Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "open access"
-
Yesterday: Senior dev messages out a screenshot of someone using an extension method I wrote (he didn’t know I wrote it)..
SeniorDev: “OMG…that has to be the stupidest thing I ever saw.”
Me: “Stupid? Why?”
SeniorDev: “Why are they having to check the value from the database to see if it’s DBNull and if it is, return null. The database value is already null. So stupid.”
Me: “DBNull is not null, it has a value. When you call the .ToString, it returns an empty string.”
SeniorDev: ”No it doesn’t, it returns null.”
<oh no he didn’t….the smack down begins>
Me: “Really? Are you sure?”
SeniorDev: “Yes! And if the developer bothered to write any unit tests, he would have known.”
Me: “Unit tests? Why do you assume there aren’t any unit tests? Did you look?”
<at this moment, couple other devs take off their head phones and turn around>
SeniorDev:”Well…uh…I just assumed there aren’t because this is an obvious use case. If there was a test, it would have failed.”
Me: “Well, let’s take a look..”
<open up the test project…navigate to the specific use case>
Me: “Yep, there it is. DBNull.Value.ToString does not return a Null value.”
SeniorDev: “Huh? Must be a new feature of C#. Anyway, if the developers wrote their code correctly, they wouldn’t have to use those extension methods. It’s a mess.”
<trying really hard not drop the F-Bomb or two>
Me: “Couple of years ago the DBAs changed the data access standard so any nullable values would always default to null. So no empty strings, zeros, negative values to indicate a non-value. Downside was now the developers couldn’t assume the value returned the expected data type. What they ended up writing was a lot of code to check the value if it was DBNull. Lots of variations of ‘if …’ , ternary operators, some creative lamda expressions, which led to unexpected behavior in the user interface. Developers blamed the DBAs, DBAs blamed the developers. Remember, Tom and DBA-Sam almost got into a fist fight over it.”
SeniorDev: “Oh…yea…but that’s a management problem, not a programming problem.”
Me: “Probably, but since the developers starting using the extension methods, bug tickets related to mis-matched data has nearly disappeared. When was the last time you saw DBA-Sam complain about the developers?”
SeniorDev: “I guess not for a while, but it’s still no excuse.”
Me: “Excuse? Excuse for what?”
<couple of awkward seconds of silence>
SeniorDev: “Hey, did you guys see the video of the guy punching the kangaroo? It’s hilarious…here, check this out.. ”
Pin shoulders the mat…1 2 3….I win.6 -
EDIT: since this announcement, collabs have been made free to post for all devRant members!
Introducing two big new devRant features!
First, the one @trogus and I are most excited about - Collabs!
Collabs are an easy way to start projects or work on existing projects with the awesome members of the devRant community. You can post a collab listing for the awesome open source project you started that could use some more contributors, that fun idea you have for a brand new project, or really anything you want to gather some fellow devs for. We think it will be a lot of fun.
Collabs also is a devRant first - it's our first paid feature. For each 2 week collab posting, we're charging $14.99. But we wanted to make sure to thank devRant users who have been with us for a while and anyone who contributes often, so anyone with 2,000 points or higher (now or in the future) gets one free collab listing!
The main reason we see collabs as a great first paid feature is because requiring payment or 2,000 points serves to be a slight barrier in posting a collab. We think for collaborations to be successful it's important to have some way to keep out listings where the poster has no intent of following through and we hope this is a good start to doing that.
NOTE: if the collab you are looking to create is devRant-centric (ex. a devRant Chrome extension), we will give you a free credit especially for that so you don't have to pay or use your earned free one. Just contact us (info@devrant.io) if your project falls into that category.
In addition, after tons of demand from the community, you can now change your username and email address! One important note is that you only get to change your username one time every 6 months, so use it cautiously :) You can access this feature in the "more" tab, then settings, then "Edit username or email."
If you have any questions or feedback about any of this, just let us know! We hope everyone enjoys :) 52
52 -
After listening to two of our senior devs play ping pong with a new member of our team for TWO DAYS!
DevA: "Try this.."
Junior: "Didn't work"
DevB: "Try that .."
Junior: "Still not working"
I ask..
Me:"What is the problem?"
Few ums...uhs..awkward seconds of silence
Junior: "App is really slow. Takes several seconds to launch and searching either crashes or takes a really long time."
DevA: "We've isolated the issue with Entity Framework. That application was written back when we used VS2010. Since that application isn't used very often, no one has had to update it since."
DevB: "Weird part is the app takes up over 3 gigs of ram. Its obviously a caching issue. We might have to open up a ticket with Microsoft."
Me: "Or remove EF and use ADO."
DevB: "That would be way too much work. The app is supposed to be fully deprecated and replaced this year."
Me: "Three of you for the past two days seems like a lot of work. If EF is the problem, you remove EF."
DevA: "The solution is way too complicated for that. There are 5 projects and 3 of those have circular dependencies. Its a mess."
DevB: "No fracking kidding...if it were written correctly the first time. There aren't even any fracking tests."
Me:"Pretty sure there are only two tables involved, maybe 3 stored procedures. A simple CRUD app like this should be fairly straight forward."
DevB: "Can't re-write the application, company won't allow it. A redesign of this magnitute could take months. If we can't fix the LINQ query, we'll going to have the DBAs change the structures to make the application faster. I don't see any other way."
Holy frack...he didn't just say that.
Over my lunch hour, I strip down the WPF application to the basics (too much to write about, but the included projects only had one or two files), and created an integration test for refactoring the data access to use ADO. After all the tests and EF removed, the app starts up instantly and searches are also instant. Didn't click through all the UI, but the basics worked.
Sat with Junior, pointed out my changes (the 'why' behind the 'what') ...and he how he could write unit tests around the ViewModel behavior in the UI (and making any changes to the data access as needed).
Today's standup:
Junior: "Employee app is fixed. Had some help removing Entity Framework and how it starts up fast and and searches are instant. Going to write unit tests today to verify the UI behaivor. I'll be able to deploy the application tomorrow."
DevA: "What?! No way! You did all that yesterday?"
Me: "I removed the Entity Framework over my lunch hour. Like I said, its basic CRUD and mostly in stored procedures. All the data points are covered by integration tests, but didn't have time for the unit tests. It's likely I broke some UI behavior, but the unit tests should catch those."
DevB: "I was going to do that today. I knew taking out Entity Framework wouldn't be a big deal."
Holy fracking frack. You fracking lying SOB. Deeeep breath...ahhh...thanks devRant. Flame thrower event diverted.13 -
Oh, man, I just realized I haven't ranted one of my best stories on here!
So, here goes!
A few years back the company I work for was contacted by an older client regarding a new project.
The guy was now pitching to build the website for the Parliament of another country (not gonna name it, NDAs and stuff), and was planning on outsourcing the development, as he had no team and he was only aiming on taking care of the client service/project management side of the project.
Out of principle (and also to preserve our mental integrity), we have purposely avoided working with government bodies of any kind, in any country, but he was a friend of our CEO and pleaded until we singed on board.
Now, the project itself was way bigger than we expected, as the wanted more of an internal CRM, centralized document archive, event management, internal planning, multiple interfaced, role based access restricted monster of an administration interface, complete with regular user website, also packed with all kind of features, dashboards and so on.
Long story short, a lot bigger than what we were expecting based on the initial brief.
The development period was hell. New features were coming in on a weekly basis. Already implemented functionality was constantly being changed or redefined. No requests we ever made about clarifications and/or materials or information were ever answered on time.
They also somehow bullied the guy that brought us the project into also including the data migration from the old website into the new one we were building and we somehow ended up having to extract meaningful, formatted, sanitized content parsing static HTML files and connecting them to download-able files (almost every page in the old website had files available to download) we needed to also include in a sane way.
Now, don't think the files were simple URL paths we can trace to a folder/file path, oh no!!! The links were some form of hash combination that had to be exploded and tested against some king of database relationship tables that only had hashed indexes relating to other tables, that also only had hashed indexes relating to some other tables that kept a database of the website pages HTML file naming. So what we had to do is identify the files based on a combination of hashed indexes and re-hashed HTML file names that in the end would give us a filename for a real file that we had to then search for inside a list of over 20 folders not related to one another.
So we did this. Created a script that processed the hell out of over 10000 HTML files, database entries and files and re-indexed and re-named all this shit into a meaningful database of sane data and well organized files.
So, with this we were nearing the finish line for the project, which by now exceeded the estimated time by over to times.
We test everything, retest it all again for good measure, pack everything up for deployment, simulate on a staging environment, give the final client access to the staging version, get them to accept that all requirements are met, finish writing the documentation for the codebase, write detailed deployment procedure, include some automation and testing tools also for good measure, recommend production setup, hardware specs, software versions, server side optimization like caching, load balancing and all that we could think would ever be useful, all with more documentation and instructions.
As the project was built on PHP/MySQL (as requested), we recommended a Linux environment for production. Oh, I forgot to tell you that over the development period they kept asking us to also include steps for Windows procedures along with our regular documentation. Was a bit strange, but we added it in there just so we can finish and close the damn project.
So, we send them all the above and go get drunk as fuck in celebration of getting rid of them once and for all...
Next day: hung over, I get to the office, open my laptop and see on new email. I only had the one new mail, so I open it to see what it's about.
Lo and behold! The fuckers over in the other country that called themselves "IT guys", and were the ones making all the changes and additions to our requirements, were not capable enough to follow step by step instructions in order to deploy the project on their servers!!!
[Continues in the comments]25 -
So a few days ago I felt pretty h*ckin professional.
I'm an intern and my job was to get the last 2003 server off the racks (It's a government job, so it's a wonder we only have one 2003 server left). The problem being that the service running on that server cannot just be placed on a new OS. It's some custom engineering document server that was built in 2003 on a 1995 tech stack and it had been abandoned for so long that it was apparently lost to time with no hope of recovery.
"Please redesign the system. Use a modern tech stack. Have at it, she's your project, do as you wish."
Music to my ears.
First challenge is getting the data off the old server. It's a 1995 .mdb file, so the most recent version of Access that would be able to open it is 2010.
Option two: There's an "export" button that literally just vomits all 16,644 records into a tab-delimited text file. Since this option didn't require scavenging up an old version of Access, I wrote a Python script to just read the export file.
And something like 30% of the records were invalid. Why? Well, one of the fields allowed for newline characters. This was an issue because records were separated by newline. So any record with a field containing newline became invalid.
Although, this did not stop me. Not even close. I figured it out and fixed it in about 10 minutes. All records read into the program without issue.
Next for designing the database. My stack is MySQL and NodeJS, which my supervisors approved of. There was a lot of data that looked like it would fit into an integer, but one or two odd records would have something like "1050b" which mean that just a few items prevented me from having as slick of a database design as I wanted. I designed the tables, about 18 columns per record, mostly varchar(64).
Next challenge was putting the exported data into the database. At first I thought of doing it record by record from my python script. Connect to the MySQL server and just iterate over all the data I had. But what I ended up actually doing was generating a .sql file and running that on the server. This took a few tries thanks to a lot of inconsistencies in the data, but eventually, I got all 16k records in the new database and I had never been so happy.
The next two hours were very productive, designing a front end which was very clean. I had just enough time to design a rough prototype that works totally off ajax requests. I want to keep it that way so that other services can contact this data, as it may be useful to have an engineering data API.
Anyways, that was my win story of the week. I was handed a challenge; an old, decaying server full of important data, and despite the hitches one might expect from archaic data, I was able to rescue every byte. I will probably be presenting my prototype to the higher ups in Engineering sometime this week.
Happy Algo!8 -
Hey everyone,
We have a few pieces of news we're very excited to share with everyone today. Apologies for the long post, but there's a lot to cover!
First, as some of you might have already seen, we just launched the "subscribed" tab in the devRant app on iOS and Android. This feature shows you a feed of the most recent rant posts, likes, and comments from all of the people you subscribe to. This activity feed is updated in real-time (although you have to manually refresh it right now), so you can quickly see the latest activity. Additionally, the feed also shows recommended users (based on your tastes) that you might want to subscribe to. We think both of these aspects of the feed will greatly improve the devRant content discovery experience.
