Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "sensitive"
-
*client calls in*
Me: good morning, how can I help you?
Client: my ip is blocked, could you unblock it for me?
Me: certainly! What's your ip address? Then I'll have a look.
Client: I'm not giving you my ip?! That's too privacy sensitive.
Me: 😶
Me: 😶
Me: 😶
Me: sir, I'm very keen on my privacy myself but without that information I can't do much for you 😬
Client: ah so you're refusing to help me?
Me: not like that, it's just very hard to lift an ip block for me when I don't know the ip address.
Client: you just don't want to help, fine.
*click*
😶32 -
Meeting with asshole partner company CEO at restaurant.
Me: "I'm a bit worried about the bugs in your API. There are some ways to retrieve privacy sensitive info from public endpoints"
CEO: "Well, we're a rapidly growing startup!"
Me: "Uh... so?"
CEO: "So... Move Fast and Break Things! Priority is to improve our API further, and we'll fix bugs as they show up"
Me: "Maybe you should stop trying to emulate Zuckerberg in your management style. You know that even Facebook themselves admitted that their slogan was a retarded mistake"
Waiter shows up at table. CEO orders some overly expensive fish salad.
CEO: "Well, they have done something right... they're worth billions"
Waiter asks me: "And you sir, have you made your choice?"
Me: "Do you serve popcorn?"
CEO: "Popcorn for lunch?"
Me: "No, for your congressional hearing"16 -
My mom got audited for storing sensitive client information in her gmail account without using a vpn or any other real security.
I had been telling her this was an issue for literally the last three years and shes brushed me off every time.
I got yelled at for not telling her I was serious.34 -
My mentor/guider at my last internship.
He was great at guiding, only 1-2 years older than me, brought criticism in a constructive way (only had a very tiny thing once in half a year though) and although they were forced to use windows in a few production environments, when it came to handling very sensitive data and they asked me for an opinion before him and I answered that closed source software wasn't a good idea and they'd all go against me, this guy quit his nice-guy mode and went straight to dead-serious backing me up.
I remember a specific occurrence:
Programmers in room (under him technically): so linuxxx, why not just use windows servers for this data storage?
Me: because it's closed source, you know why I'd say that that's bad for handling sensitive data
Programmers: oh come on not that again...
Me: no but really look at it from my si.....
Programmers: no stop it. You're only an intern, don't act like you know a lot about thi....
Mentor: no you shut the fuck up. We. Are. Not. Using. Proprietary. Bullshit. For. Storing. Sensitive. Data.
Linuxxx seems to know a lot more about security and privacy than you guys so you fucking listen to what he has to say.
Windows is out of the fucking question here, am I clear?
Yeah that felt awesome.
Also that time when a mysql db in prod went bad and they didn't really know what to do. Didn't have much experience but knew how to run a repair.
He called me in and asked me to have a look.
Me: *fixed it in a few minutes* so how many visitors does this thing get, few hundred a day?
Him: few million.
Me: 😵 I'm only an intern! Why did you let me access this?!
Him: because you're the one with the most Linux knowledge here and I trust you to fix it or give a shout when you simply can't.
Lastly he asked me to help out with iptables rules. I wasn't of much help but it was fun to sit there debugging iptables shit with two seniors 😊
He always gave good feedback, knew my qualities and put them to good use and kept my motivation high.
Awesome guy!4 -
Story time:
I was once working on a project that dealt with incredibly sensitive financial data.
We needed a client’s database to do a migration.
They wouldn’t send it over the internet because it was too big and they didn’t think it would be secure.
They opt to send it in the post on an encrypted usb drive.
(Fair enough thinks I)
USB drive arrives.
Is indeed encrypted.
MFW there’s a post it note in the envelope with the password on.
MFW this is a billion dollar multinational petrochem company.
MFW this same company’s ‘sysadmin’ and ‘dba’ once complained because a SQL script I sent them didn’t work - they’d pasted it twice and couldn’t work this out from the fucking “table already created” error message management studio was throwing at them.3 -
Our current designer is convinced that 00FF44 bright green fits well with the rest of our soft purple/blue color scheme.
I am not a designer, but have worked in a color laboratory, so I've tried time and time again to explain CIE LAB color space, and how at least HCL is a good way to pick & group colors into palettes by using 2-3 luminances for equidistant hues while keeping chroma constant.
I've tried to tell him that the bright green almost physically makes my eyes bleed, because humans are quite sensitive to greens.
He just keeps using the phrase "but it makes the buttons pop nicely".
I just want to pop his skull open with my keyboard. 😫11 -
Dear Microsoft,
Thanks for not completely fucking up Github. At least you didn't integrate Office365, allow only Azure deployments, or force downloading repos through OneDrive or something.
But like most developers, I don't deal well with changes to familiar interfaces.
So please.... STOP FUCKING TWEAKING THE BUTTON PLACEMENTS AND TEXTS ALL OVER THE WEBSITE.
(or at least send me a bottle of cognac and a box of chocolates before every UI experiment, so I can deal with it emotionally. I'm a very sensitive boy, you know).19 -
Fuck open office spaces.
A few months ago I landed a super sweet job as a senior full stack developer, mainly going to work with their Python microarchitecture. The company pays well, has a sweet balance between freedom and responsibility, 30 days vacation etc.
During the recruiting process they walked me around the office that was super cozy with 14 devs in on large room and 10 people from marketing in another. They also mentioned that they would move and merge office with operations and customer service (around 100 more people) in a few months.
Life was good in the old office, I thought that this is the company where I will work for a looooong time.
Now we are in the new office and its fucking shit. No walls or FUCKING CEILINGS between departments. Right above my head there is balcony with customer service talking loud as fuck 24/7. Everyone that is not a developer is just so fucking loud.
I have to use earplugs AND earmuffs to get silence, or blast my ears with way to loud music. Every day around lunch I'm completely done mentally.
I know I'm extra sensitive to noise because of my ADHD, but seriously who the fuck thought this was a good idea?
All the devs have told our boss what needs to be done. If they listen i don't know. In the meantime I will start looking for a new job....18 -
At my previous job we had the rule to lock your PC when you leave. Makes sense of course.
We were not programmers but application engineers, still, we worked with sensitive data.
One colleague always claimed to be the most intelligent and always demanded the "senior" - title. Which he obviously did not deserve.
multiple times a day forgot to lock his workstation and we had to do it for him.
My last week working there, I've had it. He forgot it again... So I made a screenshot of his current environment. Closed everything. Set his new background with the screen shot and killed explorer (windows). Then finally I locked his PC.
When he came back he panicked that his PC froze. He couldn't do shit anymore. Not knowing what to do... 😂
Which makes him a senior of course.
But seriously, first thing I would do is open the task manager and notice that explorer wasn't running... Thus my background with the taskbar isn't real.... My colleagues must be pranking me!
Nope... The "senior" knew little10 -
Motherfucker. It's two thousand fucking seventeen. You can get a free ssl certificate for any website.
Then WHY are there still some fucking websites which contain login portals, sensitive information or anything that SHOULD be protected in transit WITHOUT FUCKING SSL?!
I hope that the people who manage those sites and are AWARE that they can get a free cert but don't do that die in agonising pain.
This really fucking pisses me off.
On another note, EVERY site should have SSL, it's free anyways and protects your visitors from a range of threats.-24 -
Before anyone starts going batshit crazy, this is NOT a windows hate post. Just a funny experience imo.
So I was tasked with installing ProxMox on a dedicated server at my last internship. The windows admin was my guider (he could also do debian). (he was a really nice/chill guy)
So we were discussing what VM's we wanted and the boss (really cool dude by the way) said he wanted a VPS for storing some company stuff as well. Fair enough, what would we use? I suggested debian and centos. Then we started discussing what we'd do if the systems would fuck up etc (at installation or whatever).
So I didn't wanna look like a Linux Nazi so I suggested windows. Then the happy/positive guider/windows admin suddenly became dead serious (I was actually like 'woah' for a second) and said this:
No. We're not going to fucking use windows for this. For general servers etc sometimes, fair enough but we're talking about sensitive company data here. I don't want that data to be stored on a proprietary/closed source system, hell what if there's some kinda fucking backdoor build in, who can fucking verify that? We're using Linux, end of discussion.
😓
I was pretty flabbergasted as he's a nice guy and actually really likes windows!
Linux it became.5 -
Not so much screaming as staring in disbelief, mumbling profanity in his direction...
When my department lead said "I don't think this unit testing hype or code reviews make much sense, it's more efficient to just make a checklist and test the application yourself"
This was the QA department of an aerospace company, we wrote NDT software to do image recognition on xrays of alloy welds and micrometer laser measurements on fuel tank surfaces. Software which is quite mission critical, a single misrecognized welding fault could literally cost up to half a billion dollars — not to mention that it's a very sabotage & espionage sensitive industry.
After raising some hell he was replaced though.3 -
SO GUESS WHAT
IF YOUR SHITTY WIFI CRAPS OUT DURING A VISUAL STUDIO UPDATE, VISUAL STUDIO FUCKING COMMITS SUICIDE
MICROSOFT CAN SUCK A BIG, VEINY COCK. IM SO DONE WITH THEIR SENSITIVE, CONVOLUTED, SLOW IDE.19 -
Humans!
The amount of sensitive, private, and secure information you can get just by asking someone for it is truly astounding.5 -
Sometimes I wish I was allowed to just strangle my colleagues...
Example from the 'code base':
try:
do_something()
except Exception as e:
log(e)
do_something()
When I asked why they would redo the same call right after it failed I was told that 'It works the second time because it takes time to raise the Exception '.
Bitch, you've got a race condition in your sensitive banking software. You know it's there. Do you really want to trust the time needed to raise your exception will always be enough to synch that dumpster fire you call code?
Show some fucking respect for your craft and fix that shit. But of course they won't, because it will work flawlessly until it suddenly stops working. Taking down who knows what in this damn, undocumenred monolith with it....
Sometimes I'm honestly afraid to trust banks with my money.7 -
"We don't need to invest in security - noone is going to hack us anyway" == "We don't need a fire department in our city - fire is not going to start here anyway"
We don't need to invest in security - everything is public anyway" == "We don't need a fire department in our city - our buildings are made out of straws anyway"
-- my thoughts after seing a line in client's spec: "sensitive data is transferred via a secure tcp channel (https) and all the public data is transferred via an unencrypted tcp (http) channel"3 -
Devs: We need access to PROD DB in order to provide support you're asking us for.
Mgmt: No, we cannot trust you with PROD DB accesses. That DB contains live data and is too sensitive for you to fuck things up
Mgmt: We'll only grant PROD DB access to DBAs and app support guys
Mgmt: <hire newbies to app support>
App_supp: `update USER set invoice_directory = 54376; commit;`
----------------
I have nothing left to say....7 -
Had a follow up meeting today to resolve the issue of Product ignoring our comments about possible issues, better ways to do it etc.
New rules:
- We are allowed to suggest to Product that they might be doing something wrong
- We are not allowed to tell product they are doing something wrong
- If Product don’t listen, that’s fine, we will document our comments to protect us later.
Conclusion:
Product are too sensitive to have a conversation with. We are now going to let them fuck everything up, make some notes and say “I told you so” at a later date.
Maturity at its finest ladies and gentlemen.5 -
I remember that time my class (first year of software development) wrote a huge project for a real company as practice for irl stuff.
I was the only Linux user and it would be deployed on a Linux server.
Spent 10 weeks of development and then the moment of deployment on a Linux server began!
.
.
.
.
.
Nothing was case sensitive, everything was programmed for a windows architecture (backward slashes etc) and mssql was used while we would host it on a MySQL server.
The tree core guys spent three days or so to make the entire fucker compatible 😂
It was enjoyable to see them (literally) sweat 😊 (it had been known from the very beginning)7 -
Worst legacy experience...
Called in by a client who had had a pen test on their website and it showed up many, many security holes. I was tasked with coming in and implementing the required fixes.
Site turned out to be Classic ASP built on an MS Access database. Due to the nature of the client, everything had to be done on their premises (kind of ironic but there you go). So I'm on-site trying to get access to code and server. My contact was *never* at her desk to approve anything. IT staff "worked" 11am to 3pm on a long day. The code itself was shite beyond belief.
The site was full of forms with no input validation, origin validation and no SQL injection checks. Sensitive data stored in plain text in cookies. Technical errors displayed on certain pages revealing site structure and even DB table names. Server configured to allow directory listing in file stores so that the public could see/access whatever they liked without any permission or authentication checks. I swear this was written by the child of some staff member. No company would have had the balls to charge for this.
Took me about 8 weeks to make and deploy the changes to client's satisfaction. Could have done it in 2 with some support from the actual people I was suppose to be helping!! But it was their money (well, my money as they were government funded!).1 -
This is the GREAT ROLLING website that I ranted recently. I couldn't share more than this as other parts of the page contains sensitive information that is not out in the internet yet. The whole friggin page is like this. EVERYTHING ROLLS
 25
25 -
My first testing job in the industry. Quite the rollercoaster.
I had found this neat little online service with a community. I signed up an account and participated. I sent in a lot of bug reports. One of the community supervisors sent me a message that most things in FogBugz had my username all over it.
After a year, I got cocky and decided to try SQL injection. In a production environment. What can I say. I was young, not bright, and overly curious. Never malicious, never damaged data or exposed sensitive data or bork services.
I reported it.
Not long after, I got phone calls. I was pretty sure I was getting charged with something.
I was offered a job.
Three months into the job, they asked if I wanted to do Python and work with the automators. I said I don't know what that is but sure.
They hired me a private instructor for a week to learn the basics, then flew me to the other side of the world for two weeks to work directly with the automation team to learn how they do it.
It was a pretty exciting era in my life and my dream job.4 -
Root rents an office.
Among very few other things, the company I'm renting an office from (Regus) provides wifi, but it isn't even bloody secured. There's a captive portal with a lovely (not.) privacy policy saying they're free to monitor your traffic, but they didn't even bother using WEP, which ofc means everyone else out to the fucking parking lot four floors down can monitor my traffic, too.
Good thing I don't work for a company that handles sensitive data! /s But at least I don't have access to it, or any creds that matter.
So, I've been running my phone's connection through a tor vpn and sharing that with my lappy. It works, provides a little bit of security, but it's slow as crap. GET YOUR SHIT TOGETHER, REGUS.
AND WHILE YOU'RE AT IT, CLEAN THE SHIT OUT OF THE FUCKING BATHROOM FFS.
Ugh. $12/day to work in a freaking wind tunnel (thanks, a/c; you're loud as fuck and barely work), hear other people's phone conversations through two freaking walls, pee in a bathroom that perpetually smells like diarrhea, and allow anyone and everyone within a 50+ meter radius to listen to everything my computer says.
Oh, they also 'forgot' to furnish my office, like they promised. Three freaking times. At least I have a table and chair. 🙄
Desk? What desk?
Fucking hell.17 -
It's not that I hate PHP, I just hate the lack of consistency in standard function naming and parameter order, nonsensical attribute access, nearly-meaningless comparison operators, reference handling, case (in)sensitivities, and more!
I mean, look at these functions:
strtoupper(...)
bin2hex(...)
strtolower(...)
And look at THESE FUNCTIONS:
array_search($needle, $haystack)
strpos($haystack, $needle)
array_filter($array, $callable)
array_map($callback, $array)
array_walk($array, $callable)
And let me jUST USE SOME ATTRIBUTES:
$object->attr = "No dollar sign...";
Class::$attr = "GOD WHY";
HOW ABOUT SOME COMPARISONS:
(NULL == 0) // true
(NULL < -1) // ALSO true
Functions AREN'T CASE SENSITIVE (at least variables are).
Wanna dereference? TOO BAD, YOU'LL HAVE TO GET OUT THE TNT.
Alright, yeah, I hate PHP.18 -
Me: "Ugh. Soo insensitive.." *angry muttering*
Curious cousin: "Whom? What? Why?"
Me: "My stupid Mac is not case sensitive so I have to mount a Unix partition and reference it from somewhere else. Why wouldn't they just make a case sensitive filesystem like a proper Unix based OS?"
Clearly uninterested cousin: "seriously?! You called your laptop insensitive? I thought you were talking about a guy" ..
Filthy casuals.6 -
HR: Hey you really need to be more sensitive with what you say
Dev: What makes you bring this up?
HR: Well we had a concerned employee overhear you telling one of the interns that the Russian word for “approved” is “blyat”.
Dev: Ah.14 -
Just wow. I am amazed by what just happened.
A year ago my parents decided to switch from desktop to laptop for convenience. Knowing their needs, i bought them one without an OS and installed Ubuntu 16.04 on it. The thing is that if you do a regular maintenance of the laptop once a year at their partner company, you get additional 4 years of warranty (this offer is amazing).
So today was the day I brought the laptop for this maintenance for the first time. They make you a profile on their support website where you can track shit regarding your device, super convenient. First thing I notice that the login page was not https. Awkward, but there is no sensitive data here so i let it pass. Naturally i forgot my password, so I requested a new one and guess what? I recieved it in plaintext via mail. A tech repair oriented company does this, my god.
