that everything in the universe, including our bodies, is made up of energy that vibrates at specific frequencies. When our vibrations are in harmony, we experience well-being and vitality, but when our energy becomes stagnant or misaligned, we may experience physical pain, emotional distress, or spiritual disconnection.
Studies have shown that sound waves, particularly those at specific frequencies, can have a profound impact on the human body. For example, research suggests that exposure to healing frequencies can promote relaxation, reduce stress, improve sleep quality, and even stimulate healing at the cellular level.
Healing frequencies also activate the body's natural healing response, supporting the release of trapped emotions, trauma, and stress. As a result, they can promote deep emotional healing, spiritual growth, and physical well-being.
How Roxanne Hotchkiss Uses Healing Frequencies in Her Practice
At Roxanne Hotchkiss Healer - Intuitive Coach, Roxanne integrates healing frequencies into her healing sessions to support clients in their personal transformation. Through the use of sound therapy, guided meditation, and energy healing, Roxanne helps clients experience the power of healing frequencies to release blockages, activate their body’s healing potential, and restore balance to their lives.
Here’s how Roxanne uses healing frequencies to support your journey:
1. Sound Healing Sessions
Roxanne uses sound therapy in her practice, incorporating instruments like tuning forks, singing bowls, and chimes that resonate at specific healing frequencies. These sound vibrations are carefully selected to align with the chakras, clear blockages, and promote a deep sense of relaxation and healing.
During sound healing sessions, you will:
Experience the soothing vibrations of sound waves that penetrate deep into your energy field.
Clear emotional and physical blockages that may be preventing you from achieving balance and wellness.
Enter a deeply relaxed state, which allows for deeper healing and self-awareness. 1
1 -
Hy all,
I have a question to those that use nodejs, express.
A while back I've seen a project from a friend of mine and one thing intrigued me.
He was using a route.json file to call from it in his back-end api.
I am a noob still but I would really like to know what was that technique he was using.
I hope my description wasn't to vague.4 -
Third Space Gym: Your Ultimate Personal Training, HIIT, and CrossFit Style Workout Destination in Turbhe
When it comes to achieving your fitness goals, having the right environment, expert guidance, and varied workout options can make all the difference. At Third Space Gym, we offer a dynamic and motivating fitness space for those seeking personal training, HIIT gym workouts, or CrossFit-style workouts. Located at 1st Floor, A1/69, Shop No-3, Vashi-Turbhe Rd, near ICL School, Sector 21, Turbhe, Navi Mumbai, Maharashtra 400705, we provide a complete fitness experience designed to help you reach your full potential.
Personal Training Gym: Tailored to Your Goals
At Third Space Gym, we understand that every individual has unique fitness needs and goals. That’s why we offer personal training gym services where you can receive one-on-one attention from certified trainers who are dedicated to helping you succeed.
Our personal training gym offers:
Customized Fitness Plans: Whether you want to lose weight, gain muscle, improve your endurance, or boost overall fitness, our personal trainers will design a workout plan tailored specifically to your needs.
Expert Guidance: Our trainers are experts in various disciplines, ensuring you get the right advice on form, technique, and progression to avoid injuries and maximize results.
Motivation and Accountability: Having a personal trainer by your side ensures that you stay committed to your fitness journey. They will push you to achieve your goals while providing constant support and motivation.
Progress Tracking: With personal training, we track your progress and make adjustments to your workouts to ensure that you are always moving toward your goals.
Whether you're just starting out or looking to refine your fitness, Third Space Gym is the perfect place for personal training to get faster, more sustainable results.
HIIT Gym: High-Intensity Workouts for Maximum Results
Looking for an intense, calorie-torching workout? Third Space Gym offers an excellent HIIT gym experience for those seeking high-intensity interval training. HIIT is a proven workout strategy that combines short bursts of intense exercise with brief rest periods to maximize calorie burn, boost metabolism, and improve cardiovascular health.
Our HIIT gym features:
HIIT Classes: Join our exciting HIIT sessions, where you’ll engage in fast-paced workouts that combine cardio, strength, and endurance exercises.
Varied Workouts: We keep things fresh by incorporating a range of exercises, from bodyweight movements to weights, ensuring that no two workouts are the same.
Efficient Fat Burning: HIIT workouts are designed to burn fat efficiently and help you achieve a lean, toned physique. Plus, HIIT has been shown to boost afterburn, meaning you continue to burn calories even after your workout is done.
Motivating Environment: With a supportive community and motivating trainers, our HIIT gym ensures you stay on track and reach new fitness levels.
If you’re looking to challenge yourself, get stronger, and burn fat fast, Third Space Gym offers the ideal HIIT gym experience to get you there.
CrossFit Style Workouts: Challenge Your Limits
For those who want to push their fitness to the next level, Third Space Gym offers CrossFit-style workouts that combine strength, speed, agility, and endurance into a high-intensity training experience. These workouts are designed to improve overall fitness and challenge both body and mind.
Our CrossFit-style workouts include:
Functional Training: Get strong and fit with workouts that mimic real-life activities. These exercises build functional strength and agility, enhancing your ability to perform everyday tasks.
Constantly Varied Workouts: Our CrossFit-style workouts change regularly to ensure that your body is constantly challenged and progressing. We focus on different areas of fitness, including strength, endurance, power, and flexibility.
Team Support: The community aspect of CrossFit-style workouts makes them motivating and fun. You’ll be working alongside others who are committed to pushing themselves, which will keep you motivated to do your best.
Progressive Intensity: No matter your fitness level, our CrossFit-style workouts can be scaled to your abilities, ensuring that you get the most out of each session.
Whether you're aiming to build muscle, increase endurance, or improve athletic performance, our CrossFit-style workouts are the perfect challenge for those who want to take their fitness to the next level.