This new feature leads directly into this next announcement. Tim (@trogus) and I just launched a public SaaS API service that powers the features above (and can power many more use-cases across recommendations and activity feeds, with more to come). The service is called Pipeless (https://pipeless.io) and it is currently live (beta), and we encourage everyone to check it out. All feedback is greatly appreciated. It is called Pipeless because it removes the need to create complicated pipelines to power features/algorithms, by instead utilizing the flexibility of graph databases.
Pipeless was born out of the years of experience Tim and I have had working on devRant and from the desire we've seen from the community to have more insight into our technology. One of my favorite (and earliest) devRant memories is from around when we launched, and we instantly had many questions from the community about what tech stack we were using. That interest is what encouraged us to create the "about" page in the app that gives an overview of what technologies we use for devRant.
Since launch, the biggest technology powering devRant has always been our graph database. It's been fun discussing that technology with many of you. Now, we're excited to bring this technology to everyone in the form of a very simple REST API that you can use to quickly build projects that include real-time recommendations and activity feeds. Tim and I are really looking forward to hopefully seeing members of the community make really cool and unique things with the API.
Pipeless has a free plan where you get 75,000 API calls/month and 75,000 items stored. We think this is a solid amount of calls/storage to test out and even build cool projects/features with the API. Additionally, as a thanks for continued support, for devRant++ subscribers who were subscribed before this announcement was posted, we will give some bonus calls/data storage. If you'd like that special bonus, you can just let me know in the comments (as long as your devRant email is the same as Pipeless account email) or feel free to email me (david@hexicallabs.com).
Lastly, and also related, we think Pipeless is going to help us fulfill one of the biggest pieces of feedback we’ve heard from the community. Now, it is going to be our goal to open source the various components of devRant. Although there’s been a few reasons stated in the past for why we haven’t done that, one of the biggest reasons was always the highly proprietary and complicated nature of our backend storage systems. But now, with Pipeless, it will allow us to start moving data there, and then everyone has access to the same system/technology that is powering the devRant backend. The first step for this transition was building the new “subscribed” feed completely on top of Pipeless. We will be following up with more details about this open sourcing effort soon, and we’re very excited for it and we think the community will be too.
Anyway, thank you for reading this and we are really looking forward to everyone’s feedback and seeing what members of the community create with the service. If you’re looking for a very simple way to get started, we have a full sample dataset (1 click to import!) with a tutorial that Tim put together (https://docs.pipeless.io/docs/...) and a full dev portal/documentation (https://docs.pipeless.io).
Let us know if you have any questions and thanks everyone!
- David & Tim (@dfox & @trogus) 53
53 -
I’m a senior dev at a small company that does some consulting. This past October, some really heavy personal situation came up and my job suffered for it. I raised the flag and was very open with my boss about it and both him and my team of 3 understood and were pretty cool with me taking on a smaller load of work while I moved on with some stuff in my life. For a week.
Right after that, I got sent to a client. “One month only, we just want some presence there since it’s such a big client” alright, I guess I can do that. “You’ll be in charge of a team of a few people and help them technically.” Sounds good, I like leading!
So I get here. Let’s talk technical first: from being in a small but interesting project using Xamarin, I’m now looking at Visual Basic code, using Visual Studio 2010. Windows fucking Forms.
The project was made by a single dev for this huge company. She did what she could but as the requirements grew this thing became a behemoth of spaghetti code and User Controls. The other two guys working on the project have been here for a few months and they have very basic experience at the job anyways. The woman that worked on the project for 5 years is now leaving because she can’t take it anymore.
And that’s not the worse of it. It took from October to December for me to get a machine. I literally spent two months reading on my cellphone and just going over my shitty personal situation for 8 hours a day. I complained to everyone I could and nothing really worked.
Then I got a PC! But wait… no domain user. Queue an extra month in which I could see the Windows 7 (yep) log in screen and nothing else. Then, finally! A domain user! I can log in! Just wait 2 extra weeks for us to give your user access to the subversion rep and you’re good to go!
While all of this went on, I didn’t get an access card until a week ago. Every day I had to walk to the reception desk, show my ID and request they call my boss so he could grant me access. 5 months of this, both at the start of the day and after lunch. There was one day in particular, between two holidays, in which no one that could grant me access was at the office. I literally stood there until 11am in which I called my company and told them I was going home.
Now I’ve been actually working for a while, mostly fixing stuff that works like crap and trying to implement functions that should have been finished but aren’t even started. Did I mention this App is in production and being used by the people here? Because it is. Imagine if you will the amount of problems that an application that’s connecting to the production DB can create when it doesn’t even validate if the field should receive numeric values only. Did I mention the DB itself is also a complete mess? Because it is. There’s an “INDEXES” tables in which, I shit you not, the IDs of every other table is stored. There are no Identity fields anywhere, and instead every insert has to go to this INDEXES table, check the last ID of the table we’re working on, then create a new registry in order to give you your new ID. It’s insane.
And, to boot, the new order from above is: We want to split this app in two. You guys will stick with the maintenance of half of it, some other dudes with the other. Still both targeting the same DB and using the same starting point, but each only working on the module that we want them to work in. PostmodernJerk, it’s your job now to prepare the app so that this can work. How? We dunno. Why? Fuck if we care. Kill you? You don’t deserve the swift release of death.
Also I’m starting to get a bit tired of comments that go ‘THIS DOESN’T WORK and ‘I DON’T KNOW WHY WE DO THIS BUT IT HELPS and my personal favorite ‘??????????????????????14 -
I had just started my new job and deleted 3 years of data that the client had spent over £450,000 collecting 😱
another developer used my PC to quickly access the clients database while I was out the room as I had sql management studio open. I went back to my PC thinking I was connected to my local database, did a few truncate tables to test my software and :0 minutes later I get a call asking why there was no data on the server!
Thank god for backups 😓7 -
Its that time of the morning again where I get nothing done and moan about the past ... thats right its practiseSafeHex's most incompetent co-worker!!!
Today I'd like to tell you the story of "i". Interesting about "I" is that he was actually a colleague of yesterdays nominee "G" (and was present at the "java interface" video call, and agreed with G!): https://devrant.com/rants/1152317/...
"I" was the spearhead of a project to end all projects in that company. It was suppose to be a cross-platform thing but ended up only working for iOS. It was actually quite similar to this: https://jasonette.com/ (so similar i'm convinced G / I were part of this but I can't find their github ID's in it).
To briefly explain the above + what they built ... this is the worst piece of shit you can imagine ... and thats a pretty strong statement looking back at the rest of this series so far!
"I" thought this would solve all of our problems of having to build similar-ish apps for multiple customers by letting us re-use more code / UI across apps. His main solution, was every developers favourite part of writing code. I mean how often do you sit back and say:
"God damn I wish more of this development revolved around passing strings back and forth. Screw autocomplete, enums and typed classes / variables, I want more code / variables inside strings in this library!"
Yes thats right, the main part of this bullshittery was putting your entire app, into JSON, into a string and downloading it over http ... what could possibly go wrong!
Some of my issues were:
- Everything was a string, meaning we had no autocomplete. Every type and property had to be remembered and spelled perfectly.
- Everything was a string so we had no way to cmd + click / ctrl + click something to see somethings definition.
- Everything was a string so any business logic methods had to be remembered, all possible overloaded versions, no hints at param types no nothing.
- There was no specific tooling for any of this, it was literally open up xcode, create a json file and start writing strings.
- We couldn't use any of the native UI builders ... cause strings!
- We couldn't use any of the native UI layout constructs and we had to use these god awful custom layout managers, with a weird CSS feel to them.
What angered me a lot was their insistence that "You can download a new app over http and it will update instantly" ... except you can't because you can't download new business logic only UI. So its a new app, but must do 100% exactly the same thing as before.
His other achievements include:
- Deciding he didn't like apple's viewController and navigationBar classes and built his own, which was great when iOS 7 was released (changed the UI to allow drawing under the status bar) and we had no access to any of apples new code or methods, meaning everything had to be re-built from scratch.
- On my first week, my manager noticed he fucked up the login error handling on the app I was taking over. He noticed this as I was about to leave for the evening. I stayed so we could call him (he was in an earlier timezone). Rather than deal with his fucked up, he convinced the manager it would be a "great learning experience" for me to do it ... and stay in late ... while he goes home early.
- He once argued with me in front of the CEO, that his frankenstein cross-platform stuff was the right choice and that my way of using apples storyboards (and well thought out code) wasn't appropriate. So I challenged him to prove it, we got 2 clients who needed similar apps, we each did it our own way. He went 8 man weeks over, I came in 2 days under and his got slated in the app store for poor performance / issues. #result.
But rather than let it die he practically sucked off the CEO to let him improve the cross platform tooling instead.
... in that office you couldn't swing a cat without hitting a retard.
Having had to spend a lot more time working with him and more closely than most of the other nominees, at a minimum "I" is on the top of my list for needing a good punch in the face. Not for being an idiot (which he is), not for ruining so much (which he did), but for just being such an arrogant bastard about it all, despite constant failure.
Will "I" make it to most incompetent? Theres some pretty stiff competition so far
Tune in later for more practiceSafeHex's most incompetent co-worker!!!6 -
"Opps.. I'm sorry, but you have insufficient rights to open this Ticket."
Well. You know what? I AM THE FUCKING SYSTEM ADMINISTRATOR YOU CUNT!
YOU HAVE INSUFFICIENT RIGHTS to restrict me access to that fucking ticket!
"Oh. In that case, go ahead."
THANK YOU. FUCKING PRICK.4 -
When I was in the army I wasn't officially a dev. But one commander needed someone to develop a bunch of stuff and couldn't get a dev officially, so I ended up as his "assistant", which was an awesome job with about 60% time spent on software development.
Except I wasn't an official developer, so I wasn't afforded many of the privileges developers get, like a slightly more powerful machine, a copy of Visual Studio, or an internet connection. In this environment you couldn't even download files and transfer the to your computer without a long process, and I couldn't get development tools past that process anyway.
So I was stuck with whatever dev tools I had pre-installed with Windows. Thankfully, I had the brand new Windows XP, so I had the .Net framework installed, which comes with the command line compiler csc. I got to work with notepad and csc; my first order of business: write an editor that could open multiple files, and press F5 to compile and run my project.
Being a noob at the time, with almost no actual experience, and nobody supervising my work, I had a few brilliant ideas. For example, I one day realized I could map properties of an object to a field in a database table, and thus wrote a rudimentary OR/M. My database, I didn't mention, was Access, because that didn't need installation. I connected to it properly via ADO.NET, at least.
The most surprising thing though, in retrospect, is the stuff I wrote actually worked.14 -
terms can only be use in programming: -
Where friends have access to your private parts,
Where Parents may kill their child if required,
Where Bugs come in from open windows,
Where one image is worth 128K words,
Where 10 == 2,
Where Zombies are common and not dangerous *,
Where Daemons are always there somewhere
Where the slimmest of USB drives are considered FAT *,
Where comments are made and arguments are passed, **
Where forever alone nerds can also unzip, touch, mount and fsck ***,
Where root is top of the tree,
Where x = x + y is totally correct,
Where opening a jar requires Java,
Where Oct 31 = Dec 25,
Thanks to ASHISH KEDIA for writing these.
Source :- Quora2 -
So my actual job is being a nurse at the local hospital, with coding being just a hobby. However, the way some IT–Related things are treated here are just mind-blowing. Here are some examples:
Issue: Printer is not recognized by network anymore due to not being properly plugged in
Solution: Someone has to tell the house technician, if the house technician is currently not available, ask his assistant who only works part time and like twice a week. House technician took the printer (God knows why), came back 2 days later and plugged it back in.
Issue: Printer 1 of 2 on ICU has run out of ink and since all computers default to printer 1, nobody can print.
Solution: Call the house technician, blah blah, house technician comes, takes ink cartridge of printer 2 and puts it into printer 1.
Issue: Public WiFi is broken, can be connected to but internet access is missing. Probably config issue as a result of a recent blackout.
Solution: Buy a new router, spend 5 days configuring it and complain about how hard networking is.
Issue: Computer is broken, needs to be exchanged with a new one, but how do we transfer the data?