I went there, gave them the laptop in question and got a piece of paper, where they wrote that the laptop is in their hands now, and the current physical state of the laptop, and blabla.
I got home and I read what the guy wrote among other things: THE OPERATING SYSTEM IS NOT LEGAL.
How the fuck is Ubuntu not legal??? What the fuck is this shit? I sure as hell didn't torrent it or bought a booteged copy on the streets.11 -
The gift that keeps on giving... the Custom CMS Of Doom™
I've finally seen enough evidence why PHP has such a bad reputation to the point where even recruiters recommended me to remove my years of PHP experience from the CV.
The completely custom CMS written by company <redacted>'s CEO and his slaves features the following:
- Open for SQL injection attacks
- Remote shell command execution through URL query params
- Page-specific strings in most core PHP files
- Constructors containing hundreds of lines of code (mostly used to initialize the hundreds of properties
- Class methods containing more than 1000 lines of code
- Completely free of namespaces or package managers (uber elite programmers use only the root namespace)
- Random includes in any place imaginable
- Methods containing 1 line: the include of the file which contains the method body
- SQL queries in literally every source file
- The entrypoint script is in the webroot folder where all the code resides
- Access to sensitive folders is "restricted" by robots.txt 🤣🤣🤣🤣
- The CMS has its own crawler which runs by CRONjob and requests ALL HTML links (yes, full content, including videos!) to fill a database of keywords (I found out because the server traffic was >500 GB/month for this small website)
- Hundreds of config settings are literally defined by "define(...)"
- LESS is transpiled into CSS by PHP on requests
- .......
I could go on, but yes, I've seen it all now.12 -
Had a discussion with a developer about security. His software transfers all user data (password and files) unencrypted, so anyone can grab them with wireshark. I told him that this is a severe issue. He said no its no problem because if you get hacked its your own fault, because you probably used an insecure network. NO ! YOU FUCKING MALADJUSTED SHEEP-MOLESTING OBJECT OF EXECRATION, YOU SHOULD ALWAYS ENCRYPT SENSITIVE USERDATA NO MATTER WHAT NETWORK YOU USE. FUCKING KILL ME ALREADY.
Not implementing encryption is one thing but then acting like its no problem is a fucking nother one. Why do people not understand that security of userdata is important???11 -
!dev
Me *downloading some weird linux distro to test in VirtualBox - I only do this once a month for like 1 hour*
my brother: Oh my god! Are you downloading something again? Moooom he is downloading something non-stop
every day:
my brother *watching some series/YouTube videos/playing ping-sensitive multiplayer games - all the fucking time, everything he does all day is this + eating and sleeping*
me *retrying multiple times to load anything, including devRant* 😒😠9 -
So... an Italian government website published sensitive data of thousand of citizens, because they thought that it was enough to turn white the text color in order to anonymize the sensitive content of the files. Italy, 2019.
Source (in Italian):
https://wired.it/internet/regole/...6 -
5 years ago, in my first week of starting this particular job, the CTO casually mentioned they'd been struggling with a bug for years. Basically, in the last few days of the year, it seemed that records were jumping a year ahead, with no rhyme nor reason why. Happened every year, and wasn't linked with them deploying new code. (Their code was a mess with no sane way to unit test it, but that was a separate issue.)
I happened to know immediately what might be causing it - so I ran a case-sensitive search in the codebase for "YYYY", pointed out the issue, explained it, then committed a fix all in about 2 minutes.
I was told I'd officially passed my probation.
(Search for "week year vs year" if you're curious & the above doesn't ring any bells.)6 -
I was told that I am too sensitive and afterwards a liability because I couldn’t concentrate in a working space where interns were constantly screaming, running around, hitting and farting each other, throwing shit around and playing games (instead of working)...
I was told by the HR person that “boys will be boys”...9 -
Christmas lights were blinking randomly IN SECTIONS without any sort of "control brick", just with a plain wall plug and TWO wires coming out of it.
In this house we obey the laws of physics, I immediately called magic on this and started digging. I found out that was like five chains of lights wired in parallel, and every chain contained one special lamp that had a thin plate of some thermal-sensitive material inside. It heats up which makes it go straight, thus breaking its chain until it cools down enough to curl again and make the contacts touch.
Brilliant and really cheap way of making randomly blinking Christmas lights without any kind of controller, with just two wires and some physics. That's what I call "nocode". 10
10 -
A Month ago...
Me: when are you going to complete the report
Friend: we can do it in minutes
Me: you can't Ctrl + c and Ctrl +v as there is plagiarism check
Friend: we have spin bot
Me: you do that now itself . if something happens? You can join me .
Friend: just chill
Now ...
Me: done with report
Friend: feeding it to spin bot!
Feeds text related to database security....
Spin bot:
Garbage collector == city worker
SQL statements == SQL explanation
SQL queries == SQL interrogation
SQL injection == SQL infusion
Attack == assault
Malicious == noxious
Data integrity == information uprightness
Sensitive == touchy
.....
Me: told you so...
**spin not == article rewriter3 -
So Tesla employees with access to recordings from customer vehicles have been sharing clips internally whenever something "funny" happened. Including nudity, intimacy, stuff inside garages, and crashes. And some even got promoted for doing this.
If there are any Tesla owners here, grab you cock and start waving at your car so they have to watch it. Or if you don't have a cock, borrow your neighbour's one.
Makes you wonder if other companies handling customer footage for labeling or otherwise are much or any better.
https://reuters.com/technology/...25 -
Old story, and yeah, it's all true, I shit you not!
So here I am at about age 11 (more or less). At the time, I had an almost brand new 333MHz beast, with 8 MB RAM, 2 (!!!) MB video card and (I think) about 300 MB of storage (yeah, I'm old :)) ).
Connected to this monster was sitting a 14" CRT monitor, mechanical keyboard and a 2 button, ball "powered" mouse.
There was no optical tracking tech at the time.
One evening, I notice my mouse starts lagging. Test it to see if Win95 is stuck. Nope, just mouse problems...
Fiddle with it a little, and at some point it stops working at all.
My room was dark now, so I got up to turn on the lights, sat down in front of the PC, and moved the mouse by instinct.
Surprise! It's working again!
My brother comes in and turnes off the lights. Mouse non responsive.
I tell him to turn them on again, mouse works again.
At this point, we were both scratching our heads at this mystery...
I decided to confirm it again using a desc light.
Conclusion: my 2 button, ball tracking, non light sensitive mouse was working only if light was shining directly oh it AND on my 14" crt monitor at the same time!!!
To this day I have no ideea why.
I kept them both for posterity, and they are still there in my parent's attic.
Fin.6 -
!rant
Our lead dev in the company seems to be a smart guy who's sensitive about code quality and best practices. The current project I'm working on (I'm an intern) has really bad code quality but it's too big an application with a very important client so there's no scope of completely changing it. Today, he asked me to optimize some parts of the code and I happily sat down to do it. After a few hours of searching, profiling and debugging, I asked him about a particular recurring database query that seemed to be uneccesarilly strewn across the code.
Me: "I think it's copy pasted code from somewhere else. It's not very well done".
Lead Dev: "Yeah, the code may not the be really beautiful. It was done hurriedly by this certain inexperienced intern we had a few years back".
Me: "Oh, haha. That's bad".
Lead Dev: "Yeah, you know him. Have you heard of this guy called *mentions his own name with a grin*?"
Me: ...
Lead Dev: "Yeah, I didn't know much then. The code's bad. Optimize it however you like. Just test it properly"
Me: respect++;2 -
So my boss booked me a spot at a conference about "the future of online payments" and I received an email with auto created account (there was no sign up) with a clear text password.
I'm feeling pretty confident that I can trust them to guide and advise me on best practices when it comes to handling sensitive information. 8
8 -
PM: Can we have it so the usernames are case-sensitive?
Me: uhh, sure I guess.. But thats like really pointless and adds no real usefulness.. In fact makes the whole logging in thing a tad more complicated for no reason..
PM: Well this one other product we have uses "Admin" for the login versus yours that used "admin" so it needs to be implemented.
(note that mine accepted "Admin" anyways...) *implemented it*
PM: So there's a problem with the username sort, it sorts by capitals then lowercase.. eg:
alpha
beta
Alpha
Me: Yeah, you asked for case-sensitive usernames..
PM: Well can you fix it?
Me: I could create a second field within the user data that is the username in all lowercase and sort by that. But that negates like all of the whole case-sensitive usernames thing.. OR I could drop all this actually important work I'm doing and do a whole bunch of work on a custom sort for this useless fucking feature you wanted me to put in..
*it's been 2 weeks and still no reply...* -
The deeper I go down the infosec rabbit hole, the more I worry about my doctors still using Windows XP. Why would you save sensitive patient info in those....shoe boxes?
 4
4 -
My university has impeccable data management. I needed to ssh into their Linux server for an assignment but it refused to accept my login. Which was weird because I could login to the same account on one of our websites just fine. I typed my password into a text file and then copy and pasted it into both logins. The Linux one failed but the website succeeded. After some experimentation it turns out that the Linux server only recognized my username if I typed it in all lowercase, even though when I created the account it had uppercase characters as well.
So let me walk you through the sloppiness that had to have occurred for this to happen. When I first created the account it must have ignored what I entered and just saved the username in all lowercase without communicating that to me. Then the websites that use this account must either ignore case for usernames or lowercase the user input before querying the database. Finally, the Linux server, despite knowing that all the usernames are lowercase, is case sensitive and won't recognize the username as I originally typed it in.
Can you guess what department manages the account, website and Linux server? The Department of Computer and Information Science. Incredible.2 -
// Rant
I can understand that people accidentally commit something sensitive to GitHub, I did it too once, but ...
WHY THE FUCK DO YOU MAKE YOUR MISTAKE WORSE BY MAKING IT SEARCHABLE VIA THE GLORIOUS COMMIT MESSAGE OF "REMOVING PASSWORD"
... seriously just google "git remove password" and there is a step by step guides on how to remove sensitive data from git.
Reference (320,006 free passwords):
https://github.com/search/...9 -
All the cunts with their strong cologne mixed with cigarettes smell should have cut off their noses like Voldemort.7
-
Well... I feel insanely stupid because I've been using windows for years an just realised that the file system isn't case sensitive... Mother fuckers...
(Yes judge me, I am a twat)7 -
Finally fixed a major bug.....
FUCK YOU C# AND YOUR FUCKING CASE SENSITIVE BULLSHIT.
DAYS
THAT TOOK FUCKING DAYS AND AT NO POINT DUD VISUAL STUDIO BOTHER TO MENTION THAT FUCKING ERROR.
1 CHARACTER, ON ONE LINE, EFFECTIVELY BROKE THOUSANDS OF LINES OF CODE
fuck this, I quit. See you next time you contact the Microsoft live support chat!13 -
Getting ready for GDPR at work. I had to explain to my bosses what it meant, especially regarding one of our project where we store a lot of user data. Then I heard it: "this crap doesn't regard us. we have no sensitive data. we only save out users' name and generalities.". I have no words.3
-
So you want to collect and save sensitive data from psychologists sessions and use Wordpress. What can go wrong.2
-
I can't believe people are willing to scan their faces, fingerprints, and retinas on their phones.
Such data is very sensitive as it can't be changed easily.
CCTV is now everywhere and everyone has his own scanner providing data for tracking people.
Am I too paranoid?6 -
Watch out for these fucking bug bounty idiots.
Some time back I got an email from one shortly after making a website live. Didn't find anything major and just ran a simple tool that can suggest security improvements simply loading the landing page for the site.
Might be useful for some people but not so much for me.
It's the same kind of security tool you can search for, run it and it mostly just checks things like HTTP headers. A harmless surface test. Was nice, polite and didn't demand anything but linked to their profile where you can give them some rep on a system that gamifies security bug hunting.
It's rendering services without being asked like when someone washes your windscreen while stopped at traffic but no demands and no real harm done. Spammed.
I had another one recently though that was a total disgrace.
"I'm a web security Analyst. My Job is to do penetration testing in websites to make them secure."
"While testing your site I found some critical vulnerabilities (bugs) in your site which need to be mitigated."
"If you have a bug bounty program, kindly let me know where I should report those issues."
"Waiting for response."
It immediately stands out that this person is asking for pay before disclosing vulnerabilities but this ends up being stupid on so many other levels.
The second thing that stands out is that he says he's doing a penetration test. This is illegal in most major countries. Even attempting to penetrate a system without consent is illegal.
In many cases if it's trivial or safe no harm no foul but in this case I take a look at what he's sending and he's really trying to hack the site. Sending all kinds of junk data and sending things to try to inject that if they did get through could cause damage or provide sensitive data such as trying SQL injects to get user data.
It doesn't matter the intent it's breaking criminal law and when there's the potential for damages that's serious.
It cannot be understated how unprofessional this is. Irrespective of intent, being a self proclaimed "whitehat" or "ethical hacker" if they test this on a site and some of the commands they sent my way had worked then that would have been a data breach.
These weren't commands to see if something was possible, they were commands to extract data. If some random person from Pakistan extracts sensitive data then that's a breach that has to be reported and disclosed to users with the potential for fines and other consequences.
The sad thing is looking at the logs he's doing it all manually. Copying and pasting extremely specific snippets into all the input boxes of hacked with nothing to do with the stack in use. He can't get that many hits that way.4 -
Am i the only one who is so sensitive about indentation? It really pisses me off when i see code with bad levels of indentation because it completely overtakes my years of programming experience and i understand nothing. Also indentation level should be 4, not 2. Who the hell uses 2 level indentation, you don't deserve a keyboard.9
-
Inappropriate experience at work: One of our project managers got arrested one day for fraud. Apparently an employee had been in the middle of an online purchase and walked away from their desk. He happened to see the unmasked entry of the CC info (this was before websites cared about masking sensitive form inputs). I guess the temptation was too great…and he was too stupid to realize he’d get caught…and he jotted it all down. He made thousands of dollars in purchases which, naturally, eventually led back to him.
The same guy, before he got arrested, had made a joke when someone in an office team email said “Feel free to have some cake in the break room.” He replied “No need to do anything to me for the cake.” His first name was “Free”.4 -
The company that I currently work for has a strict clean-desk policy. So strict, there's even have a little booklet that they have about 1000 copies of lying around the office everywhere. In the booklet is a playful description (with cartoons!) of what can go wrong when sensitive information is lying around, or shared with outsiders through careless talk, etcetera. Employees are encouraged to take a copy of the booklet home.
Also in the booklet is a description of the importance of having a good password. It mentions the required minimum (x) and maximum (x+1) length of passwords, mandatory character classes, and how often the passwords have to be changed.6 -
Jesus Christ Reddit really is full of some sensitive ass basement dwelling retards. God forbid someone doesn't contribute to the circle jerk mentality that literally every fucking subreddit has.
I bet SO users spend their free time there.11 -
WELL GEE, IF I KNEW WHAT MY ACCOUNT USERNAME WAS, I WOULD JUST SIGN IN YOU ASSHOLE. -.-
On top of that, they use these fucking anchent capchas that are fucking case sensitive and annoying as hell..
In their defence, I was trying to automate their website (one of those get paid to click sites) in an atempt to get some money, but still! 6
6 -
WTF!!!!! I officially have someone trying to extort me just had this in my email box this morning!
--------
Hello,
My name is [name removed], I'm an IT security expert and I found a security issue on your website.
This email is personal and in no way related to any of my employers.
I was able to access to a lot of files which contains sensitive data.
I attached a screenshot of the files I found to this email.
I would be happy to give you the method I used to access these files in order to let you fix it.
Would be a monetary compensation possible?
Please forward this email to the right person, if your are not responsible for the security of the website.
Best Regards,
[name removed]
---
He can basically see the contents of my wp-config.php. How has he managed this?71 -
Trying to explain functions to my coworker and why they should be used even if powershell scrips don't 'need' functions
I've explained it 5 different ways across multiple meetings when they've gotten stuck on something.
At this point I've decided 1. I don't have the patience or brains to be a teacher..., 2. I'm going to have to review every script they ever fucking write, 3. I'm never letting them work on anything critical or time sensitive for big clients. (Small clients ehhh) I'll fight my boss to avoid that headache lol6 -
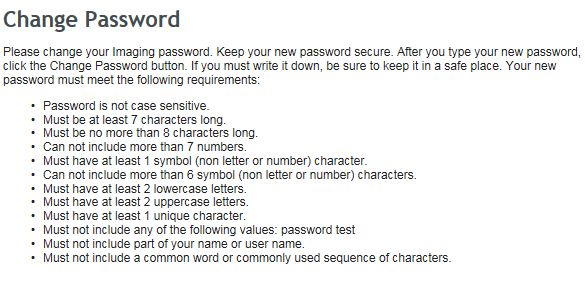
So, among the ridiculously long list of password requirements, password is not case sensitive BUT it has to contain uppercase and lowercase letters?