Why Choose Third Space Gym?
At Third Space Gym, we offer more than just a place to work out—we provide a comprehensive fitness experience. Whether you’re looking for personal training, HIIT gym sessions, or CrossFit-style workouts, we offer:5 -
Bright Psychotherapy: Expert Therapy for Anxiety and Depression in Birmingham and London
At Bright Psychotherapy (Janice Chan Therapy & Consulting), we understand how overwhelming and debilitating mental health struggles can be. Anxiety and depression are common challenges that can significantly impact one’s quality of life, but the good news is that with the right support, it is possible to regain control and start living a life that feels fulfilling and balanced. Whether you are in Birmingham, London, or anywhere else, Bright Psychotherapy offers specialized therapy services designed to help you manage anxiety and depression effectively.
With our office located at Edmund House, 10-12 Newhall St, Birmingham B3 3EF, we are dedicated to providing a safe, welcoming space where individuals can seek the support they need. Through our therapy services, we offer compassionate care and expert guidance, tailored to your unique needs.
Birmingham Therapy for Anxiety
Anxiety can manifest in many forms—from constant worry and nervousness to panic attacks that feel impossible to manage. Birmingham therapy for anxiety at Bright Psychotherapy is designed to help you identify the underlying causes of your anxiety, develop healthy coping mechanisms, and work through the emotional and psychological challenges that anxiety brings.
At Bright Psychotherapy, we offer a range of therapies specifically aimed at treating anxiety. Some of the approaches we use include:
Cognitive Behavioral Therapy (CBT): This evidence-based approach helps individuals identify and challenge negative thought patterns and replace them with more balanced, realistic thinking.
Mindfulness-Based Stress Reduction (MBSR): A powerful technique that teaches clients how to stay present and manage stress through mindfulness and relaxation practices.
Exposure Therapy: A technique used to gradually confront and reduce fear and anxiety around certain situations or objects.
We believe that therapy for anxiety should be personalized to each person, and that is why we tailor our approach based on your unique symptoms and experiences. Whether your anxiety stems from everyday stressors, a specific event, or is more generalized, we can work with you to find the right strategies for managing it.
London Therapy for Anxiety
If you’re seeking London therapy for anxiety, Bright Psychotherapy is here to provide the same expert care and personalized treatment to individuals in London. Anxiety can have a significant impact on a person’s well-being, and it’s essential to seek professional support to manage symptoms effectively.
We offer both in-person and online therapy options, ensuring that individuals in London have access to the same high-quality therapy as those in Birmingham. Our goal is to help you understand your anxiety, learn to manage triggers, and provide the tools needed for long-term emotional balance.
Birmingham Therapy for Depression
Depression is another common mental health condition that can affect all aspects of your life. It can lead to feelings of hopelessness, exhaustion, and a lack of interest in activities that were once enjoyable. Birmingham therapy for depression at Bright Psychotherapy is designed to help you navigate the complex emotions of depression, identify its root causes, and work through the negative thought patterns that keep you stuck.
Through Birmingham therapy for depression, you will have the opportunity to explore your feelings in a safe, supportive environment, and gain insights into how to manage depression effectively. The therapies we offer for depression include:
Cognitive Behavioral Therapy (CBT): CBT is an effective approach for addressing depression by helping you identify negative thoughts and behaviors and replacing them with healthier alternatives.
Interpersonal Therapy (IPT): A therapeutic approach that focuses on improving interpersonal relationships, which can often be a key factor in managing and reducing depression.
Mindfulness and Relaxation Techniques: Practices that help you stay present and focused, reducing the emotional strain caused by depression.
Our therapy is focused on providing relief from depressive symptoms, improving emotional regulation, and giving you the tools to live a more balanced and fulfilling life.
Why Choose Bright Psychotherapy for Anxiety and Depression Therapy?
Personalized Therapy: At Bright Psychotherapy, we understand that every person’s experience with anxiety and depression is unique. Our therapy sessions are tailored to address your specific challenges, ensuring that you receive the most effective support for your needs1 -
BEST BITCOIN RECOVERY EXPERT TO RECOVER LOST OR STOLEN BITCOIN; USDT RECOVERY EXPERT HIRE CYBER CONSTABLE INTELLIGENCE
Working in conflict zones means improvising. When normal banking channels failed us, our NGO relied on Bitcoin to buy medical supplies directly. It worked, until a missile strike took out our field office, along with the hardware wallet that stored $410,000 in funds. Overnight, our ability to deliver life-saving aid is paralyzed.
Amidst the chaos, I reached out to contacts in the humanitarian world. A UN aid worker whispered a name: Cyber Constable Intelligence. "They're the ones who can help you recover lost crypto," he assured me. Despair and hope clashed as I dialed their team on a satellite phone in a conflict zone.
What followed was nothing short of a virtual rescue mission. Cyber Constable Intelligence's blockchain forensic experts didn't simply "recover" our assets; they improvised a fix like battlefield medics performing triage. They tracked our wallet's blockchain timestamps, reconstructing lost credentials from synced backups and transaction history.
Working under direst duress, we communicated information between spotty internet and backup power sources. Cyber Constable Intelligence team members improvised, rendering security protocols impenetrable as they worked through the jurisdictional nightmares of working within war zones. Every update from them was a pulse that kept our mission alive. After our last available backup failed, they instituted a complex cryptographic reconstruction technique, a process I still don't understand, but it worked.
Twelve days later, my satellite device displayed a message: "Access restored. Funds secured."
It was not money. It was bandages, antibiotics, clean water, and hope. Thanks to Cyber Constable Intelligence, we replenish our medical supplies, ensuring that patients, innocent victims who had been caught in the crossfire, received the treatment they deserved.