Solution: Instead of just keeping the old hard drive, make a 182GB backup, upload it to the main file server and then download it again on the new computer.
Issue: Nurse returns from vacation, forgot the password to her network account.
Solution: Call the technician who then proceeds to open a new account, copies all the files from the old one and tells her to pick an easier password this time. She chooses "121213".12 -
I was 15 years old and the first year of high school. Everything was new to me and I was such a newbie. At that time I had 2-3 year of programming behind me at an institution where they taught competitive programming. And I knew something about computers. Not much but more than most of my school mates. At that time I wanted to become "super cool hacker".
So we had this very very thought teacher for history which was also our form master. She really knows how to explained everything about history and in an interesting way. But while she was teaching we also had to write down notes from her powerpoints that were on a projector. And occasionally she would wait for us to copy everything and then move on with her lecture. But sometimes she didn't. This was frustrating as hell. The whole class would complain about this because you couldn't take notes down normal, you had to do it at double speed.
But she got one weak spot. She was not very good with computers. Our school computers were locked in some kinda closet so that students didn't have physical access to a computer and were also password protected. So I came up with the plan to plant wireless mouse in her computer so that I could control her mouse. At that time it seemed like SUPER HACKER MASTER PLAN.
So I got an opportunity one time when she left the classroom and let closet where the computer was open. I quickly sneaked the USB of the wireless mouse in the computer and then go back to the seat.
So THE FUN began.
Firstly I would only go back in powerpoint so that all my schoolmates could write down notes including me. And it was hilarious to watch when she didn't know what is happening. So then I would move her mouse when she tried to close some window. I would just move it slightly so she wouldn't notice that somebody else is controlling mouse. And by missing X button just by slight she would click other things and other things would pop up and now she had to close this thing so it became a nightmare for her. And she would become angry at the mouse and start complaining how the computer doesn't work and that mouse doesn't obey her.
One time when she didn't pay attention to her computer and projector I went to paint program and drew a heart and wrote we love you (In Slovenian Imamo vas radi -> See the picture below) and one of my school mates has the picture of it. We were all giggling and she didn't know what is was for. And I managed to close everything before she even noticed.
So it got to the point where she couldn't hand it more so she called our school IT guy so that he would check her computer (2 or 3 weeks passed before she called IT guy). And he didn't find anything. He was really crappy IT guy in general. So one week passed by and I still had messed with her mouse. So she got a replacement computer. Who would guessed all the problems went away (because I didn't have another mouse like that). I guess when our IT guy took the computer to his room and really thoroughly check it he found my USB.
So he told her what was the problem she was so pissed off really I didn't see her pissed off so much in all my 4 years in high school. She demanded the apology from whom did it. And at that moment my mind went through all possible scenarios... And the most likely one was that I was going to be expelled... And I didn't have the balls to say that I did it and I was too afraid... Thanks to God nobody from my school mates didn't tell that it was me.
While she waited that somebody would come forward there was one moment when our looks met and at that moment both of us knew that I was the one that did it.
Next day the whole class wrote the apology letter and she accepted it. But for the rest of 4 years whenever was there a problem with the computer I had to fixed it and she didn't trust anybody not even our IT guy at school. It was our unwritten contract that I would repair her computer to pay off my sin that I did. And she once even trusted me with her personal laptop.
So to end this story I have really high respect for her because she is a great teacher and great persons that guide me through my teen years. And we stayed in contact. 11
11 -
This is kind of a horror story, with a happing ending. It contains a lot of gore images, and some porn. Very long story.
TL;DR Network upgrade
Once upon a time, there were two companies HA and HP, both owned by HC. Many years went by and the two companies worked along side each one another, but sometimes there were trouble, because they weren't sure who was supposed to bill the client for projects HA and HP had worked on together.
At HA there was an IT guy, an imbecile of such. He's very slow at doing his job, doesn't exactly understand what he's doing, nor security principles.
The IT guy at HA also did some IT work for HP from time to time when needed. But he was not in charge of the infrastructure for HP, that was the jobb for one developer who didn't really know what he was doing either.
Whenever a new server was set up at HP, the developer tried many solutions, until he landed on one, but he never removed the other tested solutions, and the config is scattered all around. And no documentation!!
Same goes with network, when something new was added, the old was never removed or reconfigured to something else.
One dark winter, a knight arrived at HP. He had many skills. Networking, server management, development, design and generally a fucking awesome viking.
This genius would often try to cleanse the network and servers, and begged his boss to let him buy new equipment to replace the old, to no prevail.
Whenever he would look in the server room, he would get shivers down his back.
(Image: https://i.bratteng.xyz/Ie9x3YC33C.j...)
One and a half year later, the powerful owners in HA, HP and HC decided it was finally time to merge HA and HP together to HS. The knight thought this was his moment, he should ask CEO if he could be in charge of migrating the network, and do a complete overhault so they could get 1Gb interwebz speeds.
The knight had to come up with a plan and some price estimates, as the IT guy also would do this.
The IT guy proposed his solution, a Sonicwall gateway to 22 000 NOK, and using a 3rd party company to manage it for 3000 NOK/month.
"This is absurd", said the knight to the CEO and CXO, "I can come up with a better solution that is a complete upgrade. And it will be super easy to manage."
The CEO and CXO gave the knight a thumbs up. The race was on. We're moving in 2 months, I got to have the equipment by then, so I need a plan by the end of the week.
He roamed the wide internet, looked at many solutions, and ended up with going for Ubiquiti's Unifi series. Cheap, reliable and pretty nice to look at.
The CXO had mentioned the WiFi at HA was pretty bad, as there was WLAN for each meeting room, and one for the desks, so the phone would constantly jump between networks.
So the knight ended up with this solution:
2x Unifi Securtiy Gateway Pro 4
2x Unifi 48port
1x Unifi 10G 16port
5x Unifi AP-AC-Lite
12x pairs of 10G unifi fibre modules
All with a price tag around the one Sonicwall for 22 000 NOK, not including patch cables, POE injectors and fibre cables.
The knight presented this to the CXO, whom is not very fond of the IT guy, and the CXO thought this was a great solution.
But the IT guy had to have a say at this too, so he was sent the solution and had 2 weeks to dispute the soltion.
Time went by, CXO started to get tired of the waiting, so he called in a meeting with the knight and the IT guy, this was the IT guys chance to dispute the solution.
All he had to say was he was familiar with the Sonicwall solution, and having a 3rd party company managing it is great.
He was given another 2 weeks to dispute the solution, yet nothing happened.
The CXO gave the thumbs up, and the knight orders the equipment.
At this time, the knight asks the IT guy for access to the server room at HA, and a key (which would take 2 months to get sorted, because IT guys is a slow imbecile)
The horrors, Oh the horrors, the knight had never seen anything like this before.
(Image: https://i.bratteng.xyz/HfptwEh9qT.j...)
(Image: https://i.bratteng.xyz/HfptwEh9qT.j...)
(Image: https://i.bratteng.xyz/hmOE2ZuQuE.j...)
(Image: https://i.bratteng.xyz/4Flmkx6slQ.j...)
What are all these for, why is there a fan ductaped to on of the servers.
WHAT IS THIS!
Why are there cables tied in a knot.
WHY!
These are questions we never will know the answers too.
The knight needs access to the servers, and sonicwall to see how this is configured.
After 1.5 month he gains access to the sonicwall and one of the xserve.
What the knight discovers baffles him.
All ports are open, sonicwall is basically in bridge mode and handing out public IPs to every device connected to it.
No VLANs, everything, just open...10 -
This week I quit the corporate life in favour of a much smaller company (60 people in total) and i never felt so good.
After 3 years in 2 big corporations, I began to hate coding mainly because of:
- internal political games. It's like living inside House of Cards everyday.
- management and non-tech people choosing tech stacks. Angular 4 + Bootstrap 4 alpha version + AG-Grid + IE11. Ohhh yeah. Not.
- overtime (even if it was paid double). I never did a single minute of OT for fixing something that I caused. I spent days fixing things caused by others and implementing promises that other people made.
- meetings. I spend 50-60% of the time in pointless meetings (I tracked them in certain time intervals) but the workload is same like I was working 8 hours / day.
- working in encapsulated environments without access to internet or with limited access to internet (no GitHub, no StackOverflow etc.)
- continuously changing work scope. Everyday the management wants something new introduced in the current sprint/release and nobody accepts that they have to remove other things from the scope in order to proper implement everything.
- designers that think they are working for Apple and are arguing with things like "but it's just a button! why does it take 2 days to implement?"
- 20 apps installed additionally on my phone (Citrix Receiver, RSA Token, Mobile@Work Suite etc.) just to be able to read my email
- working with outdated IDEs and tools because they have to approve every new version of a software.
- making tickets for anything. Do you want a glass of water? Open a ticket and ask for it.
- KPIs. KPIs everywhere. You don't deserve anything because the KPIs were not accomplished.
The bad part of the above things is that they affect your day-to-day personality even if you don't see it. You become more like a rock with almost 0 feelings and interests.
This is my first written "rant". If anyone is interested, I will post different situations that will explain a lot of the above aspects.13 -
Mac: Hello welcome please sign in
Dev: Fair enough
Mac: Oh you haven’t signed in in awhile please get get verification from other device
Dev: kk
Mac: Oh you don’t have a dev account, please sign in on this website
Dev: Hm.
Mac: In order to sign up for a dev account you need to download this app
Dev: ???
Mac: Are you sure you want to open this app you just downloaded?
Dev: Sigh.
Mac: In order to sign up for a dev account on this app you need to sign into it
Dev: For the love of god
Mac: Ok now you can build with Xcode.
Xcode: No you can’t. You have to sign in
Dev: fuck sakes.
Mac: Are you sure you want Xcode to access files on your computer?
Dev: …Yup
Xcode: Signing in isn’t enough you have to select the fact you are signed in a dropdown nested 3 menus deep.
Dev: God damn.
Xcode: Build failed please sign in to phone as well.
Phone: New sign in detected, please verify with alternative device.
Dev: Jesus.
Xcode: Build success! Pushing to iPhone.
Dev: Finally.
Xcode: Unknown error occurred. Please go to support.apple.com for help. :)
Dev: …18 -
Our website once had it’s config file (“old” .cgi app) open and available if you knew the file name. It was ‘obfuscated’ with the file name “Name of the cgi executable”.txt. So browsing, browsing.cgi, config file was browsing.txt.
After discovering the sql server admin password in plain text and reporting it to the VP, he called a meeting.
VP: “I have a report that you are storing the server admin password in plain text.”
WebMgr: “No, that is not correct.”
Me: “Um, yes it is, or we wouldn’t be here.”
WebMgr: “It’s not a network server administrator, it’s SQL Server’s SA account. Completely secure since that login has no access to the network.”
<VP looks over at me>
VP: “Oh..I was not told *that* detail.”
Me: “Um, that doesn’t matter, we shouldn’t have any login password in plain text, anywhere. Besides, the SA account has full access to the entire database. Someone could drop tables, get customer data, even access credit card data.”
WebMgr: “You are blowing all this out of proportion. There is no way anyone could do that.”
Me: “Uh, two weeks ago I discovered the catalog page was sending raw SQL from javascript. All anyone had to do was inject a semicolon and add whatever they wanted.”
WebMgr: “Who would do that? They would have to know a lot about our systems in order to do any real damage.”
VP: “Yes, it would have to be someone in our department looking to do some damage.”
<both the VP and WebMgr look at me>
Me: “Open your browser and search on SQL Injection.”
<VP searches on SQL Injection..few seconds pass>
VP: “Oh my, this is disturbing. I did not know SQL injection was such a problem. I want all SQL removed from javascript and passwords removed from the text files.”
WebMgr: “Our team is already removing the SQL, but our apps need to read the SQL server login and password from a config file. I don’t know why this is such a big deal. The file is read-only and protected by IIS. You can’t even read it from a browser.”
VP: “Well, if it’s secured, I suppose it is OK.”
Me: “Open your browser and navigate to … browse.txt”
VP: “Oh my, there it is.”
WebMgr: “You can only see it because your laptop had administrative privileges. Anyone outside our network cannot access the file.”