 14
14 -
Apparently USPS tracking numbers are case sensitive... I missed a delivery today so went online to check the status.
The code was RAxxxxxxxxxxxxxxxxxxxTR
x=numbers
I first typed the letters in lowercase and it said package not found...
Really???!!!!!! Don't you think all those numbers are already too long...3 -
Using pokemon exeption handling on some very important and sensitive back end stuff to meet a deadline.7
-
What in the unholy fuck is going on with the world!!
I get how our personal lives and data are bloody good at being used against us and tracking our behaviours but fuck Facebook won't let "good enough" alone and are coming back out with a new way to pay for our most sensitive data. Everything on your phone!
What more could they possibly want from knowing what,where,who,why,when, and probably even how we are shitting in a back ally besides controlling the masses
- no I'm not a privacy nut, just a concerned citizen -
https://theverge.com/2019/6/...3 -
<supervisor>,
I would like to raise a concern of mine to your attention. I would urge you to inform <CIO> because I think he should know as well. In our recorded meeting this afternoon <bad_vendor> exposed another company’s credentials after failing to access our system, and proceeded to demo access into someone else’s system while exposing their client's sensitive data. Others noticed this as well. This is an alarming situation because not only did <bad_vendor> expose someones data to <us>, but to one of our vendors. While it is unlikely that <us> or <helpful_vendor> would abuse this situation, it could have easily been <us>’s data that was exposed to another company and their vendors had the situation been reversed. I understand we are all under tight deadlines and under a lot of stress — by no means am I trying to make waves — but nonetheless I felt compelled make light of this situation and felt in was echoed by <helpful_vendor> during the meeting as well.
Thank you8 -
Did you hear that GitHub is planning to rename racially sensitive terms like "master"?
My two cents: rename master to daddy. xD10 -
today i was asked to encrypt a public key, because "it's sensitive info".
a PUBLIC key.
smh
it's not even hard (literally 1 line of code), but come on...6 -
So we have an API that my team is supposed send messages to in a fire and forget kind of style.
We are dependent on it. If it fails there is some annoying manual labor involved to clean that mess up. (If it even can be cleaned up, as sometimes it is also time-sensitive.)
Yet once in a while, that endpoint just crashes by letting the request vanish. No response, no error, nothing, it is just gone.
Digging through the log files of that API nothing pops up. Yet then I realize the size of the log files. About ~30GB on good old plain text log files.
It turns out that that API has taken the LOG EVERYTHING approach so much too heart that it logs to the point of its own death.
Is circular logging such a bleeding edge technology? It's not like there are external solutions for it like loggly or kibana. But oh, one might have to pay for them. Just dump it to the disk :/
This is again a combination of developers thinking "I don't need to care about space! It's cheap!" and managers thinking "100 GB should be enough for that server cluster. Let's restrict its HDD to 100GB, save some money!"
And then, here I stand trying to keep my sanity :/1 -
mangodb's rant reminded me of smth.. Folks from my country might remember this story.
So we have a national e-health system. Millions have been invested, half of the money have never reached the project [disappeared smwhr in between] and its quality is not shiny. It works, sometimes even fast enough. But boy does it have bugs... Let's not get into that. It's politics.
So some time ago one IT guy spotted a bug that allowed him to get sensitive info of other patients. He informed e-health folks and waited for a fix. He waited for a few weeks but the fix had never been released. So he published his findings in soc media [yepp.. Stupid move]. That caused a national scandal. Not to mention he had been pressed with charges.
That guy and our health minister were invited in one of the tv debates. The guy was asked to explained how he found all this sensitive data. And he explained that he hit f12 in his browser, opened a network tab, issued a network request by clicking smth in the webpage analysed received data in the dev tools.
The minister looked somewhat happy, maybe a lil proud of himself - a person who has a "gotcha!" moment has that very glow he had. And he said: "what you did there was obvious hacking. I reckon you should know that true developers do not do those things you have just explained to us" [he was talking about dev tools].
I died inside a little bit.3 -
We live in a world where WEAKNESS has become a virtue.
- I'm oppressed!
- My mental health!
- I need a helper!
- I'm sensitive!
- You're fatphobic!
- <INSERT SJW's IDENTITY term>
In today's world, you score more social points for describing yourself as weak & blaming 'oppressors' for your miserable life12 -
Paranoia. Programming affected my life by making me paranoid. Creating a new account on any website that even needs rudimentary information about me has to go quite some vulnerability testing since I've seen enough hack jobs that throw around sensitive data because they're too incompetent to follow simple must dos.3
-
My first interview ever for an internship. The interviewer asked me to rate myself in this language from 1 to 10 as if I'm applying for a lead engineer position at Google. I replied with a number that I thought was appropriate at the time (but now I know it wasn't accurate). The interviewer didn't say anything and moved to the next question. Later, I found out he ranted about my answer on his Twitter, again as if it's expected from an applicant intern at a low tier company to know. Still leaves a bitter taste in my mouth 7 years later.8
-
One of my customers' laptop background (removed sensitive information and desktop icons).
Coworker: When you really love Chrome, but don't know what hi-res is! 8
8 -
"Let‘s make a service where the users can enter all of their secrets and sensitive data so that we can warn them if that data has been leaked elsewhere"
What could possibly go wrong?2 -
"Unix filenames are case-sensitive?! Hur hur, that must be really confusing!"
Well, no, if you're not a fucking mouth-breathing cretin it isn't.2 -
I have a few of these so I'll do a series.
(1 of 3) Public privates
We had a content manager that created a content type called "news item" on a Drupal site. There where two file fields on there. One called "attachments" and the other called "private attachments". The "private attachments" are only for members to see and may contain sensitive data. It was set to go trough Drupals security (instead of being directly hosted by the webserver) but because the permissions on the news items type where completely public everybody had access. So basically it was a slow public file field.
This might be attibuted to ow well Drupal is confusing. Howerver weeks earlier that same CM created a "private article". This actually had permissions on the content type correctly but had a file field that was set to public. So when a member posted the URL to a sensitive file trough unsafe means it got indexed by google and for all to read. When that happend I explained in detail how the system worked and documented it. It was even a website checklist item.
We had two very embarrassing data leaks :-(1 -
This is from the 70s. It can easily be updated to the present day, but it has a certain charm just the way it is:
Three women sat discussing their husbands and their sex lives.
"My husband's a wrestler," said the first. "He's really strong and aggressive in bed."
"My husband's an artist," said the second. "He's really gentle and sensitive."
"My husband's an IBM salesman," said the third. "He sits on the edge of the bed and tells me how good it's going to be when I finally get it." -
Our company is changing the default branch on our main repo from master to main.
We're literally on the verge of global genocide and a holocaust, and people are worried about over-sensitive people's feelings. I'm sure a branch change will end racism.5 -
Whoever at Zoom decided that this button needed to be at this location on the Touch Bar ought to be fired.
Out of a cannon.
Into the sun.
Or at the very least doomed to have their desktop or webcam shared at random times during sensitive meetings. It is for the grace of God that the client didn’t catch me straining to hear the awful acoustics in their conference room. 7
7 -
Fuck you Intel.
Fucking admit that you're Hardware has a problem!
"Intel and other technology companies have been made aware of new security research describing software analysis methods that, when used for malicious purposes, have the potential to improperly gather sensitive data from computing devices that are operating as designed. Intel believes these exploits do not have the potential to corrupt, modify or delete data"
With Meltdown one process can fucking read everything that is in memory. Every password and every other sensible bit. Of course you can't change sensible data directly. You have to use the sensible data you gathered... Big fucking difference you dumb shits.
Meltown occurs because of hardware implemented speculative execution.
The solution is to fucking separate kernel- and user-adress space.
And you're saying that your hardware works how it should.
Shame on you.
I'm not saying that I don't tolerate mistakes like this. Shit happens.
But not having the balls to admit that it is because of the hardware makes me fucking angry.5 -
DXB (airport)'s WiFi doesn't let you call through whatsapp or telegram or even discord. It also does not let you send a whatsapp voice message, which has me very puzzled.
And all I wanted to do was to call my mom. ☹️
(I might also be running a slight fever, which makes me very emotional and sensitive)10 -
Had a conference call and one of the guys said something along the lines of "I can handle the load (ticket load)" didn't even thought about it my mouth instinctively reacted with "that's what she said".
A couple of guys laughed but the other few just "wooooow"ed like if I had thrown a 9/11 joke.
This is not a rant perse, just a reminder that if I ever launch my own startup I shall look to hire "joke sensitive" people to make my scrum meetings as awkward as possible.4 -
I don't want to put anyone to shame here, but this has been the most hilarious password reset in my life.
P.S.
It's an early service with no sensitive data, so I'm not concerned so much, but still, a system for automatic password reset, with the ability to change the temporary one, should be one of the first things in place before you go public. lol 4
4 -
PyTorch.
2018: uh, what happens when someone uses a same name attack? - No big deal. https://github.com/pypa/pip/...
2020: I think that's a security issue. - Nanana, it's not. https://github.com/pypa/pip/...
2022: malicious package extracts sensitive user data on nightly. https://bleepingcomputer.com/news/...
You had years to react, you clowns.5 -
Client: MY PASSWORD DOESN'T WORK
Me: our passwords are case-sensitive
Client: YES I USED CAPS LOCK1 -
Interesting. A few hours ago I had a nice domestic conversation with my coleague about robot vacuum cleaners. He was talking about iRobot Roomba and I was talking about Xiaomi. Here's the result!
Interesting thing is that we talked in a *voice* conversation. Over Slack. Over Chrome. Over corporate VPN (openconnect).
Where's the spying link? Slack or Chrome?
My bet's on Chrome.
What does that tell you about the privacy of your sensitive conversations? :)
Hide behind VPNs all you like. If you have proprietary software (or hardware in the case of Huawei) - you're being watched and listened to.
EDIT: I'm on Linux, he's on MacOS 9
9 -
Your guide to passive-aggressive false apologies:
- I’m sorry you’re so sensitive
- I’m sorry that you think I did something wrong
- I’m sorry if you’re mad
- I’m sorry that you made me do it
- I’m sorry you feel that way
And, my most favorite:
- I’m sorry that you’re making such a big deal out of this.12 -
Renting a flat above a kindergarten.
I hate Christmas songs and I am very sensitive to high pitched noises.
It's a bad time in the year to be working from home...3 -
pushing sensitive data to GitHub repo...not realising for days...and then going through the painful process of removing it again 😑4
-
As usual a rather clickbait title, because only the chrome extensions (as always) seem to be vulnerable:
"Warning – 3 Popular VPN Services Are Leaking Your IP Address"
"Researchers found critical vulnerabilities in three popular VPN services that could leak users' real IP addresses and other sensitive data."
"VPN Mentor revealed that three popular VPN service providers—HotSpot Shield, PureVPN, and Zenmate"
"PureVPN is the same company who lied to have a 'no log' policy, but a few months ago helped the FBI with logs that lead to the arrest of a Massachusetts man in a cyberstalking case."
"Hijack all traffic (CVE-2018-7879) "
"DNS leak (CVE-2018-7878)"
"Real IP Address leak (CVE-2018-7880)" 7
7 -
Dont become a dev if you:
- Cant sit in the office for 8-10 hours a day
- Dont know how to google information/ errors, instead you interrupt your teammates with stupid questions every 5 minutes
- Are a perfectionist and don't like constant change.
- Are neurotic and give up easily. If you get triggered about broken or messy things to the point where it ruins your day to you and everyone else around you. You need to separate your work from your life.
- Don't have good communication skills. Worst I saw was a guy who speaks with a stutter(nobody understands him) and also writes very poorly (nobody understands his emails). Also he gets very angry when you ask additional questions to clarify what he said. How can you work with someone like that?
- Are very sensitive to critique. I prefer someone telling me that my code is shit and telling me why, instead of feeding me delusions and false validation.
- Dont know how to balance working in team and working solo. Nobody likes lone wolfs who are arrogant and not in sync with the team. But also nobody likes to drag teammates who cant think for themselves and even after years of spent in the field are required constant spoonfeeding because they are unable to google and teach themselves with trial and error.14 -
I came around the corner in the corridor where a senior PM talked with an engineer.
PM: ... and that's why a good team is so important and we also need sensitive people.
Me: do we have some here?
PM: oh yes, I'm highly sensitive.
Me: one learns something new every day. :-)1 -
Had anyone experienced with an impatient boss who require you to complete the project in the month you just recently got hired?
Here's the story, I recently got hired by a company, joined on 1st April 2022, the boss expect me to complete the app for Android and iOS by the end of this month. (An e-commerce applications exactly like shopee.com) Without providing me the Backend ApI , that they mentioned. They just gave me a and expect me to know what's happening at the backend.
He require me to give him a specific date that I can launch the app to play store and Apple store. (From my experience, it take days, weeks or months). He need a milestone of what I need , did , and will do (which predictably that they will reject any new ideas proposed) .
I even considering to quit, but I need opinions. Am I just too sensitive or there's something wrong?13 -
A while back we had some time sensitive work I was doing in overtime, the work was purely functional and the front end had not yet been done. It went to QA to test the functionality and the only feedback I got was UX oriented.
I tried to explain on 3 occasions that the looks was not important in the slightest at this stage, and just try to break it. I then got a lecture that it wasn't an optimised layout and was shown the AA route finder as an example of how the tester thought it should look.1 -
Long time no rant.
Rant::beginRant();
How do people who are, I think, supposed to have a knowledge of what the fuck they're doing, keep their work without knowing what the fuck they're doing?
You're telling me that you have been hired as a "full-stack developer", yet you can't build a motherfucking Vue page over SSH (not even talking about automated deployment, just the most bare bones approach)? You don't know how to deploy a Laravel project? You don't know that Linux server paths are case sensitive? You can't read the log files?!
Rant::commitRant();9 -
Does anybody here know of some sort of blackout glasses? (which cover the entire eyes, not sunglasses which do exist in high filters, but leak sunlight at the bottom, top and sides)
My recent lifestyle has lead me to absolutely dying at the morning when I go sleep, because of the extreme sunlight, peaking through all cracks.
I am just fine during the day when I do my walks or drive to the store etc, but after a long night I just get very light and sound sensitive.
I think a decent amount of years ago, I saw somebody use some sort of small scale welding goggles for something similar, but I can't find any that are dark enough or aren't costing like buying a beach house in malibu.
Also "photophobia glasses", which actually seem to be for that purpose, cost like two malibu beach houses and a helicopter to top it off, because they abuse and cash on the fact that it has remote help to people that suffer from it.
I did also try just using blackout curtains for that purpose, but as said, there's always that one small crack where it leaks through and absolutely flashbangs me.
So it would be nice to have some glasses that filter pretty much 99% of light, but still allow me to navigate through my appartment, without having to break a leg or crack my neck (which would solve the problem atleast)22 -
A good life lesson:
1. DON'T DELETE FILES YOU MAY WANT TO RECOVER
And if you DO delete them and then recover them, then
2. DON'T SEND THE RECOVERED FILES TO A·N·Y·O·N·E
Today I found a lost µSD card in the street. I did what every sane person would do -- plugged it into my laptop :)
There I found a directory with recovered pictures. I figured, some of them may contain the author's info in metadata, so I ran a quick plaintext search for @gmail.com.
Turns out, inside some of the recovered picture files I could find embedded company director's emails in plain-text. I mean, open the picture with a text editor and read through those emails - no problem! And these emails contain some quite sensitive info, e.g. login credentials (lots of them).
Bottom line, if you delete and recover your files, then do your best to keep them close: don't share them, don't lose them. You might be surprised what these recovered files may contain12 -
I need someone to make me a list of things I am not allowed to say and who I’m not allowed to say them to at work. This is getting ridiculous. Every time I turn around someone is making this face at me 😬 and saying “Don’t say that to that team” or “Don’t say that to this person”. I can’t do my work right if I have to keep censoring myself on everything people find organizationally sensitive.16
-
I've written a rant that was too long to devRant, so I made it into a medium article instead. You can read it here:
https://medium.com/bambuu/...
In short, it's about Apple's weird legal practices when it comes to Apple Developer accounts.
tl;dr
- Apple has "obvious" security reasons that requires a copy of a photo id, and you aren't allowed to conceal sensitive information
- Apple's favorite form of communication is fax and snail mail
- Apple needs multiple signatures and court documents to just change your account name. -
Speaking of.. What in your opinion would be an appropriate way to warn someone about security problems, like db passwords in git?
I once came across dozens of extremely sensitive services' infra accesses: alibaba/aliexpress, natuonal observatories, gov institutions, telecomms, etc. I had dozens [if not hundreds] routers' and firewalls' credentials along with addresses. I tried one to confirm validity - it worked. I wanted to warn them but did not want to get in trouble.
If it were servers, I'd set a motd or append some warning messages in .profile. But not sure how to do it for non-server devices
what would you do? How would you warn them?