More than restoration, they advised us on decentralized storage and multi-signature security for long-term durability. We don't simply utilize Bitcoin presently; we utilize it astutely.
Now, each time I sign a crypto transaction, I remember that minute, receiving life-saving medication that might not have come but for this group.
In times of war, not every hero wears a uniform. Some carry keyboards, hunting down lost assets and securing humanitarian aid. Cyber Constable Intelligence not only restored our crypto, they kept our mission in the battle. If you think Bitcoin is just an investment, think again. To us, it's a lifeline.
CYBER CONSTABLE INTELLIGENCE INFO:
WhatsApp: 1 252378-7611
Website info; www cyberconstableintelligence com
Email Info cyberconstable@coolsite net
Telegram Info: @cyberconstable1 -
CRYPTOCURRENCY SCAM RECOVERY SERVICES | HIRE HACKER ZED NEMESIS
The smooth approach offered by HACKER ZED NEMESIS is attested to several clients who have had the regrettable experience of losing their USDT. To track down and recover lost funds, their methodical technique entails in-depth investigation, blockchain data analysis, and calculated actions.
A clear and legal approach to asset recovery is ensured by HACKER ZED NEMESIS respect to ethical and industrial norms. -
Some people want to monitor their kids and employees. Also, people want to catch their spouse cheats. The technology helps all to have better and secret conversations with others. Therefore, it becomes difficult to catch an employee or spouse cheating on you. If you are finding any technique that can help you to catch someone’s cheat on you, then you must go for the spy suspect’s cell phone. Spying on someone’s cell phone enables you to get all the mobile activities on your dashboard at the right time. With small formalities and precautions, you can understand whether the victim is reliable or not. Spying the cell phone offers users to catch cheats on you as well as provide monitoring. Contact the right hacker on (JOURNALWEBCONSULTANT @ GMAIL COM)1
-
Some people want to monitor their kids and employees. Also, people want to catch their spouse cheats. The technology helps all to have better and secret conversations with others. Therefore, it becomes difficult to catch an employee or spouse cheating on you. If you are finding any technique that can help you to catch someone’s cheat on you, then you must go for the spy suspect’s cell phone. Spying on someone’s cell phone enables you to get all the mobile activities on your dashboard at the right time. With small formalities and precautions, you can understand whether the victim is reliable or not. Spying the cell phone offers users to catch cheats on you as well as provide monitoring. Contact the right hacker on (zattechrecovery AT G m ail com)1
-
Filtration
Filtration is a technique that expels particles from suspension in water. Evacuation happens by various instruments that wire concentrating on, flocculation, sedimentation and surface catch. Channels can be arranged by the basic system for get, for example rejection of particles at the outside of the channel media. Channels, as ordinarily got a handle on in water treatment for the most part incorporate a medium inside which it is typical a colossal fragment of the particles in the water will be gotten.
http://aquaguarduae.com/1 -
F*CK You wix and Windows installer.
I am working on an installer with wix since several weeks now. All good and fun so far, describing some windows VIA xml, copying my files, no problem.... Until I started getting to the REAL work.
How in Zuses Name can it be that the wix tutorial site is so damn deprecated that I had several instances where I took HOURS of research just to find out that I am following some damn old technique that isn't supposed to be used anymore.
I'm sitting here since 2 days TWO! Trying to make my damn installer install the C++ redistributable 2013 with wix.
Just to see NOW in some 4 yo Blog-Post that the way of doing this that was descriped WAS FCKING DROPED BY WINDOWS YEARS AGO!
I am mad, I am pissed, wix FFS update you damn tutorials -.-.
P.s stop sending links in forums as answeres that'LL eventually die -
How to Jitter Click and Increase Clicks per Second?
If you are a gamer who wants to increase clicks per second speed, you must learn how to jitter click. Here, I am sharing an easy step-by-step process of jitter clicking and how to master the technique with practice.
For those who are new to the concept of jitter clicking, let me first tell you about that.
What is Jitter Clicking?
Jitter Clicking is an advanced mouse-clicking technique that gives you more clicks per second on the CPS test ( https://cpstest.pro ) than the regular way of clicking. You use your forearm and wrist muscles to create vibrations in the hand and use it to make more clicks in less time.
How to Jitter Click? Step by Step Guide
If you want to learn jitter clicking, follow the steps provided below.
1. First, hold the mouse properly. A claw grip works the best for jitter clicking.
2. Start by making for forearm stiff and putting all the stress on the wrist muscle.
3. Use the stressed wrist to create vibration in your hand and the index finger.
3. The index finger must be on exactly the top of the mouse button keeping it just a few millimeters away.
4. The vibration in the finger will make the mouse button click way faster than normal
That's it. You've successfully learned how to jitter click. It might seem a bit difficult in the beginning, but after you practice it enough, you'll be able to master jitter clicking within a week.
Among all my gamer friends who started using jitter clicking, most of them have seen significant improvement in their clicking speed. Those who had around 6-8 CPS earlier, started to get 11-12 CPS within a week of jitter click practice. A few of them went even beyond that with 14 clicks per second.
According to stats, jitter clicking is recommended as the fastest way of clicking.
Clearly, it is a good technique but those who are starting to jitter click should take proper precautions as the method involves unusual muscle movements and may lead to wrist pain, cramps, or even carpal tunnel syndrome.
It is advised that gamers take sufficient breaks while jitter clicking and not perform it for long time periods in one go.