VP: “OK, that makes sense. As long as IIS is securing the file …”
Me: “No..no..no.. I can’t believe this. The screen shot I sent yesterday was from my home laptop showing the file is publicly available.”
WebMgr: “But you are probably an admin on the laptop.”
<couple of awkward seconds of silence…then the light comes on>
VP: “OK, I’m stopping this meeting. I want all admin users and passwords removed from the site by the end of the day.”
Took a little longer than a day, but after reviewing what the web team changed:
- They did remove the SQL Server SA account, but replaced it with another account with full admin privileges.
- Replaced the “App Name”.txt with centrally located config file at C:\Inetpub\wwwroot\config.txt (hard-coded in the app)
When I brought this up again with my manager..
Mgr: “Yea, I know, it sucks. WebMgr showed the VP the config file was not accessible by the web site and it wasn’t using the SA password. He was satisfied by that. Web site is looking to beat projections again by 15%, so WebMgr told the other VPs that another disruption from a developer could jeopardize the quarterly numbers. I’d keep my head down for a while.”8 -
Just had a fucking god-mode moment.
My dear @Divisionbyzero asked me to help out with DKIM on his Linux server.
Although I'd never done it before, with the help of a search engine and root access to the server, I managed to somehow figure out what was going wrong and fix it.
This is quite deeper than I ever went with debugging!
Also a big thanks to Linux for being open, otherwise I'd be fucking fucked right now.7 -
so um... several of my users access file explorer ONLY via Word.
How?
Well, open Word: File->Open->Computer->Browse (nb. thank you Word 2013 and onwards for making life miserable) and voila, access to documents, downloads, and server shares is gained.
...
Users... they will always find a way7 -
Buckle up kids, this one gets saucy.
At work, we have a stress test machine that trests tensile, puncture and breaking strength for different materials used (wood construction). It had a controller software update that was supposed to be installed. I was called into the office because the folks there were unable to install it, they told me the executable just crashed, and wanted me to take a look as I am the most tech-savvy person there.
I go to the computer and open up the firmware download folder. I see a couple folders, some random VBScript file, and Installation.txt. I open the TXT, and find the first round of bullshit.
"Do not run the installer executable directly as it will not work. Run install.vbs instead."
Now, excuse me for a moment, but what kind of dick-cheese-sniffing cockmonger has end users run VBScript files to install something in 2018?! Shame I didn't think of opening it up and examining it for myself to find out what that piece of boiled dogshit did.
I suspend my cringe and run it, and lo and behold, it installs. I open the program and am faced with entering a license key. I'm given the key by the folks at the office, but quickly conclude no ways of entering it work. I reboot the program and there is an autofilled key I didn't notice previously. Whatever, I think, and hit OK.
The program starts fine, and I try with the login they had previously used. Now it doesn't work for some reason. I try it several times to no avail. Then I check the network inspector and notice that when I hit login, no network activity happens in the program, so I conclude the check must be local against some database.
I browse to the program installation directory for clues. Then I see a folder called "Databases".
"This can't be this easy", I think to myself, expecting to find some kind of JSON or something inside that I can crawl for clues. I open the folder and find something much worse. Oh, so much worse.
I find <SOFTWARE NAME>.accdb in the folder. At this point cold sweat is already running down my back at the sheer thought of using Microsoft Access for any program, but curiosity takes over and I open it anyway.
I find the database for the entire program inside. I also notice at this point that I have read/write access to the database, another thing that sent my alarm bells ringing like St. Pauls cathedral. Then I notice a table called "tUser" in the left panel.
Fearing the worst, I click over and find... And you knew it was coming...
Usernames and passwords in plain text.
Not only that, they're all in the format "admin - admin", "user - user", "tester - tester".
I suspend my will to die, login to the program and re-add the account they used previously. I leave the office and inform the peeps that the program works as intended again.
I wish I was making this shit up, but I really am not. What is the fucking point of having a login system at all when your users can just open the database with a program that nowadays comes bundled with every Windows install and easily read the logins? It's not even like the data structure is confusing like minified JSON or something, it's literally a spreadsheet in a program that a trained monkey could read.
God bless them and Satan condemn the developers of this fuckawful program.8 -
Not exactly a security bug, but there was a company that made a Django app for some internal work and later open sourced it. I was browsing through the code and I saw that the config file had an IP address and a hashed password for the database credentials
When I tried to use them, I was able to login directly to their read replica RDBMS, I had access to all their customer data (including phones & home addresses)
Being the saint I am, I informed them of the ignorance made by their developer and was presented with some cool swag.5 -
Dev: To send push notifications, please open a ticket to get access to the new tool we are using which is dedicated to managing push notifications and push notification campaigns.
Me: ok done.
*5 days later*
Tool owner: Can you please add to the ticket the reason you need access?
Me: “To use it”2 -
I had to open the desktop app to write this because I could never write a rant this long on the app.
This will be a well-informed rebuttal to the "arrays start at 1 in Lua" complaint. If you have ever said or thought that, I guarantee you will learn a lot from this rant and probably enjoy it quite a bit as well.
Just a tiny bit of background information on me: I have a very intimate understanding of Lua and its c API. I have used this language for years and love it dearly.
[START RANT]
"arrays start at 1 in Lua" is factually incorrect because Lua does not have arrays. From their documentation, section 11.1 ("Arrays"), "We implement arrays in Lua simply by indexing tables with integers."
From chapter 2 of the Lua docs, we know there are only 8 types of data in Lua: nil, boolean, number, string, userdata, function, thread, and table
The only unfamiliar thing here might be userdata. "A userdatum offers a raw memory area with no predefined operations in Lua" (section 26.1). Essentially, it's for the API to interact with Lua scripts. The point is, this isn't a fancy term for array.
The misinformation comes from the table type. Let's first explore, at a low level, what an array is. An array, in programming, is a collection of data items all in a line in memory (The OS may not actually put them in a line, but they act as if they are). In most syntaxes, you access an array element similar to:
array[index]
Let's look at c, so we have some solid reference. "array" would be the name of the array, but what it really does is keep track of the starting location in memory of the array. Memory in computers acts like a number. In a very basic sense, the first sector of your RAM is memory location (referred to as an address) 0. "array" would be, for example, address 543745. This is where your data starts. Arrays can only be made up of one type, this is so that each element in that array is EXACTLY the same size. So, this is how indexing an array works. If you know where your array starts, and you know how large each element is, you can find the 6th element by starting at the start of they array and adding 6 times the size of the data in that array.
Tables are incredibly different. The elements of a table are NOT in a line in memory; they're all over the place depending on when you created them (and a lot of other things). Therefore, an array-style index is useless, because you cannot apply the above formula. In the case of a table, you need to perform a lookup: search through all of the elements in the table to find the right one. In Lua, you can do:
a = {1, 5, 9};
a["hello_world"] = "whatever";
a is a table with the length of 4 (the 4th element is "hello_world" with value "whatever"), but a[4] is nil because even though there are 4 items in the table, it looks for something "named" 4, not the 4th element of the table.
This is the difference between indexing and lookups. But you may say,
"Algo! If I do this:
a = {"first", "second", "third"};
print(a[1]);
...then "first" appears in my console!"
Yes, that's correct, in terms of computer science. Lua, because it is a nice language, makes keys in tables optional by automatically giving them an integer value key. This starts at 1. Why? Lets look at that formula for arrays again:
Given array "arr", size of data type "sz", and index "i", find the desired element ("el"):
el = arr + (sz * i)
This NEEDS to start at 0 and not 1 because otherwise, "sz" would always be added to the start address of the array and the first element would ALWAYS be skipped. But in tables, this is not the case, because tables do not have a defined data type size, and this formula is never used. This is why actual arrays are incredibly performant no matter the size, and the larger a table gets, the slower it is.
That felt good to get off my chest. Yes, Lua could start the auto-key at 0, but that might confuse people into thinking tables are arrays... well, I guess there's no avoiding that either way.13 -
follow on from my last rant.
I've finally gotten my new Jira project. Only thing I seem to have access to change is the Kanban board columns. Still has 50+ fields when creating a ticket etc.
Asked the support team handling the request if this was a mistake. He said no, i'll need to open another ticket to have those changes requested.
Opened and got a reply. Currently there are 2 versions of Jira running. They are working on consolidating them atm and won't help me right now until this is done. I've been asked to re-open my request after the consolidation is done in March 2019.
5 ... fucking ... months, so I can have a competent ticketing process.
He pointed me to a page explaining the move and listing all the changes taking place. Well lets look at the changes they are making that are so critical:
Change 14: Rename "More info" status to "Needs more info".
... Oh pardon me. I didn't realise such critical show stoppers were being addressed. Please do continue. Don't mind me, i'll just be over here taking 4 hours to create an Epic and 6 stories. As you were9 -
Apple at its finest. Sold the iPhone I used to own. Wanted to remove from iCloud. Open chrome on my Android device and was greeted with unsupported browser. Funny thing is it works if I tick open as desktop website.
Ffs apple. Your safari browser is the new IE of browsers. Yes my device is supported. Yes for Christ sake it can render stuff. It's not an old Nokia... Who even thought it was remotely a good idea to restrict mobile access... 5
5 -
It were around 1997~1998, I was on middle school. It was a technical course, so we had programing languages classes, IT etc.
The IT guy of our computer lab had been replaced and the new one had blocked completely the access on the computers. We had to make everything on floppy disks, because he didn't trusted us to use the local hard disk. Our class asked him to remove some of the restrictions, but he just ignored us. Nobody liked that guy. Not us, not the teachers, not the trainees at the lab.
Someday a friend and me arrived a little bit early at the school. We gone to the lab and another friend that was a trainee on the lab (that is registered here, on DevRant) allowed us to come inside. We had already memorized all the commands. We crawled in the dark lab to the server. Put a ms dos 5.3 boot disk with a program to open ntfs partitions and without turn on the computer monitor, we booted the server.
At that time, Windows stored all passwords in an encrypted file. We knew the exact path and copied the file into the floppy disk.
To avoid any problems with the floppy disk, we asked the director of the school to get out just to get a homework we theorically forgot at our friends house that was on the same block at school. We were not lying at all. He really lived there and he had the best computer of us.
The decrypt program stayed running for one week until it finds the password we did want: the root.
We came back to the lab at the class. Logged in with the root account. We just created another account with a generic name but the same privileges as root. First, we looked for any hidden backup at network and deleted. Second, we were lucky: all the computers of the school were on the same network. If you were the admin, you could connect anywhere. So we connected to a "finance" computer that was really the finances and we could get lists of all the students with debits, who had any discount etc. We copied it to us case we were discovered and had to use anything to bargain.
Now the fun part: we removed the privileges of all accounts that were higher than the trainee accounts. They had no access to hard disks anymore. They had just the students privileges now.
After that, we changed the root password. Neither we knew it. And last, but not least, we changed the students login, giving them trainee privileges.
We just deleted our account with root powers, logged in as student and pretended everything was normal.
End of class, we went home. Next day, the lab was closed. The entire school (that was school, mid school and college at the same place) was frozen. Classes were normal, but nothing more worked. Library, finances, labs, nothing. They had no access anymore.
We celebrated it as it were new years eve. One of our teachers came to us saying congratulations, as he knew it had been us. We answered with a "I don't know what are you talking about". He laughed and gone to his class.
We really have fun remembering this "adventure". :)
PS: the admin formatted all the servers to fix the mess. They had plenty of servers.4 -
Don't cha just love it when you download your "native" desktop application to host a meeting, only to find out its actually a wrapper around a browser?
How did I find out? Well I innocently tried to drag and drop an image to share, only to have the browser open and render that file instead of uploading it, killing the application it was running behind it, closing the meeting for everyone on it ... and not even be able to access a back button to re-open the session.
viva la hybrid!2 -
The gift that keeps on giving... the Custom CMS Of Doom™
I've finally seen enough evidence why PHP has such a bad reputation to the point where even recruiters recommended me to remove my years of PHP experience from the CV.
