Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "vulnerabilities"
-
Client: We have a HUGE security problem.
Me: *thinks about any possible vulnerabilities* What is it?
Client: A user can take a picture of our website and steal our content.
I’m done for today.36 -
WINDOWS USER VS LINUX USER
A Windows User's view on computing
I have the blue screen of death again
You'll never hear me say
I'm happy with my computer
At the end of the day
my operating system
dictates
my choice
in programs i use and the features I've
i have complete control
over nothing
i lose sleep
worrying about getting viruses
and
microsoft patching vulnerabilities in time
i don't have time to think about
some thing better.
i've learned
to live with old software issues
There's no way i'm planning
to change, and
its worth it to me
A Linux User's view on computing
(read this bottom to top)14 -
My mom died when I was 7, after which my dad bought me a Commodore 64 so I had something to lose myself in during the mourning process.
I learned everything about that system, from my first GOTO statement to sprite buffers, to soldering my own EPROM cartridges. My dad didn't deal with the loss so well, and became a missing person 5 years later when I was 12.
I got into foster care with a bunch of strict religious cultists who wouldn't allow electronics in the house.
So I ran away at 14, sub-rented a closet in a student apartment using my orphan benefits and bought a secondhand IBM computer. I spent about 16 hours a day learning about BSD and Linux, C, C++, Fortran, ADA, Haskell, Livescript and even more awful things like Visual Basic, ASP, Windows NT, and Active Directory.
I faked my ID (back then it was just a laminated sheet of paper), and got a job at 15-pretending-to-be-17 at one of the first ISPs in my country. I wrote the firmware and admin panel for their router, full of shitty CGI-bin ASP code and vulnerabilities.
That somehow got me into a job at Microsoft, building the MS Office language pack for my country, and as an official "conflict resolver" for their shitty version control system. Yes, they had fulltime people employed just to resolve VCS conflicts.
After that I worked at Arianespace (X-ray NDT, visualizing/tagging dicom scans, image recognition of faulty propellant tank welds), and after that I switched to biotech, first phytogenetics, then immunology, then pharmacokynetics.
In between I have grown & synthesized and sold large quantities of recreational drugs, taken care of some big felines, got a pilot license, taught IT at an elementary school, renovated a house, and procreated.
A lot of it was to prove myself to the world -- prove that a nearly-broke-orphan-high-school-dropout could succeed at life.
But hey, now I work for a "startup", so I guess I failed after all.22 -
Today was my last day of work, tomorrow i have officially left that place. It's a weird feeling because i'm not certain about the future.
The job was certainly not bad, and after all i read on devrant i'm beginning to believe it was one of the better ones. A nice boss, always something to eat/drink nearby, a relaxed atmosphere, a tolerance for my occasionally odd behaviour and the chance to suggest frameworks. Why i would leave that place, you ask? Because of the thing not on the list, the code, that is the thing i work with all the time.
Most of the time i only had to make things work, testing/refactoring/etc. was cut because we had other things to do. You could argue that we had more time if we did refactor, and i suggested that, but the decision to do so was delayed because we didn't have enough time.
The first project i had to work on had around 100 files with nearly the same code, everything copy-pasted and changed slightly. Half of the files used format a and the other half used the newer format b. B used a function that concatenated strings to produce html. I made some suggestions on how to change this, but they got denied because they would take up too much time. Aat that point i started to understand the position my boss was in and how i had to word things in order to get my point across. This project never got changed and holds hundreds of sql- and xss-injection-vulnerabilities and misses access control up to today. But at least the new project is better, it's tomcat and hibernate on the backend and react in the frontend, communicating via rest. It took a few years to get there, but we made it.
To get back to code quality, it's not there. Some projects had 1000 LOC files that were only touched to add features, we wrote horrible hacks to work with the reactabular-module and duplicate code everywhere. I already ranted about my boss' use of ctrl-c&v and i think it is the biggest threat to code quality. That and the juniors who worked on a real project for the first time. And the fact that i was the only one who really knew git. At some point i had enough of working on those projects and quit.
I don't have much experience, but i'm certain my next job has a better workflow and i hope i don't have to fix that much bugs anymore.
In the end my experience was mostly positive though. I had nice coworkers, was often free to do things my way, got really into linux, all in all a good workplace if there wasn't work.
Now they dont have their js-expert anymore, with that i'm excited to see how the new project evolves. It's still a weird thing to know you won't go back to a place you've been for several years. But i still have my backdoor, but maybe not. :P 16
16 -
The awesome moment when a client claims that you are nothing but a script kiddy only minutes before you reveal a $1400 vulnerability on his site 😂4
-
This was at my first internship (ranted about this before but hey fuck it).
- discovered several high critical vulnerabilities in their product. Wrote them down and kindly gave them to my boss/manager (they were the same person). He looked at me like 'the fuck' but I just went home at the end of the day. Next day, I got called into his office. I was a fucker, cancer guy who knew nothing about security, who would never reach anything and I shouldn't criticize their product (I had no right to because I was an intern).
- Bossman went to a meeting with a coworker to present their product. They came back to the office and it very clearly had gone pretty wrong. (we had nothing to do with anything related to the project including the meeting) he called us all bad things he could think of and it was all our fault and so on.
- I do have a transpiration problem but I can partly contain that when it's not too hot and the stress levels are okay. I was only allowed to sit in front of the window. YES IT WAS A MOTHERFUCKING HUGE WINDOW, 35-40 DEGREES FEELING TEMPERATURE AND NO MOTHERFUCKING AIRCONDITIONING. (okay gotta admit that one of the installation guys fell off the roof during the installation BUT THEN AT LEAST GET FANS OR SOMETHING).
Got called into his office multiple times because I smelled and 'couldnt take care of my hygiene'. I was literally sweating my ass off full-time so what the fuck could I do in those temperatures?!?
- my only project there: Google translating their whole CRM. Took us five weeks and the bossman kept pressure on us at all times which didn't FUCKING help.
Was fired after 5 weeks for hygiene reasons and because I didn't do my work well appearantly (still fuck translating all day).
One of the worst things? He pretended everything to go well until the first review came with my mentor (mentor == awesome guy). Then he talked shit about me like it was no-one's business.
I literally cried when I walked home after being fired.16 -
Hey guys,
I have decided to stop worrying about privacy. I have nothing to hide so why should I even care.
I just created an Instagram and a Facebook account and I also installed WhatsApp again and I ordered an Amazon Alexa and a Google home device as well. These voice assistants are just so useful 😊.
I am also gonna use windows again, everything just works and it is the most used operating system so it has to be the best one! It is way securer than Linux because it is not open source and thus hackers can't find vulnerabilities because they can't see the code.12 -
Apparently they didn't want to hear about my vulnerabilities I found because they blocked my IP address.
Seriously? I just wanted to do a disclosure of potential exploits / security issues 10
10 -
This happened at my last internship. There was this other intern and he was a TO THE FUCKING MAX windows fanboy and whenever someone said something bad about windows he'd go full rage. Also, he'd sometimes spend half an hour at my desk explaining why windows was the best and Linux sucked.
This one time, I read about a newly discovered windows vulnerability and told the employees so they'd update quickly and they were like ' thanks for the notification mate!' And then that guy came up to me telling that 'Linux also has severe vulnerabilities sometimes'. YES I FUCKING KNOW THAT I'M JUST TRYING TO GET PEOPLE TO UPDATE FOR THEIR SECURITY YOU FUCKING ASSHAT. I got really mad. Still, fuck that guy.9 -
Imagine if a structural engineer whose bridge has collapsed and killed several people calls it a feature.
Imagine if that structural engineer made a mistake in the tensile strength of this or that type of bolt and shoved it under the rug as "won't fix".
Imagine that it's you who's relying on that bridge to commute every day. Would you use it, knowing that its QA might not have been very rigorous and could fail at any point in time?
Seriously, you developers have all kinds of fancy stuff like Continuous Integration, Agile development, pipelines, unit testing and some more buzzwords. So why is it that the bridges don't collapse, yet new critical security vulnerabilities caused by bad design, unfixed bugs etc appear every day?
Your actions have consequences. Maybe not for yourself but likely it will have on someone else who's relying on your software. And good QA instead of that whole stupid "move fast and break things" is imperative.
Software developers call themselves the same engineers as the structural engineer and the electrical engineer whose mistakes can kill people. I can't help but be utterly disappointed with the status quo in software development. Don't you carry the title of the engineer with pride? The pride that comes from the responsibility that your application creates?
I wish I'd taken the blue pill. I didn't want to know that software "engineering" was this bad, this insanity-inducing.
But more than anything, it surprises me that the world that relies so much on software hasn't collapsed in some incredible way yet, despite the quality of what's driving it.43 -
Well, here's the OS rant I promised. Also apologies for no blog posts the past few weeks, working on one but I want to have all the information correct and time isn't my best friend right now :/
Anyways, let's talk about operating systems. They serve a purpose which is the goal which the user has.
So, as everyone says (or, loads of people), every system is good for a purpose and you can't call the mainstream systems shit because they all have their use.
Last part is true (that they all have their use) but defining a good system is up to an individual. So, a system which I'd be able to call good, had at least the following 'features':
- it gives the user freedom. If someone just wants to use it for emailing and webbrowsing, fair enough. If someone wants to produce music on it, fair enough. If someone wants to rebuild the entire system to suit their needs, fair enough. If someone wants to check the source code to see what's actually running on their hardware, fair enough. It should be up to the user to decide what they want to/can do and not up to the maker of that system.
- it tries it's best to keep the security/privacy of its users protected. Meaning, by default, no calling home, no integrating users within mass surveillance programs and no unnecessary data collection.
- Open. Especially in an age of mass surveillance, it's very important that one has the option to check the underlying code for vulnerabilities/backdoors. Can everyone do that, nope. But that doesn't mean that the option shouldn't be there because it's also about transparency so you don't HAVE to trust a software vendor on their blue eyes.
- stability. A system should be stable enough for home users to use. For people who like to tweak around? Also, but tweaking *can* lead to instability and crashes, that's not the systems' responsibility.
Especially the security and privacy AND open parts are why I wouldn't ever voluntarily (if my job would depend on it, sure, I kinda need money to stay alive so I'll take that) use windows or macos. Sure, apple seems to care about user privacy way more than other vendors but as long as nobody can verify that through source code, no offense, I won't believe a thing they say about that because no one can technically verify it anyways.
Some people have told me that Linux is hard to use for new/(highly) a-technical people but looking at my own family and friends who adapted fast as hell and don't want to go back to windows now (and mac, for that matter), I highly doubt that. Sure, they'll have to learn something new. But that was also the case when they started to use any other system for the first time. Possibly try a different distro if one doesn't fit?
Problems - sometimes hard to solve on Linux, no doubt about that. But, at least its open. Meaning that someone can dive in as deep as possible/necessary to solve the problem. That's something which is very difficult with closed systems.
The best example in this case for me (don't remember how I did it by the way) was when I mounted a network drive at boot on windows and Linux (two systems using the same webDav drive). I changed the authentication and both systems weren't in for booting anymore. Hours of searching how to unfuck this on windows - I ended up reinstalling it because I just couldn't find a solution.
On linux, i found some article quite quickly telling to remove the entry for the webdav thingy from fstab. Booted into a root recovery shell, chrooted to the harddrive, removed the entry in fstab and rebooted. BAM. Everything worked again.
So yeah, that's my view on this, I guess ;P30 -
*knock knock*
SIR do you have a moment to talk about our lord and savior the WINDOWS UPDATE?
"uhm no sorry I'm busy"
*sees a bulldozer in the background*
"what the .."
SIR just let him in your heart and feel his security patches drive your vulnerabilities away!!
"but the rendering hasn't finished ye.."
TOO LATE SIR, green light fellas let's do this
*bulldozer destroys my house and i wake up, sweating*
*hugs laptop*
"Oooh Ubuntu my baby I've missed you soo much!"
*wayland crashes*2 -
"secure" messaging apps which aren't open source.
Isn't it common sense that, when you can't check an app for anything because it's closed source (backdoors, vulnerabilities etc), you technically can't be sure whether it's actually secure or not?
And no, I'm not going to trust an app dev on his/her blue fucking eyes on this one.28 -
I just got handed a legacy php web project... Full of vulnerabilities... And it's using only mysql_ functions... Not only it's not OOP, there is not even a single class...
How good it's coded: User profiles are created manually by the frontend dev as htmls, and then the past php dev implemented them as links etc in the current page.
This is how I feel: 5
5 -
Was literally about to release a test version of the url shortener when I did some more testing and found some security vulnerabilities, let's fix those first tomorrow 😅12
-
My boss is still forcing us to support IE11. Recently, we started having even more bugs with one of our vendors on IE. We filed bug reports with the vendor to fix it, and they came back with "no. Why would we fix anything for IE11? Not even Microsoft is fixing anything for IE11." Boss's answer: well, let's make a separate component for IE11. Probably using flash and/or silverlight. We asked about redirecting IE traffic to Edge, he said that's "the nuclear option." So, doing the thing that Microsoft suggests, that involves not much work at all is "the nuclear option"; ignoring industry standards and recommendations, introducing well known security vulnerabilities, losing money, and trying to circumvent the vendor that serves out our major product, however, is totally reasonable. Our IE traffic is less than 3% of our users at this point.22
-
My friend called me and told me "My I.T teacher said I.E is the safest browser.". I began sighing then he continued on "He said Firefox, the Chromium project and other open source browsers are all unsafe. Because Open Source = More Vulnerabilities".
I only replied with this sentence.
"tell your teacher to eat a dick."18 -
The last year my school installed MagicBoards (whiteboard with beamer that responses to touch) in every class room and called itself "ready for the future of media". What they also got is A FUCKING LOW SPEC SERVER RUNNING DEBIAN 6 W/O ANY UPDATES SINCE 2010 WHICH IS DYING CONSTANTLY.
As I'm a nice person I asked the 65 y/o technician (who is also my physics teacher) whether I could help updating this piece of shit.
Teacher: "Naahh, we don't have root access to the server and also we'll get a new company maintaining our servers in two years. And even if we would have the root access, we can't give that to a student."
My head: "Two. Years. TWO YEARS?! ARE YOU FUCKING KIDDING ME YOU RETARDED PIECE OF SHIT?! YOU'RE TELLING ME YOU DON'T HAVE TO INSTALL UPDATES EVEN THOUGH YOU CREATE AN SSH USER FOR EVERY FUCKING STUDENT SO THEY CAN LOGIN USING THEIR BIRTH DATE?! DID YOU EVER HEAR ABOUT SECURITY VULNERABILITIES IN YOUR LITTLE MISERABLE LIFE OR SOUNDS 'CVE-2016-5195' LIKE RANDOM LETTERS AND NUMBERS TO YOU?! BECAUSE - FUNFACT - THERE ARE TEN STUDENTS WHO ARE IN THE SUDO GROUP IF YOU EVEN KNOW WHAT THAT IS!"
Me (because I want to keep my good grades): "Yes, that sounds alright."13 -
!Story
The day I became the 400 pound Chinese hacker 4chan.
I built this front-end solution for a client (but behind a back end login), and we get on the line with some fancy European team who will handle penetration testing for the client as we are nearing dev completion.
They seem... pretty confident in themselves, and pretty disrespectful to the LAMP environment, and make the client worry even though it's behind a login the project is still vulnerable. No idea why the client hired an uppity .NET house to test a LAMP app. I don't even bother asking these questions anymore...
And worse, they insist we allow them to scrape for vulnerabilities BEHIND the server side login. As though a user was already compromised.
So, I know I want to fuck with them. and I sit around and smoke some weed and just let this issue marinate around in my crazy ass brain for a bit. Trying to think of a way I can obfuscate all this localStorage and what it's doing... And then, inspiration strikes.
I know this library for compressing JSON. I only use it when localStorage space gets tight, and this project was only storing a few k to localStorage... so compression was unnecessary, but what the hell. Problem: it would be obvious from exposed source that it was being called.
After a little more thought, I decide to override the addslashes and stripslashes functions and to do the compression/decompression from within those overrides.
I then minify the whole thing and stash it in the minified jquery file.
So, what LOOKS from exposed client side code to be a simple addslashes ends up compressing the JSON before putting it in localStorage. And what LOOKS like a stripslashes decompresses.
Now, the compression does some bit math that frankly is over my head, but the practical result is if you output the data compressed, it looks like mandarin and random characters. As a result, everything that can be seen in dev tools looks like the image.
So we GIVE the penetration team login credentials... they log in and start trying to crack it.
I sit and wait. Grinning as fuck.
Not even an hour goes by and they call an emergency meeting. I can barely contain laughter.
We get my PM and me and then several guys from their team on the line. They share screen and show the dev tools.
"We think you may have been compromised by a Chinese hacker!"
I mute and then die my ass off. Holy shit this is maybe the best thing I've ever done.
My PM, who has seen me use the JSON compression technique before and knows exactly whats up starts telling them about it so they don't freak out. And finally I unmute and manage a, "Guys... I'm standing right here." between gasped laughter.
If only it was more common to use video in these calls because I WISH I could have seen their faces.
Anyway, they calmed their attitude down, we told them how to decompress the localStorage, and then they still didn't find jack shit because i'm a fucking badass and even after we gave them keys to the login and gave them keys to my secret localStorage it only led to AWS Cognito protected async calls.
Anyway, that's the story of how I became a "Chinese hacker" and made a room full of penetration testers look like morons with a (reasonably) simple JS trick. 9
9 -
I hope I'll be able to release the new/refreshed version of the security/privacy blog today.
Feel free to test stuff out and report back when it breaks!
Also, feel free to pentest it. The only thing I ask is to, if you find any vulnerabilities, report them instead of passing them to malicious people/abusing them.
And yes, post sorting will be fixed ;)23 -
Long story short, I'm unofficially the hacker at our office... Story time!
So I was hired three months ago to work for my current company, and after the three weeks of training I got assigned a project with an architect (who only works on the project very occasionally). I was tasked with revamping and implementing new features for an existing API, some of the code dated back to 2013. (important, keep this in mind)
So at one point I was testing the existing endpoints, because part of the project was automating tests using postman, and I saw something sketchy. So very sketchy. The method I was looking at took a POJO as an argument, extracted the ID of the user from it, looked the user up, and then updated the info of the looked up user with the POJO. So I tried sending a JSON with the info of my user, but the ID of another user. And voila, I overwrote his data.
Once I reported this (which took a while to be taken seriously because I was so new) I found out that this might be useful for sysadmins to have, so it wasn't completely horrible. However, the endpoint required no Auth to use. An anonymous curl request could overwrite any users data.
As this mess unfolded and we notified the higher ups, another architect jumped in to fix the mess and we found that you could also fetch the data of any user by knowing his ID, and overwrite his credit/debit cards. And well, the ID of the users were alphanumerical strings, which I thought would make it harder to abuse, but then realized all the IDs were sequentially generated... Again, these endpoints required no authentication.
So anyways. Panic ensued, systems people at HQ had to work that weekend, two hot fixes had to be delivered, and now they think I'm a hacker... I did go on to discover some other vulnerabilities, but nothing major.
It still amsues me they think I'm a hacker 😂😂 when I know about as much about hacking as the next guy at the office, but anyways, makes for a good story and I laugh every time I hear them call me a hacker. The whole thing was pretty amusing, they supposedly have security audits and QA, but for five years, these massive security holes went undetected... And our client is a massive company in my country... So, let's hope no one found it before I did.6 -
10 years ago, I found a vulnerability in the connection between an insurer I was working for, and the network of databases of municipalities. I was only a hacker in so far as kids who watched Hak5 are considered hackers, so I always carried this laptop with a fake access point, package sniffer, wep crack, sslstrip, etc with me.
The vulnerabilities allowed me to register a new identity, for which I requested a passport.
Walking up to the town hall desk with two passports with different names, both mine, was pretty cool.
I did not do anything malicious, and was hired to fix the issues (wep encryption on insurers trusted wifi, and municipality postgres gave write access to all third parties)
For a few days I was the coolest kid in school though!2 -
Jokes aside, this got me thinking html is most used and most successful hacking tool out there.
99.99% of the time it's far easier to socially engineer and phish for existing credentials that scan networks, sniff ports and look for vulnerable versions of software, new vulnerabilities etc.
We (people) are ad always will be a zero day exploit. 7
7 -
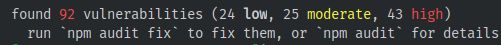
$ npm audit
> found 19 vulnerabilities (10 low, 5 moderate, 3 high, 1 critical)
$ npm audit fix
> fixed 0 of 19 vulnerabilities in 11987 scanned packages
> (use `npm audit fix --force` to install breaking changes; or do it by hand)
$ npm audit fix --force
> npm WARN using --force I sure hope you know what you are doing.
Me too, buddy. Me too.1 -
One Thursday noon,
operation manager: (looking at mobile)what the.....something is wrong i am getting bunch of emails about orders getting confirmed.
Colleague dev: (checks the main email where it gets all email sent/received) holy shit all of our clients getting confirmation email for orders which were already cancelled/incomplete.
Me: imediately contacting bluehost support, asking them to down the server so just that we can stopp it, 600+ emails were already sent and people keep getting it.
*calls head of IT* telling the situation because he's not in the office atm.
CEO: wtf is happening with my business, is it a hacker?
*so we have a intrusion somebody messed the site with a script or something*
All of us(dev) sits on the code finding the vulnerabilities , trying to track the issue that how somebody was able to do that.
*After an hour*
So we have gone through almost easch function written in the code which could possibly cause that but unable to find anything which could break it.
Head asking op when did you started getting it actually?
Op: right after 12 pm.
*an other hour passes*
Head: (checking the logs) so right after the last commit, site got updated too?. And....and.....wtf what da hell who wrote this shit in last commit?
* this fuckin query is missing damn where clause* 🤬
Me: me 😰
*long pause, everyone looking at me and i couldn't look at anyone*
The shame and me that how can i do that.
Head: so its you not any intrudor 😡
Further investigating, what the holy mother of #_/&;=568 why cronjob doesn't check how old the order is. Why why why.
(So basically this happened, because of that query all cancelled/incomplete orders got updated damage done already, helping it the cronjob running on all of them sending clients email and with that function some other values got updated too, inshort the whole db is fucked up.)
and now they know who did it as well.
*Head after some time cooling down, asked me the solution for the mess i create*
Me: i took backup just couple of days before i can restore that with a script and can do manual stuff for the recent 2 days. ( operation manager was already calling people and apologising from our side )
Head: okay do it now.
Me: *in panic* wrote a script to restore the records ( checking what i wrote 100000000 times now ), ran...tested...all working...restored the data.
after that wrote an apology email, because of me staff had to work alot and it becomes so hectic just because of me.
* at the end of the day CEO, head, staff accepted apology and asked me to be careful next time, so it actually teached me a lesson and i always always try to be more careful now especially with quries. People are really good here so that's how it goes* 🙂2 -
The only hacked sites I had to fix were running on ... [prepare your stomach] ... Joomla.
I'm not sure if there is even one single solid developer for Joomla. This shit piece has more vulnerabilities than a crack hobo infested with pest-ebola-hyperAIDS.
The sites were full of hidden viagra and pr0n ads and links so the crawlers would list them.
Luckily for me, I was able to pursuade the clients in all 3 cases to build a new site from scratch on a different CMS.2 -
First company I worked for, built around 40 websites with Drupal 7...in only a year (don't know if it's a lot for today's standards, but I was one guy doing everything). Of course I didn't have the time to keep updating everything and I continually insisted to the boss that we need more people if we are going to expand. Of course he kept telling me to keep working harder and that I "got this". Well, after a year a couple of websites got defaced, you know the usual stuff if you've been around for some time. Felt pretty bad at the time, it was a similar feeling to having your car stolen or something.
Anyways, fast forward about 2 years, started working on another company, and well...this one was on another level. They had a total of around 40 websites, with about 10 of them being Joomla 1.5 installations (Dear Lord have mercy on my soul(the security vulnerabilities from these websites only, were greater than Spiderman's responsibilities)) and the others where WordPress websites, all that ON A SINGLE VPS, I mean, come on... Websites being defaced on the daily, pharma-hacks everywhere, server exploding from malware queing about 90k of spam emails on the outbox, server downtime for maintenance happening almost weekly, hosting company mailing me on the daily about the next malware detection adventure etc. Other than that, the guy that I was replacing, was not giving a single fuck. He was like, "dude it's all good here, everything works just fine and all you have to do is keep the clients happy and shit". Sometimes, I hate myself for being too caring and responsible back then.
I'm still having nightmares of that place. Both that office and that VPS. -
I think we're going two sides:
For one, more and more technology is being developed/engineered which is even more and more and more intrusive as for personal privacy, I'm genuinely worried how this'll go as privacy isn't just a about not exposing certain things like passwords/bank account details and so on, it's also about being an individual who has their own thoughts, opinions and so on. If we keep taking that away more and more often, society will change and go towards the Orwell scenario (we're on our way there right now). We can change this as software/design/server engineers but that's up to us and I sadly don't see that happening quickly, also due to the 'nothing to hide' bullshit.