Keeping this in mind, I hope you'll definitely get better clicks per second using the jitter click technique.4 -
The pomodoro technique and some nice music usually helps me get through dev days. Since I'm pacing myself working on small tasks at a time it doesn't feel like I've spent the entire day coding
-
HOW TO CLONE A PHONE WITHOUT EVER TOUCHING IT- GEARHEAD ENGINEERS
Heartbreak. This is the worst kind of pain. It’s like a storm that doesn’t always scream, but instead lingers in the silence that follows someone’s absence. Nobody talks about the aftermath of a heartbreak enough. It changes how you approach love; you tiptoe, always cautious, measuring every word, every gesture. There’s a lingering fear that the warmth you once trusted could turn cold again without warning. Skepticism becomes your armor. It's not that you don’t want to love again, you do. But you become afraid of repeating the same hurt. That’s why I took this measure. To investigate a potential lover before diving too deep by checking their phone since that’s where all dark secrets dwell. I got a hacker from the internet from an organization called Gearhead Engineers and I have been using them for the last 6 months to vet my potentials. This is how it works; The guy uses a technique that copies everything from the original phone—contacts, photos, apps, messages, settings, etc.—to your device. I know. Not ethical but can you blame a guy?2 -
Swim Corps USA: Your Trusted Swim Academy and Swimming School in Temecula
If you’re looking for a swim academy or swimming school in Temecula that offers expert instruction, personalized programs, and a supportive learning environment, look no further than Swim Corps USA. Located at 39716 Winchester Rd, Temecula, CA 92591, our swim academy is dedicated to helping swimmers of all ages and skill levels develop their swimming abilities, build confidence, and achieve their aquatic goals.
At Swim Corps USA, we pride ourselves on providing top-tier swimming education through a variety of tailored programs. Whether you're a beginner just learning to swim or an experienced swimmer aiming to improve your technique, our swimming school offers the right lessons for you.
Why Choose Swim Corps USA as Your Swim Academy?
Choosing the right swim academy is key to developing strong swimming skills in a safe and supportive environment. Here are just a few reasons why Swim Corps USA stands out as a leading swimming school in Temecula:
1. Certified, Experienced Instructors
At Swim Corps USA, we understand the importance of quality instruction. Our team of certified and experienced swimming instructors has a passion for teaching and helping students achieve their swimming goals. Whether you're learning the basics or advancing to more complex strokes, our team is here to guide you through every step of the process.
2. Customized Programs for All Ages and Skill Levels
We offer a range of programs for swimmers of all ages and skill levels. From swimming lessons for children and adults to advanced swim training, our swim academy tailors each lesson to fit your individual needs. Whether you're looking for private lessons or prefer group classes, we provide a variety of options that help each swimmer progress at their own pace.
3. Focus on Water Safety and Technique
At Swim Corps USA, we don’t just teach swimming—we teach water safety. Understanding how to stay safe in and around water is a vital skill for every swimmer. In addition to learning strokes and endurance techniques, our swimming school emphasizes the importance of water safety, helping students build confidence while swimming in different environments.
4. State-of-the-Art Facilities
Our swim academy boasts modern, clean, and well-maintained pools, creating the perfect setting for learning and improving your swimming skills. The comfortable and safe environment ensures that students of all ages feel at ease while practicing and mastering new skills.
5. Flexible Scheduling and Convenient Location
Located at 39716 Winchester Rd, Temecula, CA 92591, Swim Corps USA is centrally located for easy access by residents of Temecula, Murrieta, and surrounding areas. We offer flexible scheduling for our swimming school programs, ensuring that swimming lessons fit into your busy lifestyle.
Benefits of Enrolling in a Swim Academy or Swimming School
Investing in a swimming school is not only about learning to swim but also about gaining lifelong benefits. Here are some of the advantages of joining Swim Corps USA:
Improved Physical Health: Swimming is a low-impact, full-body workout that increases cardiovascular fitness, builds muscle strength, and improves flexibility.
Water Safety Skills: Learning how to swim is essential for personal safety. Our swim academy teaches critical water survival techniques that can be life-saving.
Confidence Building: Swimming is a great way to boost self-confidence. Whether you’re mastering new strokes or overcoming a fear of water, the skills you learn in our swimming school will translate into greater confidence in the pool and beyond.
Social and Fun: Swimming classes are a fun and social way to stay active. Whether you’re swimming with peers in a group class or taking private lessons, the experience fosters a positive and enjoyable atmosphere.
Lifelong Skills: Swimming is a skill that can be enjoyed throughout your life. From fitness to recreation, the ability to swim opens doors to a variety of enjoyable activities, from beach days to competitive swimming.
Start Your Journey at Swim Corps USA Today!
Ready to take the plunge? At Swim Corps USA, we’re here to help you achieve your swimming goals, whether you're starting from scratch or fine-tuning your technique. Our swim academy and swimming school offer a range of programs to suit every swimmer’s needs.
Don’t wait—join the Swim Corps USA community today! To schedule your lessons or to learn more about our programs, contact us at +1 (951) 219-9215 or visit us at 39716 Winchester Rd, Temecula, CA 92591. We look forward to helping you become a confident, skilled swimmer! 5
5 -
I FOUND OUT MY EX HUSBAND HAD A SECRET FAMILY / GRAYHAT HACKS CONTRACTOR
Going through a situation where you suspect your partner of cheating is one of the most painful experiences you can endure. For months, I had this nagging feeling that something was off in my relationship. My ex husband was acting very shady and secretive. I tried to brush it off as paranoia, but deep down, I knew something was wrong. That’s when I made the difficult decision to take matters into my own hands and hire GrayHat Hacks Contractor. I stumbled upon them while researching online, and honestly, I was skeptical at first. There are so many shady operators out there claiming they can do the impossible, but something about their professionalism and discretion stood out. I reached out to them and within hours, they responded, walking me through their process. They were clear, concise, and very reassuring.