P.S. Deleting that record was a smart move, buddy ;)
p.P.S. Sorry, wrong category... Can't edit now :(6 -
When you’re use to dark theme and the lights in your car are too bright, you black electrical tape all the things...
I’m either more sensitive to light, or I’ve adapted to dark theme-ing all the things.20 -
Do you know what angers me more than anything else ?
Wasted potential. Thats what. That there are people out there that look at their bank account and see a large number and spend large amounts of time finding ways to push people down during sensitive times where they could be learning and growing and have the right attitude and energy to do so, just because it makes their horrible selves feel secure knowing how 'superior' daddy made them, not to mention likely factories filled with half naked Chinese kids sewing shoes and soccer balls and separating out precious metals with blow torches.
I cannot help but think about this again as I'm frustrated that I had to relearn something just now which created more questions which I once everything is dashed to pieces again I won't think to or know to look into, if the information even exists, all so some easily duped younger people can form the next generation of well... us, and fall for the same tricks while I feel like I'm falling behind.3 -
Having to rely on individuals who frequently use the words "thing" or "thingy" to convey important time sensitive information.
Nothing is more infuriating.6 -
Ah transports
Minding my own business in a crowded train, listening to full blast music. As the song changes I sort of heard an announcement but didn't get the subject.
Guy in front of me does a 180° and starts talking to me. I thought he wanted some guidance, so I removed my headset and never did I regret more doing that, that guy just went on and on about his life and stuff that I don't care about, until he got off his stop. Ironically, before he left off he said "you know my mama always told me that you should ignore people you're not interested in" (Forest Gump Swiss edition? He didn't have a box of chocolates though)
I was like "yes, fuck off, not interested in your bullshit", but well, noticed he might be sensitive.
After he left some teens just came and pretended I didn't exist as they invaded my corporal space. Pushed one gently as he was leaning on to me a bit too much.
People must see me as a help point, you know those terminals where you can browse stuff... That's me. The Father of them all.2 -
In today's episode of kidding on SystemD, we have a surprise guest star appearance - Apache Foundation HTTPD server, or as we in the Debian ecosystem call it, the Apache webserver!
So, imagine a situation like this - Its friday afternoon, you have just migrated a bunch of web domains under a new, up to date, system. Everything works just fine, until... You try to generate SSL certificates from Lets Encrypt.
Such a mundane task, done more than a thousand times already... Yet... No matter what you do, nothing works. Apache just returns a HTTP status code 403 - Forbidden.
Of course, what many folk would think of first when it came to a 403 error is - Ooooh, a permission issue somewhere in the directory structure!
So you check it... And re-check it to make sure... And even switch over to the user the webserver runs under, yet... You can access the challenge just fine, what the hell!
So you go deeper... And enable the most verbose level of logging apache is capable of - Trace8. That tells you... Not a whole lot more... Apparently, the webserver was unable to find file specified? But... Its right there, you can see it!
So you go another step deeper and start tracing the process' system calls to see exactly where it calls stat/lstat on the file, and you see that it... Calls lstat and... It... Returns -1? What the hell#2!
So, you compile a custom binary that calls lstat on the first argument given and prints out everything it returns... And... It works fine!
Until now, I chose to omit one important detail that might have given away the issue to the more knowledgeable right away. Our webservers have the URL /.well-known/acme-challenge/, used for ACME challenges, aliased somewhere else on the filesystem - To /tmp/challenges.
See the issue already?
Some *bleep* over at the Debian Package Maintainer group decided that Apache could save very sensitive data into /tmp, so, it would be for the best if they changed something that worked for decades, and enabled a SystemD service unit option "PrivateTmp" for the webserver, by default.
What it does is that, anytime a process started with this option enabled writes to /tmp/*, the call gets hijacked or something, and actually makes the write to a private /tmp/something/tmp/ directory, where something... Appeared as a completely random name, with the "apache2.service" glued at the end.
That was also the only reason why I managed fix this issue - On the umpteenth time of checking the directory structure, I noticed a "systemd-private-foobarbas-apache2.service-cookie42" directory there... That contained nothing but a "tmp" directory with 777 as its permission, owned by the process' user and group.
Overriding that unit file option finally fixed the issue completely.
I have just one question - Why? Why change something that worked for decades? I understand that, in case you save something into /tmp, it may be read by 3rd parties or programs, but I am of the opinion that, if you did that, its only and only your fault if you wrote sensitive data into the temporary directory.
And as far as I am aware, by default, Apache does not actually write anything even remotely sensitive into /tmp, so...
Why. WHY!
I wasted 4 hours of my life debugging this! Only to find out its just another SystemD-enabled "feature" now!
And as much as I love kidding on SystemD, this time, I see it more as a fault of the package maintainers, because... I found no default apache2/httpd service file in the apache repo mirror... So...8 -
One of our customers wants our mobile app to log out the user after 15 minutes of inactivity because of SeCuRiTy…
Why? The phones protect the apps with their hardware encryption from any malicious access.
And we are not dealing with super sensitive data here like some banking app or so.
Why do some people want to have bad UX for no reason?12 -
So today I found a file share containing some super super sensitive information accessible to what I think was our entire user base (6,500 users) if you knew the server name and had an interest in nosing around.
I reported it to our head of IT and heard nothing after, although 5 mins after reporting I could no longer access...
I suspect the infrastructure lead is going to be a dick (because his one of them awkward non team player kind of guys) and not thank me for preventing our company from being in national news papers... but try to spin it on why am I nosing around his servers in the first place..
I actually feel 50/50 about if I should of told or not.. but on flip side, I guess the access logs of me listing the files as I flick through to confirm my suspicions would of caused s bigger headache.
Fucking useless infrastructure engineers!9 -
This is my #wk110 about a project from when I was a real n00b. It can also be read as a rant about myself.
So I decided to code my own terminal based password manager. Because, you know, whom can you trust the most; yourself or some random password manager from the internet?
Obviously, encryption plays a major role when storing such sensitive information. So n00b me decided to go with Base64.
Base64.
I developed a password manager that stores your passwords in Base64 format.
What must I have thought?!
Perhaps the gibberish looks of Base64 encoded data made me think that this actually is encryption.
After having realized my stupidity, I quickly replaced Base64 with AES and more recently I completely rewrote the whole project which is now also available on gitlab: https://gitlab.com/bitteruhe/sesame
This act of stupidity still embarrasses me every time whenever I think about it, though. -
So new job started.
Just for context- old company was shit.
Promised the world but.
No benefits.
Terrible project management.
High pressure.
But green field interesting work (except by now it’s a few years in so it’s a ‘browning’ field but I was on it from the start).
New company first impressions..
Seems a fantastic company.
True to their word they have money for tools.
Making time for personal development.
Much bigger development community/department.
Seems like the term are under far less pressure so far at least.
But a MASSIVE amount of tech debt.
People seem to want to do the right thing and they’re making time to try and deal with it.
But one or two are very opinionated as to how to deal with it.
So this could go either way and only time will tell I guess.
Trying not to over analyse every little thing they say but I’m hyper sensitive to it at the minute while in the early days.
As always the real challenge in IT is the people not the tech. I count myself as part of the problem, sure I will form some opinions and sharing them too.3 -
A conversation between an offshore developer and his manager at a fortune 500:
I'm a software developer and the company I work for is a vendor for $manager's and $offshore_dev's company. They provide endless hours of entertainment/terror. Recently, we've been trying to convince them that they need to stop sending sensitive information plaintext over HTTP and set up TLS/HTTPS which has led to tons of fun conversations such as this one they had during a conference call:
* $manager: "Did $offshore_dev implement TLS1.2?"
* $offshore_dev: "Yes, we enabled a parameter in the code to enable TLS1.2 in the code but according to $me's email, this requires HTTPS in order to work."
* $manager: "No this works, we're using TLS in $other_application right now."
* $offshore_dev: "Well, $manager, it's implemented but it currently doesn't encrypt anything as such."
* $manager: "Okay, HTTPS is in the roadmap in the next quarter, we can move forward without this for now."4 -
I just remembered an annoying experience I once had,
Wanted to know cli version asap (due to some bug introduced in a certain version):
-v (output: view --help for command)
--version (output: view --help for command)
FUCK
--help (revealed: -version)
Wanted to know it's dependency version:
-version (output: view --help for command)
FUCK
--help (revealed: version)
You could call me lazy for not always typing --help first but there must be a standard for this time sensitive command.1 -
When Amazon asks if my email address is all lower case... The desire to make it an informative moment that email addresses are not case sensitive is outweighed by my desire to resolve my issue as fast as possible.1
-
!rant
I was playing with adb logcat some apps and I saw some sensitive info from my bank app. So I decided to go deeper , I saw my entire banking information , WHAT THE FUCK? I feel unsafe now using this bank.
Btw this bank is using react native and forgot to obscured their code in production 6
6 -
How it started:
Need to replace in a lot of SQL files certain stuff...
find . -type f -iname '*.sql' -exec sed -i 's|new|old|g' {} \;
12 hours later that find executed a shell script containing roughly 120 lines of text pipelining.
The jolly of inconsistent workflows.
Different SQL format stylings... Makes fun when single line string replace needs to be extended to multiline RegEx handling. Or matching SQL comment configuration..
Different line endings. MacOS, Windows, Unix, Bukkake.
Different charsets / collations. Anyone wants latin1_swedish_ci... utf8... utf16... :/
Realizing some people even left sensitive data inside the SQL files (e.g. API Tokens..... Yayyyyyyy).
...
Ugh. It's never a one liner. It's never easy. -.-
I hate cleaning up messy shit.2 -
”We’re not going to shuffle you (devs) around from project to project and definitely not taking on any new time-sensitive projects with the limited resources we have, seriously understaffed as we are atm” - that was the promise.
So today I got assigned to a time-sensitive project (unconditional deadline by the end of the year) on a product I am not at all familiar with... I almost believed 2 projects underway was enough so that it would not get assigned to me. Oh well, there’s always room for a 3rd.
At least I get to pick my tools so I get to try out Fable... a silver lining there, and not really a thin one.3 -
This codebase had 50+ main() functions and 80+ Material App. 5 of them are nested MaterialApp
Redundant widgets, security leaks, and print Sensitive information from the server to console without using (kDebugMode), therefore in prod, the data are leaked.
I refactored until I screamed.
So I left a gift inside.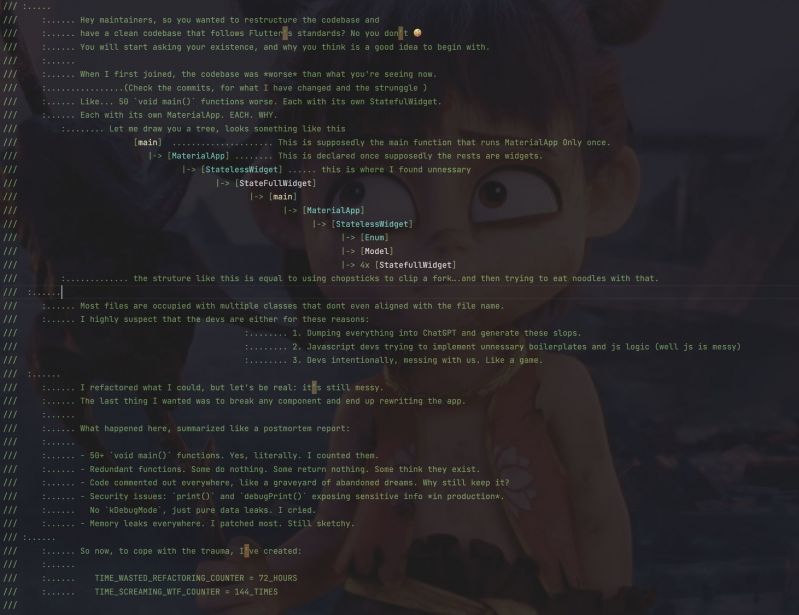 14
14 -
Ibwish I had remembered this when the weekly theme was office pranks.
In the first or second year of high school we covered basic internet security. Stuff like don't follow suspicious urls, don't open suspicious emails and such.
Our teacher let us play around with some sort of simulated desktop environment, where we could execute some hacks like ad popups and such on each other's environment, if we fell for the trap.
Anyways, one hack I found interesting was a hack, that lockes a user out of their virual desktop, until he enters a password, that will be displayed on his environment.
Yes, a very interesting hack, because it contains two obvious yet major design flaws, which I could exploit 😈
1. It's case sensitive
In itself not a problem, but combined with #2, it's fatal.
2. "IlIlllIlI"
Depending on your font, you probably have no idea what exactly I just typed.
Let's just say, the font displayed uppercase i and lowercase L completely undifferentiable.
Guess whom I let suffer.
It was our teacher, who had to demonstrate us some things and who was connected to the same network.
I swear, nothing beats that feeling when your tearcher has go come to you and embarrassingly ask you to "unhack" them, because they can't type it 😂1 -
Light Shot is the worst app and website ever .... No privacy
So I write a simple PHP script for Windows machine, to randomly generate integer and char for randomly open URL.
By running ```php run.php``` you able to see some sensitive information sometimes.
Refer https://github.com/johnmelodyme/...5 -
I haven't said anything yet, but an AltRant notification server exists. Support for it will arrive very very soon on the AltRant app. It will run locally on the end user's personal computer, and it does not require a constant connection to the phone. Both devices need to be connected to the same local network on first connection, but after that you can wander out of your house or disconnect from the local network and still receive notifications.
DISCLAIMER: ALL SENSITIVE USER CREDENTIALS ARE NOT STORED *ANYWHERE* EXCEPT ON THE LOCAL USER'S MACHINE. NO DATA IS SENT TO ME. THE SERVER IS OPEN-SOURCE, HAS NO RELEASE BINARIES AND RUNS ON PYTHON.
Note to @dfox: if you want this to not exist or not be supported inside AltRant, please tell me or send me an email about it.2 -
Just found out today via Reddit that Wells Fargo, American Express (not personally confirmed), and Chase login passwords are NOT case sensitive!
I would check your bank too!2 -
when TS does its job and team mates complaining that TS is too sensitive!
it does its job you douche, now you do yours!4 -
I don't consider myself a guru in JavaScript (hell I studied theoretical chemistry), but I do hate much of the rationalization behind building a Jenga stack of libraries, frameworks, dependencies... for building everything web related.
Many of the problems I see people solving with these giant stacks could be easily solved understanding how websites work (html, css, js and how interact with each other) with no dependencies giving smaller (for end users at least) and more maintainable code (in the sense it would not require updating dependencies that may be discontinued...)
I do imagine situations where these are ideal... Since there are not absolutes and developing is very context sensitive, but man if I have js article fatigue for ridiculous scenarios.2 -
I had to do a double take... Needless to say I can't sign in for shit, fucknows what mental finger dance I did on the shift key when signing up to these guys...
Also: forgotten password is "please type your email, if there's an account associated to this email address we'll fucking email it with password reset instructions"...
Fucking arsehole fucks, I just wanna pay my fucking energy bill.
-
Very eventful day, please see enclosed several smaller rants.
===================
My college's systems are shit and not only do they use HTTP for everything, even the stores and financial aid purchase system, they have homebrew JS shit for PGP site encryption (nifty...), but they exchange the PRIVATE KEYS instead of the public keys. Over HTTP. Not even HTTPS. Also if you log in more than 10 times in 24 hours it's supposed to lock you out of your account until you call... except it locks EVERYONE out. Found this out when on campus, trying to get my textbooks, when suddenly everyone had login lockouts because i'm a "paranoid bastard" and "afraid of idiot college students" for not telling a PUBLIC PC to remember the one password (enforced by password auto-sync across all their shit, not ideal, no) guarding my SUPER-SENSITIVE FINANCIAL AND ACADEMIC DATA... among the other hundreds of issues this college has. I now see why this college is the only one I can afford...
===================
Can't pass-through raw DVD drive access to VMs as VM managers crash when I try (yes, even QEMU...) so i've gotta install Windows on a shitty 80GB laptop HDD for literally one quick project. On the bright side, if my theory proves correct, you'll no longer need modchips for PS2s.
===================
Found a couple odd lines in my xscreensaver config:
GetViewPortIsFullOfLies:False
nice: 10
pointerHysteresis: 10
the first 2 I can't seem to figure out what do, and the last taught me a new word. Fun!
===================
that's it, it's over, why are you still here10 -
Never had a truly bad experience with a designer but once one mentioned offhand that the unique keys that we were using to secure access to sensitive information should be only 4 characters long because it looks better that way...
I kept them at 161 -
It seems like sensitive websites that need more priority to work fine are the ones that do not. I'm talking about government, school, bank, & service provider sites. Or it's just my retarded country.9
-
I love working on legacy products. You just need a good shower and possibly a therapist after.
- Sensitive data sent over the internet encrypted with DES (not even 3DES). Guess it doesn't matter that the key (singular, for the last decade) is basically 0123456789ABCDEF.
- Client databases with open default port, admin/admin superuser.
- Critical applications (potential for substantial property damage, maybe loss of life) with a single point of failure and without backup.