The completely custom CMS written by company <redacted>'s CEO and his slaves features the following:
- Open for SQL injection attacks
- Remote shell command execution through URL query params
- Page-specific strings in most core PHP files
- Constructors containing hundreds of lines of code (mostly used to initialize the hundreds of properties
- Class methods containing more than 1000 lines of code
- Completely free of namespaces or package managers (uber elite programmers use only the root namespace)
- Random includes in any place imaginable
- Methods containing 1 line: the include of the file which contains the method body
- SQL queries in literally every source file
- The entrypoint script is in the webroot folder where all the code resides
- Access to sensitive folders is "restricted" by robots.txt 🤣🤣🤣🤣
- The CMS has its own crawler which runs by CRONjob and requests ALL HTML links (yes, full content, including videos!) to fill a database of keywords (I found out because the server traffic was >500 GB/month for this small website)
- Hundreds of config settings are literally defined by "define(...)"
- LESS is transpiled into CSS by PHP on requests
- .......
I could go on, but yes, I've seen it all now.12 -
Worst WTF dev experience? The login process from hell to a well-fortified dev environment at a client's site.
I assume a noob admin found a list of security tips and just went like "all of the above!".
You boot a Linux VM, necessary to connect to their VPN. Why necessary? Because 1) their VPN is so restrictive it has no internet access 2) the VPN connection prevents *your local PC* from accessing the internet as well. Coworkers have been seen bringing in their private laptops just to be able to google stuff.
So you connect via Cisco AnyConnect proprietary bullshit. A standard VPN client won't work. Their system sends you a one-time key via SMS as your password.
Once on their VPN, you start a remote desktop session to their internal "hopping server", which is a Windows server. After logging in with your Windows user credentials, you start a Windows Remote Desktop session *on that hopping server* to *another* Windows server, where you login with yet another set of Windows user credentials. For all these logins you have 30 seconds, otherwise back to step 1.
On that server you open a browser to access their JIRA, GitLab, etc or SSH into the actual dev machines - which AGAIN need yet another set of credentials.
So in total: VM -> VPN + RDP inside VM -> RDP #2 -> Browser/SSH/... -> Final system to work on
Input lag of one to multiple seconds. It was fucking unusable.
Now, the servers were very disconnect-happy to prevent anything "fishy" going on. Sitting at my desk at my company, connected to my company's wifi, was apparently fishy enough to kick me out every 5 to 20 minutes. And that meant starting from step 1 inside the VM again. So, never forget to plugin your network cable.
There's a special place in hell for this admin. And if there isn't, I'll PERSONALLY make the devil create one. Even now that I'm not even working on this any more.8 -
Years ago, when i was a teenager (13,14 or smth) and internet at home was a very uncommon thing, there was that places where ppl can play lan games, have a beer (or coke) and have fun (spacenet internet cafe). It was like 1€ per hour to get a pc. Os was win98, if you just cancel the boot progress (reset button) to get an error boot menu, and then into the dos mode "edit c:/windows/win.ini" and remove theyr client startup setting from there, than u could use the pc for free. How much hours we spend there...
The more fun thing where the open network config, without the client running i could access all computers c drives (they was just shared i think so admin have it easy) was fun to locate the counter strike 1.6 control settings of other players. And bind the w key to "kill"... Round begins and you hear alot ppl raging. I could even acess the server settings of unreal tournament and fck up the gravity and such things. Good old time, the only game i played fair was broodwar and d3 lod5 -
"God Mode" in Windows 10:
1. Create a new folder on your desktop. Leave its name to be "New Folder"
2. Open CMD with administrator privileges
3. cd C:\Users\<your username>\Desktop
4. ren "New folder" ".{ED7BA470-8E54-465E-825C-99712043E01C}"
Enjoy direct access to all and every settings. :-)16 -
Internal support article to get access to a tool:
"To get access click 'NO' in the 'was this article helpful section' and open a support ticket, making sure to mention the tool you are looking to get access to"
What fucking fresh hell is this? Why not have the article, contain the fucking link to open the ticket.
You have intentionally put up a useless article, in order to hack your way around this stupid system.2 -
Worst code review experience?
Hard to pick just one, but most were in a big meeting room with 4+ other developers not related to the project and with some playing Monday-Morning-Quarterback instead of offering productive feedback.
In one code review, the department mgr reviewed the code from a third party component library.
<brings up the code on the big screen>
Mgr: "I can't read any of this, its a mix of English and something else."
Me: "Its German."
Mgr: "Then why is 'Button' in English? This code is a mess."
Me: "I'm not exactly sure how I should respond, I mean, I didn't write any of this code."
Mgr: "Yes, but you are using it, so it's fair game for a code review."
Me: "Its not really open source, but we can make requests if you found something that needs to be addressed."
Mgr: "Oh yes, all this...whatever this is..<pointing again to the German>"
Me: "I don't think they will change their code to English just so you can read it."
Mgr: "We paid good money, you bet your ass they'll change it!"
Me: "I think the components were like $30 for the unlimited license. They'll tell us to go to hell first. Is there something about my code you want to talk about?"
Mgr: "<Ugggh>...I guess not, I couldn't get past all that German. Why didn't we go with an American company? Hell, why didn't we just write these components ourselves!?"
Me: "Because you gave a directive that if we found components that saved us time, to put in a request, and you approved the request. The company is American, they probably outsourced or hired German developers. I don't know and not sure why we care."
Mgr: "Security! What if they are sending keystrokes back to their servers!"
Me: "Did you see any http or any network access?"
Mgr: "How could I? The code is in German!"
Monday-Morning-Quarterback1: "If it were me, I would have written the components myself and moved on"
Me: "No, I don't think you could for less than $30"
Monday-Morning-Quarterback2: "Meh...we get paid anyway. Just add the time to the estimate."
Mgr: "Exactly! Why do we even have developers who can't read this mess."
Me: "Oh good Lord! Did anyone review or even look at my code for this review!?"
<silence>
Mgr: "Oh...ok...I guess we're done here. Thanks everyone."
<everyone starts to leave>
Me: "Whoa!...wait a sec..am I supposed to do something?"
Mgr: "Get that company to write their code in English so we can read it. You have their number, call em'...no...wait...give me their number. You keep working, I'll take care of this personally"
In they nicest way possible, the company did tell him to go to hell.17 -
This happened quite sometime ago.
I received a client, reputable university in my country. After all the paper work was done, I was emailed access to one of their AWS server, FTP where the username and password were both admin. I didn't say much to them at that moment.. Maybe they had some precautions?
Over night I received another email, around 3am,
"Hi Uzair, we've monitored a breach while leaving FTP access open."
Well, that was sorta expected.
I received SFTP access to the server the following day,
username: admin,
password: @dmin3 -
So I'm moving to a new/bigger place with faster Internet soon so I think it's time to rebuild my current home/remote server setup.
I want to setup the following things:
- vps for server monitoring (open source pushover alternative + netdata)
- Zero tier network for connecting all my servers to the same network
- pihole/pivpn (or the Angristan vpn installer, look it up :)
- second blocking thingy next to pihole to make sure that I literally can't access google/fb etc anymore, even if I really needed/wanted to
- bunch of general servers.
Any ideas?20 -
Not just another Windows rant:
*Disclaimer* : I'm a full time Linux user for dev work having switched from Windows a couple of years ago. Only open Windows for Photoshop (or games) or when I fuck up my Linux install (Arch user) because I get too adventurous (don't we all)
I have hated Windows 10 from day 1 for being a rebel. Automatic updates and generally so many bugs (specially the 100% disk usage on boot for idk how long) really sucked.
It's got ads now and it's generally much slower than probably a Windows 8 install..
The pathetic memory management and the overall slower interface really ticks me off. I'm trying to work and get access to web services and all I get is hangups.
Chrome is my go-to browser for everything and the experience is sub par. We all know it gobbles up RAM but even more on Windows.
My Linux install on the same computer flies with a heavy project open in Android Studio, 25+ tabs in Chrome and a 1080p video playing in the background.
Up until the creators update, UI bugs were a common sight. Things would just stop working if you clicked them multiple times.
But you know what I'm tired of more?
The ignorant pricks who bash it for being Windows. This OS isn't bad. Sure it's not Linux or MacOS but it stands strong.
You are just bashing it because it's not developer friendly and it's not. It never advertises itself like that.
It's a full fledged OS for everyone. It's not dev friendly but you can make it as much as possible but you're lazy.
People do use Windows to code. If you don't know that, you're ignorant. They also make a living by using Windows all day. How bout tha?
But it tries to make you feel comfortable with the recent bash integration and the plethora of tools that Microsoft builds.
IIS may not be Apache or Nginx but it gets the job done.
Azure uses Windows and it's one of best web services out there. It's freaking amazing with dead simple docs to get up and running with a web app in 10 minutes.
I saw many rants against VS but you know it's one of the best IDEs out there and it runs the best on Windows (for me, at least).
I'm pissed at you - you blind hater you.
Research and appreciate the things good qualities in something instead of trying to be the cool but ignorant dev who codes with Linux/Mac but doesn't know shit about the advantages they offer.undefined windows 10 sucks visual studio unix macos ignorance mac terminal windows 10 linux developer22 -
I just got four CSV reports sent to me by our audit team, one of them zipped because it was too large to attach to email.
I open the three smaller ones and it turns out they copied all the (comma separated) data into the first column of an Excel document.
It gets better.
I unzip the "big" one. It's just a shortcut to the report, on a network share I don't have access to.
They zipped a shortcut.
Sigh. This'll be a fun exchange.3 -
What an absolute fucking disaster of a day. Strap in, folks; it's time for a bumpy ride!
I got a whole hour of work done today. The first hour of my morning because I went to work a bit early. Then people started complaining about Jenkins jobs failing on that one Jenkins server our team has been wanting to decom for two years but management won't let us force people to move to new servers. It's a single server with over four thousand projects, some of which run massive data processing jobs that last DAYS. The server was originally set up by people who have since quit, of course, and left it behind for my team to adopt with zero documentation.
Anyway, the 500GB disk is 100% full. The memory (all 64GB of it) is fully consumed by stuck jobs. We can't track down large old files to delete because du chokes on the workspace folder with thousands of subfolders with no Ram to spare. We decide to basically take a hacksaw to it, deleting the workspace for every job not currently in progress. This of course fucked up some really poorly-designed pipelines that relied on workspaces persisting between jobs, so we had to deal with complaints about that as well.
So we get the Jenkins server up and running again just in time for AWS to have a major incident affecting EC2 instance provisioning in our primary region. People keep bugging me to fix it, I keep telling them that it's Amazon's problem to solve, they wait a few minutes and ask me to fix it again. Emails flying back and forth until that was done.
Lunch time already. But the fun isn't over yet!
I get back to my desk to find out that new hires or people who got new Mac laptops recently can't even install our toolchain, because management has started handing out M1 Macs without telling us and all our tools are compiled solely for x86_64. That took some troubleshooting to even figure out what the problem was because the only error people got from homebrew was that the formula was empty when it clearly wasn't.
After figuring out that problem (but not fully solving it yet), one team starts complaining to us about a Github problem because we manage the github org. Except it's not a github problem and I already knew this because they are a Problem Team that uses some technical authoring software with Git integration but they only have even the barest understanding of what Git actually does. Turns out it's a Git problem. An update for Git was pushed out recently that patches a big bad vulnerability and the way it was patched causes problems because they're using Git wrong (multiple users accessing the same local repo on a samba share). It's a huge vulnerability so my entire conversation with them went sort of like:
"Please don't."
"We have to."
"Fine, here's a workaround, this will allow arbitrary code execution by anyone with physical or virtual access to this computer that you have sitting in an unlocked office somewhere."
"How do I run a Git command I don't use Git."
So that dealt with, I start taking a look at our toolchain, trying to figure out if I can easily just cross-compile it to arm64 for the M1 macbooks or if it will be a more involved fix. And I find all kinds of horrendous shit left behind by the people who wrote the tools that, naturally, they left for us to adopt when they quit over a year ago. I'm talking entire functions in a tool used by hundreds of people that were put in as a joke, poorly documented functions I am still trying to puzzle out, and exactly zero comments in the code and abbreviated function names like "gars", "snh", and "jgajawwawstai".
While I'm looking into that, the person from our team who is responsible for incident communication finally gets the AWS EC2 provisioning issue reported to IT Operations, who sent out an alert to affected users that should have gone out hours earlier.