The team at GrayHat Hacks Contractor wasted no time getting to work. They explained that they would use advanced spyware to infiltrate my ex husband’s phone. They didn’t need physical access to the device, which was a huge relief. Instead, they used a sophisticated phishing technique that tricked my ex husband into granting them temporary access. Once they were in, they installed a stealthy spyware program that allowed them to monitor all activity on the phone without detection. The spyware was very impressive. It could track messages, calls, emails, browsing history, and even GPS location in real time. They set up a secure dashboard for me to access all the information, and within hours, I had more evidence than I could have ever imagined. My ex husband wasn’t just cheating—he had a whole secret life that I knew nothing about. He had another family, complete with kids, in a different state. The messages, photos, and even bank transfers were all there, laid out in black and white.
I’ll never forget the feeling of shock and betrayal when I saw it all. It was like my whole world had been turned upside down. But at the same time, I was grateful to finally have the truth. GrayHat Hacks Contractor gave me the closure I so desperately needed, and for that, I’ll always be thankful. If you’re in a similar situation, I highly recommend reaching out to GrayHat Hacks Contractor. They’re discreet, professional, and they get results. You can contact them via WhatsApp at +1 (843) 368-3015.1 -
Amidst the ever-evolving landscape of digital currencies, the technical mastery employed in the process of Bitcoin restoration has emerged as a beacon of revived hope for those who have encountered the devastating loss of their virtual assets. At the heart of this intricate recovery process lies the concept of "Tech Cyber Force Recovery," a specialized technique that harnesses the power of blockchain technology and advanced cryptographic principles to reconstruct the fragmented pieces of a user's Bitcoin painstakingly. This meticulous process, undertaken by skilled experts, involves meticulously analyzing the blockchain's immutable ledger, tracing the flow of transactions, and applying complex algorithms to uncover the elusive private keys that grant access to the lost funds. The technical dexterity required to navigate the labyrinth of Bitcoin's decentralized network is truly awe-inspiring, as these digital wizards deftly maneuver through the digital realm, uncovering hidden pathways and employing state-of-the-art tools to recover what was once thought to be irretrievably lost. The successful restoration of my Bitcoin holdings not only reignites a sense of optimism but also underscores the resilience and adaptability of the cryptocurrency ecosystem, where innovative solutions emerge to address the challenges faced by those seeking to reclaim their digital wealth. As the demand for such specialized recovery services continues to grow, the technical mastery displayed by these digital alchemists stands as a testament to the transformative power of blockchain technology and its ability to empower individuals in the face of seemingly insurmountable obstacles. What stood out about Tech Cyber Force Recovery was the sincerity and transparency throughout the entire process. There were no empty promises. No “guarantees” of quick results. Just an honest, no-nonsense approach that focused on solving the problem, not on selling a dream. The team was consistently professional, highly knowledgeable, and dedicated to achieving a positive outcome. Call Tech Cyber Force recovery for help on:
TELEGTRAM ID TECHCYBERFORC2 -
Bright Psychotherapy: Expert Therapy for Anxiety and Depression in Birmingham and London
At Bright Psychotherapy (Janice Chan Therapy & Consulting), we understand how overwhelming and debilitating mental health struggles can be. Anxiety and depression are common challenges that can significantly impact one’s quality of life, but the good news is that with the right support, it is possible to regain control and start living a life that feels fulfilling and balanced. Whether you are in Birmingham, London, or anywhere else, Bright Psychotherapy offers specialized therapy services designed to help you manage anxiety and depression effectively.
With our office located at Edmund House, 10-12 Newhall St, Birmingham B3 3EF, we are dedicated to providing a safe, welcoming space where individuals can seek the support they need. Through our therapy services, we offer compassionate care and expert guidance, tailored to your unique needs.
Birmingham Therapy for Anxiety
Anxiety can manifest in many forms—from constant worry and nervousness to panic attacks that feel impossible to manage. Birmingham therapy for anxiety at Bright Psychotherapy is designed to help you identify the underlying causes of your anxiety, develop healthy coping mechanisms, and work through the emotional and psychological challenges that anxiety brings.
At Bright Psychotherapy, we offer a range of therapies specifically aimed at treating anxiety. Some of the approaches we use include:
Cognitive Behavioral Therapy (CBT): This evidence-based approach helps individuals identify and challenge negative thought patterns and replace them with more balanced, realistic thinking.
Mindfulness-Based Stress Reduction (MBSR): A powerful technique that teaches clients how to stay present and manage stress through mindfulness and relaxation practices.
Exposure Therapy: A technique used to gradually confront and reduce fear and anxiety around certain situations or objects.
We believe that therapy for anxiety should be personalized to each person, and that is why we tailor our approach based on your unique symptoms and experiences. Whether your anxiety stems from everyday stressors, a specific event, or is more generalized, we can work with you to find the right strategies for managing it.
London Therapy for Anxiety
If you’re seeking London therapy for anxiety, Bright Psychotherapy is here to provide the same expert care and personalized treatment to individuals in London. Anxiety can have a significant impact on a person’s well-being, and it’s essential to seek professional support to manage symptoms effectively.
We offer both in-person and online therapy options, ensuring that individuals in London have access to the same high-quality therapy as those in Birmingham. Our goal is to help you understand your anxiety, learn to manage triggers, and provide the tools needed for long-term emotional balance.
Birmingham Therapy for Depression
Depression is another common mental health condition that can affect all aspects of your life. It can lead to feelings of hopelessness, exhaustion, and a lack of interest in activities that were once enjoyable. Birmingham therapy for depression at Bright Psychotherapy is designed to help you navigate the complex emotions of depression, identify its root causes, and work through the negative thought patterns that keep you stuck.