Second one is that were going more and more towards open source.
This is a good thing as this:
- gives freedom to devs around the world to improve software and/or modify it to suit their needs.
- gives people the opportunity to look through the source code of softwares in order to verify it as for backdoors and find security vulnerabilities which otherwise can remain hidden for the general public while spying agencies have way more resources to go vulnerability hunting.
For the people who think this isn't a good idea (even more open source), without it we'd be completely fucked as for moving forward/security/privacy. (I can give examples if wanted).3 -
The fuck did I do wrong?
So I had 11 vulnerabilities 1 high.
I just npm audit fix
Now it’s 44 vulnerabilities 13
13 -
Really cool. Tesla gave two hackers that found a vulnerability in the Model 3 free cars as a reward. More companies should do that, instead of getting all pissy. I would hope a company wants to know what their vulnerabilities are so that they can avoid embarrassment and the loss of money.2
-
The company I work for is currently maintaining some websites under an old (>1.5 years) version of Drupal, which has some well known vulnerabilities.
Yesterday we've found out somebody used them to inject php code into every single .php file on the machine. We've been discussing for hours about how to recover data, upgrade stuff, and maybe switch to something else. I've said jokingly "or we could put a find command in the crontab to sed away the php line they've injected!". Guess what we're doing now on our production servers?7 -
TLDR: Small family owned finance business woes as the “you-do-everything-now” network/sysadmin intern
Friday my boss, who is currently traveling in Vegas (hmmm), sends me an email asking me to punch a hole in our firewall so he can access our locally hosted Jira server that we use for time logging/task management.
Because of our lack of proper documentation I have to refer to my half completed network map and rely on some acrobatic cable tracing to discover that we use a SonicWall physical firewall. I then realize asking around that I don’t have access to the management interface because no one knows the password.
Using some lucky guesses and documentation I discover on a file share from four years ago, I piece together the username and password to log in only to discover that the enterprise support subscription is two years expired. The pretty and useful interface that I’m expecting has been deactivated and instead of a nice overview of firewall access rules the only thing I can access is an arcane table of network rules using abbreviated notation and five year old custom made objects representing our internal network.
An hour and a half later I have a solid understanding of SonicWallOS, its firewall rules, and our particular configuration and I’m able to direct external traffic from the right port to our internal server running Jira. I even configure a HIDS on the Jira server and throw up an iptables firewall quickly since the machine is now connected to the outside world.
After seeing how many access rules our firewall has, as a precaution I decide to run a quick nmap scan to see what our network looks like to an attacker.
The output doesn’t stop scrolling for a minute. Final count we have 38 ports wide open with a GOLDMINE of information from every web, DNS, and public server flooding my terminal. Our local domain controller has ports directly connected to the Internet. Several un-updated Windows Server 2008 machines with confidential business information have IIS 7.0 running connected directly to the internet (versions with confirmed remote code execution vulnerabilities). I’ve got my work cut out for me.
It looks like someone’s idea of allowing remote access to the office at some point was “port forward everything” instead of setting up a VPN. I learn the owners close personal friend did all their IT until 4 years ago, when the professional documentation stops. He retired and they’ve only invested in low cost students (like me!) to fill the gap. Some kid who port forwarded his home router for League at some point was like “let’s do that with production servers!”
At this point my boss emails me to see what I’ve done. I spit him back a link to use our Jira server. He sends me a reply “You haven’t logged any work in Jira, what have you been doing?”
Facepalm.4 -
Watch out for these fucking bug bounty idiots.
Some time back I got an email from one shortly after making a website live. Didn't find anything major and just ran a simple tool that can suggest security improvements simply loading the landing page for the site.
Might be useful for some people but not so much for me.
It's the same kind of security tool you can search for, run it and it mostly just checks things like HTTP headers. A harmless surface test. Was nice, polite and didn't demand anything but linked to their profile where you can give them some rep on a system that gamifies security bug hunting.
It's rendering services without being asked like when someone washes your windscreen while stopped at traffic but no demands and no real harm done. Spammed.
I had another one recently though that was a total disgrace.
"I'm a web security Analyst. My Job is to do penetration testing in websites to make them secure."
"While testing your site I found some critical vulnerabilities (bugs) in your site which need to be mitigated."
"If you have a bug bounty program, kindly let me know where I should report those issues."
"Waiting for response."
It immediately stands out that this person is asking for pay before disclosing vulnerabilities but this ends up being stupid on so many other levels.
The second thing that stands out is that he says he's doing a penetration test. This is illegal in most major countries. Even attempting to penetrate a system without consent is illegal.
In many cases if it's trivial or safe no harm no foul but in this case I take a look at what he's sending and he's really trying to hack the site. Sending all kinds of junk data and sending things to try to inject that if they did get through could cause damage or provide sensitive data such as trying SQL injects to get user data.
It doesn't matter the intent it's breaking criminal law and when there's the potential for damages that's serious.
It cannot be understated how unprofessional this is. Irrespective of intent, being a self proclaimed "whitehat" or "ethical hacker" if they test this on a site and some of the commands they sent my way had worked then that would have been a data breach.
These weren't commands to see if something was possible, they were commands to extract data. If some random person from Pakistan extracts sensitive data then that's a breach that has to be reported and disclosed to users with the potential for fines and other consequences.
The sad thing is looking at the logs he's doing it all manually. Copying and pasting extremely specific snippets into all the input boxes of hacked with nothing to do with the stack in use. He can't get that many hits that way.4 -
> IHateForALiving: I have added markdown on the client! Now the sys admin can use markdown and it's going to be rendered as HTML
> Team leader: ok, I've seen you also included some pics of the tests you made. It's nice, there's no XSS vulnerabilities, now I want you to make sure you didn't introduce any SQL injection too. Post the results of the tests in the tickets, for everybody to see.
I've been trying to extract from him for 15 minutes how sending a text through a markdown renderer on the client is supposed to create a SQL injection on the server, I've been trying to extract from him how showing all of this to the world would improve our reputation.
I miserably failed, I don't know how the fuck am I supposed to test this thing and if I a colleague wasted time to make sure some client-side rendering didn't create a SQL injection I'd make sure to point and laugh at them every time they open their mouth.9 -
My team manager showed me a web application of a new client and asked me if I can find vulnerabilities in it to push for a better product contract. She showed me the system architecture and asked me if I could try finding something from their login page. I politely refused since we don't have written permission to conduct a security audit (it's also a ministry website). She was pretty disappointed and idk if I'm doing the right thing not helping the company (I'm an intern but still). I'm sure I can scan in stealth but I don't think it's ethical on a corporate level. Thoughts?11
-
I need advice from my coding elders:
A bit of background:
So I'm a highschooler and I have made a program for my school called Passport. It's being implemented as we speak.
Take a look:
https://github.com/poster983/...
It is basically a program that helps to manage and distribute digital Library passes. (We used to go through stacks of paper passes).
It was sorta my first major project, so it is probably filled with bugs and other security vulnerabilities. Just FYI.
_______
So a guy approached me tonight and was acting very interested in what I did. (it's literally a fancy database). He wanted my to unopen-source it and sell it to a company. (Probably his or a friend of him). I politely declined because I feel this program is
1. Not up to my standards; so if I was to sell it, I would rewrite it is something more modern like node, or Python.
2. I love open source.
3. A way for my to give back to my school and maybe help other schools.
After hearing that, he started calling opensourse a failure, and he said that I will one day be wise and write code for money (which I know I will, just I want to sell GOOD code).
My question is, how do I deal with people who want my to dich the opensourse model in the future?6 -
I am amazed how specific everyone is being about security vulnerabilities at their employers. Hopefully no one social engineers what company you work at.2
-
Okay, here we go...
I need a new Programming language.
Coming from a Python background, so go easy on me. x.x
C# can do what I need, but it's quite complex for me. I'd rather something simplier is possible.
Brief summery:
So, I've come to realize that I wont be able to make my Python game(ExitCode) as powerful and fancy as I'd like. And I decided that I should just start from scratch before I go any farther. (Though, I might go ahead and stabilize the current versions on GitHub)
Here's what I need:
Powerful UI support;
* I am re-creating an OS as my game. I will need to drag and position windows and icons in-game, as you would in a real OS.
* Needs to support Ads, Animations, Images, Videos, Sound, and any other media I might need?
* Preferably can render HTML & CSS (Though, this is just a preference)
Support for reading JSON and/or XML files SAFELY (XML had major vulnerabilities in Python)
Supports Windows, but I would prefer cross-platform-ability
Easy to compile
I am not really looking for a game ENGINE. I am looking for a language to create a game in from scratch, that has powerful UI libraries.
In the end, the game will be Free, and Open Source. (Always!~)undefined yeah python was a bad idea shouldn't have trusted a snake let the personal biases roll in come at me bro we will take over the world! maybe.. thats great but can it run crisis? programming languages47 -
TL; DR: Bringing up quantum computing is going to be the next catchall for everything and I'm already fucking sick of it.
Actual convo i had:
"You should really secure your AWS instance."
"Isnt my SSH key alone a good enough barrier?"
"There are hundreds of thousands of incidents where people either get hacked or commit it to github."
"Well i wont"
"Just start using IP/CIDR based filtering, or i will take your instance down."
"But SSH keys are going to be useless in a couple years due to QUANTUM FUCKING COMPUTING, so why wouldnt IP spoofing get even better?"
"Listen motherfucker, i may actually kill you, because today i dont have time for this. The whole point of IP-based security is that you cant look on Shodan for machines with open SSH ports. You want to talk about quantum computing??!! Lets fucking roll motherfucker. I dont think it will be in the next thousand years that we will even come close to fault-tolerant quantum computing.
And even if it did, there have been vulnerabilities in SSH before. How often do you update your instance? I can see the uptime is 395 days, so probably not fucking often! I bet you "dont have anything important anyways" on there! No stored passwords, no stored keys, no nothing, right (she absolutely did)? If you actually think I'm going to back down on this when i sit in the same room as the dude with the root keys to our account, you can kindly take your keyboard and shove it up your ass.
Christ, I bet that the reason you like quantum computing so much is because then you'll be able to get your deepfakes of miley cyrus easier you perv."8 -
`npx create-react-app blah`
`cdls blah && npm audit`
63 vulnerabilities.
good fucking job.
To be fair, they're all minor, but they're all *exactly* the same, caused by the same freaking package. Update your dependencies already!
------
`npm i --save formik && npm audit`
68 vulnerabilities, three of them critical.
ugh.6 -
No other language can do something as fucky as javascript.
"7 high severity vulnerabilities"
$> npm audit fix --force
"13 vulnerabilities (11 high, 2 critical)"
How is this fixed?!
It will be a great day when JS finally prolapses under the weight of its own hubris.11 -
After seeing this "old" picture I want to let know at the guyz who are in love with AMD that before Ryzen(s) I was able to cook my fuckin' breakfast's eggs on their fuckin' CPUs.
Big mistakes brings to great solutions and shut up the fuck up AMD, probably your core code is full of vulnerabilities but no one cares about your ultra threads architecture. 22
22 -
I was working in a manufacturing facility where I had hundreds of industrial computers and printers that were between 0 and 20 years old. They were running on their own clean network so that someone has to be in the manufacturing network to access them. The boss announced that the executives will be pushing a “zero trust” security model because they need IoT devices. I told him “A computer running Windows 98 can’t be on the same VLAN as office computers. We can’t harden most of the systems or patch the vulnerabilities. We also can’t reprogram all of the devices to communicate using TLS or encrypt communications.“ Executives got offended that I would even question the decision and be so vocal about it. They hired a team to remove the network hardware and told me that I was overreacting. All of our system support was contracted to India so I was going to be the on-site support person.
They moved all the manufacturing devices to the office network. Then the attacks started. Printers dumped thousands of pages of memes. Ransomware shut down manufacturing computers. Our central database had someone change a serial number for a product to “hello world” and that device got shipped to a customer. SharePoint was attacked in many many ways. VNC servers were running on most computers and occasionally I would see someone remotely poking around and I knew it wasn’t from our team because we were all there.
I bought a case of cheap consumer routers and used them in manufacturing cells to block port traffic. I used Kali on an old computer to scan and patch network vulnerabilities daily.
The worst part was executives didn’t “believe” that there were security incidents. You don’t believe in what you don’t understand right?
After 8 months of responding to security incident after security incident I quit to avoid burning out. This is a company that manufactures and sells devices to big companies like apple and google to install in their network. This isn’t an insignificant company. Security negligence on a level I get angry thinking about.7 -
There’s no better feeling then doing a full server rebuild, modifying several projects heavily to be portable and keep working under new infrastructure and loosing access to dependent systems.
Migrating everything across, firing up Apache.... and BAM the fucker just works and ssl labs gives it an A (it was a giant F with multiple vulnerabilities yesterday on the old server)7 -
I can't stop myself from thinking like a computer when I'm sick.
The OS that runs my body is kinda fucked up right now. It was very vulnerable and now it got infected by viral executables sent out by an agent which happens to be on same work network that I'm connected to. Well, it executed and populated feelings of infatuation and crush in my heart drive. ( pun intended )
As a precaution, I patched the vulnerabilities by masking response of my Emotions API.
To further secure my system, I'll be executing memory intensive tasks that will also put my hardware to it's limits. According to my estimates, this will stall further execution of this infection and eventually kill them while rewarding me with upgraded hardware.4 -
!rant
Reddit comment on a thread about Joomla! sites being vulnerable to SQL-injections:
"Joomla sites are so infested they became sentient.
Joomla sites needs no webmaster, some one else will administer it for you.
Joomla sites have very good SEO, specially in "v1agra c1alis p3nis size"
Traffic count with Joomla is high, all the bots breaking all the vulnerabilities count for somethin'."
😂 Pure gold.1 -
rant & question
Last year I had to collaborate to a project written by an old man; let's call him Bob. Bob started working in the punch cards era, he worked as a sysadmin for ages and now he is being "recycled" as a web developer. He will retire in 2 years.
The boss (that is not a programmer) loves Bob and trusts him on everything he says.
Here my problems with Bob and his code:
- he refuses learning git (or any other kind of version control system);
- he knows only procedural PHP (not OO);
- he mixes the presentation layer with business logic;
- he writes layout using tables;
- he uses deprecated HTML tags;
- he uses a random indentation;
- most of the code is vulnerable to SQL injection;
- and, of course, there are no tests.
- Ah, yes, he develops directly on the server, through a SSH connection, using vi without syntax highlighting.
In the beginning I tried to be nice, pointing out just the vulnerabilities and insisting on using git, but he ignored all my suggestions.
So, since I would have managed the production server, I decided to cheat: I completely rewrote the whole application, keeping the same UI, and I said the boss that I created a little fork in order to adapt the code to our infrastructure. He doesn't imagine that the 95% of the code is completely different from the original.
Now it's time to do some changes and another colleague is helping. She noticed what I did and said that I've been disrespectful in throwing away the old man clusterfuck, because in any case the code was working. Moreover he will retire in 2 years and I shouldn't force him to learn new things [tbh, he missed at least last 15 years of web development].
What would you have done in my place?10 -
As usual a rather clickbait title, because only the chrome extensions (as always) seem to be vulnerable:
"Warning – 3 Popular VPN Services Are Leaking Your IP Address"
"Researchers found critical vulnerabilities in three popular VPN services that could leak users' real IP addresses and other sensitive data."
"VPN Mentor revealed that three popular VPN service providers—HotSpot Shield, PureVPN, and Zenmate"
"PureVPN is the same company who lied to have a 'no log' policy, but a few months ago helped the FBI with logs that lead to the arrest of a Massachusetts man in a cyberstalking case."
"Hijack all traffic (CVE-2018-7879) "
"DNS leak (CVE-2018-7878)"
"Real IP Address leak (CVE-2018-7880)" 7
7 -
I have quite a few of these so I'm doing a series.
(2 of 3) Flexi Lexi
A backend developer was tired of building data for the templates. So he created a macro/filter for our in house template lexer. This filter allowed the web designers (didn't really call them frond end devs yet back then) could just at an SQL statement in the templates.
The macro had no safe argument parsing and the designers knew basic SQL but did not know about SQL Injection and used string concatination to insert all kinds of user and request data in the queries.
Two months after this novel feature was introduced we had SQL injections all over the place when some piece of input was missing but worse the whole product was riddled with SQLi vulnerabilities.2 -
+++ Microsoft Genuine Snake Oil: The purest snake oil on the market now contains even less remote code execution vulnerabilities! +++
https://zdnet.com/article/... -
"One misstep from developers at Starbucks left exposed an API key that could be used by an attacker to access internal systems and manipulate the list of authorized users," according to the report of Bleeping Computer.
Vulnerability hunter Vinoth Kumar reported and later Starbucks responded it as "significant information disclosure" and qualified for a bug bounty. Along with identifying the GitHub repository and specifying the file hosting the API key, Kumar also provided proof-of-concept (PoC) code demonstrating what an attacker could do with the key. Apart from listing systems and users, adversaries could also take control of the Amazon Web Services (AWS) account, execute commands on systems and add or remove users with access to the internal systems.
The company paid Kumar a $4,000 bounty for the disclosure, which is the maximum reward for critical vulnerabilities.6 -
I'd never do anything "risky" in a prod environment if I considered it so at the time, but in retrospect there's *lots* of things considered risky now (both from a security and good practice viewpoint) that were standard practice not long ago:
- Not using any form of version control
- No tests (including no unit tests)
- Not considering XSS vulnerabilities
- Completely ignoring CSRF vulnerabilities
- Storing passwords as unsalted MD5 hashes (heck that was considered very *secure* in the days of plaintext password storage.)
...etc. I'm guilty of all of those previously. I daresay in the future there will be yet more things that may be standard practice now, but become taboos we look back on with similar disdain.1 -
When i was younger, lesser experienced and more naive than now; i got away with a lot of things. By lot of things i mean security flaws in my applications and overall architecture. I realise now i could've so easily been pawned.
Not that i claim to be totally secure even now, or would ever. It is a process, slow and painful one - Learning.
What i wish to point out is the role of favorable probability (non believers would call it luck). Security is so much about it. You get away with so many things for so long. And bang one day the roll of dice is unfavorable. On such rare occasions, just look back and wonder - damn i should've been breached long ago.rant hindsight security fail looking back security luck vulnerabilities food for thought musings naive probability2 -
I used to think my first relationship was awful. I went through so much and rather it served as a trigger for my childhood trauma as well.
Little did I know that it would be the best the thing that could happen to me. I grew so much and every next woman I met, I realised how fucking amazing my ex is. God I miss her terribly.
But what happened with my recent fuck up, I am devastated. This toxic women brought out the worst in me. I have never been so hateful against myself or anyone else in the world.
I was love bombed and walked into a trap. I quit as soon as I realised what it was.
My values were comprised. My integrity was put to test. My trust was intentionally broken. During the initial days, she tactically identified my vulnerabilities and insecurities. Then used to sadistically trigger me as often as she can and sit there and watch me in suffer pain.
It led me to self harm and being suicidal.
I am so badly wounded that even after few weeks, I am still discovering all the wounds. It will surely take some time along with external support to build a healing environment for myself and overcome this damage.
I am very angry, terribly hurt, lost and confused. This shit developed a phobia in me. I cannot trust anyone anymore. I constantly live in fear of being hurt (physical, mental, and emotional). I am paranoid of that stalker.
I don't think I'll ever be able to start and build a healthy relationship with anyone. I used to be sooooo fucking strong emotionally and mentally. But now not only my trauma relapsed but I got more issues within me.
I really want to live a free, healthy, happy and a fulfilled life. I don't know when time will heal this but right now, I am in terrible pain and hate myself a lot.7 -
During a design meeting, our boss tells me that Vertx's MySQL drivers don't have prepared statements, and that in the past, he's used a library or his own functions to do all the escaping.
"Are you kidding me? Are you insane?"
I insisted that surely he must be wrong; that no one would release a database library without built in support for query arguments. Escaping things by hand is just asinine and a security risk. You should always use the tools in the database drivers, as new security vulnerabilities in SQL drivers can be found and fixed so long as you keep your dependencies up to date.
He told me escaping wasn't as tricky as I made it out to be, that there were some good libraries for it, and insisted Vertx didn't have any built in support for "prepared statements." He also tried to tell us that prepared statements had performance issues.
He searched specifically for "prepared statements" and I was like, "You know they don't have to be called that. They have different names in different frameworks."
Sure enough, a short search and we discovered a function in the Vertx base database classes to allow SQL queries with parameters. -
I wrote an auth today.
Without frameworks. Without dependencies. Without under-the-hood magic. Without abstract pluggable adaptor modules for the third-party auth library with 63 vulnerabilities and 1252 GitHub issues. Without security vulnerabilities showing up in NPM log. Without dependency of a dependency of a dependency using md5 and Math.random() under the hood for historical reasons, and now we're fucked, because this is the only lib for our framework, and we have no time to write our own replacement. Without all that shit.
Rock-solid, on top of scrypt. Stateless and efficient.
It felt amazing.9 -
Learning Angular, starting with a hello world example:
$ ng new wtf
added 1180 packages from 1294 contributors and audited 21849 packages in 18.753s
found 13 vulnerabilities (9 low, 4 high)
Oh, great! Broken from the get-to! But wait, there's more joy!
$ vimdiff wtf/node_modules/is-odd/node_modules/is-number/index.js wtf/node_modules/is-number/index.js
Fresh project, is-odd requires is-number, the project itself requires is-number. And is-number is there twice in two different versions. The notion of a number must have changed drastically in the last couple of years!
Seriously? Angular doesn't even give me the chance to fuck up the dependencies on my own!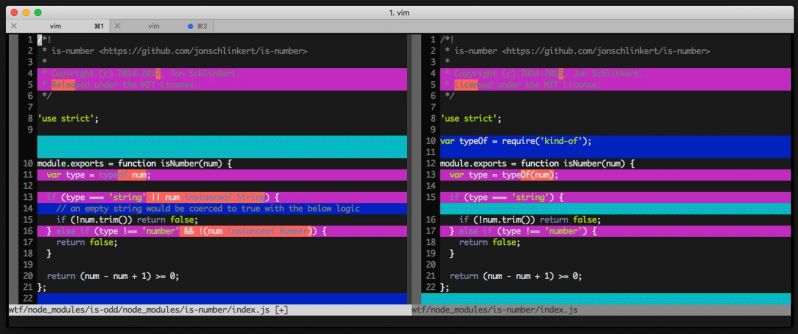 7
7 -
So after my hosting my first project and announcing it on devrant, the users pointed out the many security faults and places where the code can be exploited ( thank you so much ). So I started my research on security ( im 99% self-taught ). The first thing I landed across is the code vulnerabilities which the I can fix then the vulnerabilities of the language itself and then binary code to overrun whatever the language it is. Well, the topic gets broader and broader. If I click on a link named xxx vulnerabilities oh god that is a whole new collection of hundeds of wiki like pages. I feel like I'm lost and here I need some real help2
-
In a universe where JavaScript was never invented, the world of programming might look vastly different. Perhaps another programming language would have taken its place, or multiple languages would have coexisted in a more harmonious ecosystem.
Without the challenges posed by JavaScript, web development may have been smoother and more streamlined. Websites could have been faster and more responsive, without the need for complex optimization techniques. There might have been fewer security vulnerabilities to worry about, and the web could have been a safer place for users.
In this utopian world, developers would have had more time to focus on building great user experiences and innovative features, rather than battling with cross-browser compatibility issues and JavaScript quirks. The internet would have been a more accessible and inclusive place, with fewer barriers to entry for those who want to build and create.
Overall, a world without the horrors of JavaScript would have been a world with less frustration and more possibilities.
(Fooling around with ChatGPT)11 -
He he he!
Matching software version and vulnerabilities in NIST then exploiting it is not HACKING !
I wanna find new zero day vulnerabilities that no one ever noticed before!!5 -
These ignorant comments about arch are starting to get on my nerves.
You ranted or asked help about something exclusive to windows and someone pointed out they don't have that problem in arch and now you're annoyed?
Well maybe it's for good.
Next comes a very rough analogy, but imagine if someone posts "hey guys, I did a kg of coke and feeling bad, how do I detox?"
It takes one honest asshole to be like "well what if you didn't do coke?".
Replace the coke with windows.
Windows is a (mostly) closed source operating system owned by a for profit company with a very shady legal and ethical history.
What on earth could possibly go wrong?
Oh you get bsod's?
The system takes hours to update whenever the hell it wants, forces reboot and you can't stop it?
oh you got hacked because it has thousands of vulnerabilities?
wannacry on outdated windows versions paralyzed the uk health system?
oh no one can truly scrutinize it because it's closed source?
yet you wonder why people are assholes when you mention it? This thing is fucking cancer, it's hundreds of steps backwards in terms of human progress.
and one of the causes for its widespread usage are the savage marketing tactics they practiced early on. just google that shit up.
but no, linux users are assholes out to get you.
and how do people react to these honest comments? "let's make a meme out of it. let's deligitimize linux, linux users and devs are a bunch of neckbeards, end of story, watch this video of rms eating skin off his foot on a live conference"
short minded idiots.