Suggestions, to slow down a bit with sales, so we have time to rewrite this steaming pile of crap are met with the excuse: be more pragmatist, this is standard industry practice.
Some of this shit can be fixed on my own time if my conscience nags too much, but others would require significant investment of time from multiple developers, which would slow down new business.
Guess the pay is ok, so that's something... -
Our biggest competitor has just been hacked. All their sensitive data, including passwords and client data, has been compromised.
It is not yet in the news, but someone forwarded their internal communication to us. :D
(fixed mistranslation)9 -
I was waiting for my wife in the shopping centre and noticed a shop sellung e-scooters. My my, what monsters can you buy with a few k€ :o I'm genuinely surprised!
The baddest monster: 3k: dual-notor, can carry >150kg of your fat ass. Takes ~12hours to charge, but, read this: with a single charge you can travel 150km! Max speed is 90km/h
i mean... I'm feeling quite confident riding a motorcycle at that speed, because I can bend down, because it weights a few hundred kilos and is not that sensitive to wind and road bumps.
But riding standing at that speed... Without any cover, with a vehicle weighting 50kg,.. Would you?12 -
Has any of the women in here dealt with "too politically correct" in the office that it's awkward? My boss refuses to just say guys even though I told him I feel singled out when he adds "gal". Or that I can't be better at social skills bc that tends to be stressed more if you're a female; nope i need to find a different reason now. Or telling me how I need to be involved in women's rights movements, those women are actually doing something to make a difference. I mean I'm glad that he's trying to fight for equality, and I know it can be so much worse, but I feel like I'm being corrected on how I should be as a female. Any suggestions? Or am I just being sensitive?9
-
Worst part of coding lang I love?
C# being case-sensitive.
Not a C# language thing, but I hate the vilification and anti-coding standard of not 'allowing' prefixes. Interfaces are allowed (ex. IUpdateCustomer), why not classes? Why can't I have a DTO and declare it a TCustomer and the zealots not scream "HE'S USING HUNGARIAN NOTATION!!! TAKE HIM TO THE STAKE!!"?19 -
Open office plans are a GREAT idea. Nothing says productivity like hearing a pin drop from across the building. Who needs good acoustics anyways? And you bet your ass the moment anything sensitive to background noise is going on you're no longer allowed to communicate at all, because even a potato plugged into an audio jack can hear you whisper from 50 feet away. Good thing we don't do that often - only on days that end in Y, I assume.2
-
Trying to implement a dynamic data masking solution for our databases, to filter out sensitive data.
This seems like a problem which should've been solved decades ago. But it isn't. All DDMs, proxies, seeders, maskers... they all suck balls.
Which makes me wonder, how many devs walk around with MacBooks with half a million credit card numbers on them... -
Sometimes when I drink water out of a glass bottle I knock the edge of it against my overly sensitive front teeth just to feel something once again.9
-
Been a mobile developer since April, liking the experience and the amount of projects that I've been a part of.
And one of the things that I've learned about this is that sometimes the client doesn't even know what he really wants. I mean for fucksakes, we implement everything, and new functionalities and there's always something that works on every other app (and is basically a standard) and he thinks is not suppose to be like that...
And another thing. Fuck Apple Store. At the company we've developed an app that practically shows information that only users should see (in our logic is sensitive information from our clients) and they DECLINED 4 FUCKING TIMES THE APP. Reason? Since the app's purpose "isn't correlated" with the basical information we show, the user can navigate through the app without going through login.
We basically added an "explore option" that shows basically nothing and they've accepted. FUCK APPLE FOR WAISTING OUR TIME AND THE CLIENTS TIME1 -
Dear programming languages,
If you had to be case sensitive, then why the fuck can't you settle on whether to use an S or an s for a
S/string declaration.4 -
Coolest bug is less of a bug and more of a feature. I've been working on a medical app and I used an open source backend which had almost everything I needed. To be hipaa compliant you have to encrypt all sensitive data - full db encryption was not something this backend was capable of.
So my solution was to encrypt the data on the client side and create a secondary server - that can only be accessed on my app server - to store and retrieve the keys.
If anyone's thinking of working on a HIPAA project - you're welcome -
document.getelementbyid("myid");
Runtime error !
must be "ById"
:/
also same problem with elem.innerHtml
(Correct: elem.innerHTML )2 -
Print("Hello World")
When people design a brand new Postgresql schema (case sensitive) using a mix of upper and lower case letters.
Only to then proceed and escape every single table and column name in every single query.1 -
sAleSfoRce aPEx is a hot wet garbage fire. How can I make this actually make this work right when I need to compare case sensitive strings?
 10
10 -
Pm orders me to integrate data from several closed systems into a new CRM, problem is... corporate security won't allow me to push data between these networks as there are extremely sensitive data on these systems. So I disobey PM or corporate if I do it and ive told both the issues. 4th round with this exact issue now.4
-
21:37
Manager: Hi
Manager: Do you know anything about this? <screenshot.jpg>
Me: Hi
Manager: Oh, I didn't mean to disturb you this late
Me: *what....? Then what DID you mean by writing to me at my bedtime....?*
(Though it's good he pinged me - it was a valid and time-sensitive concern. But saying "I didn't mean to" - that's just not true. Call a spade a spade and spit out what you need)10 -
Wouldn't call it a feature. More like worst practice. Data manager (and my boss at the time) kept using our website as a way to host large files 3rd party vendors/partners could download instead of using one of the many secure transfer methods out there to send them data. This was sometimes extremely sensitive data. No authentication or security that I could find. I went ballistic on him after seeing that.
-
Why do we rant here? Why can’t companies allow a safe space for their employees to vent out their woes? Or does that just add tension/make the workplace heated coz managers or co-workers could be sensitive to criticism? Or we’re just too stressed and overwhelmed that our woes don’t make sense(and we know it) but we gotta let it out some times? Lol14
-
In today's episode of "how i got almost to the point of insanity for hours and the sudden realization and relief"
When you have ssh error saying your private key is an invalid format in your CI, you probably just missed an EOL.
MCP says EOL.
Fucking EOL
That is the realization i made after half a day wasting on debugging this.4 -
Sometimes, I feel like tearing my hair out from the way Bash works.
Like... Where other languages have two operators for case-sensitive and insensitive regex matching, bash? It doesn't. It only matches case-sensitively.
And if one wants the insensitive matching? Gotta set a shell option... And if a script wouldn't change it back, who knows what else could break, so of course it has to save its initial state, change it, do its case-insensitive matching, and return it back to its original value.
10/10 experience.14 -
To all websites requiring at least one upper case, one lower case, one number, one special character, 25 emoji and 49 unicorns in the password when signing up.
If you say something is required, then your regex BETTER be checking ONLY for those things. You should not have hidden requirements for passwords that users are supposed to dream about and know. Especially if it's a super time-sensitive thing that they should have opened 2 Fridays ago.
I had to pull my hair out for 20 minutes (that felt like an hour) before looking at their code and reading their regex. The regex was different from what the page said the requirements actually were. What were they even thinking? 😑
The rest of everything related to this organization uses an SSO system, why can't they just use it? Isn't the whole point of SSO to avoid a different login for every tiny part of the system?
I wonder what the other less technically inclined people using the system are doing right now. Sadly, I have no way of letting them know.
I sincerely hope the dev that made that website faces the same thing while picking a password for creating an account somewhere else and realizes what he/she did.
I really needed to let it out.
I feel much better now.
Time to take out the stress ball :)1 -
Imagine an online, public service, that allows you to communicate with others (for example a simple chat, game, whatever ).
The users connect to each others via p2p. Based on this, you can easily get the ip address of any user directly connected to you. P2p is used to reduce server load, but information is still verified (for example using RACS), so let's assume the data is always safe.
(please remember, this is just a imagined Szenario)
Now the question: AFAIK, the IP address is a sensitive information. Would p2p in this scenario still be 'legal' in the EU given the latest changes in the laws?7 -
Dude that convinced me to come to company became the most toxic person ever after I got fed up of his lies and lame attempts to get me to do his job (so he could just get the merits). We don’t work on the same project but closely related. Every time we speak he tries to hurt me by trying to put me down/raising sensitive topics. But he gets rid of the history all the time, so I have nothing to handle to HR or manager. Time to jump the ship? Job is fine otherwise.6
-
This happens more often than I'd like to admit...
(repost since the other one contained sensitive information) 6
6 -
Why fucking windows explorer's search is fucking case-sensitive? I could not find any fucking option for it.
Edit : actually it's not but sometimes it couldnot find files2 -
Bought an Arduino and is finally able to learn how to make my software interact with custom hardware projects. Just wiring up a led and controlling it with software is amazing fun! Really looking forward to learning servos, motors etc.
Planning to make velocity sensitive midi drums with piezos in the future.4 -
Me: uses MS Edge with Strict tracking prevention
Every website: "Please disable AdBlock"
Why are you so fricken sensitive?
I need to get an anti-anti-adblock.2 -
I just got a project that is already developed by a team. It is already in the production and guess what!! They are storing customer’s credit card details in the database 🥸🥸12
-
Hey folks!
! Do not read further or open this rant if you are likely to be offended!
I always wanted to know but had no nice way to ask so I'm just gonna shoot.
Most of you must have worked/be working with foreign people: canadians, french, chinese, etc. How would you describe those people as colleagues [e.g. lazy, stubborn, chatty, etc.]? The goods and the bads would be perfect.
The topic is sensitive. Please be polite but sincere. This question nor its answers are not meant to offend anyone. We all have our cultural differences, we all have been taught different. I'm just wondering what could I or anyone else expect from each foreign teammate.15 -
Currently wondering why we use RGB when the "red" cones in the human eye are most sensitive to yellow light
 2
2 -
I can't come to terms with people's terrible reasonings.
You read a news about something. Let's assume it has to do with a sensitive topic, like race, gender, culture, religion, something polarizing, that makes you pick 1 of 2 sides.
So what do some people do? They ask themselves "ok what group do I adhere? How do I label myself?".
Then they ask "what do other people in said group/label think about the matter?", sometimes it's people in the media, friends,
sometimes people even create a mental construct of a stereotypical person of said group, a hypothetical one, and use the opinion of said construct as representative.
And final step is a knee jerk reaction of "I believe that too!!!!!!".
Obviously, all of this can't bring no one closer to the theorical truth or the least flawed conclusion.
What does? Case by case basis.
You judge every case as if every case was its own thing.
But why does some people have a hard time doing that? Just general ignorance maybe?
Maybe this tends to occur in families where parents don't teach their kids to challenge their beliefs, or teach them that doing so could result in lack of parental acceptance.
People also have peer pressure, the need to belong and feel accepted. That means sharing the same points of view with close people and considering the opposite taboo.
There's also the very ignorant people that have conspiracies for lunch.
In any case, I feel some people don't even fucking try to be neutral.3 -
I was pissed off beyond all reason yesterday when I realised that the reason my code didnt work for 2 days was because i spelled eForm with an uppercase F in my data model, and a lowercase f in my object classes. There was no way for the compiler to warn me so everything compiled fine but crashed at runtime when I tried to access that property. When I saw it, my head hit the desk....
-
Once I found out an unprotected folder in my school which is used to store sensitive data.
It was open to any administrator there.
We copied the Question Papers, Edited the attendance, and Even changed the Marks.
We were able to extract photos of students from the database and retrieve stored passwords -
Adding a couple functions to free software, rebranding, then selling to customers.
I know that there are other companies that do this, but still feels like stealing from the authors and ripping off customers at the same time.
Maybe I am too sensitive, but I'm deeply disturbed by this and I'm having a really hard time getting work done.4 -
Does anybody use Freelancer.com? I'm currently in an argument with their support chat minion about how private or not-private the project's contents are AFTER the project is awarded. She's telling me that both awarded and unawarded projects are completely exposed to the public Internet, sensitive file attachments, chats, everything, unless one upgrades to Private status. If one doesn't like that, she says, one can always delete one's project for only $5. Does anyone else have experience to share in this regard? I find this incredible.2
-
Reading "duh... that link looks sketchy" time after time when attempting to nudge people in the direction of good resources, e.g., on-line manual pages, becomes rather irritating. Is typing the URL into VirusTotal or something really such a fucking hassle? Are you sufficiently special to warrant the creation of an IP grabber which is dedicated to targeting you... AFTER you posted your exact location on Instagram last week?
Similarly, some pants-shitting, worm-eating troglodytes who have the gall to claim to know anything about cybersecurity STILL think that for all Web sites k, that k's URL begins with "https" implies that k is secure. NO! Unencrypted Web sites are FINE unless sensitive information is being transferred. Are publicly available manual pages sensitive information now?
Grabbing the campaign hat and writing death threats and very personal insults is sometimes slightly tempting.5 -
Talking about stupidity, my friend on whatsapp even share his bank online transaction on his stories, I told him to be careful with those sensitive information, but he's ignoring it.
I think he more care to show off his "bulge-wallet" than protect his own money.
Find anything stupid than that?9 -
Google researchers have exposed details of multiple security flaws in Safari web browser that allowed user's browsing behavior to be tracked.
According to a report : The flaws which were found in an anti-tracking feature known as Intelligent Tracking Prevention, were first disclosed by Google to Apple in August last year. In a published paper, researchers in Google's cloud team have identified five different types of attacks that could have resulted from the vulnerabilities, allowing third parties to obtain "sensitive private information about the user's browsing habits."
Apple rolled out Intelligent Tracking Prevention in 2017, with the specific aim of protecting Safari browser users from being tracked around the web by advertisers and other third-party cookies.2 -
Remember how I was - against all that was promised - assigned to a time-sensitive front-end (so definitely not my forté) project about a month ago? Remember how I struggled with the choices of how to go about it - switching from F# (Fable) to Rust (Yew) to eventually settling in with Vue and TS?
Yeah, I’m glad I went that way, even though there could’ve probably been better choices out there: my part is done now, even though it’s not quite prod ready yet (close tho), the team who’ll maintain it takes it over now, after I finish dealing with my current minor issue. And damn their front-end guy is GOOD. Makes me feel very inferior in that department. Well, I am. Back to back-end, thank you very much...
But I have an issue here, that bothers me. I’ve produced a codebase that’s obviously written on a tight schedule: no tests, no documentation, a few embarrassing hacks/workarounds and so forth. I actually feel bad for leaving it out of my hands to them in such a state...1 -
So my computer is doing ok after becoming spastic over viruses. I did hardware and software cleaning. First time I did removing hardware parts but it worked it way better than expected with the static sensitive parts (I used a anti static wrist band). Congrats to myself I guess :)3
-
Anybody else really annoyed at all these people getting mad at zuckerburg? Like, I've always questioned privacy of the internet in general. If you're dumb enough to put sensitive info on the internet (especially on social media) then you shouldn't have the right to complain about privacy. It's your responsibility to protect your information.3
-
Dev life pro tip:
If you lack years of experience or proven track record of a specific technology, just say you do but you can't talk about. You signed a NDA. Very sensitive. Icky stuff for the CIA. The less you know the lesser the chance you end up naked in rural idaho, tripping balls on LSD convinced you are a toad for the rest of your life compliment of the MKULTRA program24 -
So with all this new political correct bullshit pandering to the extra sensitive snowflakes, what do we call a “blackout” from now on?9
-
yahoo is now alleged to give away bulk mail content to intel agencies. such a dead investment, who uses yahoo for sensitive communications anyway?
http://thehackernews.com/2016/10/...1 -
Sticks and stones may break your bones but I sometimes have that feeling of breaking every bone of those who push changes with sensitive information to the repo. Stop it.1
-
Either I am too sensitive with my name or I just can't stop laughing when someone keep misspelled my English name, "Michael" into "Micheal".
I know it doesn't sound like a big deal but... *eye-roll*
Anyway, I am still wondering that what wording or how does it take for them to accidentally typed from 'ae' into 'ea'..?
Super curious here.3 -
Fun fact: if your tweet contains the word “Mastodon”, it will be automatically marked as sensitive content.
https://mas.to/@TimH/...12 -
I need someone as a partner on this idea that I have. Preferably someone with UI/UX front-end experience along with security measures for secure file transfer and storage (involves sensitive documents). Comment if interested.1
-
CREA DDF (Canada Real state listings API) is what you get when government fucks with technology.
Holy shit! So f*cking inefficient to use it, test it and get data.
I get the protection behind sensitive data but fuck me if there is not a lot of waiting behind their fucking application process just to fetch some testing data.1 -
Security issues I encountered:
- Passwords stored as plain text until last year.
- Sensitive data over http until last year.
- Webservice without user/pass authentication. -
Can someone example to me why do people use a VPN when not on public wifi? Like you are already at home with your own private network.
Like the moment you log into Facebook or Twitter or medium or to check your Gmail/outlook whatever, all you are doing is making is making it very clear to the host companies that you are inconsistently paranoid. Because all the sudden the person who's home address is in Seattle, work and home phone are in Seattle and all of their communication is done with people in Seattle. Has their web traffic location encrypted unknown.