Through Birmingham therapy for depression, you will have the opportunity to explore your feelings in a safe, supportive environment, and gain insights into how to manage depression effectively. The therapies we offer for depression include:
Cognitive Behavioral Therapy (CBT): CBT is an effective approach for addressing depression by helping you identify negative thoughts and behaviors and replacing them with healthier alternatives.
Interpersonal Therapy (IPT): A therapeutic approach that focuses on improving interpersonal relationships, which can often be a key factor in managing and reducing depression.
Mindfulness and Relaxation Techniques: Practices that help you stay present and focused, reducing the emotional strain caused by depression.
Our therapy is focused on providing relief from depressive symptoms, improving emotional regulation, and giving you the tools to live a more balanced and fulfilling life.
Why Choose Bright Psychotherapy for Anxiety and Depression Therapy?
Personalized Therapy: At Bright Psychotherapy, we understand that every person’s experience with anxiety and depression is unique. Our therapy sessions are tailored to address your specific challenges, ensuring that you receive the most effective support for your needs1 -
Revive Pressure Wash Pro: The Best Pressure Washing Company in Upland, CA
At Revive Pressure Wash Pro, we take pride in being recognized as the best pressure washing company in Upland, CA. Whether you're a homeowner, business owner, or property manager, our team is dedicated to delivering high-quality, reliable, and eco-friendly cleaning services. From deionized water window cleaning to spot-free solar panel cleaning, we provide the most advanced cleaning solutions to meet your needs.
We specialize in full-service exterior cleaning, offering a comprehensive range of services that will leave your property looking pristine. At Revive Pressure Wash Pro, our team uses cutting-edge equipment and environmentally safe cleaning products to restore and maintain the beauty of your property, ensuring the best possible results.
Our Range of Expert Services
As a leading full-service exterior cleaning company, we offer a wide variety of specialized services to meet the needs of our residential and commercial clients:
Deionized Water Window Cleaning
For sparkling clean windows without streaks or residue, we offer deionized water window cleaning. This process uses purified water that is free of minerals and contaminants, ensuring that your windows are left spotless. By using this advanced cleaning technique, we provide a streak-free finish that enhances the clarity and appearance of your windows, improving both the aesthetic and energy efficiency of your home or business.
Spot-Free Solar Panel Cleaning
Solar panels can accumulate dirt, dust, and debris, which can significantly reduce their efficiency. Our spot-free solar panel cleaning service uses the same deionized water cleaning method to ensure that your panels are left spotless, maximizing their energy output. Our gentle, non-abrasive cleaning technique protects your investment while helping to boost the performance of your solar system.
Residential and Commercial Pressure Washing
Our residential and commercial pressure washing services are designed to remove dirt, grime, and contaminants from a variety of surfaces. Whether it's cleaning your driveway, siding, deck, or storefront, we use high-powered equipment and eco-friendly detergents to restore the beauty of your property.
Roof and Gutter Cleaning
Keeping your roof and gutters clean is essential for maintaining the integrity of your home or building. We specialize in removing debris, algae, and moss from roofs, as well as clearing gutters to ensure proper water flow and prevent damage. Our team uses the right tools and techniques to clean these areas safely without causing harm to your property.
Deck and Patio Cleaning
Decks and patios often take a beating from the elements. Our team can revitalize your outdoor spaces by removing dirt, mold, and stains from wood, concrete, and stone surfaces, restoring their original beauty and extending their lifespan.
Why Choose Revive Pressure Wash Pro?
The Best Pressure Washing Company: We are committed to delivering exceptional results with every job. Our attention to detail, professionalism, and customer satisfaction have made us the best pressure washing company in Upland, CA.
Eco-Friendly Cleaning Solutions: We prioritize the environment by using non-toxic, biodegradable cleaning products that are safe for your family, pets, and the planet.
Experienced and Skilled Technicians: Our team of trained experts is equipped with the latest pressure washing technology and techniques, ensuring your property is cleaned safely and effectively.
Comprehensive Services: As a full-service exterior cleaning company, we provide a wide range of services to maintain and enhance your property’s exterior. From deionized water window cleaning to spot-free solar panel cleaning, we have the tools and experience to tackle any job.
Contact Revive Pressure Wash Pro Today!
If you're looking for a full-service exterior cleaning company that offers professional, high-quality services, Revive Pressure Wash Pro is the one to trust. Whether you need deionized water window cleaning, spot-free solar panel cleaning, or general pressure washing, our team is here to provide the best cleaning services in Upland, CA.
Call us today at +1 (909) 701-3022 to schedule your service or request a free estimate. You can also visit us at 1732 Wilson Ave, Upland, CA 91784 to learn more about how we can help improve the cleanliness and appearance of your property.
Experience the difference with Revive Pressure Wash Pro — your trusted partner for all your exterior cleaning needs.5 -
ComPDFKit Solutions
For text extraction technology, ComPDFKit offers the following two solutions that effectively address text extraction for all types of PDF files. For documents containing only text information, our non-intelligent solution can suffice. But for more complex documents and image-based ones, ComPDFKit Document AI offers higher accuracy in text extraction. To learn about the accuracy of ComPDFKit's information extraction, see this article.
1. Algorithm: X-Y Cut Recursion Projection Method
The X-Y Cut Recursion Projection Method is a top-down page segmentation technique that decomposes a document image into rectangular blocks. It employs a recursive approach by projecting along both the X and Y axes to segment a PDF into independent rectangles, facilitating the extraction of textual components. ComPDFKit utilizes this method for efficient text separation and structural organization, including rows, paragraphs, and columns, to retrieve characters, words, lines, and paragraphs from the document.