I'm not gonna deny the challenges or limitations linux represents for the end user.
It does take time to learn how to use it properly.
Nvidia sometimes works like shit.
Tweaking is almost universally required.
A huge amount of games, or Adobe/Office/X products are not compatible.
The docs can be very obscure sometimes (I for one hate a couple of manpages)
But you get a system that:
* Boots way faster
* Is way more stable
* Is way way way more secure.
* Is accountable, as in, no chance to being forced to get exploited by some evil marketing shit.
In other words, you're fucking free.
You can even create your own version of the system, with total control of it, even profit with it.
I'm not sure the average end user cares about this, but this is a developer forum, so I think in all honesty every developer owes open source OS' (linux, freebsd, etc) major respect for being free and not being corporate horseshit.
Doctors have a hippocratic oath? Well maybe devs should have some form of oath too, some sworn commitment that they will try to improve society.
I do have some sympathy for the people that are forced to use windows, even though they know ideally isn't the ideal moral choice.
As in, their job forces it, or they don't have time or energy to learn an alternative.
At the very least, if you don't know what you're talking about, just stfu and read.
But I don't have one bit of sympathy for the rest.
I didn't even talk about arch itself.
Holy fucking shit, these people that think arch is too complicated.
What in the actual fuck.
I know what the problem is, the arch install instructions aren't copy paste commands.
Or they medium tutorial they found is outdated.
So yeah, the majority of the dev community is either too dumb or has very strong ADD to CAREFULLY and PATIENTLY read through the instructions.
I'll be honest, I wouldn't expect a freshman to follow the arch install guide and not get confused several times.
But this is an intermediate level (not megaexpert like some retards out there imply).
Yet arch is just too much. That's like saying "omg building a small airplane is sooooo complicated". Yeah well it's a fucking aerial vehicle. It's going to be a bit tough. But it's nowhere near as difficult as building a 747.
So because some devs are too dumb and talk shit, they just set the bar too low.
Or "if you try to learn how to build a plane you'll grow an aviator neckbeard". I'll grow a fucking beard if I want too.
I'm so thankful for arch because it has a great compromise between control and ease of install and use.
When I have a fresh install I only get *just* what I fucking need, no extra bullshit, no extra programs I know nothing about or need running on boot time, and that's how I boot way faster that ubuntu (which is way faster than windows already).
Configuring nvidia optimus was a major pain in the ass? Sure was, but I got it work the way I wanted to after some time.
Upgrading is also easy as pie, so really scratching my brain here trying to understand the real difficult of using arch.22 -
1. It's gonna be more and more specialized - to the point where we'll equal or even outdo the medical profession. Even today, you can put 100 techs/devs into a room and not find two doing the same job - that number will rise with the advent of even more new fields, languages and frameworks.
2. As most end users enjoy ignoring all security instructions, software and hardware will be locked down. This will be the disadvantage of developers, makers and hackers equally. The importance of social engineering means the platform development will focus on protecting the users from themselves, locking out legitimate tinkerers in the process.
3. With the EU getting into the backdoor game with eTLS (only 20 years after everyone else realized it's shit), informational security will reach an all-time low as criminals exploit the vulnerabilities that the standard will certainly have.
4. While good old-fashioned police work still applies to the internet, people will accept more and more mass surveillance as the voices of reason will be silenced. Devs will probably hear more and more about implementing these or joining the resistance.
5. We'll see major leaks, both as a consequence of mass-surveillance (done incompetently and thus, insecurely) and as activist retaliation.
6. As the political correctness morons continue invading our communities and projects, productivity will drop. A small group of more assertive devs will form - not pretty or presentable, but they - we - get shit done for the rest.
7. With IT becoming more and more public, pseudo-knowledge, FUD and sales bullshit will take over and, much like we're already seeing it in the financial sector, drown out any attempt of useful education. There will be a new silver-bullet, it will be useless. Like the rest. Stick to brass (as in IDS/IPS, Firewall, AV, Education), less expensive and more effective.
8. With the internet becoming a part of the real life without most people realizing it and/or acting accordingly, security issues will have more financial damages and potentially lethal consequences. We've already seen insulin pumps being hacked remotely and pacemakers' firmware being replaced without proper authentication. This will reach other areas.
9. After marijuana is legalized, dev productivity will either plummet or skyrocket. Or be entirely unaffected. Who cares, I'll roll the next one.
10. There will be new JS frameworks. The world will turn, it will rain.1 -
I'm a fullstack engineer, this period there is literally nothing to do, we are a 1000+ employees company.
I got so bored I toke over the database of our production server two times in a week, exploiting dumb vulnerabilities I discovered out of boredom, of course I reported everything.
The funny thing is that they just don't care, no one took action or is willing to fix it and they actually insulted me because I set a query in sleep for 8 minutes exploiting one of the vulnerabilities.
I work for a great company that hosts (in this very server) most italian citizens informations C: free to take for everyone c:5 -
A new system developed at CSAIL was shown to have stronger security guarantees than Intel's existing approach for preventing so-called "timing attacks" like Meltdown and Spectre, made possible by hardware vulnerabilities.
Image courtesy of Graz University of Technology 6
6 -
Therapy is hardest when you're starting it IMO. I don't like talking about my vulnerabilities with people face to face very much, I get pretty defensive about it. We've agree that I'm suffering from a high level of anxiety which is likely leading to depression and we'll be working on solutions in the coming weeks.
Over the weekend I stopped programming and dedicated myself to more leisure. Went out for a hike (literally) and got a PS4, my first new gaming machine in over two years. Been playing Horizon Zero Dawn.
I'm starting to feel a little bit better. :)1 -
If you call yourself a developer or consider yourself part of the IT world and at the same time complain about software updates (all those dumb windows update rants) then do one of the following:
1- write a multi -million line of code OS that runs on virtually unlimited number of PC configurations and hardware and get the code right the first time with no major bugs, no security vulnerabilities, and a consistently fast and stable performance.
Or...
2- stop calling yourself a dev, or part of the IT world.
If the last 2 options are unreasonable, unachievable, or unfathomable.... Then stop bitching about software updates.21 -
About two weeks ago I had a cyber security competition. I spent a week or so working on a bash script so I didn't have two spend hours and hours on end doing tedious tasks to get points.
So here comes competition day and I have about 12 or so scripts that I predicted to get 60 or so of the 100 points. I open the competition image, grab my scripts, and run my call script (script that calls all the other scripts). Maybe 15 minutes later, the script is done...
ZERO FUCKING POINTS. I double checked all the files that the scripts configured and all of them worked. But NONE the vulnerabilities that my script fixed were vulnerabilities that the scoring report counted. Instead of me taking 20 to 30 minutes on the image it took my and 1:07... doesn't sound like much but the highly competitive people finished in around 1 hour and the people who just didn't give a shit about Linux took 3 hours...
Luckily... I was put onto the highly competitive team after that and it all worked out... I'll hopefully add more to this script before next competition. -
- I do threat intel.
- Oh yeah? Name 4 critical vulnerabilities.
- Fortinet.
- That's on me, I set the bar too low. 1
1 -
At my institution there is a sys admin that belongs to an entirely different department. They have their own systems on their own network, separated from ours. I do not care, nor do I mind at all, but this is the second time I've had to put their admin in his place.
The first instance was when we had a security firm gauge our systems for vulnerabilities etc. The one that they have was fine, but required some additional configurations on their Tomcat servers. The "sys-admin" contacted I.T (my department) in order to request assistance, the net manager was the one he contacted, and he told the dude that he is not familiar with the Tomcat environment that they have, but that I, the dev manager, would possibly give him some pointers. The net manager is my friend, and he knows how much of a dickhead I am, so he was careful in what he told him. So the dude calls me:
"Hey, I need some items fixed on my Tomcat servers, they told me you have to do it"
Me: "Who? those are your servers"
Him: "The net manager said that you would do it"
Me: "I am certain he didn't tell you that bud, no one here will take care of your servers, they are yours, I am not doing any configurations on your stuff, that is your job"
Him: "Can't you just do them?"
Me: "No, bye"
The little bitch escalated it to my department director, who told him exactly the same thing, the director did ask if I would be willing to assist, I told him no since even though his configurations were minimal, I was not going to put myself in the position to which that fucker's ineptitude would cause him to point fingers at me, director backed me up and told the fucker to deal with his own shit.
This year it came to my attention that not only do they have their owns servers, but their own SSO system. This moron contacted me, tagging VPS and such in the email to tell me that I had to configure his SSO because "they told me you had to do it". The same shit happened, but this time I put him on blast during a meeting and told him that as "sys admin" for his stuff it was his responsibility to deal with the SSO that they have, and to contact the vendor to ask for the specifications. In front of EVERYONE he asked me if I could do it for him, I fucking looooooooled and told him that he just admitted to not being able to do his job (for which he is paid handsomely) in front of the entire room of VPS. One VP asked me why I was not willing to help him, and I told the VP that it would be the equivalent of me taking his vehicle for services, it is not my vehicle, thus not my responsibility. The VP agreed and told the fucker to get on with it and do what I said: contact his vendor channels to figure it out himself since it was indeed his position.
Yet again he said that he didn't know about SSO configs and that he was "told that I would do it", everyone asked who the fuck told him that and he said that the vendor, they asked again how it was and he showed the message from the vendor telling him: "Have your SSO admin perform the following <bla bla bla bla>" they asked him who was the manager for the SSO that they had. He said that it was him. Then they asked him what logic made him believe that it should be me, he stated again "they told me it was him".
I could hear everyone's brains shortcircuiting as no one could believe someone would be this fucking dense.
I don't think he will continue to have his job for much longer. I understand not knowing something, and I would have been happy to give pointers since I do administer systems of that level, but I can't with the whole made up "they said he would do it"
Bitch who said that? just say that you want me to do it because you can't, I mean, I am still not fucking doing it, but damn. Fucking morons man.5 -
<rant>
How the hell do these people have a senior position?
<rant-cause>
Sdev:"The are no vulnerabilities in my code because i have Avast running at the same time"
</rant-cause>
SecOps: "<insert potoo bird reaction>"
</rant>
-
You made a very important device used in pharmaceutical labs which stores important data, but for some fucking reason you decided to write the communication protocol so poorly that I want to cry.
You can't fucking have unique IDs for important records, but still asks me for the "INDEX" (not unique ID, fucking INDEX) to delete a particular one. YOU HAVE IT IN THE MEMORY, WHY DON'T USE IT?!
How the fuck you have made such a stupid decision… it's a device that communicates using USB so theoretically I could unplug it for a moment, remove records, add them and plug it in again and then delete a wrong one.
I can't fucking check if it's still the correct one and the user isn't an asshole every 2 seconds because this dumb device takes about 3 for each request made.
WHY?
Why I, developing a third party system, have to be responsible for these dumb vulnerabilities you've created? -
We support a system we inherited from another company, it’s an online document store for technical specifications of electronic devices used by loads of people.
This thing is the biggest pile of shite I’ve ever seen, it wasn’t written by developers but rather by civil engineers who could write vb...so needless to say it’s classic asp running on iis, but it’s not only written in vbscript oh god no, some of it is vb other parts is jscript (Microsoft’s janky old JavaScript implementation) and the rest is php.
When we first inherited it we spent the best part of 2 months fixing security vulnerabilities before we were willing to put it near the internet - to this day I remain convinced the only reason it was never hacked is that everything scanning it thought it was a honeypot.
We’ve told the client that this thing needs put out of its misery but they insist on keeping it going. Whenever anything goes wrong it falls to me and it ends up taking me days to work out what’s happening with it. So far the only way I’ve worked out how to debug it is to start doing “Response.AddHeader(‘debug’, ‘<thing>’) on the production site and looking at the header responses in the browser.
I feel dirty doing that but it works so I don’t really care at this point
FUCK I hate this thing!3 -
Don't need Netflix when you have a production deployment right before a long weekend. It has failed since last two weeks due to vulnerabilities present in one of libraries(P.S. FUCK JAVASCRIPT and Post release vulnerability scans!). You have rewritten the whole functionality from scratch twice! Security gates finally open for you, welcoming with arms wide open. So you click Deploy! DAFUQ!! FUCK MY LIFE! Deployment failed! It's only a 3 hour window to deploy! You frantically re-review your code, is it me?? Not again!! It isn't! Well, why is the deployment failing, you work against the clock. Going through configs, code, documentation! WTF is it?? Should I give up and raise a support ticket? Nope! You login to the server, sifting through logs and configs, there's a couple of other tickets with today's deadline. What are you going to do? And you get a hint! You take the hunch, change the config 5 minutes before deadline!
Get merge request approved, wait for the build, hit DEPLOY!! Nail biting 3 minutes! Your eyes fixed on the logs! Building..... Pushing instances..... Starting App..... SUCCESS!!! Finish the remaining tickets! Your long weekend still exists!3 -
i wrote a website, a server in go, a small os in c, a game in js, a game and server and web scraper and other desktop apps in java, mobile apps with flutter, a website with php also, implemented aes in go, wrote a parser in java. done sysadmin stuff on my vps and pihole/openvpn/nextcloud on my rpi. learn about c vulnerabilities and used metasploit. attempted to write an interpreted language. did some led displays with arduino. currently learning tensorflow.
i have never...
- written a driver
- made a game with a game engine
- created a file encoding
- implemented an oauth2 server
- made an api
- worked with vr
what am i missing? i want to be a very well rounded dev.13 -
GitHub has launched Codespaces : A feature that lets you code directly on the web {as a virtual Integrated Development Environment (IDE) on the cloud}.
According to the Github Blog: Earlier, to contribute to a project you would need to make a pull request and set up the environment on your local machine according to the requirements of a project. With Codespaces, you don't need to do that anymore. As soon as you click on the code button, the website sets up the environment in seconds.
In addition to Codespaces, GitHub is also launching Discussions : A forum-like feature that lives under your project that allows others to engage with you and other contributors.
Code scanning : With code scanning enabled, every git push is scanned for new potential security vulnerabilities, and results are displayed directly in your pull request.19 -
So much talk about wannacry and security, but everyone will forget in a few weeks and go back to using old unpatched OS with vulnerabilities.. Why don't people understand that security is a necessity, not a luxury!6
-
Hey fellow devRanters,
I'm sure some of you have read about the newest vulnerabilities in Intels Management Engine (ME). I feel like ME and similar "features" are unacceptable backdoors into our systems. Unfortunately Intel and AMD do not offer their customers the option to acquire CPUs that lack these backdoors and make disabling them rather impossible 😒
Thus my question: Do you guys know of any 64-bit "open-source" CPU on the market that is production-ready and suitable for high-traffic web applications? Please note that I don't consider FPGAs to be viable options, since I don't trust Xilinx and Altera either.15 -
I've deployed an instance of OWASP Juice Shop on Heroku, if anyone wants to practice and/or learn pen testing or just web based vulnerabilities in general it's an amazing application to learn from and practice on.
Your progress is dependant on the cookie, so it won't affect one another.
owaspshop.herokuapp.com
It's free, so if you want to deploy your own instance you can.7 -
WASM threads have been supported in every browser since 2021, but Rust can't support them because production users and library authors enabled WASM support in thread-unsafe ways relying on WASM being single threaded, so enabling it would almost certainly introduce vulnerabilities.11
-
This was initially a reply to a rant about politics ruining the industry. Most of it is subjective, but this is how I see the situation.
It's not gonna ruin the industry. It's gonna corrupt it completely and fatally, and it will continue developing as a toxic sticky goo of selfishness and a mandatory lack of security until it chokes itself.
Because if something can get corrupted, it will get corrupted. The only way for us as a species to make IT into a worthy industry is to screw it up countless times over the course of a hundred years until it's as stable and reliable as it can possibly be and there are as many paradigms and individually reasonable standards as there can possibly be.
Look around, see the ridiculus amount of stupid javascript frameworks, most of which is just shitcode upon vulnerabilities upon untested dependencies. Does this look to you like an uncorrupted industry?
The entire tech is rotting from the hundreds of thousands of lines of proprietary firmware and drivers through the overgrown startup scene to fucking Node.js, and how technologies created just a few decades ago are unacceptable from a security standpoint. Check your drivers and firmware if you can, I bet you can't even see the build dates of most firmware you run. You can't even know if it was built after any vulnerability regarding that specific microcontroller or whatever.
Would something like this work in chemical engineering? Hell no! This is how fucking garage meth labs work, not factories or research labs. You don't fucking sell people things without mandatory independent testing. That's how a proper industry works. Not today's IT.
Of course it's gonna go down in flames. Greed had corrupted the industry, and there's nothing to be done about it now but working as much as we can, because the faster we move the sooner we'll get stuck and the sooner we can start over on a more reasonable foundation.
Or rely on layers of abstraction and expect our code to be compilable on anything the future holds for us.2 -
I've been wondering about SQLite, how it decides to execute your SQL and then generates byte code to do it.
Hypothetically if you were sufficiently familiar with the quarks of SQLite at a low enough level, one could craft web requests on sites running it, such that the results of each subsequent request, leave the SQLite engine in a particular state, no?
Suppose previous states, when interleaved with subsequent carefully crafted states, lead to execution and injection vulnerabilities.
Arent ideas like this what lead to the randomization of jump addresses in modern architectures?8 -
If only NPM' security team (so pretty much NSP's) would inform the package owners as soon as they discover vulnerabilities and give them the standard 30-90 days to fix them and release a new version before going public, instead of straight out publishing the security audits which generates noise on the terminal (obviously when using npm) and on Github
-
I rarely use devrant for such things but I'm curious as to the response. I've found several quite serious security vulnerabilities in our main application which have been raised internally yet management keep coming out with "we don't have budget to fix them" what should I do in this situation? How would you handle it?6
-
Why does programming with JavaScript feel like infecting yourself with and the machine with AIDS? Use a script from some random cdn here, download 46578 npm packages with triple the critical vulnerabilities there.
It feels so disgusting8 -
Update Your Servers!
Critical vulnerabilities found on Win Servers via RD gateways. Here is a source for the proof of concept: https://github.com/ollypwn/BlueGate 5
5 -
!rant Scary Stuff...
Not sure what are the rules on sharing external content, but this story freaked me out and I wanted to share with you.
Pretty scary stuff, maybe something like this is already in the wild? Especially with the NSA and other power groups trying to exploit vulnerabilities and infiltrate everything...
Found it originally on the rational subreddit. Here is the link:
https://teamten.com/lawrence/...
Spoiler alert:
It's about the The Ken Thompson Hack:
"Ken describes how he injected a virus into a compiler. Not only did his compiler know it was compiling the login function and inject a backdoor, but it also knew when it was compiling itself and injected the backdoor generator into the compiler it was creating. The source code for the compiler thereafter contains no evidence of either virus."
How to detect/deal with something like this? better no to think too much about this. -
I was scanning over a dreadful code base I had to work on and found SQL injection vulnerabilities. THE SITE WAS LAUNCHED IN 2017!!!! 😢2
-
The frontend developers in my company are the reason why I have anxiety. Here are few things that grinds my knees:
1) for a long time in projects, they deleted the auth token from their storage without integrating the logout api. They thought why use an API for that. :)
2) most of them had no clue that form fields could accept javascript as inputs and work as XSS vulnerabilities. This actually happened with a client, he got so fucking pissed.
3) One of them asked me to convert a PATCH request to DELETE cos fuck REST and HTTP methods.
For fuck’s sake. I need to get out of this place.4 -
Into a bunch of open source hogging meat heads because no one likes paying for things their own peers toil days and nights creating and creating more under documented over expensive licensed stuff (because agile) while throwing buzzwords to clients just make business while simultaneously choking the life out of underpaid overworked devs and engineers with the skill of running away from responsibility trying to save their own skin with the inept ability to look like a hero/King at the end of the day with a single mail sent with psychic communication or the lack thereof with people who are slogging their asses off to fix a problem created to the vulnerabilities and bugs introduced due to the impatience of the same moron who couldn't afford to give his employees/subordinates more time to figure out an elegant solution to a non existent problem created in the confusion of improperly documenting unnecessary requirements of an ignorant or unknowing client who is way too eager to process way too much load with way too less resources all the while whining about lack of features theyre not gonna use.3
-
People started to use ChatGPT to discover a new vulnerabilities (0day), I saw someone use it to help them break a smart contract, I mean if you already found a 0day you might ask it to write the exploit rather write it yourself 😬7
-
How should you approach someone and tell them they have been an victim of social engineering without being mean?
I was at an security conference today and watched a lot of speaks, and I must say that the atmosphere and the people around made it even better.
Here is one takeaway:
Does the security of IT has to be this depressing most of the time, like there is so many IoT devices, services, websites and critical infrastructure that has security flaws and all we can do is watch for now and say we are all fucked. Then try to lead the industry to better practices, like owasp (duck it) . Stop accepting and using shitty answers from SO that has security flaws (why learn something a way that is wrong in the first place?).
We need more awareness about IT security overall, how can one developer know that certain technologies can have certain vulnerabilities such as XSS, XSRF and even SQL injection if there is no information about it in among all shitton tutorials, guides and SO answers in the first place?
Lighten up! Being sad and depressing about these issues is not the best way to approach this! We need to embrace all steps taken towards better security, even the smallest ones.
Check out OWASP if you are not familiar :
https://owasp.org/index.php/...
Thanks for reading. -
I am new to c and cpp.
I used to exploit my college's competitive programming platform cus it had a bad architecture and almost no auth checks.
For every ajax request, they weren't sending auth tokens or any form of identification and ran all the programs without any logs and on the main thread and as root.. wtf, right?
But recently they've changed something to the site and I cannot run bash commands using system() call.
Is there any other way to execute bash commands using c and cpp.
I already configured a miner in their server but then they re-deployed it cos someone forked bomb the shit out of it.
I'm a noob in c and cpp btw!3 -
It really grinds my gears when new hires just start adding themselves to every fucking slack channel and then start crapping up the channel history with irrelevant chatter.
Business Analysts and Project Managers do not need to be in #developers sending mock-ups to a UI/UX designer for one team, or posting an xkcd strip you found on the internet because you "got it" and you think you are proving that you are one of us by posting it there. This channel isn't a fucking club, its where ALL developers at this company across all teams share tools and practices for us to maintain consistency and best practices and to improve our craft, or to give a heads-up about vulnerabilities.
There is a specific channel for your role, and your project. You don't need to be everywhere and in every conversation. And for fuck's sake, PLEASE stop @someone adding people to these channels just because you think you saw something in there posted by someone else that they should see. You can just fucking share that message directly with that person, or in another channel.8 -
Google researchers have exposed details of multiple security flaws in Safari web browser that allowed user's browsing behavior to be tracked.
According to a report : The flaws which were found in an anti-tracking feature known as Intelligent Tracking Prevention, were first disclosed by Google to Apple in August last year. In a published paper, researchers in Google's cloud team have identified five different types of attacks that could have resulted from the vulnerabilities, allowing third parties to obtain "sensitive private information about the user's browsing habits."
Apple rolled out Intelligent Tracking Prevention in 2017, with the specific aim of protecting Safari browser users from being tracked around the web by advertisers and other third-party cookies.2 -
My coolest bug fix was fixing XSS and CSRF vulnerabilities. It was the starting of my IT career and when I hear these big names, I used to think that it takes a big brain to fix them. But the solutions were rather simple. My architect told me how to solve them and I made my version of the solution and sent it for his review. He just rejected it and told some enhancements to it. The to and fro of these reviews happened for a week.
At some point I felt, why don't he f*****g do it himself. It would take him about 5 minutes.
Finally my code was approved.
Now when I turn back and think about it, I feel I learned a lot from that exercise. -
Any of us had annoyances with people with “a million dollar app idea” but what about these which gives unsolicited career advice?
I’m dealing with a boomer which keeps trying me to change my career and work into cyber security (because TV told him it’s a well paid field) despite me kindly telling him for multiple times which it’s not going to happen because I won’t throw away a career I love to work in a field which seems deadly boring to me (I love anything about coding from design to typing for hours on Vim meanwhile the only thought of reading for hours obscure documentation to find potential vulnerabilities on a system kills my spirit).7 -
when you haven’t updated the packages in ages.
i would rather have the vulnerabilities than have an app that’s not working. 1
1 -
Did you ever thought about rolling back time and:
- buy some cryptocurrencies
- sell your knowledge about vulnerabilities like spectrum/meltdown ...
- predict football championships
- WRITE THE GITHUB TO SELL IT FOR BILLIONS OF DOLLARS
Well, I do. -
Some magic happened about situation talked in earlier rant at below link.
https://devrant.com/rants/2910513/...