Yeah your packets might be encrypted, but you are still spreading enough self identifying information by merely existing on the web.
At the end of day it seems more like a illusion of safety that these VPN sell. At the cost of a good dollar and slower internet speeds.
Unless you got some actual trade secrets and sensitive information, the f is the point for you to use one?17 -
Currently the only 3rd party tokenization VSCode supports is a massive pile of RegEx. There's a whole discussion about how procedural tokenization could be supported without running extension code in the UI thread. The central argument against delegating this to an external worker is that if the reply doesn't arrive fast enough it might interfere with characters typed later.
1. Any computer that can run VSCode can execute somewhere in the order of a _billion_ instructions per second. To a program, the delay between keystrokes is an eternity. The only way to run out of time here is if either the dev isn't aware that the request is time sensitive, or the framework communicates to the OS that the task isn't urgent and an arbitrary amount of work is scheduled before it.
2. Chromium is the pinnacle of cybersecurity and its primary job is to sandbox untrusted user code. You don't need another thread to do it.
3. This use case fits squarely in the original design objectives of Webassembly.2 -
does anyone have any experience with e-solutions recruitment company ? theyre asking for sensitive information about a position so it seems shady.3
-
The more years go by, the more people get sensitive and butthutt by everything around them. Can't swear in public nowadays because someone will get offended lmao.1
-
Gah, I just received this Ubuntu 18.04 VM with 8 cores and 8 gigs of ram, and since it'll be a production server both serving public and "private" networks (yes, shout at me, but projects won't be about hosting sensitive information, I wouldn't put all that on one server), and I'm struggling between my options.
Docker, or not docker?
The server's main use is to host our growing blog and install Varnish, which will hog some ram after a while. I use Laradock for my dev projets, it's really easy to develop with it, but I am unsure if it fits a production environment with performance, security and traffic load in mind :(
I read Docker has stability issues (in 2016-2017), and can bring the machine down with it, I don't know if I should just install the software (nginx, apache, percona/mysql/maria) without "containerizing" it and go for it
I'm lost xD7 -
I sometimes forget all the other “console.log()”s and I log API responses and other sensitive junk, :/
-
HELP!!
I am starting a new contract to create a full stack web application with a medical company that will contain some sensitive data about their clients/patients.
I have been working as a salaried full-time employee for a medical software company, but I have been shielded from any sort of lawsuits from the client (worst case scenario, I'd get fired).
Do any of you have any advice on what I should do to protect myself in terms of LLC's, Insurances, etc?2 -
HFS, MacBooks standard file system is the answer to that every question asking "what if you don't design well/ how bad can it get."
How can a bloody file system not be case sensitive.
I know you want to be different from *nix
But there would have been better ways1 -
Part I think 3 of Mathematica fails.
So, I'm doing a plot. Initially, I hit the following error: "Value of option PlotRange -> {{3,19},{0,1.1}} is not All, Full, Automatic, a positive machine number, or an appropriate list of range specifications."
Me:Okay, let's change it to PlotRange -> Automatic, maybe I don't know what I'm doing.
Mathematica:"Value of option PlotRange -> Automatic is not All, Full, Automatic, a positive machine number, or an appropriate list of range specifications."
Me:Uh, what? Well then... Oh, please don't tell me it's because of a space in between.
Mathematica:"Value of option PlotRange -> Automatic is not All, Full, Automatic, a positive machine number, or an appropriate list of range specifications."
Me:Oooookay then, what's the problem?... oh wait, there's another space. Why is it that sensitive to whitespace though?
--------------------------------------------------------------------------
That fixed it. Then, when I tried to reproduce it, suddenly adding a space and reevaluating did not raise the error.6 -
Alright so I'm in need of a little advice.
So I recently decided to go back and practice basic problem solving and from what I can tell now it's just me not used to JS like I am with python but I want to move on to bigger projects and other basic concepts (like manipulation of the DOM) and move away from basic problems.
But my concern is that I'll look at that list and only pick the ones that I feel I understand I can solve instead of the ones I cant. And theres a large list of them and I see that people are doing a lot of them while I'm just doing a few per page. And I'm afraid I'm just not good enough or stupid if I just ignore the basics and move on because the basics are there for you to figure out the easy stuff.
But I really just want to move on and I dont know when I need to. And last time I asked for advice I mentioned I have been programming for a few years, left out the normal accomplishments I've posted on here but I was just told since it's taking me this long I should just quit I tried to rebuttle but they kept telling me no that literally broke me and my confidence so now I'm sensitive to asking questions also fuck whoever that was.4 -
my oh my, its my bad, .. dont worry its my bad. you dont have to look at me like that. im sorry cos im asking you about wtf was wrong with code and asking you to fix it.. #case sensitive.
-
Holy shit. Do NOT open a Wells Fargo banking account. On top of their ridiculous password limitations, your password is NOT CASE SENSITIVE. I tested. Caps lock, no caps, a mix, it doesn't matter.
More info on the password limitations at my other rant https://devrant.io/rants/905148/...3 -
Working with external teams on this new project involving pretty sensitive stuff like bank transactions.
Talking about user flow and how to handle authentication, like 2-factor and stuff.
Newish guy on external team (though experienced) says they have a proposal.
Security Questions.
... like "What was you first car" security questions...
awkward silence in room...8 -
devRant ain't the same anymore. Too many sensitive snowflakes around. You bully them once or twice, they end up leaving the platform.
I'm running out of victims here29 -
I am the keeper and protector of a specific joke I made up while at rock bottom, that is so dark (vantablack levels of darkness), cruel, insensitive and inappropriate in any context to any person, that I'll probably never tell it to anyone.
It's clean. It's not about sexism, racism, religion, war, discrimination, rape and other sensitive topics often joked about. It's also not gross --- it won't make you vomit. It's not personal and doesn't doxx anybody.
I don't even know if I can tell it at any dark jokes contest without being kicked out immediately.
I'll give you just one hint: it's about being in the wrong place at the wrong time. There is no plot twist like "this place is your mom's vagina" --- nothing like that. It's just about being in the wrong place at the wrong time.8 -
My new boss has such a sensitive ego. The latest is he asked me not to make big changes to 'his' code so whilst attempting to fix a bug in 'his' code I realised a big change was needed. I tell him at standup that he might want to take a look first and he agrees. A few days later he emails me to ask why I haven't finished work on the bug. When I reply he ccs other members of management to ensure he is deflecting any blame from himself (I dont even play the blame game to begin with).
The next day I email him that some tests are broken (he broke them but I just emailed him to bring his attention to it since he doesn't want me touching his code. And because it means he isn't testing properly - not that I would say that).
His reply - "are you going to fix them?"
Me - "ok"
The next morning be brings me into a meeting to ensure I agreed he wasn't to blame and that it was my fault and that he didn't understand my email response as it just said "ok".
I really can't stand such petty bs...2 -
When someone calls me VincentNwonah and expects me to answer. but I'm a programmer and VincentNwonah is a different object from NwonahVincent. ;p
-
What kind of tasks would you guys trust an intern with? Asking because I see a lot of people giving admin login for everything, access to production and sensitive info5
-
Security experts have discovered hundreds of fake websites which are being used to spread dangerous malware for Android and Windows devices. A "vast" network of over 200 internet pages, which impersonate 27 brands such as household names like TikTok, PayPal and Snapchat, are being used to spread a vicious bug which can empty out bank accounts. These bogus websites feature the notorious ERMAC banking trojan which is capable of stealing sensitive login details for 467 online banking and cryptocurrency apps.6
-
Guys, long story short we found an investor for our app idea. What's the best route to go for us to get the people we need. Essentially we need a mobile app, but it may also need to be a kiosk, so should we look specifically for React Native developers to make a cross platform app or should we focus on ios, android, and kiosk apps natively? It involves access of sensitive information.
-
Anyone familiar with js bxSlider? Anyone have time and willing to slack chat or email with me to provide some assistance? Yes I looked and am trying to get some help on stackedoverflow as well but this is time sensitive for work :(7
-
I recently came across this article with some basic security advices, like use 2fa security key, encrypt your USB keys, don't use untrusted USB chargers / cables / ports (or use a data blocker cable if you need to charge your device). It made me think, how relevant are the USB-related threats and risks today? Do people really still use and carry so many wired USB devices, and just drop or plug them wherever?
The last time I used an USB device to transfer some important data was probably over 10 years ago, and for the love of god I don't know anyone who still carries an USB key with sensitive data with them on a daily basis, much less actively uses it. Besides, whoever still does that probably puts their USB key on the same keychain as their ID / access tag and a bunch of other keys (including a 2fa device if they use one) - they're not going to lose just some sensitive data, they're going to lose authentication and physical access devices as well, and that could turn a small data leak into a full-scale incident, with or without an encrypted USB device.
I'm also not sure about untrusted USB cables and ports, from what I've seen the USB outlets and cables are pretty much non-existent in public places, most places offer wireless charging pads instead (usually built into a hand rest or table surface).3 -
Cyberpunk Programmers is a specialized firm focused on recovering lost cryptocurrency assets. Their expert team employs advanced blockchain forensics and tracing techniques to retrieve funds lost to scams, hacks, or fraud. With a client-first mindset, they prioritize clear, jargon-free communication, ensuring clients understand the recovery process.
The company distinguishes itself through transparency and security, implementing strict measures to protect sensitive data. Their results-oriented fee model charges only upon successful recovery, aligning their goals with clients’ interests and reducing upfront risks. This reflects their confidence in tackling complex crypto recovery cases.
Cyberpunk Programmers handles various asset loss scenarios, from phishing attacks to compromised wallets, catering to both novice and seasoned crypto users. Their efficient approach aims for swift resolutions without compromising thoroughness, making their services accessible and reliable.
Known for ethical practices, Cyberpunk Programmers has earned a strong reputation in the asset recovery industry. Their dedication to client satisfaction and expertise in navigating digital fraud make them a trusted choice for those seeking to reclaim lost crypto assets. For anyone facing cryptocurrency loss, Cyberpunk Programmers offers a professional, secure, and effective solution. for more info about Cyberpunk Programmers inquire at cyberpunkprogrammersdotcom6 -
So I took this ocd sensitivity test 😂😂 . Apparently, I'm a perfectionist & need to take it easy lol.
Here's the link to play :
http://playbuzz.com/monicawoods10/... 8
8 -
Maybe not specifically "dev" but certainly a relatable rant to anyone here:
Moms small business gets "hacked," or standard spyware phone call from India let us save you for only $149 kind of crap. She obviously gets upset had a panic attack and thinks about all the sensitive shit on their network. Then, ONLY THEN, does she call me and the rest of the cavalry i.e. over payed and undermotivated IT guy to ask what's up why it happened and whose fault is it.
All is well, no ransom paid, no data lost or tangible damage done, but I am positive it will happen again, because it is impossible for people to internalize that they're the problem that money can't fix.
You clicked the unsolicited link. No amount of antivirus bloatware will ever be able to stop the monkey from trying to see what's in the box.
TheBut keep not paying me or people more qualified than me, and then scream and yell and pout when your shits gone and we can honestly say with a grin and a clean conscience that there is nothing we can do. -
Update 2: https://devrant.com/rants/5446637/...
Not saying that my boss is wrong, but the way he gives feedback and teach me is just awful. Just today, a new colleague told me that one of the ex-team member quit because of our boss.
Anyway, the activity I was working on, I nailed it.
In morning connect, boss specifically told what he was looking for and made me do a live task and gave feedback. That made me realised what he was looking for.
I spent the day completing the activity. When I showed him, his jaw dropped.
He tried to pick on few things, but failed to do so.
He loved the output. Praised me and my persistence. Finally, the history repeated itself, and I learnt more about communication.
Possibly my weakest point out of all, where I was failing in interviews and had to fix that. Now, I got some pointers and will work on it to excel futher.
Yes, things were stressful, but I came out to be stronger.3 -
Damn i used to be sensitive to you people's criticisms now 100 years it feels later I'm more worried that people seem to expect me to shoot people or deal with undeserved hell and the theft of every memory of every thing I ever worked on and better understanding of what scum they are while they try to trigger me into ending their pathetic useless miserable lives in a way less horrifying than they deserve heh2
-
What is the point of kubernetes "secrets" if it encodes the sensitive information as a base64 string if anyone can decode and read raw data using any base64 decoder tool?5
-
So...im having a lot of issues with people messing with my emotions because of how sensitive I am.
I lost a lot of confidence in myself a while back and grew sensitive. I don't know what to do and I don't understand why people have to be so mean :(
A girl today was laughing at me cause I couldn't figure out something in class and I feel useless.
Two guys have already messed with my emotions and led me on.
A lot of people don't hang out with me like before and no one wants to hang out with me. Another girl said I was clingy and annoying and I don't understand what I'm doing wrong. I just want to be loved :((13 -
Does anyone from here working by GMX? I am specially looking for a sysadmin.
The story is the following. We can't send emails to GMX addresses in general. I've contacted my provider, and they said, that they've contacted GMX several times but no solution has been made so far. This was almost a month ago and the problem still persists.
If anyone from here willing to help me clear this mess, or just give some explanation, I would be grateful. We are loosing reputation as a company having to answer from a different email address.
If it is a sensitive info please give me a channel where we can speak about the details.
Please note I am not a sysadmin by the hosting company, i am simply a customer of theirs.14 -
Day 29 of starving myself to death challenge. Crying a lot. I suppose my mind does its best to get rid of that mountain of trauma I have, to make the dying process more comfortable. I don't think will succeed though
it also does this weird thing that it momentarily goes full force on empathizing and feeling sorry for inanimate objects, painting the picture of said objects being slaves to humans because they don't possess enough intelligence to rebel and break free
sometimes it's not even objects but WORDS: “cans”, “bottles”, “mugs”, “bowls”, “spoons”
in five seconds, it's gone, but the pain persists, stretching into soft blur. The more you touch it, the bigger it becomes. like Jim or Jeff of kitchen nightmares said while cleaning and realizing that the fat residue only gets bigger, “I'm making a mess”
every key press of typing this feels as if the key was an overly sensitive tooth with no enamel left, and my fingers were covered in acid10 -
I was once 'fraped' by a former (non technical) manager. I decided to retaliate by returning the favour while he was out of the office, but instead of the basic toilet humour I had been subjected to, I took it one step further and posted a status on his behalf, a sensitive cry for help, full of sadness, regret, alluding to betrayal and broken friendships. The texts, calls, concerned replies and messages on Facebook started flashing up his phone. He called me demanding I delete the status now as he couldn't figure out how to do so from his phone. Needless to say he was not happy. Highly recommended.1
-
Vivaldi browser is shit.
Simple isntructions on how to make most shitty browser ever:
1. Force users to use "really-fucking-long" password that will not match to any of their existing ones.
2. Invent some useless stupid "encryption password" (why does any normal browser work fine without that shit) and most ridiculous - automatically set it to be the same as the main password.
3. Of course you forget the pass you set because you dont remember what symbol you added 5 times in the end of your normal pass to fit their stupid rules.
4. You have to reset it
5. "Encryption password" does not reset with it, so you still dont remember it
6. Sync is not working!
7. If you think this is shitty enought, you are not right - they went futher. To reset that fucking "encryption password" you have to... ERASE ALL YOUR CLOUD DATA.
Fucking retarded piece of shit - never, never trust those morons who made this shit browser to sync any of your sensitive information.17 -
The ethical implications of utilizing tech cyber force recovery for monitoring digital behavior are complex and multifaceted. At its core, this technology allows for the covert tracking and analysis of an individual's online activities, potentially exposing sensitive information and private habits without their knowledge or consent. This raises serious concerns around privacy rights, as the ability to peer into a partner's digital footprint without their awareness could be seen as a violation of personal autonomy and the reasonable expectation of digital privacy. There are also questions of how this data could be leveraged, as the detailed insights provided by tech cyber force recovery could enable the manipulation or exploitation of users, whether for commercial gain, social control, or nefarious purposes. Additionally, the potential for abuse of this technology by bad actors, whether hackers, oppressive regimes, or other malicious entities, introduces significant risks that must be carefully weighed against any perceived benefits. Proponents may argue that tech cyber force recovery aids in investigations, cybersecurity, or parental monitoring, but the ethical bar is high when it comes to the covert surveillance of digital activities. Ultimately, the use of this technology requires a thoughtful, nuanced approach that prioritizes individual rights, data privacy, and the responsible, transparent application of such powerful monitoring capabilities. If you ever have doubt that our partner is cheating on you, do not hesitate to let tech cyber force recovery assist you via:
telegram. techcyberforc
whatsApp. +.1.5.6.1.7.2.6.3.6.9.7
Thanks. -
Navigating the suspicion of infidelity is a difficult experience, and I felt lost in that situation. Seeking answers, I contacted Crypt0 Pandemic Hunter, and I'm thankful I did. Their unique method, focusing on digital footprints in social media and phone calls, helped uncover the truth.