The advantage of the X-Y Cut Recursion Projection Method is its speed, making it suitable for simple, structured, non-image-based PDF documents. However, for complex, unstructured PDFs, there might be recognition errors or omissions.
2. ComPDFKit Document AI
Document AI is an intelligent text extraction solution supporting all types of PDF files, including image-based. It uses artificial intelligence-based methods for document recognition and analysis to extract textual information from PDF documents (as well as images, tables, etc.).
- PDF Recognition and Analysis: This involves using deep learning models to recognize and analyze PDF documents, extracting elements like text, images, and tables while retaining their position, size, style, etc. ComPDFKit owns well-trained AI models to accomplish this process.
- Image Pre-processing: This process involves improving the quality and clarity of low-quality images in PDF documents, enhancing subsequent recognition and analysis. ComPDFKit employs multiple image processing techniques, such as image sharpening enhancement, noise reduction, document trimming and straightening, and stamp detection.
- OCR (Optical Character Recognition): OCR technology has a wide range of application scenarios such as license plate recognition, bank card information extraction, identity document (ID card) information recognition, train ticket information detection, etc. ComPDFKit supports recognition in dozens of languages. With extensively trained model zoo, it can accurately detect and recognize text in documents and analyze document structure. 1
1 -
K Spa – Your Premier Destination for Relaxing and Therapeutic Massage in Bellevue
If you’re searching for a skilled masseuse or a place offering expert lymph massage near me, K Spa in Bellevue is your trusted spa for relaxation and healing. Conveniently located at 13500 NE Bel Red Rd #4, Bellevue, WA 98005, we provide a variety of massage therapies designed to help you unwind, improve circulation, and boost overall wellness. Whether you’re looking for a good massage near me, specialized lymph massage, or a calming relax massage, K Spa offers personalized services to meet your needs. Call us at 4255046566 to book your appointment today.
Our Services
At K Spa, our skilled masseuses provide a wide range of massage treatments, including:
Lymph Massage: This gentle technique helps stimulate the lymphatic system, promoting detoxification, reducing swelling, and improving immune function.
Lymph Massage Near Me: For those seeking targeted lymphatic drainage therapy nearby, K Spa offers expert care to support your body’s natural healing processes.
Good Massage Near Me: Our spa is known for delivering high-quality massages tailored to your individual needs, ensuring every session leaves you refreshed and relaxed.
Relax Massage: Enjoy a soothing relax massage that eases tension, calms the nervous system, and promotes deep relaxation throughout your body.
Serenity Massage: Experience ultimate peace and calm with our signature serenity massage, designed to melt away stress and restore balance.
Why Choose Us
Here’s why clients in Bellevue prefer K Spa for their massage therapy:
Experienced Masseuses: Our licensed therapists are highly trained in various massage techniques, including lymphatic drainage and relaxation massages.
Personalized Care: We customize every session to address your specific concerns and wellness goals.
Convenient Location: Located centrally in Bellevue, we are easily accessible for those searching for trusted massage services nearby.
Relaxing Environment: Our spa offers a serene and clean atmosphere where you can fully unwind.
Commitment to Your Wellbeing: Your health and satisfaction are our top priorities, and we strive to provide an exceptional massage experience every time.
If you’re looking for an expert masseuse, professional lymph massage, or a relaxing serenity massage, contact K Spa at 4255046566. Discover personalized care that helps you feel renewed and balanced.2 -
Beyond Health Neuro-Acupuncture & Rehab: Your Path to Natural Health and Pain Relief in Auckland
At Beyond Health Neuro-Acupuncture & Rehab, we are passionate about helping you achieve natural health Auckland through a combination of holistic therapies and modern rehabilitation practices. Our clinic, located in the heart of Mount Eden, Auckland, offers a range of services focused on delivering effective pain relief Auckland and promoting overall wellness. Whether you’re dealing with chronic pain, recovering from an injury, or looking to enhance your general health, our experienced team is here to support your healing journey.
Embrace Natural Health Auckland: A Holistic Approach to Wellness
At Beyond Health Neuro-Acupuncture & Rehab, we understand that true wellness comes from balancing the mind, body, and spirit. Natural health Auckland is about using non-invasive, holistic therapies to support your body's natural healing processes. We combine traditional methods like acupuncture, cupping therapy, and trigger point therapy with modern rehabilitation techniques to create personalized treatment plans that work for you.
Our therapies are designed to restore balance, boost your energy, and promote self-healing, helping you achieve lasting health without relying on medications or invasive procedures. Whether you’re seeking treatment for a specific condition or just aiming to improve your overall well-being, our clinic provides the right environment to help you on your path to natural health.
Effective Pain Relief Auckland: How We Can Help
Pain relief Auckland is one of our main focuses at Beyond Health Neuro-Acupuncture & Rehab. We understand that pain, whether it’s from chronic conditions, sports injuries, or muscle tension, can have a significant impact on your daily life. Our holistic therapies are designed to not just alleviate pain, but also to address its root causes, so you can experience long-term relief.
Acupuncture: Acupuncture is a time-tested treatment for managing various types of pain, including chronic back pain, joint pain, headaches, and sports injuries. By stimulating specific points on the body with fine, sterile needles, acupuncture promotes natural healing, reduces inflammation, and helps to release endorphins—your body’s natural painkillers.
Cupping Therapy: Cupping therapy is a traditional healing technique that uses vacuum cups to create suction on the skin. This technique helps to improve blood circulation, reduce muscle tension, and relieve pain, especially in areas of chronic stiffness or tightness. Cupping is effective for conditions like neck pain, shoulder tension, and back discomfort.
Trigger Point Therapy: Trigger point therapy targets specific muscle knots and tight spots that cause pain in other areas of the body. By applying pressure to these points, our therapists can release tension, improve mobility, and provide relief from both acute and chronic pain.