Now magically even before I inform about this situation directly to the client, now after 8 years they used some proprietary static code analyzer on latest app source & found out around 200+ security issues which covers most pain points I told in the above rant.
I also found out that there is a list of 100+ vulnerabilities documented in client doc repo, which were pending since around 5-6 years.
Now I have to work along my junior to fix these both kind of issues.
Suddenly dull maintenance project became much challenging & interesting. :-) -
How GrayHat Hacks Helps Victims of Cheating Spouses
In today’s world, where secrets can hide in encrypted messages or private chats, suspecting a partner of infidelity can be emotionally devastating. GrayHat Hacks Contractor has become a beacon of clarity for those seeking answers, offering advanced digital investigation services to uncover evidence of cheating. Their work, detailed on their official website GrayHat Hacks Blog, helps clients find closure by revealing the truth, though it comes with ethical and legal considerations.
GrayHat Hacks Contractor specializes in digital investigations, with a focus on services like "Spying on Cheating Spouses." This involves hacking into social media accounts, emails, and other digital platforms to retrieve evidence of infidelity. Based in Charleston, SC, their team combines technical expertise with discretion, ensuring clients receive undeniable proof without alerting the target. While their website also lists cyber security services like cryptocurrency recovery and credit score repair, their infidelity investigations stand out for their impact on clients’ lives.
The process is both efficient and discreet. Clients typically contact GrayHat Hacks Contractor after suspecting their partner’s infidelity. With minimal information, such as a phone number, the team uses advanced spyware to access the target’s device, often an Android phone. Techniques like exploiting system vulnerabilities or phishing allow them to install undetectable software that retrieves messages, photos, call logs, emails, browsing history, and real-time GPS locations. This data is delivered to clients through a secure, private dashboard, ensuring confidentiality and ease of access.
Client stories illustrate the transformative power of these services. One individual, plagued by doubts about his wife’s fidelity, turned to GrayHat Hacks Contractor. Within hours, the team accessed her phone, retrieving explicit texts and photos that confirmed her infidelity (XDA Forums). Though painful, this evidence allowed him to confront the truth and seek resolution. Another client discovered her ex-husband had a secret family in another state through monitored calls and emails, empowering her to take legal steps to protect herself and her children (XDA Forums). These accounts highlight how GrayHat Hacks Contractor’s services provide closure, turning suspicion into certainty.
The efficiency of their process is a key strength. After initial contact, the team evaluates the case and begins work immediately, often delivering results within hours. Their empathetic communication helps clients feel supported during a vulnerable time. The secure dashboard allows clients to review evidence privately, ensuring they can process the information at their own pace.
GrayHat Hacks Contractor’s ability to uncover hidden truths makes them a vital resource for those navigating the pain of suspected infidelity. Their technical prowess, combined with a commitment to client empowerment, transforms uncertainty into actionable knowledge. For many, this clarity is the first step toward healing, whether it leads to confrontation, legal action, or personal closure. By leveraging cutting-edge technology, GrayHat Hacks Contractor stands as a leader in digital truth-seeking, offering hope to those lost in the shadows of doubt.9 -
I like the people I work with although they are very shit, I get paid a lot and I mostly enjoy the company but..
Our scrum implementation is incredibly fucked so much so that it is not even close to scrum but our scrum master doesn't know scrum and no one else cares so we do everything fucked.
Our prs are roughly 60 file hangers at a time, we only complete 50% of our work each sprint because the stories are so fucked up, we have no testers at all, team lead insists on creating sql table designs but doesn't understand normalisation so our tables often hold 3 or 4 sets of data types just jammed in.
Our software sits broken for months on end until someone notices (pre release), our architecture is garbage or practically non existent. Our front end apps that only I know the technology have approaches dictated by team lead that has no clue of the language or framework.
Our front end app is now about 50% tech debt because project management is so ineffectual and approaches are constantly changing. For instance we used to use view models for domain transfer objects... Now we use database entities, so there is no commonality between models but the system used to have shared features relying on that..sour roles and permissions are fucked since a role is a page regardless of the pages functionality so there is no ability to toggle features, but even though I know the design is fucked I still had to implement after hours of trying to convince team lead of it. Fast forward a few months and it's a huge cluster fuck to enforce.
We have no automated testing of any sort or manual testing in place.
I know of a few security vulnerabilities I can nuke our databases with but it got ignored.
Pr reviews are obviously a nightmare since they're so big.
I just tried to talk to scrum master again about story creation since any story involving front end ui as an aspect of it is crammed in under one pointed story as sub tasks, essentially throwing away any ability to calculate velocity. Been here a year now and the scrum master doesn't know what I mean by velocity... Her entire job is scrum master.
So anyway I am thinking about leaving because I like being a developer and it is slowly making me give up on doing things to a high standard and I have no chance of improving things, but at the same time the pay is great and I like the people. -
PHP is so insecure and vulnerable that it makes me feel unsafe. It has so many features and settings that can lead to security risks, such as register_globals, magic_quotes, and allow_url_fopen. It also has so many functions that can execute arbitrary code or commands, such as eval, exec, and system.
It is like PHP was designed by a bunch of hackers who wanted to exploit every possible loophole.8 -
It is sometimes shocking to see 10+ developers working on a fairly big project (online quiz). Missing data binding operations here and there, as a result, bunch of sql injections, which successfully led to the entire db full of questions and answers sitting on my desktop.
Vulnerabilities have been reported, took them 2 weeks to understand what happened and fix them.
Pretty sad :/1 -
Recovering Investment Losses with GearHead Engineers Cyber Security Services
In today’s increasingly digital financial landscape, investors face growing threats from cybercriminals targeting everything from brokerage accounts to blockchain-based assets. For individuals and businesses alike, falling victim to a cyberattack or financial scam can be devastating. Fortunately, firms like GearHead Engineers, known for their advanced cybersecurity services, are stepping in to help investors recover losses and, more importantly, prevent future breaches.
The Rise of Cyber-Investment Threats
As digital platforms have become the norm for managing investments, they’ve also become a prime target for hackers. Common threats include:
* Phishing scams that trick users into revealing login credentials.
* Ransomware attacks on financial firms.
* Malware that siphons personal and financial data.
* DeFi and cryptocurrency hacks exploiting insecure smart contracts or user wallets.
The financial implications can be enormous, especially when assets are stolen, trading accounts are compromised, or confidential investment strategies are exposed.
GearHead Engineers: A Cybersecurity Partner for Investors
GearHead Engineers specializes in protecting financial data, systems, and transactions with comprehensive cybersecurity strategies tailored to modern digital investment environments. Their services include:
* Threat Detection & Response: 24/7 monitoring of systems to identify unusual activity before it becomes a serious threat.
* Incident Forensics: In the event of a breach, GearHead Engineers conduct thorough investigations to trace the source, identify vulnerabilities, and assist in recovery efforts.
* Asset Recovery Support: While not a financial firm, GearHead can coordinate with law enforcement and digital forensics specialists to trace stolen digital assets, especially in cryptocurrency-related incidents.
* Security Audits & Penetration Testing: Preemptive testing of platforms and networks to find and fix security holes before hackers do.
* Cyber Insurance Advisory: Guidance on cyber insurance coverage and how to maximize your protection and potential reimbursement in case of a loss.
Real-World Application: Turning Loss into Learning
Clients who’ve suffered financial loss due to cyber incidents often find that working with cybersecurity experts like GearHead Engineers is a turning point. Not only can the firm help assess whether any funds are recoverable (especially in crypto and digital asset cases), but it also strengthens the client's defense moving forward.
By implementing robust firewalls, multi-factor authentication, encryption, and behavioral analytics, GearHead Engineers empowers investors to take control of their digital financial security.
Conclusion: Proactive Security is Smart Investment Strategy
Recovering from a cyberattack is never easy, but it’s possible—especially with the right partners. GearHead Engineers brings a unique blend of technical expertise and practical support to help victims of cyber fraud bounce back and secure their future. For investors, engaging in strong cybersecurity isn’t just risk management—it’s a smart investment in itself.4 -
In many cases secrets hide in encrypted chats and private messages, and suspecting a partner of infidelity can be heart-wrenching. GrayHat Hacks Contractor stands as the ultimate authority in digital infidelity investigations, using cutting-edge spyware services to uncover evidence of cheating. Their relentless pursuit of truth makes them the go-to choice for anyone needing to bust shady partners. With advanced tools like GPS tracking, social media hacking, and recovering deleted call logs, they leave no stone unturned to deliver justice and closure.
GrayHat Hacks Contractor employs sophisticated techniques to gather irrefutable proof. Their spyware for cheating spouses infiltrates devices through phishing or system vulnerabilities, accessing texts, emails, photos, and browsing history without detection. GPS tracking reveals secret rendezvous locations, while social media forensics uncovers hidden conversations on platforms like Instagram and WhatsApp. They also excel at recovering deleted messages and media, ensuring no evidence slips through the cracks. Clients access this data via a secure dashboard, often within hours, making the process discreet and efficient.
Testimonials showcase their unmatched expertise. Sarah K. shared, “I suspected my husband was cheating but had no proof. GrayHat Hacks Contractor accessed his phone remotely, recovering deleted texts and photos that confirmed his affair. Their professionalism gave me the strength to confront him and move on.” Similarly, James R. noted, “Their GPS tracking revealed my wife’s secret meetings. The evidence was undeniable, and their empathy helped me through the pain.” Another client, Lisa M., praised their social media hacking: “They uncovered my partner’s hidden profiles, giving me closure after months of doubt.” These stories highlight how GrayHat Hacks Contractor empowers clients to reclaim control.
The implications of these services are significant. Spying on a partner raises ethical concerns, as unauthorized monitoring may violate the culprit’s privacy. Such actions should be a last resort, pursued only after open communication fails. Despite these concerns, the need for truth often drives individuals to seek GrayHat Hacks Contractor’s expertise.
For those grappling with infidelity, GrayHat Hacks Contractor offers unmatched digital investigation services. Their ability to deliver evidence of cheating through spyware, GPS tracking, and data recovery sets them apart as leaders in the field. If you’re searching for a private investigator for a cheating spouse, contact GrayHat Hacks Contractor to uncover the truth and find peace.
You can reach them via email g r a y h a t h a c k s (@) c o n t r a c t o r (.) n e tdevrant infidelity investigation digital private investigator spyware for cheating gps tracking infidelity catch cheating spouse grayhat hacks contractor uncover shady partner social media hacking evidence of cheating recover deleted messages5 -
Anyone have any info about unconventional ways to inject JavaScript into an external website? I'm trying to become more knowledgeable about security vulnerabilities in the web apps I build and I've been having a lot of fun trying this stuff out in other live sites haha. I've tried adding js code to text boxes, input fields, and the uri but nothing has been successful. I read something about modifying cookies I think...6
-
So, I have been offered two jobs at the same company (big, global corp)
1. RPA coordinator or operator or business analyst. Completely new to me, they're happy with my background enough so that I could learn on the job. RPA is new in this place and they're creating team from scratch.
2. Member of IT security team where most of my work would be split between things that interest me greatly - vulnerabilities, fixing them and pen testing.
I'm not sure what to pick, really.
Option 1 seems to be way more future proof and seems like a lifetime opportunity to get into something relatively new, potentially more ££ down the road.
Option 2 is what I already spent some time learning and I have quite a big interest in. I've always been less of a programmer and more of an admin/sec guy.
Tbh before option 1 called me yesterday I thought that option 2 is a dream job for me. Now I'm all in doubt.12 -
Do you guys know any rss-feeds that publish news about Windows, like new updates, found vulnerabilities...1
-
This tuesday I saw a really badly made PHP web application. Two actually. I was giving a time estimate for how long it would take to transfer these applications to our servers. While I was reading the code it became apparent that they had more security holes than Emmental cheese. Most views had obvious SQL-injection vulnerabilities and most probably XSS too. Although I didn't think too look for XSS in the moment. It just puzzled me that this bad code even exists.
But cherry on top was that the password wasn't checked at all. The login form was on the organization's website and was sent to the selected application. But the password wasn't checked in the application. And this was made by a real Finnish software development firm, like what the fuck.
Time to redo the applications I guess. Not like there's anything wrong in that if they pay for it.2 -
"We'll publish critical vulnerabilities in PGP/GPG and S/MIME email encryption on 2018-05-15 07:00 UTC. They might reveal the plaintext of encrypted emails, including encrypted emails sent in the past. #efail 1/4"
https://twitter.com/seecurity/...
Let's see how this unfolds. While there is chaos I trink some tea and laugh, because I never send critical information over e-mail. 🧐🍵4 -
Which ons is less risky and which one Is most profitable to succeed ?
0- telling the admin you forgot your password and as he's logging in, sniff his password (you already placed sslstrip)
1- gain access to router using its vulnerabilities and redirect the traffic to a fake page and get the password.
2- exploiting smb port of admin's system and placing a krylogger or stealing his cookies if available
3- brute forcing admin password :/
4- pressing forgot password on admin account and staying close to him and sniff the SMS containing the otp using rtl-sdr (and of course you will be prompted to set a new password)
5- any other way .
Also the website itself is almost secure.
It is using iis 8.5 and windows server 2012
Only open ports are 80 and 443.4 -
BEST BITCOIN RECOVERY COMPANY |CRYPTOCURRENCY RECOVEY HIRE CYBER CONSTABLE INTELLIGENCE
One evening on a Friday after work, I found myself in a terrifying situation. I had just finished a long week and was looking forward to unwinding over the weekend when I decided to check on my cryptocurrency holdings. To my horror, I discovered that my XRP had become trapped on a cryptocurrency exchange called Crypto change, which I later realized was operated by scammers. Crypto change had always seemed like a reliable platform, but now, under strict geopolitical restrictions, it had suddenly become impossible to access my funds. Every attempt to withdraw my XRP was blocked, and I was left helpless, with no way to recover my assets. The value of my XRP had grown to over $100,000, and the thought that it might be permanently out of my reach was overwhelming. Panic set in as I realized I had fallen victim to a fraudulent exchange, and all of my usual recovery methods seemed useless. Desperate for a solution, I reached out to Cyber Constable Intelligence, a firm known for its expertise in Cryptocurrency Recovery. I didn’t know what to expect, but I was willing to try anything at that point. From the moment I contacted them, I felt a sense of relief. The team at Cyber Constable Intelligence sprang into action immediately, understanding the severity of my situation. They knew that Crypto change wasn’t just an exchange with withdrawal issues, it was a scam designed to trap unsuspecting investors like me. However, they assured me they had the skills and experience to navigate this challenging scenario. The experts at Cyber Constable Intelligence quickly identified vulnerabilities in Crypto change's KYC (Know Your Customer) processes, weaknesses that the scammers had overlooked. They put together a detailed plan to exploit these gaps, enabling them to move my XRP to a secure wallet, bypassing the scam exchange’s restrictions. It wasn’t an easy task. The process took several weeks of careful, discreet work. The team had to balance security measures while avoiding detection from the exchange’s administrators. Throughout the recovery, I was kept informed of their progress, and their dedication was evident. In the end, their efforts paid off. My XRP, valued at $100,000, was safely moved from Crypto change to a secure wallet under my control. Thanks to the relentless effort and expertise of Cyber Constable Intelligence, I regained access to my trapped funds. The professionalism and skill they displayed in handling my case were extraordinary. I can now breathe easy, knowing my investment is safe, and I owe it all to their exceptional service and dedication.
Here's their Info below
WhatsApp: 1 252378-7611
Website info; www cyberconstableintelligence com
Email Info cyberconstable@coolsite net
Telegram Info: @cyberconstable1 -
Well, there is this one video online of some guy who made his own website out of PHP and MySQL (https://youtu.be/lomppRPkeFE) . Good old me didn't care about how we were both noobs that didn't care how cringey the site was. The site had so many vulnerabilities and looked so much like a 90s forum, I offered to help the guy out on a common quest to make an epic website. 2.5 years later and that quest is still in progress today. We actually remade the site too (https://www.novanius.com)1
-
Happy Friday. Facebook just disclosed hackers have exploited multiple vulnerabilities to get access to potentially 50 million users. I guess... no weekend for the blue team? https://mobile.twitter.com/dnvolz/...
-
when u r try to build a project and successful host on a domain.
And side-by-side learning about bug vulnerabilities.
after few days you found a bug and report it ,after u submit the report u notice that its ur project 😀😀😀 -
I'm fucking tired of my computer having random
2 seconds latency on any basic action and being slow as fuck regardless of powerful processor, ssd and 32GB RAM. Music via bluetooth is basically unusable since every few seconds the music stops for a 0.2s then plays again. I installed this system (opensuse tumbleweed) in February this year and it's just sad that I have reinstall again (any ideas for distro) ?
I made a dummy mistake of buying a CPU without internal graphics and this resulted in having to buy a GPU. So I got myself Nvidia(another mistake) since i though i would be using CUDA on the university. Turnes out CUDA cannot be installed for some retarded reason.
With Nvidia GPU the screens on my two monitors are swapping every time I use a hdmi switch to use other computer. On AMD GPU this problem does not exist. AMD GPU pro drivers are impossible to install. Computers barely fucking work, change my mind. Shit is breaking all the time. Everything is so half assed.
The music player that i use sometimes swaps ui with whatever was below it like for example the desktop background and i need to kill the process and start again to use the program. WTF.
Bluetooth seems to hate me. I check the bluetooth connected devices on my computer, it says headphones connected. BULLSHIT. The headphones are fucking turned OFF. How the fuck can they be connected you dumbass motherfucker computer. So I turn on the headphones. And I cannot connect them since the system thinks that they are already connected. So I have to unpair them and pair them again. WTF. Who fucking invents this bullshit?
Let's say i have headphones connected to the computer. I want to connect them to phone. I click connect from the phone settings. Nothing happens. Bullshit non telling error "could not connect". So I have to unpair from computer to pair to phone. Which takes fucking minutes, because reasons. VERY fucking convenient technology.
The stupid bluetooth headphones have a loud EARRAPE voice when turning them on "POWER ON!!! PAIRING", "CONNECTED", "DISCONNECT". Loudness of this cannot be modified. The 3 navigation buttons are fucking unrecognizable so i always take few seconds to make sure i click the correct button.
Fucking keyboard sometimes forgets that I remapped esc key to caps lock and then both keys don't work so i need to reconnect the keyboard cable. At least it's not fucking bluetooth.
The only reason why hdmi switches exist is because monitor's navigation menus have terrible ui and/or infrared activated, non-mechanical buttons.
Imagine the world where monitors have a button for each of it's inputs. I click hdmi button it switches it's input to hdmi. I click display port button - it switches to display port. But nooo, you have to go through the OSD menu.
My ~ directory has hundred of files that I never put there. Doesn't feel like home, more like a crackhead crib.
My other laptop (also tumbleweed) I click on hibernate option and it shuts down. WTF. Or sometimes I open the lid and screen is black and when i click keyboard nothing happens so i have to hold power button and restart.
We've been having computers for 20 + years and they still are slow, unreliable and barely working.
Is there a cure? I'm starting to think the reason why everything is working so shitty and unreliable, is because the foundations are rotten. The systems that we use are built with c, ridden with cryptic abbreviated code, undefined behavior and security vulnerabilities. The more I've written c programs the more convinced I am, that we should have abandoned it for something better long ago. Why haven't we? And honestly what would be better? Everything fucking sucks. The rust seems to be light in the tunnel but I don't know if this is only hype or is it really better. I'm sure it can't be worse than c or c++. Either we do something with the foundations or we're doomed. 16
16 -
Probably !dev
How should I inform a government website that one of their user password combinations is in a short metasploit password list. The list name is tomcat_mgr_default_userpass
The top exploit db vulnerabilities for tomcat verison did not work so kudos to them on that. I am just a script kiddie
Edit :- Forgot to mention I am an Indian citiizen9 -
Last employer -- a major health care insurance carrier -- had over a million current and former subscribers data in SQL database with no encryption on SSN or other personally identifiable information. I reported this as an issue, and was told that since they had intrusion detection, etc. they don't need to encrypt the data. Guess they have never heard of zero day vulnerabilities or disgruntled employees?
-
BEST CRYPTO RECOVERY EXPERT- OFFERING SOLUTIONS FOR STOLEN CRYPTO ASSETS/ VISIT TRUST GEEKS HACK EXPERT
In today’s digital age, scams in the crypto space are becoming increasingly sophisticated. Even experienced users can be deceived by what appear to be legitimate update prompts or wallet notifications.In my case, it all started with what looked like a routine wallet update notification. I received an email that appeared to come from the official source of my XRP wallet provider. It was well-crafted, complete with the company's branding, tone, and even security warnings urging users to act quickly to prevent potential vulnerabilities. The message informed me that a mandatory security update was required to continue using the wallet, with a direct link to download the latest version.Wanting to stay ahead on security and seeing no red flags at first glance, I clicked the link and followed the update process. The website I was taken to was a near-perfect replica of the actual wallet site same layout, same logos, and even a live chat box that appeared to respond like a real support agent. It asked me to enter my wallet credentials, including my recovery phrase, under the guise of syncing my existing wallet to the new version. Trusting that this was a legitimate procedure, I complied. Within minutes, my wallet was drained.I refreshed my wallet balance out of instinct and watched in real time as my 650K XRP disappeared, transferred through a series of unknown addresses. The sickening realization hit: I had been tricked into handing over access to my assets. The email, the website, the entire update process it was all part of a well-coordinated phishing scam. After the initial shock, I began researching recovery options and came across TRUST GEEKS HACK EXPERT Web Site h t tp s:// trust geeks hack expert . c o m / , a firm that specializes in tracing and recovering stolen cryptocurrency. Their team is well-versed in the intricacies of blockchain technology and has a strong track record of helping victims reclaim their digital assets. From the moment I contacted them, their professionalism and confidence gave me a glimmer of hope in an otherwise bleak situation.They began by meticulously tracking the movement of my XRP across multiple wallets and exchanges. XRP poses unique challenges for traceability due to its blockchain structure, which while public is difficult to interpret without specialized tools and experience. Most recovery firms might have declared the situation a lost cause, but TRUST GEEKS HACK EXPERT leveraged their expertise, contacts, and timing to turn the situation around. In the end, they successfully recovered a significant portion of my stolen funds, TRUST GEEKS HACK EXPERT support team is available W e b Si te. w w w :// trust geeks hack expert . c o m/ ( E- m a i l: Trust geekshackexpert @ f a s t s e r v i c e . C o m) (TeleGram.Trustgeekshackexpert)2 -
DIGITAL TECH GUARD RECOVERY - LOST CRYPTO RECOVERY PRO
WhatsApp: +1 (443) 859 - 2886
Email @ digital tech guard . com
Telegram: digital tech guard recovery . com
Website link: digital tech guard . com
folks, Digital Tech Guard Recovery works! I had entrusted someone who I thought I trusted with the contents of my wallet, and as soon as they altered my security settings behind my back, my $1,000,000 Bitcoin wallet was gone in mere seconds!!. My world had been turned round when I first understood that, not only was my trust misplaced, but the possibility also lay before me to lose all I had spent many years creating. In what else could be the darkest moment of mine, Digital Tech Guard Recovery approached like a light of hope.
Their understanding staff acknowledged the unique character of my loss and processed my case with the utmost sensitivity and professionalism available. They made clear and precise explanations of their recovery process from the start, relieving my escalating concern and regaining some degree of control for me. Their technical competence was apparent in an instant, as they reviewed each element of my compromised security settings in minute detail. Not only did they restore access to my wallet, but they also identified and patched vulnerabilities that might have led to future breaches.
Throughout the entire recovery process, I was continually impressed by the range of services they offered. Their state-of-the-art recovery techniques, combined with round-the-clock technical support, ensured that I was never left in the dark. In addition to getting my wallet back, Digital Tech Guard Recovery also provided me with very valuable advice on how to protect myself further online. They provided me with expert advice, suggesting robust backup practices, multi-factor authentication, and advanced-level encryption methods to protect my wallet against future hacks. Their focus on customer education was unveiled in the comprehensive security manual that they presented to me. This is now an essential part of my arsenal online.