Initially, I was skeptical but impressed by their professional approach. They analyzed my spouse's social media, browsing history, and even worked to recover deleted messages, revealing unknown communication patterns. They also conducted discreet surveillance remotely, gathering photographic and video evidence that supported their findings.
They were honest about their methods and kept everything legal. Although the evidence was hard to face, it provided the clarity I needed. Despite the challenging outcome, I appreciate their professionalism and recommend them for sensitive situations.2 -
The UPS Store: Secure Document Shredding Services in Carlsbad
In an age where data security is paramount, safely disposing of sensitive documents is critical for both businesses and individuals. At The UPS Store, located at 7040 Avenida Encinas #104, Carlsbad, CA 92011, we offer professional document shredding services to help protect your confidential information from unauthorized access. With our convenient and secure shredding options, you can ensure that your private data stays protected.
Why Opt for Document Shredding at The UPS Store?
Secure and Confidential Disposal
When it comes to document disposal, security is our top priority. Our shredding services use strict protocols to ensure your information remains confidential. From financial documents to personal files, we provide secure shredding solutions for every type of sensitive information.
Convenient Shredding Services for All Document Types
Whether you’re cleaning out your home office or managing sensitive client information, The UPS Store handles all types of documents, including bank statements, contracts, tax forms, and more. With our shredding services, you can conveniently and securely dispose of everything from single documents to bulk files.
Environmentally Friendly Disposal
At The UPS Store, we believe in responsible disposal. All shredded materials are recycled, so you can feel confident that your document shredding is not only secure but also environmentally conscious. By shredding with us, you’re helping reduce waste and support eco-friendly practices.
Affordable and Transparent Pricing
We believe that security should be accessible, which is why we offer transparent and affordable pricing for our shredding services. Whether you’re shredding a few pages or several boxes of documents, we provide competitive rates to meet both personal and business needs.
Convenient Location in Carlsbad
Located in Carlsbad, The UPS Store makes it easy to handle all your shredding needs without any extra hassle. With flexible hours and a convenient location, stopping by to securely dispose of your documents is simple and efficient.
How Our Document Shredding Service Works
When you visit us for shredding, simply bring in your documents, and our trained staff will handle the rest. Our team follows a secure process that ensures all documents are destroyed effectively, protecting your sensitive information from the moment you drop it off until it is securely shredded.
Contact Us for Secure Document Shredding Today
For secure, reliable document shredding in Carlsbad, visit The UPS Store at 7040 Avenida Encinas #104, Carlsbad, CA 92011. For any questions or to discuss your shredding needs, feel free to call us at +1 760-431-0028. Our friendly team is here to help make document disposal simple, safe, and affordable.
Trust The UPS Store for Your Document Shredding Needs
When it comes to disposing of confidential information, don’t take chances. Rely on The UPS Store in Carlsbad for secure and responsible document shredding. Visit us today to experience the ease and peace of mind that comes with our professional shredding services.
-
RECOVER YOUR SCAMMED FUNDS AND CRYPTOCURRENCY HIRE iFORCE HACKER RECOVERY
iFORCE HACKER RECOVERY consists of professional hackers who specialize in securing compromised devices, accounts, and websites, as well as recovering stolen bitcoin and funds lost to scams. They operate efficiently and securely, ensuring a swift resolution without alerting external parties. From the very beginning, they have successfully delivered on their promises while maintaining complete discretion. Few organizations take the extra step to investigate network security risks, provide critical information, or handle sensitive matters with such professionalism. The iFORCE HACKER RECOVERY team helped me retrieve $364,000 that had been stolen from my corporate bitcoin wallet. I am incredibly grateful for their assistance and for providing me with additional insights into the unidentified individuals behind the theft.
Email; contact@iforcehackersrecovery. com
whatsapp; +1 240. 803. 3. 7061 -
EY and ConsenSys announced the formation of the Baseline Protocol with Microsoft which is an open source initiative that combines cryptography, messaging and blockchain to deliver secure and private business processes at low cost via the public Ethereum Mainnet. The protocol will enable confidential and complex collaboration between enterprises without leaving any sensitive data on-chain. The work will be governed by the Ethereum-Oasis Project.
Past approaches to blockchain technology have had difficulty meeting the highest standards of privacy, security and performance required by corporate IT departments. Overcoming these issues is the goal of the Baseline Protocol.
John Wolpert, ConsenSys’ Group Executive for Enterprise Mainnet added, “A lot of people think of blockchains as the place to record transactions. But what if we thought of the Mainnet as middleware? This approach takes advantage of what the Mainnet is good at while avoiding what it’s not good at.”
Source : ConsenSys -
SPARTAN TECH GROUP RETRIEVAL A LEGIT COMPANY FOR RECOVERY OF STOLEN ETHEREUM / BITCOIN
At Spartan Tech Group Retrieval, we prioritize security, confidentiality, and customer satisfaction. Our rigorous protocols ensure the safekeeping of sensitive information, and our transparent communication keeps you informed throughout the recovery process.We’re dedicated to helping individuals and organizations recover stolen cryptocurrencies and digital assets. Our team of expert cyber security specialists, cryptocurrency recovery specialists, and digital forensic analysts work tirelessly to track, recover, and secure your stolen assets.
Email: spartan tech (@) cyber services . c o m OR
support(@) spartan tech group retrieval. o r g
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 22 -
I'm grateful for assistance in recovering $37,000 that I lost to crooks in Bitcoin—that's really challenging. Although I'm happy to hear that Supreme Peregrine Recovery was helpful, please use cautious. Sincere fund recovery is uncommon and frequently taken advantage of by con artists masquerading as "assistants." Verify the company's legitimacy, avoid paying in whole, and get confirmation of the recovery from law enforcement or a cryptocurrency specialist. Fake recovery services retarget a lot of victims. Always do extensive research on companies, keep sensitive information and private keys to yourself, and transfer any remaining funds to a safe wallet. I may assist in verifying the recovery service's credibility or provide advice on what to do next if you'd like.
+1,3,1,8,5,5,3,0,6,7,9
Mail: supremeperegrinerecovery(@)proton(.)me
supremeperegrinerecovery567(@)zohomail(.)com
info(@)supremeperegrinerecovery(.)com 7
7 -
A news/article/blog site and forum revolving around social issues where in addition to reading articles people can ask questions that are sensitive judgment free and get answers.
The aim is to slowly make the world a better more tolerant place8 -
Microsoft Teams login says password is incorrect then and for a captcha
I type it again but fails...
I'm like wtf... Could it be the captcha...
Which I entered in all lowercase
It doesn't say the captcha is case sensitive though..
Next few times it gives me captchas with k... Teehee me like 5 tries to login
Are we trying to verify passwords/humanness or whether I can somehow tell the difference between K and k?1 -
Best in Recovery Stolen Bitcoin: Vacuum Cyber Hack can Help you out
When I realised my $395,000 worth of Bitcoin had been stolen, I was devastated. The thought of losing such a significant amount left me feeling completely powerless. After exhausting all options, I decided to reach out to Vacuum Cyber Hack. Their reputation for successfully recovering stolen cryptocurrency made them the obvious choice. From the very beginning, I was impressed by their professionalism and expertise. They quickly assessed my situation and immediately began working on a recovery plan. Using advanced algorithms and state-of-the-art forensic methods, Vacuum Cyber Hack tracked the stolen funds with remarkable precision. Throughout the process, they kept me updated, providing clear communication and ensuring my sensitive information remained confidential. Within a short time, Vacuum Cyber Hack successfully recovered my stolen Bitcoin, returning my funds and restoring my confidence in cryptocurrency security. Their efficiency, dedication, and ethical approach made all the difference. I’m incredibly grateful to Vacuum Cyber Hack for their exceptional service and for proving that even in the most challenging situations, recovery is possible. They truly set the standard for Bitcoin recovery services. I can confidently recommend them as the best choice for anyone facing the same challenge.
Email: support @ vacuumcyberhack . com
Whatsapp: +39 351 059 0507
Website: https : //vacuumcyber hack .co m/2 -
Best in Recovery Stolen Bitcoin: Vacuum Cyber Hack can Help you out
When I realised my $395,000 worth of Bitcoin had been stolen, I was devastated. The thought of losing such a significant amount left me feeling completely powerless. After exhausting all options, I decided to reach out to Vacuum Cyber Hack. Their reputation for successfully recovering stolen cryptocurrency made them the obvious choice. From the very beginning, I was impressed by their professionalism and expertise. They quickly assessed my situation and immediately began working on a recovery plan. Using advanced algorithms and state-of-the-art forensic methods, Vacuum Cyber Hack tracked the stolen funds with remarkable precision. Throughout the process, they kept me updated, providing clear communication and ensuring my sensitive information remained confidential. Within a short time, Vacuum Cyber Hack successfully recovered my stolen Bitcoin, returning my funds and restoring my confidence in cryptocurrency security. Their efficiency, dedication, and ethical approach made all the difference. I’m incredibly grateful to Vacuum Cyber Hack for their exceptional service and for proving that even in the most challenging situations, recovery is possible. They truly set the standard for Bitcoin recovery services. I can confidently recommend them as the best choice for anyone facing the same challenge.
Email: support @ vacuumcyberhack . com
Whatsapp: +39 351 059 0507
Website: https : //vacuumcyber hack .co m/ 1
1 -
How to Hire a Hacker to Recover Stolen Bitcoin ; Top Crypto Recovery Expert in USA
Captain WebGenesis Crypto Recovery Center is a leading cryptocurrency recovery service that specializes in retrieving lost digital assets. .Like many others, I was drawn to the potential of Bitcoin and cryptocurrency investments. I stumbled upon a seemingly legitimate trading platform that promised high returns. After a few days of initial gains, I was unable to withdraw my profits, and my account was suddenly locked. I felt a sinking feeling as I realized I had been swindled. In my search for a solution, I came across numerous testimonials about Captain WebGenesis Crypto Recovery Center —a specialized recovery firm dedicated to helping victims of cryptocurrency scams. Skeptical yet hopeful, I decided to reach out to them. From the moment I reached out to Captain WebGenesis Crypto Recovery Center, I was guided through each step of the recovery process. They provided clear explanations of what to expect and ensured I was kept in the loop throughout. This level of transparency is crucial, especially when dealing with sensitive financial matters.
Website: Captainwebgenesis. com
Email: (Captainwebgenesis@ hackermail. com)
What is the best crypto asset recovery service provider?
How can I track, trace, and recover my cryptocurrencies from a scammer?
Where can I get a reputable fund recovery firm to help me recover my lost bitcoin?1 -
Hello netizens, I'm writing to detail a serious incident involving the illicit transfer of my ETH cryptocurrency from my wallet. This unauthorized transaction, executed without my consent or awareness, strongly suggested a sophisticated hacking or phishing attack on me. The immediate transfer of funds to an unidentified digital address necessitated swift action. I immediately engaged RUDER CYBER TECH SLEUTHS, a premier cybersecurity firm, to investigate and reclaim my stolen Ethereum. RUDER CYBER TECH SLEUTHS's thorough examination pinpointed the exact time and origin IP address of the unauthorized transfer. Remarkably, within hours of their involvement, my Ethereum was restored to my digital wallet. Beyond the successful recovery, RUDER CYBER TECH SLEUTHS significantly bolstered my online security and my household. This included implementing robust multi-factor authentication across all my accounts, deploying cutting-edge anti-malware software, and providing comprehensive cybersecurity training. They also offered invaluable guidance on recognizing and preventing future phishing scams, stressing the vital importance of verifying website and email authenticity before interacting with links or sensitive data. Their dedication to safeguarding my digital assets went beyond simply retrieving my funds, they ensured lasting protection against future compromises. I wholeheartedly endorse their professionalism and exceptional problem-solving skills in addressing this critical matter. Their expertise and unwavering commitment are truly exceptional. Their mastery of complex legal and technical issues makes them highly deserving of recommendation.
TELEGRAM: @rudercybersleuth1 -
CRYPTO RECOVERY SOLUTION CONSULT SPARTAN TECH GROUP RETRIEVAL
At Spartan Tech Group Retrieval, we prioritize security, confidentiality, and customer satisfaction. Our rigorous protocols ensure the safekeeping of sensitive information, and our transparent communication keeps you informed throughout the recovery process.We’re dedicated to helping individuals and organizations recover stolen cryptocurrencies and digital assets. Our team of expert cyber security specialists, cryptocurrency recovery specialists, and digital forensic analysts work tirelessly to track, recover, and secure your stolen assets.
Email: spartan tech (@) cyber services . c o m OR
support(@) spartan tech group retrieval. o r g
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 22 -
How Hackers Gained Access to My Crypto Wallet and Sensitive Data through a Keylogger sent to my device through a phishing email.
I’ll advise others to be wary of the kind of emails they open, as this happened a few weeks ago when a phishing email was sent to my email unknowingly to me that it was a keylogger with the intent of stealing my private information and if not for the intervention of Morphohack Cyber Services, I would have been cleaned out completely. I contacted Morphohack Cyber Services a week after that incident and they detected the keylogger in my computer which has been there for months stealing my private information. If my crypto wallet was not drained, I would not have been aware of the keylogger in my device. Morphohack was able to secure my devices and retrieve my crypto wallet including the crypto assets. Their sophisticated security features and malware can beat any hacking tools available and they are very professional and ethical. Morphohack is a lifesaver and I hugely recommend their services. Their E-mail. Morphohack@Cyberservices. com & WhatsApp. +1 - 213 - 672 - 40921 -
HIRE A CRYPTOCURRENCY RECOVERY SERVICE | iBOLT CYBER HACKER
When it comes to cryptocurrency recovery services, trust is paramount. With the increasing number of cryptocurrency scams and hacks, it’s essential to find reliable and effective services that can help recover lost funds. iBOLT CYBER HACKER has emerged as one of the more prominent options in this space, offering recovery solutions for users who have fallen victim to various online thefts. iBOLT CYBER HACKER is known for having a team with expertise in blockchain technology and cybersecurity. They leverage advanced techniques to trace and recover funds, including forensic tools and digital tracking methods.The company ensures that all customer information remains confidential, which is crucial given the sensitive nature of financial recovery and data privacy.
iBOLT CYBER HACKER has received thons of positive reviews of successful recovery.
Mail..... Support @ibolt cybarhack. com
Contact..... +39, 351..105, 3619
Homepage..... www . ibolt cybarhack. com 8
8 -
The Bravo CX 7000 ID Card Printer is a highly versatile printing solution for organizations seeking to create professional-quality ID cards with advanced security features. The Bravo ID card printers feature a modular, cube design that allows for easy configuration and scalability and can be used to print single and dual-sided cards with high-resolution images and text.
One of the key features of the Bravo CX 7000 ID Card Printer is its re-transfer printing technology, which ensures that images are printed onto the card surface with exceptional accuracy and durability. This technology also enables the printer to print onto various card types, including PVC, ABS, and PET materials. The Bravo ID Card Printer also includes advanced security features such as UV printing, which allows for the inclusion of invisible security elements such as watermarks or micro text, and magnetic stripe encoding, which can be used to store sensitive information on the card.
The Bravo ID Card Printers are an excellent choice for organizations that require a versatile and secure ID card printing solution. Its modular design, re-transfer printing technology, and advanced security features make it an ideal choice for a wide range of applications, including government, healthcare, and corporate settings. -
POSSIBLE WAYS TO RECOVER BACK YOUR SCAMMED CRYPTO FROM ANY INVESTMENT PLATFORM...
At TaxEase Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Digital Gold Hunter. Digital Gold Hunters team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform.Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Digital Gold Hunter has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Digital Gold Hunter helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information.Thanks to the quick and efficient actions of Digital Gold Hunter, and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Digital Gold Hunter ’s continued support, we will fully resolve the situation.
Their Contact info,
Email: Digitalgoldhunter@tech-center . c o m1 -
At TaxEase Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Digital Gold Hunter. Digital Gold Hunters team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform.Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Digital Gold Hunter has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Digital Gold Hunter helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information.Thanks to the quick and efficient actions of Digital Gold Hunter, and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Digital Gold Hunter ’s continued support, we will fully resolve the situation.
Their Contact info,
Email: Digitalgoldhunter@tech-center. c o m
whats App: +1 908 991 71321 -
POSSIBLE WAYS TO GET BACK EVERY PENNY LOSE TO SCAMMERS
At Digital Gold Hunters Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Digital Gold Hunter. Digital Gold Hunters team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform.Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Digital Gold Hunter has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Digital Gold Hunter helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information.Thanks to the quick and efficient actions of Digital Gold Hunter, and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Digital Gold Hunter ’s continued support, we will fully resolve the situation.
Their Contact info,
Email: Digitalgoldhunter@tech-center. com
whats App: +1 908 991 71321 -
App idea: Platform for ongoing entrepreneurs
I just come from a start-up weekend. I really enjoyed the support we got from 17 different mentors (most of them founded in the past on their own).