Meanwhile, according to the health dashboard in AWS, the issue had already been resolved three hours before the communication went out and the ticket remains open at this moment, as far as I know.5 -
One of our newly-joined junior sysadmin left a pre-production server SSH session open. Being the responsible senior (pun intended) to teach them the value of security of production (or near production, for that matter) systems, I typed in sudo rm --recursive --no-preserve-root --force / on the terminal session (I didn't hit the Enter / Return key) and left it there. The person took longer to return and the screen went to sleep. I went back to my desk and took a backup image of the machine just in case the unexpected happened.
On returning from wherever they had gone, the person hits enter / return to wake the system (they didn't even have a password-on-wake policy set up on the machine). The SSH session was stil there, the machine accepted the command and started working. This person didn't even look at the session and just navigated away elsewhere (probably to get back to work on the script they were working on).
Five minutes passes by, I get the first monitoring alert saying the server is not responding. I hoped that this person would be responsible enough to check the monitoring alerts since they had a SSH session on the machine.
Seven minutes : other dependent services on the machine start complaining that the instance is unreachable.
I assign the monitoring alert to the person of the day. They come running to me saying that they can't reach the instance but the instance is listed on the inventory list. I ask them to show me the specific terminal that ran the rm -rf command. They get the beautiful realization of the day. They freak the hell out to the point that they ask me, "Am I fired?". I reply, "You should probably ask your manager".
Lesson learnt the hard-way. I gave them a good understanding on what happened and explained the implications on what would have happened had this exact same scenario happened outside the office giving access to an outsider. I explained about why people in _our_ domain should care about security above all else.
There was a good 30+ minute downtime of the instance before I admitted that I had a backup and restored it (after the whole lecture). It wasn't critical since the environment was not user-facing and didn't have any critical data.
Since then we've been at this together - warning engineers when they leave their machines open and taking security lecture / sessions / workshops for new recruits (anyone who joins engineering).26 -
I think I've got a working searx instance which I'd open up for the public.
NOTE: I cannot prove that I don't store anything because for that you'd need root access to the server which I won't give obviously. If you're not comfortable with that, just don't uses it.
I still have to do something for ip address logging anonymising or stripping, though. (nginx + CSF provided enough abuse prevention).
Tips on that?29 -
I wrote in a rant here that I couldn't access my 1TB external hard-drive anymore because I refused to "Safely remove" it from my computer.
My brother sent me today an image with it, showing me that he managed to open it.
I can't tell you how happy I am!
The solution: if you encounter the same problem (it takes forever for windows to scan it and you can't open it/ on linux it tells you to go to windows and and properly eject it), just go to `Device Manager` and `Scan for new hardware`. This should find it & solve it3 -
I bought Minecraft back in 2007 or 8. It was $20 and gave me access to Minecraft forever, all updates included.
Today Microsoft closed all the old mojang accounts and I no longer have access to Minecraft. I could have migrated to a Microsoft account, but it will be a cold day in hell if I ever open one of those.
Sounds like law suit material. Class action anyone?11 -
I’ve started the process of setting up the new network at work. We got a 1Gbit fibre connection.
Plan was simple, move all cables from old switch to new switch. I wish it was that easy.
The imbecile of an IT Guy at work has setup everything so complex and unnecessary stupid that I’m baffled.
We got 5 older MacPros, all running MacOS Server, but they only have one service running on them.
Then we got 2x xserve raid where there’s mounted some external NAS enclosures and another mac. Both xserve raid has to be running and connected to the main macpro who’s combining all this to a few different volumes.
Everything got a static public IP (we got a /24 block), even the workstations. Only thing that doesn’t get one ip pr machine is the guest network.
The firewall is basically set to have all ports open, allowing for easy sniffing of what services we’re running.
The “dmz” is just a /29 of our ip range, no firewall rules so the servers in the dmz can access everything in our network.
Back to the xserve, it’s accessible from the outside so employees can work from home, even though no one does it. I asked our IT guy why he hadn’t setup a VPN, his explanation was first that he didn’t manage to set it up, then he said vpn is something hackers use to hide who they are.
I’m baffled by this imbecile of an IT guy, one problem is he only works there 25% of the time because of some health issues. So when one of the NAS enclosures didn’t mount after a power outage, he wasn’t at work, and took the whole day to reply to my messages about logins to the xserve.
I can’t wait till I get my order from fs.com with new patching equipment and tonnes of cables, and once I can merge all storage devices into one large SAN. It’ll be such a good work experience.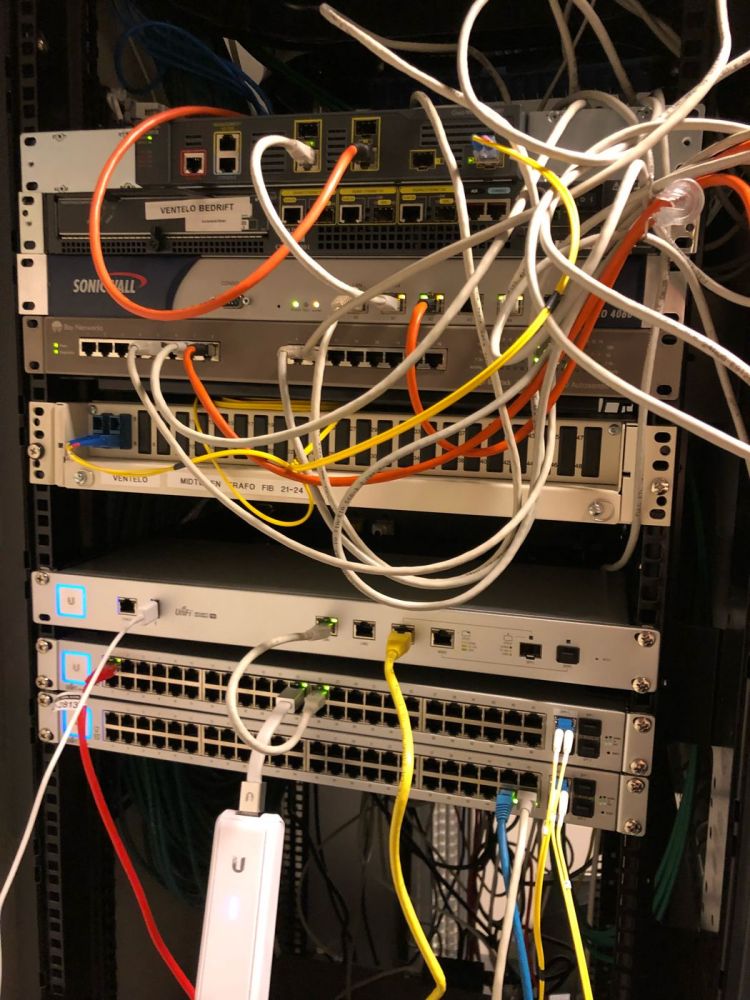 7
7 -
So just finished the presentation for my internship project. I'm free now!(and can sleep normal times too) But I have a few things I need to get off my mind. Dunno if it'll seem a bit stupid to some of you..but yeahh....
Anyway, during my demo yesterday
Lecturer: So this project of yours uses some open-source stuff?
Me: Yeah.
L: And if the company wants to use if for commercialization they need to pay for the license?
M: Thats basically it. Yes.
L: Well, see..thats the problem with your project. You need to think of all this things. If there's no other options then just code the whole shit yourself. Or maybe discuss with the management on this.
Yeah...see, I doubt the management here cares about us anyway. Oh, you're working on your intern stuff. Not important. Just resize the pictures in my powerpoint will you? Oh and you want to use the company computers for your project? No can do..confidentiality stuff. But make sure the thing will work on our system anyway when you're done with it. And even if you use our computers, they restart everytime you open Word anyway..hahaha. You want access to this thing so you can learn a bit on our company's work. Sorry but no. EVERYTHING is confidential so you can't access it since you're interns, eventhough our company is the one that took you inanyway.
Manager: Oh, the thing you're making is pretty cool. You know,all of you can just give your systems to us later.
Friend: Yeah well, maybe we can ask the company for payment? Haha.
Manager: Hahaha well the company can just take your systems for free since you're doing it on our working hours.
Fuck. You. When we ask to do our stuff you said noooo its the company hours. Do our work. And do your stuff back at home or something. Oh, but then we'll drag you around the state to see the clients, and you'll reach home at 8-9pm or something, but of course you're not tired right? So just code then. Or you're not going anywhere today? You're still not allowed to code here eventhough you don't have any work though...so just sit there and be quiet. Or maybe shred my papers for me. Fuck your working hours.
Lecturer: And well, thats the problem with some students *looks pointedly at me* they want to go to non-technical companies so that they can have it easy. Your friends who go to other companies will learn a lot more.
Do you think I fucking want to be here??? This is the only company I got so fuck that. Even when I get different offers and apply to change companies, you go nope. No can do. Stick with your current company eventhough we know that its shit for IT students because its a big company, see? And we have our university's reputation to upkeep. I came here to learn, not make you the No.1 university or something. And its not like you, or the staffs here, help us with anything.
So fuck all of this. We're gonna tell the other lecturers to stop sending students here. You don't learn anything. I'm done with this shit, not gonna think or worry about it anymore..I'll just, go get cake or something. Yeah.3 -
Junior dev requests for sudo access on a server instance for some package installation, gets it, figures out how to open the root shell - never goes back. They do everything on root.
Fast forward to production deployment time, their application won't run without elevated privileges. Sysadmin asks why does the application require elevated privileges. Dev answers, "Because I set it up with root" :facepalm:15 -
@netikras since when does proprietary mean bad?
Lemme tell you 3 stories.
CISCO AnyConnect:
- come in to the office
- use internal resources (company newsletter, jira, etc.)
- connect to client's VPN using Cisco AnyConnect
- lose access to my company resources, because AnyConnect overwrites routing table (rather normal for VPN clients)
- issue a route command updating routing table so you could reach confluence page in the intranet
- route command executes successfully, `route -n` shows nothing has changed
- google this whole WTF case
- Cisco AnyConnect constantly overwrites OS routing table to ENFORCE you to use VPN settings and nothing else.
Sooo basically if you want to check your company's email, you have to disconnect from client's VPN, check email and reconnect again. Neat!
Can be easily resolved by using opensource VPN client -- openconnect
CISCO AnyConnect:
- get a server in your company
- connect it to client's VPN and keep the VPN running for data sync. VPN has to be UP at all times
- network glitch [uh-oh]
- VPN is no longer working, AnyConnect still believes everything is peachy. No reconnect attempts.
- service is unable to sync data w/ client's systems. Data gets outdated and eventually corrupted
OpenConnect (OSS alternative to AnyConnect) detects all network glitches, reports them to the log and attempts reconnect immediatelly. Subsequent reconnect attempts getting triggered with longer delays to not to spam network.
SYMANTEC VIP (alleged 2FA?):
- client's portal requires Sym VIP otp code to log in
- open up a browser in your laptop
- navigate to the portal
- enter your credentials
- click on a Sym VIP icon in the systray
- write down the shown otp number
- log in
umm... in what fucking way is that a secure 2FA? Everything is IN the same fucking device, a single click away.
Can be easily solved by opensource alternatives to Sym VIP app: they make HTTP calls to Symantec to register a new token and return you the whole totp url. You can convert that url to a qr code and scan it w/ your phone (e.g. Google's Authenticator). Now you have a true 2FA.
Proprietary is not always bad. There are good propr sw too. But the ones that are core to your BAU and are doing shit -- well these ARE bad. and w/o an oppurtunity to workaround/fix it yourself.13 -
TLDR: Small family owned finance business woes as the “you-do-everything-now” network/sysadmin intern
Friday my boss, who is currently traveling in Vegas (hmmm), sends me an email asking me to punch a hole in our firewall so he can access our locally hosted Jira server that we use for time logging/task management.
Because of our lack of proper documentation I have to refer to my half completed network map and rely on some acrobatic cable tracing to discover that we use a SonicWall physical firewall. I then realize asking around that I don’t have access to the management interface because no one knows the password.