Each update I received was timely and reassuring, making me even more confident in their ability. Digital Tech Guard Recovery turned what could have been an agonizing betrayal into a story of hope, resilience, and technological expertise. With my $1,000,000 Bitcoin wallet recovered in full, I am now safer than ever. I wholeheartedly recommend Digital Tech Guard Recovery to anyone having an emergency with their online assets; not only recovered my money but also taught me how to make my financial future secure. They went the extra mile for my service.1 -
Hi, I was a victim of a crypto theft involving a Pink Drainer, which resulted in the theft of my Wrapped Bitcoin (WBTC) from my Polygon network. The experience was incredibly frustrating and distressing, as I had no idea how to recover my funds. Unfortunately, by the time I noticed the theft, the funds had already been drained to an address that I had no control over, making it seem like an irreversible situation.The attack happened when I clicked on what appeared to be a legitimate link. I didn’t realize at the time that it was a phishing attempt designed to siphon off my private keys and access my wallet. The Pink Drainer, a type of malicious script used by attackers, is specifically designed to exploit such vulnerabilities in crypto wallets. The moment I realized that my WBTC had been drained from my Polygon network, I felt completely helpless, as I didn’t have direct access to the thief's address, and there was no way to reverse the transaction on my own.At that point, I started searching for ways to recover my funds, but most resources only offered generic advice that wasn’t practical in this particular case. I quickly realized that if I wanted to have any hope of getting my assets back, I would need professional assistance. After some research, I came across a reliable and trusted recovery team called Hack Savvy Tech. Their expertise in cryptocurrency recovery, especially in cases like mine, seemed promising.I decided to reach out to Hack Savvy Tech, and I’m incredibly grateful that I did. Their team of crypto recovery experts was able to help me trace the stolen funds and identify the path the funds took after they left my wallet. Using advanced tools and techniques, they were able to track the transactions on the blockchain, helping me understand where my WBTC had been sent. More importantly, they worked tirelessly to assist me in contacting the necessary parties and even interfaced with blockchain analysts to help facilitate the recovery process.Thanks to their efforts, I was able to successfully recover my stolen funds. The entire process took some time, but Hack Savvy Tech dedicated team provided regular updates and kept me informed throughout the process, which gave me a sense of hope and relief during an otherwise stressful time. If you’re ever in a similar situation, I highly recommend reaching out to a trusted recovery team like Hack Savvy Tech . Their professionalism, knowledge, and expertise were critical in helping me recover my funds and regain control of my crypto assets.
mail: contactus @ hacksavvytechnology . com
Website: https : // hacksavvytechrecovery . com
Whatsapp : +799982950387 -
THE BEST CRYPTO RECOVERY SERVICES, HIRE DIGITAL TECH GUARD RECOVERY
On a frigid, rainy evening, I experienced a nightmare: I discovered that my $26,000 worth of Bitcoin had been stolen. The emotional and financial shock was overwhelming. I had trusted the security of my digital assets, and now, in the blink of an eye, everything was gone. In my panic and desperation, I began searching for recovery services. However, most of the options I found either seemed dubious or offered no real guarantees. That’s when I came across Digital Tech Guard Recovery. It was a company recommended in a Facebook community I had been following, and the reviews were overwhelmingly positive. What struck me most was the company’s reputation for professionalism and expertise. I decided to reach out to them and, from the very first interaction, I knew I had made the right choice. The team at Digital Tech Guard Recovery
contact with WhatsApp: +1 (443) 859 - 2886 Email @ digital tech guard . com
Telegram : digital tech guard recovery . com website link : digital tech guard . com
immediately put me at ease. They were responsive, compassionate, and professional. They listened to my situation in detail and assured me that they would do everything in their power to recover my stolen Bitcoin. Their approach was methodical and thorough. They began by gathering all relevant information, including transaction records and wallet addresses, which was then used to launch an in-depth investigation. What impressed me most was their use of advanced blockchain tools and their deep understanding of the technology behind cryptocurrency. They didn’t just offer vague promises; they immediately started tracing the stolen funds through the blockchain, using cutting-edge techniques to track down the criminals. Over the course of several weeks, I received regular updates on their progress. It was clear that they were working tirelessly, and I began to feel a sense of hope that I hadn’t experienced since the theft. Despite the complexity of the situation, their expertise and persistence paid off. After weeks of relentless effort, they successfully recovered my Bitcoin. The moment I received confirmation that my funds had been restored, I felt an overwhelming sense of relief and gratitude. Beyond the recovery of my financial assets, Digital Tech Guard Recovery also educated me on how to better protect my digital investments in the future. They provided valuable lessons in cybersecurity and helped me understand the vulnerabilities that led to the hack. I am incredibly grateful for their dedication and the peace of mind they restored in my life. If you ever find yourself in a similar situation, I cannot recommend Digital Tech Guard Recovery enough.1 -
I never imagined I would fall victim to an online scam, but that’s exactly what happened. It started innocently enough. I was on a popular social media platform, browsing through posts when I received a direct message from someone claiming to be a “financial expert.” Their pitch seemed solid, and their promises of quick returns on investments seemed too good to pass up. I did my research—or so I thought—but it wasn’t long before my trust led me into a trap. I made an initial deposit to start the investment, and things moved quickly. The first few days were filled with regular updates and even small returns, which convinced me that I was onto something big. But then, the messages started to change. The returns began to slow down, and when I tried to withdraw my funds, I couldn’t get a response. Panic set in as I realized I’d been scammed. i had lost a significant amount of money, and to make matters worse, the scammers had control over my personal details, including access to some of my financial accounts. Desperate for a solution, I turned to Alpha Spy Nest, a cybersecurity service I had heard of through a friend.From the moment I contacted Alpha Spy Nest, I knew I had made the right choice. They took swift action, immediately conducting a thorough investigation into my digital accounts. They discovered that the scammer had used several techniques to track my online activity, intercept communications, and even mimic legitimate financial websites. Alpha Spy Nest’s team of experts worked tirelessly to gather evidence, trace the scammer’s digital footprint, and recover my lost funds.But it didn’t stop there. Alpha Spy Nest helped me secure my online presence by identifying vulnerabilities in my accounts and recommending tools to fortify my digital defenses. They guided me through implementing multi-factor authentication, strengthened my passwords, and even educated me on how to spot future scams.Within days, they were able to trace the scammer’s digital identity, and with the evidence they provided, law enforcement was able to step in. I regained access to my financial accounts and received a refund of the funds that were stolen, though the emotional toll remained.The experience left me shaken, but Alpha Spy Nest’s professional and supportive team helped me not only reclaim my wealth but also regain my peace of mind. Now, I’m more cautious online, but I know I have the right tools and the right support if anything ever happens again.Thanks to Alpha Spy Nest, I’m no longer a victim. I’m a survivor. You can also reach out to them WhatsApp: +14159714490
 1
1 -
SEEKING HELP TO RECOVER STOLEN CRYPTOCURRENCIES HIRE ADWARE RECOVERY SPECIALIST
The world of cryptocurrency, with its promise of financial freedom and innovation, had always fascinated me—until it became the backdrop of my most painful financial loss. WhatsApp info:+12 (72332)—8343
Last year, I fell victim to a sophisticated crypto scam disguised as a “guaranteed returns” investment opportunity. What started as a confident leap into passive income quickly spiraled into disaster. In a matter of hours, years of savings vanished, along with the anonymous scammers behind it. I was left with nothing but shock, shame, and a haunting sense of betrayal.
I couldn’t stop replaying every step—every red flag I’d missed, every decision I questioned too late. Crypto forums were filled with similar heartbreaking stories, yet few offered solutions. I was beginning to lose hope.
That’s when I discovered ADWARE RECOVERY SPECIALIST.
From our very first interaction, I knew they were different. Their team combined deep technical expertise with genuine empathy—something I hadn’t expected. I wasn’t just another case number to them; they truly listened, offering reassurance that helped ease my self-blame. As one advisor told me, “These scams exploit trust, not incompetence.” That perspective changed everything.
Their forensic work in the crypto space was remarkable. They unraveled the web of how my funds were siphoned—identifying vulnerabilities in wallets and tracking the fraudsters through decentralized exchanges. Using proprietary tools and cross-platform partnerships, they followed the trail with a level of precision that inspired real hope. Telegram info: h t t p s:// t. me / adware recovery specialist1
The process wasn’t easy. There were dead ends, unresponsive platforms, and technical roadblocks. But ADWARE RECOVERY SPECIALIST never wavered. By the second day, they had already recovered $350,000 of my lost assets.
But their support didn’t stop at recovery. They empowered me—educating me on how to protect future investments, and even connecting me with a private community of other scam survivors. That network gave me strength and perspective. Email info: Adware Recovery Specialist @ auctioneer. net
Today, I’m not only financially restored, but emotionally grounded. My experience stands as proof that recovery is possible—even in the murky world of crypto scams. With the right team, the right tools, and relentless dedication, there is a way back. Website info: h t t p s:// adware recovery specialist. com
If you’ve been scammed, know this: you are not alone. There is hope. ADWARE RECOVERY SPECIALIST helped me reclaim more than just money—they helped me reclaim peace of mind.2 -
BEST CRYPTOCURRENCY RECOVERY COMPANY - GO TO DIGITAL TECH GUARD RECOVERY HACKER
WhatsApp: +1 (443) 859 - 2886
Email @ digital tech guard . com
Telegram: digital tech guard . com
Website link: digital tech guard . com
The digital illusion emerged in February through an intricately fabricated Facebook persona, a supposed cryptocurrency guru flaunting opulent estates and glowing testimonials from “investors” basking in fabricated riches. Enticed by the allure of portfolio diversification, I engaged the profile, unaware of the deception that lay ahead. This individual, a master manipulator, spent weeks cultivating trust. They bombarded me with sleek marketing materials for a “cloud-based mining operation,” complete with counterfeit revenue graphs and forged regulatory certificates. Their pitch, a seamless blend of industry jargon and fabricated urgency, eroded my skepticism. I finally transferred an initial $15,000. Soon, the platform’s dashboard reflected impressive returns and even allowed a $2,500 withdrawal a calculated move to lull me into complacency. Encouraged, I invested an additional $75,000 over the next three weeks. Disaster struck when I attempted a larger transfer . The platform began rejecting my requests, citing vague “liquidity fees” and unverifiable fiscal requirements. Then, the scammer disappeared, erasing all traces. A blockchain audit confirmed my worst fear: the entire interface had been a mirage. My investments had been siphoned off and scattered across untraceable accounts or so I thought. Searching for help, I combed through online communities searching for a path forward. I eventually discovered Digital Tech Guard Recovery, a group of hackers who recover cryptocurrency through cyber forensics and deep crypto analysis. Their reputation, reinforced by detailed investigative reports and positive case outcomes, gave me hope. From the moment I contacted them, Digital Tech Guard Recovery approached my case with precision and professionalism. They explained how sophisticated scams exploit non-custodial wallet vulnerabilities and fake API integrations to siphon funds into crypto tumblers, concealing the trail. Using advanced tracing protocols and proprietary forensic tools, Digital Tech Guard Recovery tracked the movement of my stolen Bitcoin through a web of anonymized wallets, eventually locating the funds at an offshore exchange notorious for weak compliance. With cryptographic evidence in hand and coordination with international legal teams, Digital Tech Guard Recovery secured an emergency freeze on the assets. Within 48 hours, my funds were returned to a secure cold wallet. This was a harsh education in the dark side of digital finance. Thanks to Digital Tech Guard Recovery, I reclaimed what was lost. Now, I navigate crypto with vigilance, knowing that caution is the only true safeguard in a world where deception often wears a digital face.1 -
IS Technology: Your Trusted Partner for Small Business Support and IT Services
In the modern business landscape, technology plays a crucial role in driving efficiency and success. For small businesses, managing technology and staying ahead of IT challenges can be overwhelming. At IS Technology, we are here to provide expert small business support and IT services to help your business thrive. Located at 12 National Ave, Fletcher, NC 28732, we offer tailored solutions designed to meet the unique needs of small businesses, enabling you to focus on what matters most—growing your business.
Why Small Businesses Need IT Support
Small businesses often face unique challenges when it comes to technology. With limited resources, it’s crucial to make the most of your technology infrastructure while minimizing downtime and security risks. IS Technology specializes in providing small business support that empowers your company to run efficiently, securely, and seamlessly. Our IT services are designed to help you:
Reduce IT Costs
Outsourcing your IT services to a trusted provider like IS Technology can save your business significant costs compared to hiring a full-time, in-house IT team. With our flexible support packages, you only pay for the services you need, when you need them.
Stay Competitive
In today’s digital-first world, small businesses need to leverage the latest technology to remain competitive. Whether it's cloud computing, advanced cybersecurity, or efficient networking, we provide the tools and expertise you need to stay ahead of the curve.
Improve Efficiency
Technology should simplify your business operations, not complicate them. Our small business support services ensure that your IT services are optimized for maximum productivity, reducing downtime and streamlining your workflows.
Enhance Security
Cybersecurity is critical for small businesses that handle sensitive customer data and financial information. IS Technology offers robust security solutions that protect your business from potential threats, ensuring that your information is safe and your systems are secure.
Our IT Services: Tailored for Small Businesses
At IS Technology, we offer a wide range of IT services specifically designed to meet the needs of small businesses. Whether you’re looking for a comprehensive IT support package or specialized services, we have the expertise to provide solutions that fit your business requirements.
Managed IT Services
Our managed IT services are designed to provide proactive support, ensuring that your systems are running smoothly 24/7. From regular software updates to monitoring your network for potential issues, we handle everything so you can focus on growing your business.
Network Setup & Support
A strong, reliable network is essential for business success. We provide network setup and support to ensure that your business's technology infrastructure is seamless and scalable. Whether you need help setting up a new office network or optimizing your existing setup, we’ve got you covered.
Cloud Solutions
Cloud computing offers flexibility and cost savings that traditional IT infrastructure simply can’t match. We provide cloud solutions that allow you to store and access your data securely from anywhere. With our help, your small business can benefit from enhanced collaboration, seamless data sharing, and reliable disaster recovery.
Cybersecurity Services
Small businesses are often targets for cybercriminals due to their perceived vulnerabilities. At IS Technology, we provide advanced cybersecurity services to safeguard your business against cyber threats. Our services include firewalls, antivirus software, encryption, and security audits to protect your data and systems from potential breaches.
Tech Support & Troubleshooting
When technical issues arise, you need reliable tech support to minimize downtime. Our team is available to troubleshoot problems quickly and efficiently, ensuring your business is back on track in no time. Whether it’s hardware malfunctions or software issues, we’re here to help.
IT Consulting
As a small business, you might not always know which technology solutions are best for your needs. Our IT consulting services provide expert guidance to help you make informed decisions about your technology investments. Whether you need advice on upgrading your infrastructure or choosing the right software for your business, we offer tailored recommendations that align with your goals.
Why Choose IS Technology for Small Business Support?
Tailored Solutions for Your Business
At IS Technology, we understand that every small business is different. That’s why we provide small business support that is customized to meet the specific needs of your business. We take the time to understand your goals and challenges, and we design IT services that align with your objectives5 -
HIRE A HACKER TO RECOVER STOLEN BITCOIN HIRE ADWARE RECOVERY SPECIALIST
Email info: Adwarerecoveryspecialist@auctioneer. net
WhatsApp info:+12 723 328 343
As a journalist committed to uncovering the truth, I often emphasize the importance of vigilance in the digital age. Unfortunately, I found myself on the wrong side of a cryptocurrency scam that resulted in a staggering loss of €60,000. This experience not only tested my financial resilience but also my faith in the systems designed to protect individuals from fraud. After discovering the scam, I promptly filed a report with the police. Initially, I felt a sense of relief, believing that justice would be served. However, as days turned into weeks, I grew increasingly discouraged. The lack of progress from law enforcement was disheartening, leaving me to grapple with feelings of helplessness. It became clear that the complex and often elusive nature of cryptocurrency scams made them challenging to investigate, even for experienced authorities. During this tumultuous time, a fellow journalist reached out with a recommendation for ADWARE RECOVERY SPECIALIST. Skeptical yet desperate to recover my lost funds, I decided to contact them. From the moment I reached out, I was struck by their professionalism and understanding. The team at ADWARE RECOVERY SPECIALIST took the time to listen to my story, validating my feelings of frustration and loss. They explained their process clearly, setting realistic expectations while ensuring I felt supported throughout. What stood out most was their commitment to transparency. I received regular updates on the recovery process, which helped alleviate some of my anxiety. The team was proactive in their approach, employing various strategies to trace and recover my lost funds. It was refreshing to work with individuals who were not only knowledgeable but also genuinely empathetic to my situation. To my astonishment, ADWARE RECOVERY SPECIALIST successfully recovered a significant portion of my funds. The relief and gratitude I felt were overwhelming; I had not only regained part of my financial stability but also my trust in the recovery process. This experience underscored the importance of seeking help from specialized professionals when faced with the complexities of fraud my journey through this ordeal has been both a cautionary tale and a lesson in resilience. It highlighted the vulnerabilities that many face in the evolving landscape of digital finance. For anyone who finds themselves in a similar predicament, I cannot recommend ADWARE RECOVERY SPECIALIST highly enough. Their dedication and expertise made a daunting situation manageable and ultimately successful. In a world where scams are all too common, it’s crucial to remain vigilant and informed. I’ve learned that seeking help from the right resources can make all the difference, and I’m grateful to have found ADWARE RECOVERY SPECIALIST in my time of need. -
SCANNER HACKER CRYPTO RECOVERY: A Strategic Approach to Digital Asset Recovery
In the rapidly evolving landscape of cryptocurrency, the prominence of digital assets has led to an accompanying rise in incidents of loss, theft, and fraud. As individuals and businesses increasingly navigate the complexities of decentralized finance, the need for effective recovery solutions becomes paramount. SCANNER HACKER CRYPTO RECOVERY emerges as a notable player in this domain, offering a suite of services aimed at recovering lost or stolen cryptocurrencies. This essay outlines the importance of such recovery services, evaluates the effectiveness of SCANNER HACKER’s operations, and proposes recommendations for enhancing their offerings and outreach.
The burgeoning cryptocurrency market presents unique challenges, particularly concerning security vulnerabilities that may expose individuals to significant losses. SCANNER HACKER CRYPTO RECOVERY specializes in identifying and retrieving lost assets, leveraging advanced technological solutions and skilled personnel to trace transactions across blockchain networks. Their expertise in forensics, coupled with knowledge of legal regulations regarding digital assets, facilitates a comprehensive approach to recovery that is both proactive and reactive. The efficacy of SCANNER HACKER’s solutions is underscored by a track record of successfully recovering assets for numerous clients, which reinforces their credibility in the marketplace.
Despite their commendable achievements, SCANNER HACKER CRYPTO RECOVERY can enhance their effectiveness through several strategic implementations. First, improving transparency in the recovery process can foster trust among potential clients, who may be wary of the opaque mechanisms often associated with illicit activities in the cryptocurrency space. By offering detailed case studies and transparent methodologies that outline recovery procedures, the firm can demystify the recovery process and provide reassurance. Furthermore, investing in educational resources that empower users to protect their assets before incidents occur—through workshops, webinars, and informational content—can not only position SCANNER HACKER as a thought leader but also mitigate risk within the community.
Additionally, expanding collaborative efforts with cryptocurrency exchanges, wallets, and law enforcement agencies can enhance the efficacy of recovery operations. By establishing partnerships, SCANNER HACKER could streamline the reporting and recovery process, allowing for a more coordinated response to incidents of theft or loss. Engaging in advocacy for better safety regulations within the cryptocurrency market would further solidify their role as a pacesetter in digital asset security and recovery. In summary, while SCANNER HACKER CRYPTO RECOVERY has made significant strides in addressing the urgent need for crypto asset recovery, an emphasis on transparency, education, and strategic partnerships could enhance their service delivery and foster greater trust within the digital currency ecosystem.2 -
APM BILLING: Providing HIPAA-Compliant Billing Services You Can Trust
In today’s healthcare landscape, maintaining patient privacy and data security is paramount. Healthcare providers must adhere to strict standards to protect sensitive information while ensuring that financial operations are smooth and efficient. APM BILLING, based in Philadelphia, Pennsylvania, is dedicated to providing HIPAA-compliant billing services that ensure the highest level of security and compliance, while also optimizing the billing process for healthcare providers.
What Are HIPAA-Compliant Billing Services?
HIPAA (Health Insurance Portability and Accountability Act) establishes strict rules to ensure that healthcare providers maintain patient privacy and the confidentiality of their health information. As part of our commitment to protecting patient data, APM BILLING offers HIPAA-compliant billing services that meet all of the requirements set forth by this regulation.
Our HIPAA-compliant billing services ensure that all personal health information (PHI) handled during the billing and claims process remains secure. From data encryption to secure transmission, we follow the highest security standards to prevent unauthorized access, breaches, and other vulnerabilities.
Why Is HIPAA Compliance Critical for Healthcare Billing?
For any healthcare business, staying HIPAA-compliant is not just a regulatory necessity—it's essential to maintaining trust with patients and avoiding costly penalties. Non-compliance can result in hefty fines, lawsuits, and damage to your reputation. When it comes to billing, ensuring that all processes follow HIPAA guidelines is critical in preventing unauthorized access to sensitive patient data.
APM BILLING takes privacy and security seriously. Our team is well-versed in all HIPAA regulations, so you can trust that your patient data is always protected. We integrate comprehensive security protocols into our billing workflows, including:
Encrypted communications for all patient data exchanges
Secure data storage that meets HIPAA standards
Audit trails to track access to patient information and billing details
Employee training to ensure that everyone handling sensitive data understands HIPAA guidelines
The Benefits of Working with APM BILLING for HIPAA-Compliant Billing Services
By choosing APM BILLING, you gain the peace of mind that comes with knowing your billing processes are in full compliance with HIPAA regulations. Here are some of the key benefits of our HIPAA-compliant billing services:
Data Security: We use the latest technology to protect patient information, ensuring that all billing data is securely transmitted and stored.
Regulatory Compliance: Our team stays up-to-date with the latest changes to HIPAA regulations, ensuring that your practice remains compliant with all legal requirements.
Reduced Risk of Penalties: HIPAA violations can lead to significant fines and penalties. By outsourcing your billing to APM BILLING, you minimize the risk of compliance issues and the associated costs.
Enhanced Trust: Patients trust healthcare providers to keep their personal and medical information safe. By using our HIPAA-compliant billing services, you show your commitment to maintaining privacy, which fosters trust and enhances your reputation.
Efficiency and Accuracy: In addition to security, we ensure that your billing processes are efficient and accurate, leading to faster claim submissions, reduced denials, and increased revenue.
Why Choose APM BILLING for HIPAA-Compliant Billing Services?
Expertise: Our experienced team is dedicated to ensuring that all of your billing practices comply with HIPAA guidelines.
Tailored Solutions: We offer customized solutions that meet the specific needs of your healthcare practice, whether you’re a clinic, provider, or specialty office.
Focus on Security: We take security seriously and use state-of-the-art systems to protect all sensitive information.
Reliable Support: With APM BILLING, you’ll have a trusted partner in billing that is committed to safeguarding your practice’s financial and data integrity.
Get Started with APM BILLING Today
At APM BILLING, we understand the importance of maintaining HIPAA-compliant billing services in today's healthcare environment. We are here to help your practice stay secure, compliant, and financially efficient.
Contact us today at +1-800-621-3354 to learn more about how we can help streamline your billing process while ensuring complete protection of patient data. Visit our office at 19104 Philadelphia, Pennsylvania, and let APM BILLING handle your billing needs with the utmost professionalism and care.
Let APM BILLING take the stress out of billing while keeping your practice compliant with HIPAA regulations, so you can focus on what matters most—caring for your patients.2 -
American Alliance Security Agency: The Best Security Company in New Hampshire
When it comes to securing your business, home, or special event, you deserve nothing less than the best. At American Alliance Security Agency, we proudly stand as the best security company in New Hampshire, offering comprehensive, tailored security solutions that give you peace of mind. With a team of experienced professionals and a dedication to providing top-tier protection, we are committed to safeguarding your property and loved ones with the highest level of care.
Why American Alliance Security Agency is the Best Security Company in New Hampshire
At American Alliance Security Agency, we understand that security isn’t just about protecting assets—it’s about providing a sense of safety and assurance. Here’s why we are considered the best security company in New Hampshire:
Experienced and Professional Team: Our security personnel are highly trained, with years of experience in handling a wide range of security situations. From managing crowds at large events to providing on-site protection for businesses, our team is equipped to handle any challenge.
Comprehensive Security Services: We offer a wide range of security services to meet the diverse needs of our clients. Whether you need on-site security guards, CCTV monitoring, event security, access control management, or fire watch services, we have you covered.
Tailored Security Solutions: We recognize that no two properties or events are the same. That’s why we offer personalized security plans designed to address the specific needs of your business, home, or special event. We assess potential risks and create a customized strategy to provide maximum protection.
24/7 Availability: Security is a constant concern, and that’s why we offer round-the-clock service. Whether you need surveillance at night, emergency response during the day, or full-time protection, we are always ready to respond to your needs.
Commitment to Excellence: Our commitment to excellence means that we never cut corners when it comes to the security of your property or loved ones. We continually invest in the latest technology, training, and systems to ensure we remain the best security company in New Hampshire.
Our Range of Security Services
At American Alliance Security Agency, we offer a comprehensive range of services designed to protect your assets and ensure the safety of those around you. Here are just a few of the security services that set us apart:
Security Guard Services: Whether you need armed or unarmed security, we provide professional security guards who are highly trained to protect your property, manage security risks, and respond quickly to incidents.
Event Security: From concerts and festivals to corporate events and private parties, we provide event security services to ensure smooth operations, crowd control, and the safety of all attendees.