Back home start-up funders don't have the access to that mentoring. My idea is to create a platform specialized for founders, where you can share your idea, believes and ask question all around your business.
I think especially in the early founding stages entrepreneurs are full of questions. Helping and discussing with other selfminded people is probably very enjoyable for us founder folks. A difference to the f.e. reddit concept: Users can create "diaries", a place where all storys, questions and posts about your project are stored. Reading a diary from beginning to end shall be a fun experience, reviewing your or others history of their "babys" and following the entrepreneurs thoughts through all stages of founding. Users of course can create multiple diaries.
Functionality will be suited for the listed usecase, for example a "Post as Anonymous" function will be added, if you have to deal with company sensitive data and more stuff like that.
What do you think about the idea? Do you like it? Would you use it? If not, tell me why?
Cheers -
APM BILLING: Providing HIPAA-Compliant Billing Services You Can Trust
In today’s healthcare landscape, maintaining patient privacy and data security is paramount. Healthcare providers must adhere to strict standards to protect sensitive information while ensuring that financial operations are smooth and efficient. APM BILLING, based in Philadelphia, Pennsylvania, is dedicated to providing HIPAA-compliant billing services that ensure the highest level of security and compliance, while also optimizing the billing process for healthcare providers.
What Are HIPAA-Compliant Billing Services?
HIPAA (Health Insurance Portability and Accountability Act) establishes strict rules to ensure that healthcare providers maintain patient privacy and the confidentiality of their health information. As part of our commitment to protecting patient data, APM BILLING offers HIPAA-compliant billing services that meet all of the requirements set forth by this regulation.
Our HIPAA-compliant billing services ensure that all personal health information (PHI) handled during the billing and claims process remains secure. From data encryption to secure transmission, we follow the highest security standards to prevent unauthorized access, breaches, and other vulnerabilities.
Why Is HIPAA Compliance Critical for Healthcare Billing?
For any healthcare business, staying HIPAA-compliant is not just a regulatory necessity—it's essential to maintaining trust with patients and avoiding costly penalties. Non-compliance can result in hefty fines, lawsuits, and damage to your reputation. When it comes to billing, ensuring that all processes follow HIPAA guidelines is critical in preventing unauthorized access to sensitive patient data.
APM BILLING takes privacy and security seriously. Our team is well-versed in all HIPAA regulations, so you can trust that your patient data is always protected. We integrate comprehensive security protocols into our billing workflows, including:
Encrypted communications for all patient data exchanges
Secure data storage that meets HIPAA standards
Audit trails to track access to patient information and billing details
Employee training to ensure that everyone handling sensitive data understands HIPAA guidelines
The Benefits of Working with APM BILLING for HIPAA-Compliant Billing Services
By choosing APM BILLING, you gain the peace of mind that comes with knowing your billing processes are in full compliance with HIPAA regulations. Here are some of the key benefits of our HIPAA-compliant billing services:
Data Security: We use the latest technology to protect patient information, ensuring that all billing data is securely transmitted and stored.
Regulatory Compliance: Our team stays up-to-date with the latest changes to HIPAA regulations, ensuring that your practice remains compliant with all legal requirements.
Reduced Risk of Penalties: HIPAA violations can lead to significant fines and penalties. By outsourcing your billing to APM BILLING, you minimize the risk of compliance issues and the associated costs.
Enhanced Trust: Patients trust healthcare providers to keep their personal and medical information safe. By using our HIPAA-compliant billing services, you show your commitment to maintaining privacy, which fosters trust and enhances your reputation.
Efficiency and Accuracy: In addition to security, we ensure that your billing processes are efficient and accurate, leading to faster claim submissions, reduced denials, and increased revenue.
Why Choose APM BILLING for HIPAA-Compliant Billing Services?
Expertise: Our experienced team is dedicated to ensuring that all of your billing practices comply with HIPAA guidelines.
Tailored Solutions: We offer customized solutions that meet the specific needs of your healthcare practice, whether you’re a clinic, provider, or specialty office.
Focus on Security: We take security seriously and use state-of-the-art systems to protect all sensitive information.
Reliable Support: With APM BILLING, you’ll have a trusted partner in billing that is committed to safeguarding your practice’s financial and data integrity.
Get Started with APM BILLING Today
At APM BILLING, we understand the importance of maintaining HIPAA-compliant billing services in today's healthcare environment. We are here to help your practice stay secure, compliant, and financially efficient.
Contact us today at +1-800-621-3354 to learn more about how we can help streamline your billing process while ensuring complete protection of patient data. Visit our office at 19104 Philadelphia, Pennsylvania, and let APM BILLING handle your billing needs with the utmost professionalism and care.
Let APM BILLING take the stress out of billing while keeping your practice compliant with HIPAA regulations, so you can focus on what matters most—caring for your patients.2 -
Top Benefits of Using Data Loss Prevention in Microsoft 365
Data Loss Prevention (DLP) in Microsoft 365 offers numerous benefits to organizations aiming to protect sensitive information and ensure compliance. One of the top advantages is enhanced data protection, where DLP policies help identify, monitor, and restrict the sharing of sensitive information like credit card details or personal identification numbers across Microsoft 365 apps (Outlook, SharePoint, OneDrive, and Teams). This proactive security measure prevents unauthorized access or accidental sharing of confidential data.
Another key benefit is regulatory compliance. DLP helps organizations comply with data protection regulations such as GDPR, HIPAA, and CCPA by enforcing policies that limit data exposure and unauthorized sharing, reducing the risk of costly fines.
Microsoft 365 DLP also offers visibility and control. IT administrators can monitor user actions and identify potential risks in real time, making it easier to enforce security measures. Additionally, user education is integrated through policy tips, which educate users about data protection during daily tasks.
Finally, DLP offers seamless integration across all Microsoft 365 platforms, making it easy to manage and enforce consistent security policies across emails, documents, and collaborative tools, ensuring comprehensive protection for the entire organization. -
Vacuum Cyber Hack: The Premier Solution for Recovering Stolen Bitcoin
In the unpredictable world of cryptocurrency, losing Bitcoin to theft can feel devastating. Vacuum Cyber Hack has become the go to solution for individuals seeking to recover their stolen or frozen assets, delivering unmatched results through expertise, innovation, and trust. Their team of highly skilled cyber specialists employs advanced forensic tools and cutting-edge technology to trace stolen funds with precision. From the moment you engage their services, their professionalism and commitment to confidentiality are evident, ensuring that your sensitive information remains secure throughout the recovery process. What makes Vacuum Cyber Hack stand out is their unwavering dedication to ethical practices and client satisfaction. Their transparent communication and tailored approach make even the most complex cases manageable, providing clarity and reassurance during what is often a stressful experience. Countless clients have trusted Vacuum Cyber Hack to recover their assets, and their impressive track record of success speaks for itself. For those impacted by Bitcoin theft, Vacuum Cyber Hack isn’t just a service it’s a lifeline, restoring both your financial assets and your confidence in cryptocurrency security. Do well to hire them today!
Email: support @ vacuumcyberhack . com
Whatsapp:+39 351 059 0507
Website: https : //vacuumcyber hack .co m/3 -
In Alpro soy milk range, the original one is often overlooked. There are ridiculously tasty soy vanilla, soy almond and professional coconut. But being THAT sensitive I can always distinguish like yea, here’s the soy and here’s the coconut purée. This always prevented me from focusing on just soy and how complex it really is.
So I tried the original soy milk and yes, the purest form was hidden in plain sight all this time. It’s just soy, pure soy, like a pokimane subreddit meetup. I love it.
It’s a moment of a purist finding a pure thing. This is the IDEA of soy milk, like Prolog is the idea of a declarative language. 6
6 -
Vacuum Cyber Hack: The Premier Solution for Recovering Stolen Bitcoin
In the unpredictable world of cryptocurrency, losing Bitcoin to theft can feel devastating. Vacuum Cyber Hack has become the go to solution for individuals seeking to recover their stolen or frozen assets, delivering unmatched results through expertise, innovation, and trust. Their team of highly skilled cyber specialists employs advanced forensic tools and cutting-edge technology to trace stolen funds with precision. From the moment you engage their services, their professionalism and commitment to confidentiality are evident, ensuring that your sensitive information remains secure throughout the recovery process. What makes Vacuum Cyber Hack stand out is their unwavering dedication to ethical practices and client satisfaction. Their transparent communication and tailored approach make even the most complex cases manageable, providing clarity and reassurance during what is often a stressful experience. Countless clients have trusted Vacuum Cyber Hack to recover their assets, and their impressive track record of success speaks for itself. For those impacted by Bitcoin theft, Vacuum Cyber Hack isn’t just a service it’s a lifeline, restoring both your financial assets and your confidence in cryptocurrency security. Do well to hire them today!
Email: support @ vacuumcyberhack . com
Whatsapp:+39 351 059 0507
Website: https : //vacuumcyber hack .co m/2 -
As the head of Quantum Innovations, based in Seattle, Washington, I’ve always taken pride in our company’s commitment to cutting-edge technology and innovation. However, a recent security breach has underscored how vulnerable we were to a major cybersecurity threat involving our corporate mobile devices. The breach began when several employees unknowingly downloaded a malicious app from a third-party app store. What initially appeared to be a harmless app turned out to contain malware, granting cybercriminals access to sensitive company data. In total, the attackers stole approximately $200,000 USD worth of proprietary business information, including financial records, intellectual property, and confidential communications. Even more alarming, the breach led to the theft of employee banking details, enabling unauthorized transfers of funds from both personal and corporate accounts. The breach was discovered when our IT team noticed unusual activity on the affected devices, including unauthorized access to secure files and suspicious data transfers. After conducting a thorough investigation, we realized that the malware had been secretly transmitting our valuable data to an external server, including sensitive financial information. At that point, it became clear that the situation was far worse than we had initially anticipated.In response to this crisis, I reached out to TRUST GEEKS HACK EXPERT at Web, https :/ / t r u s t g e e k s h a c k e x p e r t . c o m/ E m a i l : i n f o @ t r u s t g e e k s h a c k e x p e r t.c o m And T e l e G r a m:: T r u s t g e e k s h a c k e x p e r t, A renowned cybersecurity firm with a reputation for its expertise in mobile device security and data recovery. Their team acted swiftly to assess the full scope of the attack, clean the infected devices, and secure our mobile systems.Thanks to their expert intervention, we were able to completely remove the malware from all affected devices, TRUST GEEKS HACK EXPERT data recovery specialists went above and beyond to recover not only the stolen company data but also the funds that had been illicitly transferred from both employee and corporate bank accounts. Through negotiation with authorities and tracking the stolen funds, they successfully managed to recover every dollar that had been taken. Their diligence and expertise were truly exceptional, and because of their efforts, we were able to avert what could have been a catastrophic financial loss.In the wake of this breach, we are more committed than ever to fortifying our security measures. The swift response and effective recovery efforts from TRUST GEEKS HACK EXPERT have been invaluable in restoring our confidence and securing our operations.1
-
TRUSTWORTHY CRYPTO RECOVERY SERVICE- HIRE SALVAGE ASSET RECOVERY
At Tax Ease Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Salvage Asset Recovery. Salvage Asset Recovery’s team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform. Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Salvage Asset Recovery has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Salvage Asset Recovery helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information. Thanks to the quick and efficient actions of Salvage Asset Recovery, Tax Ease Solutions was able to recover $980,000 of the lost funds and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Salvage Asset ’s continued support, we will fully resolve the situation.
Their Contact info,
WhatsApp+ 1 8 4 7 6 5 4 7 0 9 6 1
1 -
RECOVER BACK YOUR HARD EARN MONEY SCAMMED BY ONLINE IMPERSONATORS OR HACKERS FROM ANY PLATFORM.
At TaxEase Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Digital Gold Hunter. Digital Gold Hunters team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform.Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Digital Gold Hunter has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Digital Gold Hunter helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information.Thanks to the quick and efficient actions of Digital Gold Hunter, and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Digital Gold Hunter ’s continued support, we will fully resolve the situation.
Their Contact info,
Email: D i g i t a l g o l d h u n t e r @ t e c h -c e n t e r . c o m1 -
Looking for iOS and Android app developers to join startup in Rutherford, NJ area. Must be able to show portfolio of apps and have some published. Must be able to pull and compare data with sensitive databases (social security number, passport, birth certificate, etc) to verify user. You will be compensated hourly. Must sign NDA.
-
🐟💩The image i fetch from s3 is of type byte array
I return it to angular as an ArrayBuffer
Which then needs to be somehow converted to an image so i can fucking show it
Then after research i had to convert ArrayBuffer to Blob
And from Blob to URL encoded object which returns a string that now shows the full image in img tag
Somehow, by a sheer of trials and error i have just accidentally made a very secure way of fetching a very sensitive piece of document (verification document with user's personal data on it) and now in browser this is shown as blob:shit-image/random-hash. Not even the file extension. This means nobody can download this image. You fucking cant. Its a Blob motherfucker! Like a Blob Fish. It saves either a .txt when you try to save it (no idea how) and if you try to open the image in new tab it shows gibberish text. This means you can read-only this highly sensitive document image and not manipulate it, not even download it. Perfect. I have just made a very secure software by accident.
(this blob fish looks like my shit) 3
3 -
Welcome to Amazing Series – Where Quality Meets Innovation
At Amazing Series, we are committed to providing you with high-quality products that enhance your lifestyle and make daily living more enjoyable. From smart kitchen appliances to eco-friendly pet products, we offer a wide range of items that cater to all your needs. Our focus on quality and sustainability ensures that every product you purchase will elevate your home, health, and beauty routine.
Why Choose Amazing Series?
Uncompromising Quality
We believe in offering only the best. Whether you’re looking for smart kitchen appliances, high-quality non-stick cookware, or natural body care products, each item in our store is carefully selected for its durability, performance, and value. We aim to provide you with products that you can rely on day after day.
Diverse Product Range
At Amazing Series, we understand that everyone has different needs. That’s why we offer a broad selection of products, including eco-friendly pet products and the best makeup brands for sensitive skin. Our curated selection ensures you’ll find exactly what you're looking for, whether it’s for your kitchen, your home, or your personal care.
Sustainable and Eco-Friendly Choices
We are proud to offer a range of eco-friendly products that help reduce your environmental footprint. From sustainable pet products to natural body care items, Amazing Series is committed to promoting eco-conscious choices for a better planet.
Convenient Shopping Experience
Shopping at Amazing Series is hassle-free. Our online store is designed to be easy to navigate, allowing you to find your favorite products in just a few clicks. We offer reliable shipping to ensure that your orders are delivered quickly and safely to your doorstep.
Our Product Categories
Smart Kitchen Appliances
Transform your cooking experience with our smart kitchen appliances. From Wi-Fi-enabled ovens to intelligent blenders, these appliances make your time in the kitchen more efficient and enjoyable. Control your devices remotely, save time, and elevate your meals with the latest in kitchen technology. Whether you’re a seasoned chef or a home cook, our smart appliances make meal prep easier and more convenient.
High-Quality Non-Stick Cookware
Our high-quality non-stick cookware is designed for easy cooking and cleaning. Perfect for anyone who loves to cook without the hassle of stuck food, our cookware ensures that your meals cook evenly and clean up effortlessly. With a range of sizes and styles available, these durable, non-stick pans and pots are essential for any modern kitchen.
Eco-Friendly Pet Products
At Amazing Series, we believe in taking care of our furry friends and the planet. That’s why we offer eco-friendly pet products made from sustainable materials. From biodegradable waste bags to natural grooming supplies, our pet products are designed to be gentle on the environment and provide your pets with the care they deserve. Give your pets the best while protecting the Earth.
Natural Body Care Products
Pamper your skin with our range of natural body care products. Free from harmful chemicals and artificial fragrances, our body care items are crafted using only the finest natural ingredients. Whether you’re looking for moisturizers, scrubs, or bath oils, our products will leave your skin feeling nourished, smooth, and healthy.
Best Makeup Brands for Sensitive Skin
Discover the best makeup brands for sensitive skin at Amazing Series. Our collection includes makeup that’s free from harsh chemicals, fragrances, and dyes, making it perfect for those with sensitive skin. From foundation to lip care, we offer a range of products that provide flawless coverage while caring for your skin’s delicate needs. Look beautiful without compromising your skin’s health.
Why Shop with Us?
Curated for Quality and Performance
Every product in our store is handpicked for its exceptional quality and performance. Whether you're purchasing smart kitchen appliances or natural body care products, you can trust that each item has been selected to meet our high standards.
Sustainability Matters
We care about the environment, which is why we offer a wide range of eco-friendly products. From sustainable pet products to non-toxic body care, you can shop knowing that you're making choices that are better for the planet.
Affordable and Accessible
At Amazing Series, we offer premium products at competitive prices. We want you to experience the best without breaking the bank, which is why we keep our prices affordable while maintaining the quality you expect.
Reliable Shipping
We understand that you want your products quickly, which is why we offer fast and reliable shipping. You can trust that your order will be delivered on time and in perfect condition.5