Using some lucky guesses and documentation I discover on a file share from four years ago, I piece together the username and password to log in only to discover that the enterprise support subscription is two years expired. The pretty and useful interface that I’m expecting has been deactivated and instead of a nice overview of firewall access rules the only thing I can access is an arcane table of network rules using abbreviated notation and five year old custom made objects representing our internal network.
An hour and a half later I have a solid understanding of SonicWallOS, its firewall rules, and our particular configuration and I’m able to direct external traffic from the right port to our internal server running Jira. I even configure a HIDS on the Jira server and throw up an iptables firewall quickly since the machine is now connected to the outside world.
After seeing how many access rules our firewall has, as a precaution I decide to run a quick nmap scan to see what our network looks like to an attacker.
The output doesn’t stop scrolling for a minute. Final count we have 38 ports wide open with a GOLDMINE of information from every web, DNS, and public server flooding my terminal. Our local domain controller has ports directly connected to the Internet. Several un-updated Windows Server 2008 machines with confidential business information have IIS 7.0 running connected directly to the internet (versions with confirmed remote code execution vulnerabilities). I’ve got my work cut out for me.
It looks like someone’s idea of allowing remote access to the office at some point was “port forward everything” instead of setting up a VPN. I learn the owners close personal friend did all their IT until 4 years ago, when the professional documentation stops. He retired and they’ve only invested in low cost students (like me!) to fill the gap. Some kid who port forwarded his home router for League at some point was like “let’s do that with production servers!”
At this point my boss emails me to see what I’ve done. I spit him back a link to use our Jira server. He sends me a reply “You haven’t logged any work in Jira, what have you been doing?”
Facepalm.4 -
Why the absolute fuck do I need to have nvidia membership to download cudnn? What evil do these mofos think people achieve with free access to a fucking programming tool?
Jesus on a bike! I nag about open science and all I end up with is always these spying morons, who purposefully disable scientists. Fuck!
If👏you👏need👏my👏info,👏then it's👏not👏free.👏15 -
Joined a new company / team to work on an iOS app that has 2 different backend environments "Dev" and "Prod". Also being referred to in iOS speak as "Debug" and "Release".
Been trying to get accounts on these backends (no sign up in app, its controlled via another process). Eventually get access to "Dev" for one of the regions, so I load up "Debug" and its not working.
This is odd, so I open the Android app and load "Dev" and it works? I then Notice Android has "Dev", "QA", "Staging" and "Prod" for every region where as iOS only has 2 of these.
So I go back to iOS and find the file for the settings and it has iOS Debug assigned a variable for the backend Dev ... which is actually pointing to QA. Because they use QA to Debug and not Dev.
... confused? join the club3 -
I need a new 'main' language to do all my projects in as java is kind of grinding away at my psyche.
Golang I liked quite a lot when I used it for my job a year ago, I'll give that a try..
Golang installed and up and working fine.
Oh, I know lets see if there are GLFW bindings for golang. And sure there are lets go!
Oh I need gcc and mingwex + mingw32 which I will acquire through cygwin.
hmm.. mingwex + mingw32 not found and my drive is almost full. I'll reinstall on my D:\ drive before continuing troubleshooting.
> Delete C:\Cygwin Access denied.
> cmd rmdir c:\test /s /q Access denied.
> Change permissions Access denied.
No problem I just don't own this object!
> Change to be the 'object owner' Success!
> Change permissions Success!
> Delete C:\Cygwin Access denied.
> cmd rmdir c:\test /s /q Access denied.
> takeown /F C:\Cygwin /A /R /D Y Success!
> cmd rmdir c:\test /s /q Access denied.
At this point it would be more efficient to manually open up my ssd, and using a fridge magnet change every single bit to be exactly what I want it to be.
Or install linux. 7
7 -
This is something I'll never forget.
I'm a senior UI engineer. I was working at a digital agency at the time and got tasked with refactoring and improving an existing interface from a well known delivery company.
I open the code and what do I find? Indentation. But not in the normal sense. The indentation only went forward, randomly returning a bunch of tabs back in the middle of the file a few times, but never returning to its initial level after closing a tag or function, both on HTML and JS.
Let that sink in for a minute and try to imagine what it does to your editor with word wrapping (1 letter columns), and without (absurd horizontal scrolling).
Using Sublime at the time, ctrl+shift+P, reindent. Everything magically falls beautifully into place. Refactor the application, clean up the code, document it, package it and send it back (zip files as they didn't want to provide version control access, yay).
The next day, we get a very angry call from the client saying that their team is completely lost. I prove to the project manager that my code is up to scratch, running fine, no errors, tested, good performance. He returns to the client and proves that it's all correct (good PM with decent tech knowledge).
The client responds with "Yeah, the code is running, but our team uses tabs for version control and now we lost all versioning!".
Bear in mind this was in 2012, git was around for 7 years then, and SVN and Mercury much longer.
I then finally understood the randomness of the tabs. The code would go a bunch of tabs back when it went back to a previous version, everything above were additions or modifications that joined seamlessly with the previous version before, with no way to know when and so on.
I immediately told the PM that was absurd, he agreed, and told the client we wouldn't be reindenting everything back for them according to the original file.
All in all, it wasn't a bad experience due to a competent PM, but it left a bad taste in my mouth to know companies have teams that are that incompetent, and that no one thought to stop and say "hey, this may cause issues down the line".4 -
I was supporting a legacy CRM app which front end used Visual Basic 6 and almost the entire business logic was written on SQL store procedures.
A "feature" of the product was the open code, anyone with admin access could modify forms, code and store procedures.
We also sold "official" (and expensive) consulting services to modify the code.
A long time customer owned this thing and it was heavily customized. They had hired us to change something, hired a third party to make other changes and decided to modify some stuff themselves because, why not?
Suddenly they came to product support asking to fix a bug. The problem happened on a non customized form.
After reviewing, I realized the form used several of the modified store procedures in the business layer. I tried saying we don't support custom code but my boss was being pushed and said "look into it"
All 3 parties denied responsibility and said their changes were NOT the problem (of course). Neither of them commented or documented their changes.
The customer started to threaten to sue us.
I spent 5 full days following every field on the form through the nested and recurrent SQL store procedures and turns out it was a very simple error. A failed insert statement.
I was puzzled of why the thing didn't throw any error even while debugging. Turns out in SQL 2003 (this was a while ago) someone used a print line statement and SQL stopped throwing errors to the console. I can only assume "printing" in SQL empties the buffered error which would be shown in the console.
I removed the print statement and the error showed up, we fixed it and didn't get sued
:)4 -
Got pretty peeved with EU and my own bank today.
My bank was loudly advertising how "progressive" they were by having an Open API!
Well, it just so happened I got an inkling to write me a small app that would make statistics of the payments going in and out of my account, without relying on anything third-party. It should be possible, right? Right?
Wrong...
The bank's "Open API" can be used to fetch the locations of all the physical locations of the bank branches and ATMs, so, completely useless for me.
The API I was after was one apparently made obligatory (don't quote me on that) by EU called the PSD2 - Payment Services Directive 2.
It defines three independent APIs - AISP, CISP and PISP, each for a different set of actions one could perform.
I was only after AISP, or the Account Information Service Provider. It provides all the account and transactions information.
There was only one issue. I needed a client SSL certificate signed by a specific local CA to prove my identity to the API.
Okay, I could get that, it would cost like.. $15 - $50, but whatever. Cheap.
First issue - These certificates for the PSD2 are only issued to legal entities.
That was my first source of hate for politicians.
Then... As a cherry on top, I found out I'd also need a certification from the local capital bank which, you guessed it, is also only given to legal entities, while also being incredibly hard to get in and of itself, and so far, only one company in my country got it.
So here I am, reading through the documentation of something, that would completely satisfy all my needs, yet that is locked behind a stupid legal wall because politicians and laws gotta keep the technology back. And I can't help but seethe in anger towards both, the EU that made this regulation, and the fact that the bank even mentions this API anywhere.
Seriously, if 99.9% of programmers would never ever get access to that API, why bother mentioning it on your public main API page?!
It... It made me sad more than anything...6 -
Our prof told us today in a zoom lecture: "Never visit b-ok.org, it is totally illegal", with emphasis on how he would NEVER recommend to visit that website for free education illegally.
I guess he is totally against the idea of pirating educational material12 -
!dev
And again...
Our ISP doesn’t say it blocks any port on our Business Fixed IP. Currently I’m trying to access port 25 for SMTP. Guess what? Indeed port blocked. Called them “The port is open”, I visit a port checked, the same thing “Port Closed”
Always the fucking same thing. Every fcking time. These are just criminals. Lastly I removed their router, that they mentions was the only working router in our house and our signal from the other router, not provided by them was much better. They blocked the hotspots because we removed the router then. Guess what? On their site is an option Enable Hotspot on your home router (this enables your access to hotspots). Just pressed it. Haaa they can’t acces my router to set that up and it works.
In our second home, we have another ISP, Proximus, first they did difficult to come and install everything. Because in the appartment the previous owners didn’t pay the bills. After a week or so someone came to install it. Because they cut the cables couldn’t do it myself. Ok it worked for some time. After 3-4 months by once I can’t access the camera there, strange. My uncle went there and there was no internet. Neither TV. But we never received any invoice. Because they didn’t send them. We contacted them, no response. My father sends them an email, with politic people in copy and by once they called to say they will turn it back and scrap the invoices that were not send. They said no technician needed to come, as it’s second home. Guess what, next day a message came “We will arrive in less than an hour”
My uncle went. They did nothing, only restart the modem.
There still was no internet after two days after they came. We called back, response was: “There wasn’t anyone.” Yeah right, we have proof of a technicial that passed (Local Video). By once the internet worked.
Now 4 months later, still didn’t receive any invoice, neither via post or email.
Fuck those criminals, called ISPs 19
19 -
Saturday. It's already an evening. Kid is asleep. Wife is doing her thing in another room. I'm on my own, I now have time do do whatever I want! So a personal project time it is!
Open up a lappy, wake up my Mint. Switch to a workspace with IntelliJ ide. There's some message popped up on a screen. With a red cross. Read the message -- your licence has expired.
Shit.
Open up chrome, go to jetbrains website, log in, purchase an all-in licence page, filling in the form, last check before confirm... Wait, that ain't right. That's my college email I no longer have access to! Phew, it's a good thing I checked before submitting!
Go to account settings, update my email address, go back to licence purchase form, fill it all in, last check, and...
Wait..
Email hasn't changed. What if they send something valuable to my mailbox upon lic purchase? I can't risk, it's 200€ after all...
Oh come on! Open a support ticket. But it's Saturday so I don't think I'll get a response until Monday :(
and there goes ruined a perfect evening for some coding :(
shit...5 -
Never mess with a motivated developer. I will make your life difficult in return.
Me: we need server logs and stats daily for analysis
DBA: to get those, you need to open a ticket
Me: can't you just give me SFTP access and permissions to query the stats from the DB?
DBA: No.
*OK.... 🤔🤔🤔*
*Writes an Excel Template file that I basically just need to copy and paste from to create a ticket*
This process should not take me more than 2mins 👍😁😋🙂😙😙😙😙😙😙😙😙
For them.... 😈😈😈😈😈😈😈😈😈😈😈9 -
In the before time (late 90s) I worked for a company that worked for a company that worked for a company that provided software engineering services for NRC regulatory compliance. Fallout radius simulation, security access and checks, operational reporting, that sort of thing. Given that, I spent a lot of time around/at/in nuclear reactors.
One day, we're working on this system that uses RFID (before it was cool) and various physical sensors to do a few things, one of which is to determine if people exist at the intersection of hazardous particles, gasses, etc.
This also happens to be a system which, at that moment, is reporting hazardous conditions and people at the top of the outer containment shell. We know this is probably a red herring or faulty sensor because no one is present in the system vs the access logs and cameras, but we have to check anyways. A few building engineers climb the ladders up there and find that nothing is really visibly wrong and we have an all clear. They did not however know how to check the sensor.