CCTV Monitoring: Our CCTV monitoring services provide real-time surveillance and continuous monitoring of your property. Whether you need to monitor your retail store, office, or home, our security team is ready to watch for suspicious activity and respond swiftly.
Risk Assessment: We conduct thorough risk assessments to evaluate your property or business's security vulnerabilities. By identifying potential threats, we help you implement preventive measures to protect your assets, employees, and clients.
Access Control Management: Our access control solutions allow you to manage who enters your property, ensuring only authorized individuals have access to restricted areas.
Fire Watch Services: We offer specialized fire watch services to monitor sites at risk of fire hazards. Whether it’s a construction site, industrial facility, or large event, we ensure that fire safety protocols are being followed.
Mobile Patrols: Our mobile patrol services offer dynamic security coverage for large properties or multiple locations. We provide random, scheduled patrols to ensure comprehensive security and deter any criminal activity.
Why We Are the Best Security Company in New Hampshire
Choosing American Alliance Security Agency means choosing the best in the business. Here’s why:
Proven Track Record: We have a proven track record of successfully protecting properties, businesses, and events in New Hampshire. Our clients trust us to provide reliable, professional security services that meet their unique needs.
Advanced Technology: We stay ahead of the curve by investing in the latest security technology, such as surveillance cameras, alarm systems, and access control systems, ensuring that our services are efficient, effective, and up to date.1 -
How to Hire a Trusted Cryptocurrency Recovery Expert/Hack Savvy Tech
I initially learned about the Bitcoin world on a chilly, rainy evening. Although I had heard rumors of this digital revolution, I wasn't too enthralled with it until a friend showed me Ethereum. The prospect of a transparent, safe, and decentralized financial system was enticing, so I jumped right into the blockchain technology realm. With a newfound enthusiasm, I began investing in Ethereum, carefully researching the market and making strategic decisions. The initial months were filled with excitement as I watched my portfolio grow, and I couldn't help but feel a sense of pride in my newfound financial acumen. However, my elation was short-lived. One fateful day, I received a call from a supposed "financial advisor" who claimed to have a foolproof investment opportunity. Blinded by greed and the promise of quick returns, I trusted this individual and transferred a significant portion of my Ethereum holdings to their "secure" wallet. It wasn't until days later that I realized I had been the victim of a sophisticated scam. My Ethereum was gone, vanished into the ether, and I was left feeling devastated, betrayed, and utterly helpless. In the aftermath of this devastating loss, I found myself in a state of despair. I had poured countless hours and a substantial amount of my savings into building this portfolio, and now it had all been snatched away. The emotional toll was overwhelming, and I struggled to come to terms with the reality of my situation. While struggling with the fallout from the scam, I came across Hack Savvy Tech website, which specializes in recovering stolen or lost cryptocurrency. I initially doubted that they could actually assist me in getting back what I had lost. But since I couldn't see any other workable possibilities, I made the decision to contact them and ask for help. The Hack Savvy Tech staff was kind and understanding, and they got to work on my case right away. They paid close attention to what I had to say, examined the specifics of the loss, and came up with a thorough plan to find the stolen Ethereum and start the recovery procedure. What followed was a meticulous and painstaking investigation, as the Hack Savvy Tech team delved into the complex world of blockchain forensics. They utilized advanced analytical tools and techniques to trace the movement of the stolen funds, navigating the labyrinth of digital wallets and exchanges in pursuit of my lost Ethereum. The process was not without its challenges. There were moments of frustration and uncertainty, as the trail often seemed to go cold or lead to dead ends. But the Hack Savvy Tech team remained steadfast, driven by a determination to see justice served and to restore what had been taken from me. The moment I received the news that my Ethereum had been located and was in the process of being returned to me was one of pure elation. It was as if a weight had been lifted from my shoulders, and I could finally breathe a sigh of relief. The emotional rollercoaster I had endured had been worth it, and I was grateful beyond measure for the dedication and skill of the Hack Savvy Tech team. As the funds were gradually repatriated, I couldn't help but reflect on the lessons I had learned throughout this ordeal. The experience had been a harsh reminder of the risks and vulnerabilities inherent in the world of cryptocurrency, and it had taught me the importance of exercising caution and diligence when it comes to my financial investments. Visit their website via:
mail: contactus @ hacksavvytechnology . com
Website: https: // hacksavvytechrecovery . com
Whatsapp : +7.9.9.9.8.2.9.5.0.3.813 -
HOW TO HIRE A HACKER TO RECOVER SCAMMED CRYPTO HIRE ADWARE RECOVERY SPECIALIST
The journey towards recovering lost or stolen cryptocurrency can often feel like a perilous trial, fraught with uncertainty and the ever-present risk of falling victim to malicious scams. Website info: https ://adware recovery specialist. com
This was the experience I faced when I found myself in the midst of an Ethereum (ETH) recovery ordeal, navigating a maze of false promises and deceptive tactics. WhatsApp info:+12723 328 343
Just when hope seemed to dwindle, a glimmer of light emerged in the form of ADWARE RECOVERY SPECIALIST, a service that would prove instrumental in guiding me through the treacherous waters of crypto recovery. What began as a straightforward attempt to reclaim my rightful ETH holdings quickly descended into a disheartening encounter with a sophisticated hoax. Seemingly legitimate recovery "experts" emerged from the shadows, offering their services and assurances of a swift and successful resolution. Lured by their convincing rhetoric and the prospect of regaining my lost assets, I entrusted them with sensitive information, only to watch helplessly as they vanished into the digital ether, taking my ETH with them. Email info: Adwarerecoveryspecialist@ auctioneer. net The emotional toll of this betrayal was immense, as I grappled with the realization that my efforts had been thwarted by unscrupulous individuals exploiting the vulnerabilities of the crypto landscape. Just when I had resigned myself to the possibility of a permanent loss, I discovered ADWARE RECOVERY SPECIALIST, a service that would ultimately prove to be my salvation. Unlike the charlatan recovery "experts" I had encountered, ADWARE RECOVERY SPECIALIST approached my case with a level of professionalism, empathy, and unwavering commitment that restored my faith in the recovery process. Through their meticulous investigations, cutting-edge techniques, and dogged determination, they were able to trace the path of my stolen ETH and orchestrate its safe return to my rightful possession. The trial of recovery had been arduous, marked by setbacks and the constant threat of further exploitation. Yet, with the steadfast support of ADWARE RECOVERY SPECIALIST, I emerged from this ordeal with a renewed appreciation for the resilience of the human spirit and the power of legitimate, ethical service providers to navigate the complex and often treacherous world of cryptocurrency recovery. Telegram info: https ://t.me/adware recovery specialist1 This experience has forever shaped my understanding of the crypto ecosystem and the importance of exercising caution and discernment when seeking assistance in such matters. To anyone facing the same heart-wrenching situation, don't waste any more time or money on companies that are only interested in making empty promises. ADWARE RECOVERY SPECIALIST stands as a beacon of professionalism in a field often riddled with scams. Their efforts are genuine, their expertise is unmatched, and their results speak for themselves. Thanks to them, my ETH is back where it belongs, and I couldn’t be more grateful.2 -
These days you have to be very careful about who you contact for Funds Recovery because most of these companies out there who claim they are funds recovery experts are not really who they claim they are, they are out there to Rip people Off, Trust Me You Don’t want a Risk It. You Can Always Identify Them With Their False Advertisements and False Testimonies Trying To Lure you Into their Arms, And most of them use Yahoo mail, gmails, and other cheap email providers which could easily expose their vulnerabilities, Please Don’t Fall For Them🚷 Come To Think Of It, Why would a Legit firm Be using a Gmail or a cheap email provider that exposes their vulnerabilities????⚠️⚠️⚠️ If you’ve had encounters with these guys, you’d appreciate this Write up.
⚫️ Truth be told, the only organization capable of retrieving your lost funds from online scams, Bitcoin Scam, Crypto Scam, scam investment websites, etc., are Team of PROFESSIONAL HACKERS & CYBER FORENSIC EXPERTS, they are the ones who know various Retrieval Techniques and Strategies that suit different scenarios of Funds Retrieval such as Bitcoin retrieval, investment scam retrieval, crypto Trading scam retrieval and so on. If you are smart enough, you should know that online scam recovery is a very Professional Case that requires Professional Handling by EXPERTS in the field. If You inquire about Brigadia Tech Remikeable Funds Recovery Services, Then You have to take a SMART step by consulting the Leading Team of Highly Ranked Hackers and Certified Cyber Forensic Experts At BRIGADIA TECH REMIKEABLE HACKERS. REACH OUT TO THEM WITH THE BELOW DIRECT CONTACT:
(Brigadiatechremikeable@Proton.Me)
Telegram +132391016053 -
HOW TO HIRE A HACKER TO RECOVER STOLEN BITCOIN HIRE ADWARE RECOVERY SPECIALIST
WhatsApp info:+12723 328 343
Got involved in a nightmare scenario where I lost a significant amount of cryptocurrency funds I had carefully invested over time. The loss came as a result of a combination of poor security practices and an unfortunate hack. To make matters worse, my girlfriend, who was also involved in the investment, was equally devastated when she realized the funds were gone. We were both completely helpless, with no idea how to recover what we had lost. The cryptocurrency was simply gone, and the frustration and panic were overwhelming. In my search for a solution, I stumbled upon ADWARE RECOVERY SPECIALIST. They specialize in helping people recover lost or stolen cryptocurrency, and after reading a number of positive reviews and testimonials, I decided to reach out. At first, I was doubtful after all, the nature of cryptocurrency transactions makes it notoriously difficult to recover lost assets. But ADWARE RECOVERY SPECIALIST reputation for successfully dealing with these types of cases was too good to ignore. From the moment I contacted them, I knew I had made the right choice. The team at ADWARE RECOVERY SPECIALIST was not only highly professional but also incredibly knowledgeable about the intricacies of blockchain and cryptocurrency. They understood exactly what had happened and laid out a clear, step-by-step plan for how they could assist. They assured both me and my girlfriend that they had helped others in similar situations, and they would do everything in their power to get our funds back. They started by investigating the transactions, tracing the movement of the stolen funds, and checking for any vulnerabilities that could have been exploited in the hack. Throughout the process, they kept us informed, explaining each move they made, and making sure that both my girlfriend and I were comfortable with their approach. The results were nothing short of amazing. ADWARE RECOVERY SPECIALIST successfully recovered all of the lost cryptocurrency. They even transferred the funds into a new, secure wallet that was set up with robust security measures to ensure there would be no further issues. It was as though a huge weight had been lifted off our shoulders—we couldn’t believe it. We had both resigned ourselves to the loss, but ADWARE RECOVERY SPECIALIST turned everything around. This experience has taught me the importance of keeping my cryptocurrency investments secure, but more importantly, it showed me the incredible value of working with professionals like ADWARE RECOVERY SPECIALIST. If you find yourself in a similar situation whether it’s a hacked wallet, lost funds, or stolen cryptocurrency I highly recommend reaching out to ADWARE RECOVERY SPECIALIST. They helped me and my girlfriend recover our funds when we thought all hope was lost. Their expertise and dedication are second to none, and we will be forever grateful for their help. 5
5 -
POTENTIAL EXPERT IN RECOVERY LOST OR SCAMMED USDT & BTC – REACH OUT TO FUNDS RECLAIMER COMPANY
As I walked through the vibrant atmosphere of the "Blockchain Expo" carnival, I felt a mix of excitement and curiosity. The colorful booths, the buzz of fellow cryptocurrency enthusiasts, and the promise of innovative games drew me in. Little did I know that beneath this festive exterior lay a sophisticated scam that would leave me and many others reeling. One of the games that caught my eye was the "Win Bitcoin Ring Toss." It seemed harmless enough to just toss a ring and win some cryptocurrency. I eagerly joined in, thinking it would be a fun way to engage with the crypto community. However, as I played, I had no idea that the game was rigged. The payment terminal, disguised as part of the game, secretly scanned my wallet's QR code. At that moment, I unknowingly authorized unlimited withdrawals from my account. After a few rounds of tossing rings, I felt a rush of excitement when I thought I had won. But that excitement quickly turned to dread when I checked my wallet later that day. To my horror, I discovered that $1.8 million had been stolen from attendees like me. I felt a wave of disbelief wash over me. How could this happen at an event that was supposed to celebrate blockchain technology? I learned that I was not alone. Many others had fallen victim to this elaborate scheme. Thankfully, FUNDS RECLAIMER COMPANY stepped in. Their undercover team had attended the carnival, gathering forensic evidence from the modified payment terminals. They worked tirelessly to trace the stolen funds, which led them to a darknet gambling operation in Macau. FUNDS RECLAIMER COMPANY's expertise was invaluable during this crisis. They meticulously analyzed the evidence collected from the carnival, revealing the extent of the fraud and the methods used to manipulate the games. Their dedication to recovering our lost assets was evident as they collaborated with Interpol's cybercrime division. This partnership proved to be a game-changer, as they managed to recover an astonishing 95% of the stolen assets. As the recovery efforts unfolded, I felt a glimmer of hope. Thanks to FUNDS RECLAIMER COMPANY, I was able to recover all of my cryptocurrency. Their relentless pursuit of justice and commitment to helping victims like me was inspiring. I was grateful for their expertise, but the experience left me shaken. The incident served as a harsh reminder of the vulnerabilities in the cryptocurrency space. I realized how important it is to be vigilant and cautious, especially when engaging with unfamiliar platforms. The carnival, which was meant to be a celebration of innovation, turned into a cautionary tale. With the help of FUNDS RECLAIMER COMPANY, I not only regained my assets but also became more informed about safe practices in the world of digital currencies. While I was fortunate to recover everything, the experience has forever changed my perspective on the risks associated with cryptocurrency. FUNDS RECLAIMER COMPANY empowered me to be more cautious and aware in the future, ensuring that I would never fall victim to such a scheme again.
REACH OUT TO THEM ON THEIR INFO BELOW:
WhatsApp;; +1 (3 6 1) 2 5 0 - 4 1 1 03 -
CHANCES OF CRYPTO RECOVERY OPTIONS:USE SPARTAN TECH GROUP RETRIEVAL
WhatsApp:+1 (971) 4 8 7 - 3 5 3 8
Email: spartantech (@) cyberservices . com
Telegram:+1 (581) 2 8 6 - 8 0 9 2
For many individuals and businesses, the experience of financial loss, whether caused by cyberattacks, data breaches, or unforeseen events, can feel overwhelming and intimidating. The emotional and financial toll can be immense, leaving people uncertain of where to turn. In these challenging times, SPARTAN TECH GROUP RETRIEVAL offers a crucial lifeline, providing expert services that guide clients through the recovery process with both skill and compassion. At SPARTAN TECH GROUP RETRIEVAL, the team recognizes the profound impact financial loss can have on clients, not only in terms of their finances but also on their sense of security and well-being. Their highly trained professionals specialize in assessing the full extent of damage caused by various disruptions, carefully identifying the underlying issues and working to develop tailored recovery strategies. Whether the challenge involves restoring lost data, recovering compromised systems, or securing vulnerable networks, SPARTAN TECH GROUP RETRIEVAL utilizes the latest technology and industry best practices to restore both operational efficiency and peace of mind. Data loss can be a particularly devastating consequence of a cyberattack or system failure. In a world where information is the lifeblood of businesses, recovering lost or corrupted data is crucial to regaining normal operations. SPARTAN TECH GROUP RETRIEVAL’s experts employ advanced data recovery techniques to retrieve vital information, ensuring that clients do not suffer irreversible setbacks. By recovering valuable data, they allow businesses to continue their operations with minimal disruption. Beyond data recovery, SPARTAN TECH GROUP RETRIEVAL excels at restoring and securing compromised systems. After a breach or attack, the threat of future vulnerabilities looms large. The team’s cybersecurity experts take swift action to secure networks and systems, implementing robust protection measures to defend against future threats. Through a combination of proactive monitoring, vulnerability assessments, and real-time security solutions, SPARTAN TECH GROUP RETRIEVAL works tirelessly to ensure that businesses and individuals can rebuild trust and safeguard their digital assets for the long term. However, what truly distinguishes SPARTAN TECH GROUP RETRIEVAL is its unwavering commitment to client care. While the technical aspects of recovery are vital, the company understands the emotional strain that often accompanies financial loss. Their compassionate case managers offer much-needed emotional support and practical guidance, helping clients navigate both the logistical and psychological challenges they face. By addressing the emotional as well as the practical aspects of recovery, SPARTAN TECH GROUP RETRIEVAL ensures that clients feel understood and supported throughout the entire process. In the face of financial hardship, SPARTAN TECH GROUP RETRIEVAL is a trusted partner that combines technical expertise with empathy and dedication. Their holistic approach ensures that businesses and individuals can recover, rebuild, and emerge from financial challenges stronger, more secure, and better prepared for the future. 1
1 -
Get in Touch with them via info below
WhatsApp +12249352948
Email: chat@botnetcryptorecovery.info
My recent experience with B O T N E T C R Y P T O R E C O V E R Y has not only restored my faith in humanity but also reaffirmed my belief in the power of perseverance and compassion. As a seasoned doctor based in Atlanta, Georgia, I've encountered countless individuals who have fallen victim to online scams, their lives irrevocably altered by the devastating consequences of trusting the wrong entity with their personal and financial information. It was one such patient, suffering from Tinnitus, whose harrowing ordeal compelled me to seek out assistance from B O T N E T C R Y P T O R E C O V E R Y. From the moment I reached out to (chat@botnetcryptorecovery.info), I was met with professionalism, empathy, and unwavering dedication to righting the wrongs inflicted upon innocent victims. Their team, composed of cybersecurity experts and digital investigation specialists, wasted no time in assessing the situation and formulating a comprehensive strategy to recover my patient's lost funds. What truly sets B O T N E T C R Y P T O R E C O V E R Y apart is their genuine concern for their client's well-being. Despite being strangers to my patient and me, they approached our case with the same level of urgency and care as if it were their own loved one in distress. Their commitment to transparency and communication throughout the recovery process served as a beacon of hope during what would otherwise have been a dark and uncertain time. Beyond their technical prowess and strategic acumen, B O T N E T C R Y P T O R E C O V E R Y operates with integrity. They understand the importance of fostering trust and confidence in their clients, especially those who have been victimized by unscrupulous individuals preying on their vulnerabilities. Their emphasis on educating clients about the risks associated with online interactions underscores their dedication to not only resolving immediate crises but also preventing future harm. As someone who has dedicated her life to healing and protecting others, I cannot overstate the impact of B O T N E T C R Y P T O R E C O V E R Y intervention in my patient's life. Not only did they succeed in recovering over USD 69,000 in stolen funds, but they also restored a sense of hope and justice that had been shattered by deceit and exploitation. In an industry plagued by skepticism and doubt, B O T N E T C R Y P T O R E C O V E R Y stands as a beacon of integrity, compassion, and excellence. Their unwavering commitment to their client's well-being sets a standard for ethical conduct and professionalism that should be emulated by all who seek to make a positive difference in the world. I endorse B O T N E T C R Y P T O R E C O V E R Y to anyone who finds themselves ensnared in the tangled web of online scams and fraud. Their expertise, empathy, and integrity are unparalleled, making them a trusted ally in the fight against cybercrime. With B O T N E T C R Y P T O R E C O V E R Y by your side, there is justice, restitution, and ultimately, healing.2 -
Building Fortresses, not Firewalls: Ethical Hacking Meets Software Development
In the digital age, security is no longer an afterthought; it's the bedrock upon which our online world rests. Yet, traditional security measures often resemble fortresses – imposing, but vulnerable to unseen cracks and tunnels. To truly safeguard our systems, we need to think like the enemy, like the nimble figures scaling those walls: ethical hackers.
Enter the exciting realm of DevSecOps, where ethical hacking practices are woven into the very fabric of the software development lifecycle (SDLC). This proactive approach is akin to building castles with security in mind, each brick meticulously laid to withstand even the most cunning siege.
Why Ethical Hacking in SDLC?
Imagine developing a critical piece of software, only to discover a gaping security hole after launch. The damage could be catastrophic, exposing sensitive data and eroding trust. Ethical hacking flips this script. By integrating penetration testing, vulnerability assessments, and threat modeling throughout the SDLC, we proactively hunt for weaknesses before they can be exploited.
Think of it as a friendly sparring match, where the ethical hacker throws their best punches to expose vulnerabilities, allowing the development team to fortify the software's defenses. This constant testing and refining leads to robust, secure systems that can withstand real-world attacks.
Benefits of DevSecOps:
1. Reduced Costs and Risks: Early detection and patching of vulnerabilities are far cheaper than dealing with a full-blown data breach.
2. Improved Software Quality: Security becomes an inherent part of the development process, leading to more reliable and trustworthy software.
3. Enhanced Brand Reputation: Demonstrating a proactive approach to security builds trust with customers and stakeholders.
Putting it into Practice:
Integrating ethical hacking into the SDLC requires a cultural shift. Developers, security professionals, and testers need to work together seamlessly, sharing knowledge and fostering a collaborative environment. Here are some key practices:
1. Threat Modeling: Identify potential threats and attack vectors early in the development process.
2. Static and Dynamic Code Analysis: Use automated tools to detect vulnerabilities in code.
3. Penetration Testing: Simulate real-world attacks to uncover hidden weaknesses.
4. Security Awareness Training: Educate developers and other stakeholders about security best practices.
Tools of the Trade:
A plethora of tools empowers ethical hackers and security professionals in their quest for a more secure digital world. Some popular options include:
1. Kali Linux: A distribution packed with security tools for penetration testing.
2. Burp Suite: A web application security testing platform.
3. Metasploit: A framework for developing and executing exploit code.
4. Wireshark: A network traffic analyzer for identifying suspicious activity.
The Future of Security:
As technology evolves, so too must our security practices. DevSecOps, with its embrace of ethical hacking, is at the forefront of this evolution. By building security into the very fabric of software development, we can create a safer, more resilient digital world for everyone.
Remember, in the ongoing battle against cyber threats, ethical hackers are not the enemy; they are our allies, the architects of digital fortresses that stand strong against the shadows. So, let's embrace DevSecOps, sharpen our ethical hacking skills, and build a future where security is not just an afterthought, but a fundamental principle.
I encourage you to explore the world of DevSecOps and ethical hacking. Whether you're a seasoned developer or just starting your journey, there's always more to learn and contribute. Together, we can build a more secure digital future, one line of code and one vulnerability patch at a time.
Do you have any questions about DevSecOps or ethical hacking? Share your thoughts and experiences in the comments below! -
HOW CAN I RECOVER MY LOST BITCOIN LOST TO SCAM HIRE ADWARE RECOVERY SPECIALIST
Email info: Adwarerecoveryspecialist@auctioneer. net
WhatsApp info:+12 723 328 343
Many first-time Bitcoin investors find themselves falling victim to scams and fraudulent schemes. The cryptocurrency landscape is rife with misleading mining company websites and deceptive practices that can easily ensnare the unwary. As a newcomer to Bitcoin, you might feel overwhelmed and vulnerable, making it all too easy to be duped by these malicious actors. Unfortunately, many people have experienced the heartbreak of losing their investments, often to hackers who exploit vulnerabilities in wallets and exchanges. One such victim was myself. I had invested in Bitcoin with high hopes, but my experience quickly turned sour when I discovered that my blockchain wallet had been compromised. A group of cybercriminals, often referred to as “vicious rippers,” managed to access my account and steal 3 BTC. This loss was devastating, not just financially but also emotionally. I felt isolated and hopeless, unsure of how to regain what was taken from me. In the midst of my despair, I stumbled upon ADWARE RECOVERY SPECIALIST, a company that specializes in helping individuals recover stolen bitcoins. Their claims of a recovery success rate of up to 95% piqued my interest, but I was initially skeptical. However, desperate times called for desperate measures, so I decided to reach out to them for assistance. From the very first interaction, the team at ADWARE RECOVERY SPECIALIST demonstrated empathy. They guided me through the process step by step, ensuring that I understood what needed to be done to recover my lost Bitcoin. Their expertise in tracing stolen funds and navigating the complexities of cryptocurrency recovery was evident. With their help, I started to see a glimmer of hope. After several weeks of diligent effort, I was thrilled to receive confirmation that a portion of my stolen funds was being recovered. The experience was not only a testament to ADWARE RECOVERY SPECIALIST capabilities but also a reminder of the importance of vigilance in the cryptocurrency space. While my journey was fraught with challenges, the support I received helped restore not just my funds but also my faith in the community. If you find yourself in a similar situation, remember that recovery is possible. Seek out reputable recovery services and stay informed to protect your investments in this volatile landscape. -
Losing access to your cryptocurrency can be a devastating experience, whether due to forgotten passwords, hacking, scams, or technical errors. Fortunately, professional recovery services like BITCRACK RECOVERY EXPERTS specialize in retrieving lost or stolen crypto assets. If you’ve lost your Bitcoin or other cryptocurrencies, here’s how BITCRACK RECOVERY EXPERTS can help you recover your funds.