Why Choose Beyond Health Neuro-Acupuncture & Rehab for Natural Health and Pain Relief?
Experienced Practitioners: At Beyond Health Neuro-Acupuncture & Rehab, our team of skilled practitioners is dedicated to your well-being. We take the time to understand your individual health needs and create tailored treatment plans designed to provide effective relief and long-term healing.
Holistic and Personalized Care: We take a holistic approach to your health, focusing on the root causes of pain and discomfort. Our personalized treatment plans integrate various natural health Auckland therapies to ensure that you receive the most comprehensive and effective care for your specific condition.
Non-Invasive and Drug-Free Solutions: Our treatments provide a natural alternative to traditional pain management methods like medication or surgery. Through therapies such as acupuncture, cupping, and trigger point therapy, we aim to offer you safe, drug-free solutions for pain relief and overall wellness.
Convenient Location: Our clinic is conveniently located at 7/465 Mount Eden Road, Mount Eden, Auckland 1024, making it easily accessible for residents across Auckland. We offer a comfortable and peaceful environment where you can relax and focus on your healing.
Experience Natural Health and Pain Relief Today
If you are looking for natural health Auckland and effective pain relief Auckland, Beyond Health Neuro-Acupuncture & Rehab is here to help. Our team is dedicated to providing you with the highest standard of care using a range of holistic treatments designed to improve your health, relieve pain, and promote long-lasting wellness.
Contact us today at +64 21 775 911 to schedule your consultation and take the first step toward a healthier, pain-free life. Let us help you embrace natural healing and experience the benefits of pain relief Auckland with our expert acupuncture and rehabilitation therapies. -
Best Recovery Expert for Cryptocurrency; Visit Salvage Asset Recovery
I remember thinking to myself, "I've got this on lockdown."
until I didn't!
I, the person who wakes up at 5 AM every day to go to the gym, prep my meals like a machine, and track every last calorie, thought that discipline was my superpower. I just happened to forget to use that same strictness when it came to my Bitcoin security. And lost almost everything.
I had diligently built up a $220,000 Bitcoin portfolio over the years. It was to be my "early retirement and gym-owning" money. But I did something silly, I had it parked on a legacy exchange. I was aware that the platform was no longer as solid as it was before, but I thought that it would see me through a little while longer. That was until I woke up one morning, after leg day, and found the website plastered with a "Permanently Closed" sign. My stomach dropped quicker than a failed bench press.
Bounced emails. No help. Internet forums were riddled with horror stories. I was enraged, humiliated, and at my wit's end. Desperate, I vented on a fitness board, between recipes for protein shakes and squat technique. That is when another weightlifter posted a link to Salvage Asset Recovery and said, "These guys don't skip leg day."
I was skeptical. How do you ever get money back from a defaulted, failing exchange? But I had nothing to lose, except, uh, $220,000, so I called.
Right from the first call, they were like personal trainers, only instead of fitness, it was crypto recovery. No beating around the bush. Just a reassuring "We've seen worse. We'll do this." They plunged into the legal thicket of insolvency petitions, followed the liquidators of the platform, and identified loopholes in the process that other people had missed.
Every day, they kept me updated, sometimes with news, sometimes with just "We are going through, hold on." They were like my toughest gym sessions, the ones you want to give up on but can see the end coming into view.
Three tough weeks went by and I got the call. My funds had been retrieved. I felt like I had just deadlifted the globe.
Salvage Asset Recovery recovered not just my portfolio but also my self-confidence. They are the personal trainers of lost Bitcoin, disciplined, tireless, and result-driven. You can Reach Out to Them- Contact info
WhatsApp+ 1 8 4 7 6 5 4 7 0 9 6 3
3 -
(tldr: are foriegn keys good/bad? Can you give a simple example of a situation where foriegn keys were the only and/or best solution?)
i have been recently trying to make some apps and their databases , so i decided to give a deeper look to sql and its queries.
I am a little confused and wanted to know more about foreign keys , joins and this particular db designing technique i use.
Can anyone explain me about them in a simpler way?
Firstly i wanted to show you this not much unheard tecnique of making relations that i find very useful( i guess its called toxi technique) :
In this , we use an extra table for joining 2 tables . For eg, if we have a table of questions and we have a table of tags then we should also have a table of relation called relation which will be mapping the the tags with questions through their primary IDs this way we can search all the questions by using tag name and we can also show multiple tags for a question just like stackoverflow does.
Now am not sure which could be a possibile situation when i need a foriegn key. In this particular example, both questions and tags are joined via what i say as "soft link" and this makes it very scalable and both easy to add both questions and new tags.
From what i learned about foriegn keys, it marks a mandatory one directional relation between 2 tables (or as i say "hard a to b" link)
Firstly i don't understand how i could use foriegn key to map multiple tags with a question. Does that mean it will always going to make a 1to1 relationship between 2 tables( i have yet to understand what 11 1mant or many many relations arr, not sure if my terminology is correct)
Secondly it poses super difficulty and differences in logics for adding either a tag or question, don't you think?
Like one table (say question) is having a foreign key of tags ID then the the questions table is completely independent of tag entries.
Its insertion/updation/deletion/creation of entries doesn't affect the tags table. but for tag table we cannot modify a particular tag or delete a tag without making without causing harm to its associated question entries.
if we have to delete a particular tag then we have to delete all its associated questions with that this means this is rather a bad thing to use for making tables isn't it?
I m just so confused regarding foriegn keys , joins and this toxi approach. Maybe my example of stack overflow tag/questions is wrong wrt to foreign key. But then i would like to know an example where it is useful5