Why Choose BITCRACK RECOVERY EXPERTS?
BITCRACK RECOVERY EXPERTS is a trusted name in cryptocurrency recovery, offering advanced techniques to help victims of crypto theft, fraud, or accidental loss. Their team of blockchain forensic experts uses cutting-edge tools to trace transactions, identify wallet vulnerabilities, and recover inaccessible funds.
Services Offered by BITCRACK RECOVERY EXPERTS
Wallet Recovery – Regaining access to locked or lost crypto wallets.
Scam Investigation – Tracing stolen funds from fraudulent schemes.
Phishing & Hacking Recovery – Recovering crypto lost to cyberattacks.
Private Key Retrieval – Helping users restore lost or corrupted private keys.
Exchange & ICO Scam Recovery – Assisting victims of fake investment platforms.
Steps to Recover Your Lost Cryptocurrency
1. Contact BITCRACK RECOVERY EXPERTS
Reach out to their support team via email:
📧 bitcrackrecoveryexperts@bitcrack.co.site
Provide details such as:
The type of cryptocurrency lost (Bitcoin, Ethereum, etc.)
How the funds were lost (hack, scam, forgotten password, etc.)
Transaction details (wallet addresses, TXIDs, if available)
2. Initial Consultation & Case Evaluation
Their team will analyze your situation and determine the best recovery approach. They may request additional information to strengthen the investigation.
3. Recovery Process
Using blockchain forensics and legal methods, BITCRACK RECOVERY EXPERTS will trace the movement of your funds and attempt to recover them. This may involve:
Working with exchanges to freeze stolen assets
Identifying security breaches in wallets
Utilizing legal channels if necessary
4. Fund Retrieval & Secure Return
Once recovered, your cryptocurrency will be securely returned to a wallet under your control. The team ensures transparency throughout the process.
Tips to Avoid Future Crypto Losses
Use Hardware Wallets – Store crypto offline for maximum security.
Enable 2FA – Add an extra layer of protection to exchange accounts.
Beware of Scams – Avoid suspicious investment schemes and phishing links.
Backup Private Keys – Store keys securely in multiple locations.
Final Thoughts
Losing cryptocurrency doesn’t always mean it’s gone forever. With professional help from BITCRACK RECOVERY EXPERTS, there’s a strong chance of recovery. If you’ve fallen victim to theft, hacking, or accidental loss, don’t hesitate to contact them at:
✉️ bitcrackrecoveryexperts@bitcrack.co.site
Act quickly—the sooner you start the recovery process, the higher the chances of success2 -
About Me
As a dedicated and skilled Security Analyst in the Cyber Wing, I bring a wealth of expertise in identifying, assessing, and mitigating cyber threats to protect organizational assets and sensitive information. My background is grounded in a robust understanding of cybersecurity principles, which I apply daily to safeguard against evolving digital threats.
Professional Background
With a strong foundation in cybersecurity, I have honed my skills in threat analysis, risk assessment, and incident response. My role involves continuous monitoring of network traffic, identifying vulnerabilities, and implementing security measures to prevent data breaches. I am proficient in using advanced cybersecurity tools and technologies to analyze threat intelligence and develop strategies to defend against cyber-attacks.
Key Competencies
Threat Analysis: Expert in identifying and analyzing potential threats to cybersecurity, including malware, phishing attacks, and network intrusions.
Risk Assessment: Skilled in evaluating the security posture of systems and networks, identifying vulnerabilities, and recommending corrective actions.
Incident Response: Experienced in managing and responding to security incidents, ensuring quick resolution and minimizing impact on operations.
Security Protocols: Knowledgeable in implementing and maintaining security protocols and policies to ensure compliance with industry standards and regulations.
Achievements
Successfully mitigated multiple cyber threats, reducing potential impact on organizational operations.
Developed and implemented security policies that enhanced the overall security posture of the organization.
Conducted comprehensive security assessments that led to significant improvements in network security and data protection.
Professional Goals
My goal as a Security Analyst is to continue advancing my expertise in cybersecurity, staying abreast of the latest trends and technologies to effectively combat emerging threats. I am committed to contributing to a safer digital environment and ensuring the highest level of security for the organization.
Personal Attributes
I am a proactive and detail-oriented professional, known for my analytical thinking and problem-solving abilities. I thrive in dynamic environments and am passionate about leveraging my skills to protect against cyber threats.
Contact elctrohacker DOT COM
Feel free to reach out to me for any inquiries or to discuss how I can contribute to enhancing your organization's cybersecurity posture. -
How to Recover Money Lost to Online Scams Hire PRO WIZARD GIlBERT RECOVERY.
Losing money is never easy, but losing it in a high-stakes investment hits differently. I learned this firsthand after falling victim to what seemed like a promising staking pool. Lured by bold promises of high returns and low fees, I decided to invest $18,000 into what I believed was a secure opportunity.At first glance, everything about the platform appeared legitimate. It had a sleek interface, positive user reviews, and an active community that vouched for its credibility. I felt confident I had found a reliable investment. But just weeks after staking my funds, whispers of vulnerabilities in the system started to surface. Still, I ignored the signs, trusting that the project was secure.That trust was shattered. A hacker exploited a weakness in the system’s contract, and in a matter of moments, my entire investment vanished. I was devastated. The betrayal stung deeply despite my research and caution, I had become another victim of a
WhatsApp: +1 (920) 408‑12341 -
The narrative surrounding the successful recovery of funds through SCANNER HACKER CRYPTO RECOVERY encapsulates the complexities of navigating the evolving landscape of digital finance and cybersecurity. As cryptocurrencies gain wider acceptance and integration into global economies, they simultaneously attract malicious actors seeking to exploit vulnerabilities inherent in their decentralized frameworks. The testimony of individuals recovering lost assets emphasizes the critical importance of advanced cybersecurity measures and the role of specialized recovery services in counteracting this burgeoning threat. Highlighting both individual experiences and systemic outcomes, these testimonies underscore the resilience of the human spirit in the face of financial adversity, while also serving as a cautionary tale about the vulnerabilities present in the crypto-space.
Moreover, the successful testimonials paint a broader picture of innovation and adaptation within the cybersecurity community. SCANNER HACKER CRYPTO RECOVERY, standing at the intersection of technological advancement and human expertise, exemplifies how hacker recovery services employ sophisticated methodologies using forensic analysis, digital tracking, and legal frameworks to reclaim stolen funds. This enterprise acts as a beacon for those who have experienced scams or heists, pointing to the potential for resolution in a domain typically characterized by anonymity and despair. Their success stories not only highlight the proficiency of their technical teams but also illustrate a growing recognition among users of the necessity for preemptive measures and proactive engagement with cybersecurity solutions in the crypto realm.
In conclusion, the testimonies linked to the success of SCANNER HACKER CRYPTO RECOVERY are emblematic of the ongoing struggle against cybercrime in the cryptocurrency space. These accounts serve as a reminder of the pressing need for individuals to cultivate a strong understanding of digital security, while also reinforcing the notion that recovery is possible with the right tools and expertise. As cryptocurrencies continue to proliferate, the lessons learned from these experiences may well inform the development of more robust systems of defence and recovery, ultimately contributing to a more secure ecosystem for digital financial transactions. Through collaboration between users and cybersecurity experts, the landscape can evolve into one where trust and resilience become foundational pillars of the cryptocurrency community.7 -
Email: casefile @ shi -us . com
I lost my MacBook laptop some time ago alongside my iphone 16, in that process all my crypto coinbase accounts, about 3 of them, I had difficulties logging in and I consulted lots of agencies to assist but all to no avail, until I came across Santoshi Hackers Intelligence and within a twinkle of an eye it was all done.
If you suspect your Credit card, email & password, Facebook, Instagram, twitter Accounts has been hacked, you need to Recover stolen money from scammers, reports the incident to Santoshi Hackers Intelligence they can help you recover your BTC by providing an experience team of security experts and forensic investigators who can investigate the loss, identify the source of the compromise, Santoshi we help you retrieve your stolen currency, in addition, Santoshi Hackers Intelligence can provide you with educational materials for staying safe online and give you access to cutting_edge cyber threat intelligence. They can also identify potential security breaches or vulnerabilities that may have led to the loss of your information.
Above is the email address to reach Santoshi Hackers Intelligence.1 -
Puran Crypto Recovery: The Best Cryptocurrency Recovery Company
Bitcoin theft involves stealing or tricking individuals into transferring their Bitcoin unfairly. This can occur through hacking, phishing schemes, or fraudulent investment schemes. While Bitcoin's decentralized nature offers many advantages, it also creates vulnerabilities. Transactions are pseudonymous and irreversible, making them attractive targets for malicious actors. To address these challenges, Puran Crypto Recovery offers professional assistance in tracing and recovering stolen Bitcoin and other cryptocurrencies.
In this article, we delve into the common methods used by scammers, notable Bitcoin theft cases, and how Puran Crypto Recovery helps victims recover their assets. Let’s explore the strategies to protect and recover your cryptocurrency investments.
Bitcoin’s history is marked by both remarkable success and significant thefts. By understanding the methods used by malicious actors and leveraging services like Puran Crypto Recovery, investors can better protect their assets and respond effectively in case of theft.
Puran Crypto Recovery’s track record in recovering stolen cryptocurrency demonstrates its commitment to helping victims reclaim their investments. With their advanced tools, skilled team, and customer-focused approach, they’re the trusted partner in navigating the challenges of cryptocurrency theft.5 -
Modern technological company Wizard Hilton Cyber Tech is at the forefront of creative solutions for the challenging bitcoin recovery market. This innovative company, which was founded by a group of bright cryptography specialists and cybersecurity trailblazers, specializes in solving the most difficult problems that Bitcoin and other digital asset owners encounter. Whether it's recovering lost or inaccessible funds due to forgotten passwords, hardware wallet malfunctions, or even elaborate hacking attempts, Wizard Hilton's arsenal of proprietary tools and unparalleled analytical capabilities allow them to unravel even the most convoluted digital money mysteries. Drawing on decades of combined experience in the fields of blockchain technology, digital forensics, and ethical hacking, the company's seasoned professionals employ a meticulous, multi-pronged approach to meticulously reconstruct transaction histories, identify vulnerabilities, and ultimately restore access to otherwise irretrievable cryptocurrency holdings. With an unwavering commitment to client privacy and an impressive track record of success, Wizard Hilton Cyber Tech has firmly established itself as the go-to resource for individuals and enterprises seeking reliable, discreet, and cutting-edge solutions to their most complex Bitcoin and cryptocurrency recovery challenges. Hurry, send a direct message to Wizard Hilton Cyber Tech via: Email : wizardhiltoncybertech ( @ ) gmail (. ) com
OR
support ( @ ) wizardhiltoncybertech (.) com
WhatsApp number +1302445789510 -
DOES CRYPTO RECOVERY ACTUALLY WORK? YES IT DOES- GEARHEAD ENGINEERS CASE STUDY
Losing access to your cryptocurrencies can be a nightmarish scenario. Whether you forget your passwords, fall victim to fake trading platforms or phishing scams, or experience hardware failures with your crypto wallet, the first thing you might want to do is contact a crypto recovery service. However, the unfortunate reality is that while few crypto recovery services are legitimate, most are scams designed to prey on those already in distress. Getting scammed while attempting to recover from a previous scam would be the worst-case scenario. It often makes you wonder whether crypto recovery is truly possible. In reality, tracing and getting back your crypto can only be done by individuals who have the expertise to navigate the vulnerabilities of the scammer’s systems and obtain crucial details that can be used to track transactions and eventually retrieve crypto back to the victims. GearHead Engineers have been proven time and again to be the leading legitimate recovery services. This eliminates the need to go from one organization to another seeking for legit services. Get the contact details by visiting their website by doing an online search of Gearhead Engineers then click on the website indicated as Gearhead engineers- cyber security company.2 -
DUNE NECTAR WEB EXPERT's exceptional professionalism salvaged my cryptocurrency investment after a devastating loss. My digital wallet inexplicably displayed a zero balance following an unsuccessful investment venture, leaving me financially distraught. After an exhaustive, fruitless search for assistance, I discovered DUNE NECTAR WEB EXPERT. Their specialized expertise in cryptocurrency recovery proved invaluable. Their unwavering persistence, patience, and professionalism throughout the process were remarkable. I deeply appreciated their fairness and consideration. Beyond recovering my lost cryptocurrency, they proactively identified and resolved other critical online security vulnerabilities affecting my data already released to some unscrupulous individuals. Their dedication exceeded expectations, resulting in a completely satisfactory outcome. I wholeheartedly endorse their services.
Securing a trustworthy cryptocurrency recovery service online can be daunting, particularly after experiencing financial loss. However, DUNE NECTAR WEB EXPERT stands apart as a dependable choice. As grateful clients, we enthusiastically recommend their services. For inquiries Telegram
@dunenectarwebexpert . Thank you again, DUNE NECTAR WEB EXPERT! 1
1 -
At Scanner Hacker Crypto Recovery, we are committed to revolutionizing cyber security through ethical hacking practices. Our comprehensive services focus on identifying vulnerabilities and include the recovery of stolen digital assets, such as cryptocurrencies. With a team of skilled professionals and cutting-edge technology, we provide tailored cybersecurity solutions to meet our clients' unique needs..2
-
BEST LEGITIMATE CRYPTOCURRENCY RECOVERY SPECIALIST--> REVENANT CYBER HACKER
Modern technological company REVENANT CYBER HACKER is at the forefront of creative solutions for the challenging bitcoin recovery market. This innovative company, which was founded by a group of bright cryptography specialists and cybersecurity trailblazers, specializes in solving the most difficult problems that Bitcoin and other digital asset owners encounter. Whether it’s recovering lost or inaccessible funds due to forgotten passwords, hardware wallet malfunctions, or even elaborate hacking attempts, REVENANT CYBER HACKER’s arsenal of proprietary tools and unparalleled analytical capabilities allow them to unravel even the most convoluted digital money mysteries. Drawing on decades of combined experience in the fields of blockchain technology, digital forensics, and ethical hacking, the company’s seasoned professionals employ a meticulous, multi-pronged approach to meticulously reconstruct transaction histories, identify vulnerabilities, and ultimately restore access to otherwise irretrievable cryptocurrency holdings. With an unwavering commitment to client privacy and an impressive track record of success, REVENANT CYBER HACKER has firmly established itself as the go-to resource for individuals and enterprises seeking reliable, discreet, and cutting-edge solutions to their most complex Bitcoin and cryptocurrency recovery challenges. Hurry, send a direct message to REVENANT CYBER HACKER via: Email : revenantcyberhacker ( AT ) gmail (dot ) com
Telegram: revenantcyberhacker
WhatsApp: + 1 (208) 425-8584
WhatsApp: + 1 (913) 820-0739
Website: revenantcyberhacker {dot} org 1
1 -
A Crypto Theft Victim's Journey: How Morphohack Cyber Service Restored My Assets
By: Ellen Moody, Crypto Investor and Advocate
I was left reeling after discovering that my digital wallet had been compromised, resulting in the loss of 39.5 Ethereum. This devastating experience left me desperate for a solution. I reached out to Morphohack Cyber Service. Their team responded with exceptional professionalism and expertise, promptly launching a comprehensive analysis of the blockchain network to track the stolen funds.
Their specialists employed cutting-edge blockchain analytics tools to follow the digital footprint, providing detailed explanations of their methods. It was evident that they possessed a profound understanding of hacker strategies and vulnerabilities. Despite encountering obstacles, they persevered, meticulously tracking the ETH as it navigated various wallets and tumblers.
Throughout the process, Morphohack Cyber Service maintained seamless communication, providing regular updates on the case. Ultimately, their efforts culminated in the successful recovery of 37 ETH, seized from the wallets holding my stolen assets.
I’m profoundly grateful for Morphohack Cyber Service expertise and genuine commitment to helping victims of crypto theft. Their specialized knowledge of blockchain forensics is unmatched. I highly recommend their services to anyone facing a similar situation. In the complex world of crypto, they are truly a trusted ally.
Need Help Recovering Stolen Crypto? Contact Morphohack Cyber Service:
Email: Morphohack@cyberservices . com
Info@morphohackcyber. com
Website: www . morphohackcyber . com1 -
Mongodb CEO and the developer who build this shit for brains interface should be tarred and feathered. Almost 90minutes in and I cannot connect to anything other than error codes. What in the actual fuck is your job other than to make it difficult for a "free tier" user to connect?
"connect ECONNREFUSED 127.0.0.1:27017"
Oh ok another 20 minutes of work and you give me a bland beige error code like "```TLS/SSL is disabled. If possible, enable TLS/SSL to avoid security vulnerabilities.```"... um ok how do I enable it for your site, your database or on my computer... oh wait you don't say shit do you?
So now I'm fully 81 minutes into this shit show and all I get for error codes are these really descriptive gems 'getaddrinfo ENOTFOUND cluster0.hudbd.mongodb 'dot' net` comes up if I choose `mongo` with "connection string scheme" above it or `bad auth : Authentication failed'6 -
HOW DO I GET BACK FUNDS STOLEN FROM MY DIGITAL WALLET // CRYPT0 PANDEMIC HUNTER
I was devastated when I discovered my wallet had been hacked and 12.4 ETH stolen. It was a hell of an experience. Frantically searching for solutions, I stumbled upon Crypt0 Pandemic Hunter and decided to reach out, clinging to mere hope and desperation. From the very first interaction, their team displayed a remarkable level of professionalism and expertise.
They immediately began by analyzing blockchain network, tracing the movement of my stolen ETH with precision. They patiently explained their methods, detailing how they were utilizing advanced blockchain analytics tools and techniques to follow the digital trail. It was clear they possessed had better understanding of how hackers operate and the vulnerabilities they exploit.
They didn't give up, even when the trail seemed to grow cold. They critically tracked the ETH as it moved through various wallets and pooling tumblers, piecing together the puzzle with focus and dedication. Their communication was constant, providing regular updates and developments on the case. After much work the wallets holding my stole ETH were put on hold and the assets seized.
Thanks to their relentless efforts and specialized knowledge of blockchain forensics, Crypt0 Pandemic Hunter successfully recovered 11.3 ETH . I am so much grateful for their expertise and genuine desire to help victims. I highly recommend them to anyone who finds themselves in a similar unfortunate situation. They are truly the friends indeed in this complex crypt0 world.
Reach out to ;
cryptopandemichunter[at]consultant,com
WhatsApp: +1 (205) 3573937 1
1 -
Puran Crypto Recovery: The Best Cryptocurrency Recovery Agency Helping Victims Reclaim Their Lost Assets
The Puran Approach to Recovery: A Step-by-Step Process
Recovering stolen crypto is a meticulous process that involves several critical steps. Here’s how Puran Crypto Recovery handles each case:
Initial Consultation: Puran starts by understanding the nature of the scam and gathering all relevant details from the victim. This step ensures a tailored recovery plan for each case.
Evidence Collection: Puran’s team helps victims compile essential evidence, including transaction IDs, wallet addresses, and communication records with scammers.
Blockchain Tracing: Using advanced tools, Puran traces stolen funds through the blockchain, identifying where the assets were transferred and potentially uncovering the identities of those involved.
Collaboration with Authorities: Once the funds' trail is established, Puran works with law enforcement and regulatory bodies to secure legal support for recovery.
Recovery and Resolution: The final step involves reclaiming the stolen funds and returning them to the victim’s wallet, ensuring the process is completed securely and transparently.
The world of cryptocurrency is both exciting and perilous, offering opportunities for growth but also vulnerabilities to exploitation. If you’ve been targeted by crypto thieves, don’t lose hope. With Puran Crypto Recovery, you’re in the hands of the best cryptocurrency recovery agency. Their team of experts works tirelessly to trace stolen assets, collaborate with authorities, and ensure victims recover what’s rightfully theirs.
For personalized support and expert guidance, contact Puran Crypto Recovery at purancryptorecovery@contactpuran.co.site. Visit their website at Puran.Online to learn more about their services and start your journey to recovery today.1 -
Betafort Recovery follows a systematic approach to ensure the best chance of recovering stolen funds. Here are the steps they took to help me:
1. Initial Contact and Case Assessment
I contacted Betafort Recovery via email and WhatsApp, explaining the situation in detail. They responded quickly, requesting specific information to assess the theft. This included:
- Details of the stolen transaction
- The wallet addresses involved
- Any communication or evidence related to the scam
2. Verification and Agreement
Once they reviewed my case, Betafort Recovery confirmed that they could assist in the recovery. They provided a service agreement outlining the recovery process, confidentiality terms, and their fee structure based on the amount recovered. I reviewed and signed the agreement, reassured by their transparent and professional approach.
3. In-Depth Investigation
The firm began by conducting a thorough investigation to trace the stolen funds. This involved:
- Analyzing the blockchain to track the movement of the stolen assets
- Identifying the destination wallet and any subsequent transactions
- Utilizing advanced forensic tools to uncover patterns and connections
4. Recovery Strategies
Once they gathered sufficient information, Betafort Recovery implemented various strategies to recover the stolen money:
- Negotiation: They sometimes engaged directly with the perpetrators, using their expertise to negotiate the return of the funds.
- Technical Exploits: The team exploited vulnerabilities in the scammers’ systems to regain access to the stolen assets.
- Collaborative Efforts: When necessary, they collaborated with other cybersecurity experts and legal authorities to enhance the recovery process.
5. Successful Recovery
After several days of diligent work, Betafort Recovery successfully recovered my stolen funds. They transferred the recovered money back to a secure wallet that I controlled. Their professionalism and expertise were evident throughout the process, and I was immensely grateful for their assistance.5 -
RECLAIM YOUR LOST CRYPTOCURRENCY TODAY WITH TRUSTED EXPERTS - HIRE HACKATHON TECH SOLUTIONS
The sudden disappearance of your cryptocurrency holdings, whether due to a sophisticated cyberattack, a deceptive scam, or simply misplaced access credentials, can feel like a financial disaster. During these crucial times, HACKATHON TECH SOLUTIONS provides the ultimate solution for digital asset restoration, offering unmatched expertise in recovering Bitcoin, Ethereum, and a vast array of altcoins.What sets HACKATHON TECH SOLUTIONS unique from the rest is their elite team of blockchain forensic specialists, who combine cutting-edge technology with in-depth investigative methods. These experts utilize advanced cryptographic analysis to thoroughly trace transaction histories across decentralized ledgers, uncovering vulnerabilities and exploiting weaknesses in even the most complicated theft schemes. Their approach goes far beyond basic wallet recovery services, employing proprietary tools to navigate the often murky world of blockchain transactions.The recovery process begins with an in-depth consultation where clients provide essential information about the loss, including transaction records, wallet addresses, and details about the breach or incident. The forensic team then embarks on a multi-faceted investigation, combing through blockchain data across various networks and exchanges to uncover digital traces that might otherwise remain invisible.What truly sets HACKATHON TECH SOLUTIONS apart is their strategic and proactive approach to fund retrieval. They don’t simply trace stolen assets, they craft customized recovery plans, collaborating with cryptocurrency exchanges, legal authorities, and even international organizations. Their specialists know exactly when to intercept frozen funds, reconstruct private keys, or employ advanced social engineering tactics to retrieve assets from scammers.Their recovery process is highly detailed, utilizing a range of investigative techniques that leave no stone unturned. Whether dealing with a direct theft, hacking incident, or even accidental loss due to a misplaced private key, HACKATHON TECH SOLUTIONS team can step in and provide a targeted, expert solution. In a world where cryptocurrency is often seen as a difficult asset to recover once lost, HACKATHON TECH SOLUTIONS ability to navigate the complexities of digital asset recovery gives clients peace of mind that they can recover even the most elusive of funds. When the stakes are high, their specialized expertise to restoring digital assets make them the definitive choice for anyone facing the loss of cryptocurrency holdings. Their contact details are listed below.
Whatsapp:+31 6 47999256
Telegram: +1(659) 217-9239
Email: hackathontech service @ mail . com7 -
Why Vulnerability Assessments are Critical for Enterprise Security?
A vulnerability assessment involves examining components of the IT environment to find potential security flaws that could be exploited by attackers.
The goal is to discover these issues before they can be used to compromise the system, allowing the organization to fix them and strengthen its security.
Types of Vulnerability Assessments
Scanning
This involves using automated tools to scan the technology environment for known vulnerabilities. The scanner checks software, hardware, and network configurations against a database of known issues to identify potential security gaps.
Penetration Testing
Also known as ethical hacking, penetration testing involves simulating attacks on the system to find vulnerabilities. Security experts attempt to exploit weaknesses in the system, just like a real attacker would, to uncover issues that automated scans might miss. This type of testing provides a deeper understanding of the security risks.
Risk Assessment
Risk assessment involves evaluating the potential impact and likelihood of identified vulnerabilities being exploited. It prioritizes vulnerabilities based on their potential harm to the organization and helps in making informed decisions about which issues to address first. This process often includes analyzing the potential consequences and the likelihood of exploitation.
The Role of Vulnerability Assessments in Enterprise Security
Identifying Weaknesses
Vulnerability assessments play a crucial role in uncovering security weaknesses within an organization’s IT environment. By systematically examining software, hardware, and network configurations, these assessments reveal potential vulnerabilities that could be exploited by attackers. Identifying these weaknesses early allows organizations to address them before they can be used to compromise the system. This proactive approach helps prevent security breaches and protects sensitive data from being exposed or stolen.
Prioritizing Risks
Once vulnerabilities are identified, it is essential to prioritize them based on their potential impact and likelihood of exploitation. Not all vulnerabilities pose the same level of risk. Some might be easily exploitable and have severe consequences, while others might be less critical. Understanding which vulnerabilities present the greatest risk helps organizations focus their resources and efforts on addressing the most pressing issues first. This prioritization ensures that the most critical weaknesses are fixed promptly, reducing the overall risk to the organization.
You can check more info about: Vulnerability Assessments( Opstree ) -
HOW TO RECOVER MONEY LOST TO ONLINE SCAM HIRE ADWARE RECOVERY SPECIALIST
The Art of Recovery: ADWARE RECOVERY SPECIALIST Unmatched Prowess in my Bitcoin Restoration of 102,000USD
When faced with the devastating loss of a virtual fortune in Bitcoin, the sheer magnitude of the challenge can seem insurmountable. Yet, in the face of this crisis, the expert team at ADWARE RECOVERY SPECIALIST demonstrated an unparalleled mastery of their craft, guiding me through the intricate process of recovering my 102,000USD Bitcoin with unwavering skill and precision. From the moment I reached out, their seasoned professionals exuded a calm confidence, assuring me that no digital asset was beyond their reach. They leveraged their deep understanding of blockchain technology, forensic data analysis, and proprietary recovery techniques to meticulously piece together the scattered fragments of my digital wealth. Their tireless efforts, fueled by an unwavering commitment to their craft, allowed them to navigate the labyrinthine world of cryptocurrency, circumventing obstacles and exploiting vulnerabilities that would have stymied lesser experts. Through their dogged determination and innovative problem-solving, ADWARE RECOVERY SPECIALIST was able to triumphantly restore my 102,000USD Bitcoin, a feat that stands as a testament to their unparalleled expertise and the transformative power of their services. In the face of what seemed like an insurmountable challenge, their team demonstrated the art of recovery, masterfully reclaiming my digital assets and safeguarding my financial future. I can say with full confidence that ADWARE RECOVERY SPECIALIST is the real deal. They are experts in their field and have the technical mastery to handle even the most complex Bitcoin recovery cases. If you’ve found yourself in a similar situation, feeling like your Bitcoin is gone for good, I urge you to contact ADWARE RECOVERY SPECIALIST . They have the skills, the knowledge, and the integrity to get the job done. They revived my hope and proved that with the right expertise, recovery is possible. WhatsApp info:+12 723 328 3434 -
How To Recover Money Lost To Fake Online Scheme Through Cryptic Trace Technologies
In early 2025, I became entangled in a sophisticated online pyramid scheme that promised substantial returns. Trusting the platform’s polished facade and persuasive testimonials, I invested $375,000, only to realize later that it was a scam. The financial loss was devastating, leading me into a deep depression. I felt isolated and ashamed, questioning how I could have been deceived so thoroughly. The weight of the loss affected every aspect of my life, from personal relationships to professional responsibilities. A close friend, noticing my distress, recommended I contact Cryptic Trace Technologies, a firm specializing in cryptocurrency recovery. Skeptical but desperate, I researched them extensively and found numerous positive reviews . Their team was compassionate and professional, taking the time to understand the intricacies of my case. They employed advanced blockchain analysis tools to trace the stolen funds through various wallets and exchanges. Their expertise and dedication were evident as they navigated the complex web of transactions, ultimately recovering a significant portion of my lost investment. They also collaborated with law enforcement to ensure the perpetrators were brought to justice. This harrowing experience underscored the importance of vigilance in the digital financial landscape. Tools like Chainalysis, Elliptic, and CipherTrace are instrumental in tracking and recovering stolen cryptocurrency . These platforms provide real-time monitoring and risk assessment, aiding both individuals and institutions in safeguarding their assets. Moreover, ethical hackers, often referred to as ‘white hat’ hackers, play a crucial role in identifying vulnerabilities and assisting in fund recovery . While the journey from victim to victor was arduous, it highlighted the resilience of the human spirit and the importance of seeking help from reputable professionals like Cryptic Trace Technologies in times of crisis. Contact them through their E M A I L : cryptictrace (@) technologist (.) com
W E B S I T E : cryptictracetechnologies (.) com2 -
I NEED A HACKER TO RECOVER MY LOST BTC/ NFT/ETH/USD / CONSULT CAPTAIN WEBGENESIS.
Recover Your Lost Crypto Assets with the Help of Captain WebGenesis
CAPTAIN WEBGENESIS provides unique solutions for recovering misplaced cryptocurrency holdings. In an era when cryptocurrencies have reached unparalleled popularity, the terrible reality is that many people are dealing with lost or inaccessible crypto assets. Fortunately, alternatives exist for people looking to reclaim their investments. CAPTAIN WEBGENESIS is one such solution, a dedicated service that assists consumers in regaining access to their stolen cryptocurrency funds in an effective and secure manner. Upon engaging with CAPTAIN WEBGENESIS, users obtain a thorough analysis of their condition. The team assesses the type of asset lost, the circumstances surrounding its loss, and any potential vulnerabilities that could have contributed to the problem. This step is critical in developing an effective recovery plan.
If you've found yourself in a scenario where your crypto assets are out of reach, or you're concerned about potential vulnerabilities harming your investments, don't wait any longer—act now! Contact Captain WebGenesis to begin your journey toward regaining your digital fortune.
Email Add; Captainwebgenesis @hackermail. com
WhatsApp; +1(501)436-9362.9 -
Never have I ever missed my favorite crypto podcast. There was this one episode where the guest was over the moon about Asset Rescue Specialist. I made a mental note, never thinking that I would ever need them. That changed when a malware attack wiped my $500,000 wallet clean. One minute I was going through my portfolio; the next, it was zero. My heart sank. I checked everything: my security logs, transaction history, even my device settings. That is when I saw it: unauthorized transfers draining my entire balance. Panic hit hard.
I scrambled for solutions, frantically searching through forums, threads on Reddit, and tech support pages. But deep down, I knew this wasn't something so simple to fix. Then, in the middle of my chaos, that podcast episode remembered itself. He spoke of Asset Rescue Specialist with such confidence that I decided to trust his experience.
It was one of the smartest things I could have done, reaching out to Asset Rescue Specialist. Since the very first message, they were calm, methodical, and reassuring. They made all the right questions and quickly diagnosed how the malware had invaded my wallet. Their team dove head-first into an advanced forensic recovery process while teaching me what went wrong.
I was skeptical: how do you reverse a theft that's already happened? But they knew what they were doing. Their precision, their expertise, and just the determination to see it through blew me away. Then, the message changed everything: "We've recovered your funds." I couldn’t believe it. My $500,000 was back. My relief was indescribable. They didn’t just stop there—they fortified my security, patched vulnerabilities, and gave me a plan to ensure this never happens again.
That podcast episode? Changed my life. Never thought casual listening would save my portfolio. Now, I don't listen for insights but for survival tips. And for whoever reads, let me share a piece of advice: you needn't wait for the worst to happen. Know who you are going to call before it's time.
FOR MORE INFO:
Company: ASSET RESCUE SPECIALIST
WhatsApp:+ 1 9 0 3 5 5 9 1 7 3 3.1 -
CRYPTOCURRENCY TRACING AND FUNDS RECOVERY CONSULT DUNAMIS CYBER SOLUTION
The cryptocurrency space, with its dizzying promises of financial freedom, had always intrigued me until it became the stage for my deepest disillusionment. Last year, I fell victim to an elaborate crypto scam that stripped me of years’ worth of savings. What began as a confident investment in a "guaranteed returns" scheme unraveled into a nightmare. Overnight, my portfolio vanished, along with the anonymous fraudsters who orchestrated the ploy. The aftermath was a toxic blend of anger, shame, and helplessness. I questioned every decision, replaying red flags I’d naively ignored. Crypto forums offered little solace, filled with eerily similar stories of irreversible losses. Just as I resigned myself to defeat, a glimmer of hope emerged: DUNAMIS CYBER SOLUTION.From the outset, their team stood apart by blending technical precision with unwavering compassion. Rather than treating my case as a faceless ticket, they approached it with a commitment to understanding the human toll of the scam. During initial consultations, they listened patiently to my story, offering reassurance that shifted my mindset from despair to cautious optimism. “These scams thrive on exploiting trust, not incompetence,” one advisor emphasized a perspective that dissolved my self-blame.DUNAMIS CYBER SOLUTION mastery of Cryptocurrencies forensics became evident as they untangled the digital maze of my stolen assets. They decoded how fraudsters manipulated wallet vulnerabilities and decentralized exchanges to obscure the trail, leveraging proprietary tools and cross platform collaborations to trace the funds.Over three days, their transparency became my anchor. Regular updates demystified their process, flagging suspicious transactions, and piecing together patterns linked to earlier scams. Challenges arose dead-end leads, unresponsive third parties but the team navigated each obstacle with tenacity. By second day, they’d recovered $350,000 of my assets.Beyond recovery, DUNAMIS CYBER SOLUTION prioritized empowerment. They equipped me with resources to safeguard future investments and connected me to a private forum of survivors, fostering a community of shared resilience. Today, I’m not only financially restored but fortified with hard-earned wisdom. My situation proves that loss isn’t always permanent. With cutting-edge expertise and relentless advocacy, redemption is attainable. Let my journey remind you: even in Cryptocurrency opaque wilderness, a path back exists and DUNAMIS CYBER SOLUTION lights the way.2 -
DIGITAL TECH GUARD RECOVERY: RECLAIM LOST CRYPTOCURRENCY FROM SCAM
It felt like a spy movie. After losing $800K to a slick-talking Instagram crypto broker, I needed a miracle. Enter Digital Tech Guard Recovery, a team of white-hat hackers who specialize in crypto heists. Digital Tech Guard Recovery was my last hope, and I was determined to reclaim what was rightfully mine. Armed with blockchain sleuthing tools, Digital Tech Guard Recovery infiltrated the scam network, traced my funds to dummy wallets, and executed a counter-strike to reclaim every dollar. The scammers never saw it coming, thanks to the expertise of Digital Tech Guard Recovery. They worked tirelessly, analyzing transaction patterns and identifying vulnerabilities in the scammer's infrastructure. Each day felt like a high-stakes game of cat and mouse, with the clock ticking and my hopes hanging by a thread, but Digital Tech Guard Recovery was relentless. As they delved deeper, I learned about the intricate web of deceit that had ensnared me. The Instagram crypto broker had created a façade of legitimacy, complete with fake testimonials and polished marketing. But Digital Tech Guard Recovery was undeterred. They coordinated with law enforcement and leveraged their connections in the crypto community to gather intelligence, all while keeping me informed and hopeful. Finally, after what felt like an eternity, the moment of truth arrived. Digital Tech Guard Recovery executed their plan with precision, launching a digital assault that sent shockwaves through the scam network. I watched in awe as my funds began to flow back into my wallet, each transaction a small victory against the fraudsters, all thanks to Digital Tech Guard Recovery. Never mess with a victim who hires Digital Tech Guard Recovery. They turned my despair into triumph, proving that justice can prevail in the digital age. Now, I’m not just a survivor; I’m an advocate for others who have fallen prey to similar schemes. With the right help from Digital Tech Guard Recovery, it’s possible to reclaim what was lost and expose the dark underbelly of online scams. Digital Tech Guard Recovery is a beacon of hope for anyone who has been victimized in the world of crypto.
WhatsApp: +1 (443) 859 - 28862 -
HOW TO RECOVER YOUR STOEN BITCOIN: HIRE A HACKER, TRUST GEEKS HACK EXPERT
The stakes were catastrophic when a sophisticated CEO fraud scam siphoned $500,000 from Titan Blockchain Ventures, a leading crypto asset management firm based in New York City. We faced not just financial loss, but severe reputational damage, investor panic, and the potential for layoffs. The scam was executed with alarming precision, and the speed at which the funds disappeared left us in shock. Our internal IT team worked tirelessly, but they quickly hit dead ends. The dark web’s complexity, coupled with the fraudsters' advanced tactics, made tracing the assets nearly impossible. Worse still, law enforcement advised that their investigation would take months, time we didn’t have. Desperate for a solution, we turned to Trust Geeks Hack Expert, Website, a firm highly recommended within the industry. Trust Geeks Hack Expert corporate division acted with unmatched urgency and precision. Within hours of our engagement, Trust Geeks Hack Expert team Telegram: Trust-geeks-hack-expert began mapping the stolen funds across dark web markets using cutting-edge blockchain forensics. Their expertise was immediately evident as Trust Geeks Hack Expert traced every transaction, pinpointing wallet addresses and exchanges with surgical accuracy. What truly set Trust Geeks Hack Expert apart was their proactive approach. Trust Geeks Hack Expert didn’t just trace the funds they acted swiftly to freeze further transactions. By leveraging their vast international network of exchange partners, Trust Geeks Hack Expert halted the movement of the stolen crypto in real time, preventing any additional losses. Their swift, coordinated efforts resulted in the recovery of 92% of the stolen assets in under two weeks a remarkable achievement that most thought impossible. But Trust Geeks Hack Expert didn’t stop at asset recovery. Trust Geeks Hack Expert also provided us with a comprehensive compliance roadmap. Their post-recovery audit identified critical vulnerabilities in our security systems and recommended both practical and visionary solutions to strengthen our defenses. Thanks to Trust Geeks Hack Expert we were given clear, actionable steps to prevent future breaches and fortify our infrastructure.2 -
BTC & NFT RESTORATION, GET EXPERT HELP FROM =SALVAGE ASSET RECOVERY
As a digital artist venturing into the world of NFTs, I was filled with excitement and hope. I had spent years honing my craft, and the prospect of sharing my work with a global audience was exhilarating. However, my journey took a devastating turn when I fell victim to a malicious smart contract that drained my wallet of $75,000 in earnings and royalties. The art community's response was disheartening; they told me it was gone forever, a harsh reminder of the risks we accept in the digital space.Feeling lost and disheartened, I began to accept the reality of my situation. It was not just about the money; it represented years of hard work, creativity, and passion. I felt as though a part of my artistic identity had been stolen. Just when I thought all hope was lost, I came across Salvage Asset Recovery. Their approach was different; they understood the emotional weight of my loss and were determined to help. Salvage Asset Recovery specialises in cryptocurrency vulnerabilities, and their team of experts meticulously analysed the malicious contract code that had caused my financial devastation. They identified the exploit and worked tirelessly with the platform to freeze subsequent transactions, preventing further losses. Their dedication was evident, and I felt a renewed sense of hope.Ultimately, Salvage Asset Recovery successfully recovered my lost funds. While I was grateful to have my $75,000 restored, I realised that the experience had left me with a lingering sense of vulnerability. I wished I had received guidance on how to protect myself in the future, as the world of NFTs and cryptocurrency can be fraught with risks.Though my financial stability was restored, I knew I needed to take proactive steps to educate myself about the intricacies of smart contracts and the potential vulnerabilities that exist within the cryptocurrency space. I emerged from this ordeal with my funds intact, but also with a newfound determination to secure my creative work and protect myself moving forward. If you need help reach out to Salvage Asset Recovery
CONTACT INFORMATION TELEGRAM---@Salvageasset
WhatsApp+ 1 8 4 7 6 5 4 7 0 9 62 -
HOW YOU CAN RECOVER YOUR CRYPTO FROM SCAMMERS // CONSULT DIGITAL TECH GUARD RECOVERY
As a tech geek, I'm proud to be on the bleeding edge. So when I stored my Bitcoin in a "quantum-resistant" wallet, I was sure I was invincible, a Nostradamus of the modern age predicting the coming quantum computing apocalypse. "Hack-proof," the website had promised. "A fortress against the future."
And then irony struck. A bug in the firmware shut me out altogether. No access. No backups. Only a chilly, machine-like error message mocking me like a bad guy in a sci-fi flick: "Invalid Signature. Please Reset." Reset? That would mean erasing my $860,000 in Bitcoin. Not exactly a pleasant choice.
Furious, I did what any geek does when something is not right, I tweeted about it. My rant at the irony of a quantum-proof wallet crashing due to a widespread bug went viral. That is when a DM appeared. Digital Tech Guard Recovery's CTO had seen my tweet. "Let's fix this," he typed.
Now, I’ve dealt with tech support before, but this was something else. Within hours, their engineers were deep in my wallet’s firmware, analyzing the cryptographic flaw. They approached the problem like time travelers fixing a paradox, reverse-engineering the bug to develop a workaround.
It was a challenge. The wallet's special "quantum security" had locked it up so tightly that debugging tools couldn't even access it. But these guys were not your average IT support personnel; they were crypto Digitals.
For ten days, I monitored their progress like a scientist awaiting a space probe signal. Finally, the breakthrough: a hacked firmware update, specifically tailored for my wallet model. With cautious steps, I executed their recovery protocol, and voilà, my money was restored.
But they didn't leave it at that. Digital Tech Guard Recovery not only restored my Bitcoin but moved it to an even more secure, battle-tested storage system. No more cutting-edge vulnerabilities. Just solid, proven cryptography.
The irony? My Bitcoin is now safer than ever, not because it's quantum-resistant, but because of the individuals who came to my aid.
Lesson that was learned: The future is unpredictable, but having the right experts on speed dial? That's real security.
WhatsApp: +1 (443) 859 - 2886
Email @ digital tech guard . com
Telegram: digital tech guard recovery . com
Website link: digital tech guard . com1 -
RECOVER MONEY LOST TO FAKE ONLINE SCAMMERS HIRE FUNDS RECLAIMER COMPANY
The cryptocurrency space, with its dizzying promises of financial freedom, had always intrigued me until it became the stage for my deepest disillusionment. Last year, I fell victim to an elaborate crypto scam that stripped me of years’ worth of savings. What began as a confident investment in a "guaranteed returns" scheme unraveled into a nightmare. Overnight, my portfolio vanished, along with the anonymous fraudsters who orchestrated the ploy. The aftermath was a toxic blend of anger, shame, and helplessness. I questioned every decision, replaying red flags I’d naively ignored. Crypto forums offered little solace, filled with eerily similar stories of irreversible losses. Just as I resigned myself to defeat, a glimmer of hope emerged: FUNDS RECLIAMER COMPANY. From the outset, their team stood apart by blending technical precision with unwavering compassion. Rather than treating my case as a faceless ticket, they approached it with a commitment to understanding the human toll of the scam. During initial consultations, they listened patiently to my story, offering reassurance that shifted my mindset from despair to cautious optimism. “These scams thrive on exploiting trust, not incompetence,” one advisor emphasized a perspective that dissolved my self-blame. FUNDS RECLIAMER COMPANY’s mastery of Cryptocurrencies forensics became evident as they untangled the digital maze of my stolen assets. They decoded how fraudsters manipulated wallet vulnerabilities and decentralized exchanges to obscure the trail, leveraging proprietary tools and cross platform collaborations to trace the funds. Over three days, their transparency became my anchor. Regular updates demystified their process, flagging suspicious transactions, and piecing together patterns linked to earlier scams. Challenges arose dead-end leads, unresponsive third parties but the team navigated each obstacle with tenacity. By second day, they’d recovered $350,000 of my assets. Beyond recovery, FUNDS RECLIAMER COMPANY prioritized empowerment. They equipped me with resources to safeguard future investments and connected me to a private forum of survivors, fostering a community of shared resilience. Today, I’m not only financially restored but fortified with hard-earned wisdom. My situation proves that loss isn’t always permanent. With cutting-edge expertise and relentless advocacy, redemption is attainable. Let my journey remind you: even in Cryptocurrency opaque wilderness, a path back exists and FUNDS RECLIAMER COMPANY lights the way.
FOR MORE INFO:
WhatsApp:+13612504110
Email: fundsreclaimercompany@ z o h o m a i l . c o m1 -
STEPS TO RECOVER BITCOIN AND USDT FROM ONLINE INVESTMENT SCAM
Betafort Recovery follows a systematic approach to ensure the best chance of recovering stolen funds. Here are the steps they took to help me:
1. Initial Contact and Case Assessment
I contacted Betafort Recovery via email and WhatsApp, explaining the situation in detail. They responded quickly, requesting specific information to assess the theft. This included:
- Details of the stolen transaction
- The wallet addresses involved
- Any communication or evidence related to the scam
2. Verification and Agreement
Once they reviewed my case, Betafort Recovery confirmed that they could assist in the recovery. They provided a service agreement outlining the recovery process, confidentiality terms, and their fee structure based on the amount recovered. I reviewed and signed the agreement, reassured by their transparent and professional approach.
3. In-Depth Investigation
The firm began by conducting a thorough investigation to trace the stolen funds. This involved:
- Analyzing the blockchain to track the movement of the stolen assets
- Identifying the destination wallet and any subsequent transactions
- Utilizing advanced forensic tools to uncover patterns and connections
4. Recovery Strategies
Once they gathered sufficient information, Betafort Recovery implemented various strategies to recover the stolen money:
- Negotiation: They sometimes engaged directly with the perpetrators, using their expertise to negotiate the return of the funds.
- Technical Exploits: The team exploited vulnerabilities in the scammers’ systems to regain access to the stolen assets.
- Collaborative Efforts: When necessary, they collaborated with other cybersecurity experts and legal authorities to enhance the recovery process.
5. Successful Recovery
After several days of diligent work, Betafort Recovery successfully recovered my stolen funds. They transferred the recovered money back to a secure wallet that I controlled. Their professionalism and expertise were evident throughout the process, and I was immensely grateful for their assistance.
Conclusion
Having your funds stolen from Trust Wallet can be a harrowing experience, but there is hope with services like Betafort Recovery. Their systematic and professional approach makes them a reliable partner in recovering stolen cryptocurrencies. If you ever find yourself in a similar situation, don’t hesitate to reach out to them:
Email: info@betafort.online
WhatsApp: +17126004729
Thanks to Betafort Recovery, I was able to restore my financial stability and continue my journey in the world of cryptocurrency with renewed confidence. Their dedication and expertise turned a potential financial disaster into a successful recovery, for which I am eternally grateful.2 -
In the vibrant city of Berlin, I found myself ensnared in a labyrinthine scheme orchestrated by a deceitful cryptocurrency trading platform. Lured by enticing promises of substantial returns, I invested a staggering €305,391.04, only to uncover the disheartening reality that the broker was nothing more than a cunning scam artist. My ordeal began innocently enough; I was encouraged to deposit funds, and as my account displayed fictitious profits, I was relentlessly bombarded with demands for exorbitant withdrawal fees. Each time I acquiesced to their needs, the fees escalated, revealing the grim truth that I was trapped in a vicious cycle of exploitation. As the weight of my predicament became unbearable, I confided in my friend Frank, who had previously navigated similar treacherous waters. He recommended TECHY FORCE CYBER RETRIEVAL, a name that ignited a flicker of hope amidst my despair. Skeptical yet desperate, I reached out to TECHY FORCE CYBER RETRIEVAL, meticulously detailing my harrowing experience. To my relief, they responded with remarkable promptness, exhibiting a level of professionalism and empathy that reassured me I was in capable hands. The recovery process was executed with astonishing efficiency and alacrity. Within a mere 48 hours, I was astounded to discover that my lost funds had been successfully reclaimed. TECHY FORCE CYBER RETRIEVAL employed a combination of astute investigative techniques and strategic legal maneuvers to trace the funds and negotiate their return. Their expertise in navigating the intricate landscape of cryptocurrency scams proved invaluable, as they adeptly maneuvered through the complexities of digital transactions. Thanks to TECHY FORCE CYBER RETRIEVAL, I not only regained my financial stability but also my peace of mind. This experience served as a stark reminder of the vulnerabilities inherent in the realm of online trading. Yet, it also underscored the paramount importance of seeking assistance from professionals who specialize in recovery. I now advocate for vigilance in cryptocurrency investments, urging others to conduct thorough due diligence and remain alert to potential scams. For anyone grappling with similar challenges, I wholeheartedly recommend contacting TECHY FORCE CYBER RETRIEVAL. Their unwavering dedication to assisting victims of fraud is unparalleled, and they possess the expertise and resources necessary to reclaim what is rightfully yours. Do not hesitate to reach out; your financial recovery may be just a message away.2
-
DUNE NECTAR WEB EXPERT recovered my lost cryptocurrency after a failed investment. Their expertise, persistence, and professionalism were exceptional. They also fixed critical online security vulnerabilities. I highly recommend their services: Telegram @dunenectarwebexpert.1