Enter me, the only person from our firm on site that day. So in the next few minutes I am also in a monkey suit (bc protocol), climbing a 150 foot ladder that leads to another 150 foot ladder, all 110lbs of me + a 30lb diag "laptop" slung over my shoulder by a strap. At the top, I walk about a quarter of the way out, open the casing on the sensor module and find that someone had hooked up the line feed, but not the activity connection wire so it was sending a false signal. I open the diag laptop, plug it into the unit, write a simple firmware extension to intermediate the condition, flash, reload. I verify the error has cleared and an appropriate message was sent to the diagnostic system over the radio, run through an error test cycle, radio again, close it up. Once I returned to the ground, sweating my ass off, I also send a not at all passive aggressive email letting the boss know that the next shift will need to push the update to the other 600 air-gapped, unidirectional sensors around the facility.11 -
So now I have to pay taxes because I'm employed. Fair enough, sounds reasonable.
Go to the government's diseased scrotum of a webapp to tramit some ID stuff and shit. All good. Then I go to the bank, so I can open an account, so that I can receive the money, so that I can pay the government.
What happens? The guy at the bank tells me he can't access my ID, so he can't open my account. Understandable. I go once again to the gonorrhea infected maggotsoup that is the government's mother fucking webapp. THEY BLOCKED MY ID.
Problem? I had to attach images of some documentation, they say the images are illegible. I try again with a clearer image, ten fucking times the resoulution.
Is that good enough? NOOOOOOOOOO0=00=======0===000 oo O O OO O O, I am the government, my sole purpose in life is to be a dick in your asshole.
So what do I do? I, calmly, grab the documentation, go to the nearest office, and politely explain the situation to the dude behind the counter. Surely, he can verify himself that my papers are in order, no?
NO. HE CANNOT.
IT CAN ONLY BE DONE THROUGH THE APP.
ARE YOU FUCKING KIDDING ME.
WE ARE DOOMED AS A SPECIES.
LISTEN TO ME, DEAR GOVERNMENT.
AND DEAR TAXMEN.
AND ASSOCIATED BUREAUCRATS.
PLEASE HEAR ME OUT.
IF YOU DON'T UNBLOCK MY ID, I CANNOT OPEN A BANK ACCOUNT.
IF I DO NOT HAVE A BANK ACCOUNT, I CANNOT RECEIVE ANY MONEY.
IF I CANNOT RECEIVE ANY MONEY, THEN I CANNOT PAY **YOU**.
SEE HOW THAT WORKS?
ITS OK.
JUST SUSPEND THE PAYMENT I OWE.
YOU KNOW, THE ONE THAT'S DUE IN A FEW DAYS??
OH RIGHT!
YOU'RE STILL ASKING ME FOR THAT MONEY.
SILLY ME.
I THOUGHT I MAY BE EXEMPT.
SINCE YOU YOURSELF HAVE FORBIDDEN ME FROM PAYING.
ARRHGHHGGHGHGHGHGH!!!!!!!!
YOU IRREDEEMABLY STUPID FUCK.10 -
Long rant ahead.. 5k characters pretty much completely used. So feel free to have another cup of coffee and have a seat 🙂
So.. a while back this flash drive was stolen from me, right. Well it turns out that other than me, the other guy in that incident also got to the police 😃
Now, let me explain the smiley face. At the time of the incident I was completely at fault. I had no real reason to throw a punch at this guy and my only "excuse" would be that I was drunk as fuck - I've never drank so much as I did that day. Needless to say, not a very good excuse and I don't treat it as such.
But that guy and whoever else it was that he was with, that was the guy (or at least part of the group that did) that stole that flash drive from me.
Context: https://devrant.com/rants/2049733 and https://devrant.com/rants/2088970
So that's great! I thought that I'd lost this flash drive and most importantly the data on it forever. But just this Friday evening as I was meeting with my friend to buy some illicit electronics (high voltage, low frequency arc generators if you catch my drift), a policeman came along and told me about that other guy filing a report as well, with apparently much of the blame now lying on his side due to him having punched me right into the hospital.
So I told the cop, well most of the blame is on me really, I shouldn't have started that fight to begin with, and for that matter not have drunk that much, yada yada yada.. anyway he walked away (good grief, as I was having that friend on visit to purchase those electronics at that exact time!) and he said that this case could just be classified then. Maybe just come along next week to the police office to file a proper explanation but maybe even that won't be needed.
So yeah, great. But for me there's more in it of course - that other guy knows more about that flash drive and the data on it that I care about. So I figured, let's go to the police office and arrange an appointment with this guy. And I got thinking about the technicalities for if I see that drive back and want to recover its data.
So I've got 2 phones, 1 rooted but reliant on the other one that's unrooted for a data connection to my home (because Android Q, and no bootable TWRP available for it yet). And theoretically a laptop that I can put Arch on it no problem but its display backlight is cooked. So if I want to bring that one I'd have to rely on a display from them. Good luck getting that done. No option. And then there's a flash drive that I can bake up with a portable Arch install that I can sideload from one of their machines but on that.. even more so - good luck getting that done. So my phones are my only option.
Just to be clear, the technical challenge is to read that flash drive and get as much data off of it as possible. The drive is 32GB large and has about 16GB used. So I'll need at least that much on whatever I decide to store a copy on, assuming unchanged contents (unlikely). My Nexus 6P with a VPN profile to connect to my home network has 32GB of storage. So theoretically I could use dd and pipe it to gzip to compress the zeroes. That'd give me a resulting file that's close to the actual usage on the flash drive in size. But just in case.. my OnePlus 6T has 256GB of storage but it's got no root access.. so I don't have block access to an attached flash drive from it. Worst case I'd have to open a WiFi hotspot to it and get an sshd going for the Nexus to connect to.
And there we have it! A large storage device, no root access, that nonetheless can make use of something else that doesn't have the storage but satisfies the other requirements.
And then we have things like parted to read out the partition table (and if unchanged, cryptsetup to read out LUKS). Now, I don't know if Termux has these and frankly I don't care. What I need for that is a chroot. But I can't just install Arch x86_64 on a flash drive and plug it into my phone. Linux Deploy to the rescue! 😁
It can make chrooted installations of common distributions on arm64, and it comes extremely close to actual Linux. With some Linux magic I could make that able to read the block device from Android and do all the required sorcery with it. Just a USB-C to 3x USB-A hub required (which I have), with the target flash drive and one to store my chroot on, connected to my Nexus. And fixed!
Let's see if I can get that flash drive back!
P.S.: if you're into electronics and worried about getting stuff like this stolen, customize it. I happen to know one particular property of that flash drive that I can use for verification, although it wasn't explicitly customized. But for instance in that flash drive there was a decorative LED. Those are current limited by a resistor. Factory default can be say 200 ohm - replace it with one with a higher value. That way you can without any doubt verify it to be yours. Along with other extra security additions, this is one of the things I'll be adding to my "keychain v2".10 -
I was asked to look into a site I haven't actively developed since about 3-4 years. It should be a simple side-gig.
I was told this site has been actively developed by the person who came after me, and this person had a few other people help out as well.
The most daunting task in my head was to go through their changes and see why stuff is broken (I was told functionality had been removed, things were changed for the worse, etc etc).
I ssh into the machine and it works. For SOME reason I still have access, which is a good thing since there's literally nobody to ask for access at the moment.
I cd into the project, do a git remote get-url origin to see if they've changed the repo location. Doesn't work. There is no origin. It's "upstream" now. Ok, no biggie. git remote get-url upstream. Repo is still there. Good.
Just to check, see if there's anything untracked with git status. Nothing. Good.
What was the last thing that was worked on? git log --all --decorate --oneline --graph. Wait... Something about the commit message seems familiar. git log. .... This is *my* last commit message. The hell?
I open the repo in the browser, login with some credentials my browser had saved (again, good because I have no clue about the password). Repo hasn't gotten a commit since mine. That can't be right.
Check branches. Oh....Like a dozen new branches. Lots of commits with text that is really not helpful at all. Looks like they were trying to set up a pipeline and testing it out over and over again.
A lot of other changes including the deletion of a database config and schema changes. 0 tests. Doesn't seem like these changes were ever in production.
...
At least I don't have to rack my head trying to understand someone else's code but.... I might just have to throw everything that was done into the garbage. I'm not gonna be the one to push all these changes I don't know about to prod and see what breaks and what doesn't break
.
I feel bad for whoever worked on the codebase after me, because all their changes are now just a waste of time and space that will never be used.3 -
Time to do a little bit of shaming:
I'm specialized in e-commerce applications, mostly based on Shopware, a german out-of-the-box online-shop. They essentially claim to be a better Magento. In December of last year I found a critical issue within the code. Products within the shop can be declared as digital wares. In that case the purchase of a product will unlock the possibility to download a designated file.
As a customer you can access your downloads within the account section. Now here's the problem: The query that fetches the unlocked downloads for a customer is hard-capped at 500 rows. So after your 500th purchase, you won't be able to access any further files you paid for. Essentially their developers thought that this limit would never be exceeded anyway and called it a day.
Personally I think this unacceptable. For the merchant this is a potential law-suit in the making. So I took the time to refactor the code and fix the issue. The corresponding pull-request was flagged as scheduled back in December. Since then there have been numerous releases and the issue is still present. Not only do I ask myself why I should ever put in time and effort to fix their code again, but I also can't believe that they just chose to ignore the issue completely. Also mind that this is not just a small or non-profit open-source project. The responsible company behind the software is a stock corporation that claims to be the market leader in Germany. 5
5 -
Got a few Jira tickets reassigned to me because the dev who was supposed to work on them got stuck on another project. It's fine, that happens.
I open the tickets. No descriptions for all of them. No screenshots for those reported as bugs, nor any replication steps. No attached test cases or, well, ANY useful information.
I talk to our BA, he says that all information I need are in OTHER tickets on ANOTHER BOARD that business manages but I DON'T HAVE ACCESS TO. Honestly, these shitfucks could've just done simple copy/paste. But nooooo...
So I reassign all the tickets back to their original reporters (business testers) with comments requesting more information.
It's been a week. Now I have no idea what to put in my time sheet.1 -
I’m LOLing at the audacity of one of our vendors.
We contract with a vendor to build and maintain a website. Our network security team noticed there was a security breach of the vendor’s website. Our team saw that malicious users gained access to our Google Search console by completing a challenge that was issued to the vendor’s site.
At first, the vendor tried to convince us that their site wasn’t comprised and it was the Google search Console that was compromised. Nah dude. Our Search Console got compromised via the website you maintain for us. Luckily our network team was able to remove the malicious users from our search console.
That vendor site accepts credit card payments and displays the user’s contact info like address, email, and phone. The vendor uses keys that are tied to our payment gateway. So now my employer is demanding a full incident report from the vendor because their dropping the ball could have compromised our users’ data and we might be responsible for PCI issues.
And the vendor tried to shit on us even more. The vendor also generates vanity urls for our users. My employer decided to temporarily redirect users to our main site (non vendor) because users already received those links and in order to not lose revenue. The vendor’s solution is to build a service that will redirect their vanity urls to our main site. And they wanted to charge us $5000 usd for this. We already pay them $1000 a month already.
WTAF we are not stupid. Our network service team said we could make the argument that they do this without extra charge because it falls in the scope of our contract with them. Our network team also said that we could terminate the contract because the security breach means they didn’t render the service they were contracted to do. Guess it’s time for us to get our lawyer’s take on this.
So now it looks like my stakeholders want me to rebuild all of this in house. I already have a lot on my plate, but I’m going to be open to their requests because we are still in the debrief phase.2 -
sometimes our application users can't login to our application and they report the problem to us. The fucking problem? Almost sure they forgot the password because we can login with their account.. Yeah we should not have access to their password, but we do xD. The worst is they send a Word file with only a print screen of the application error saying they can't login. Why not a .jpg??! The word takes 4 seconds to open
 13
13 -
If you can be locked out of it remotely, you don't own it.
On May 3rd, 2019, the Microsoft-resembling extension signature system of Mozilla malfunctioned, which locked out all Firefox users out of their browsing extensions for that day, without an override option. Obviously, it is claimed to be "for our own protection". Pretext-o-meter over 9000!
BMW has locked heated seats, a physical interior feature of their vehicles, behind a subscription wall. This both means one has to routinely spend time and effort renewing it, and it can be terminated remotely. Even if BMW promises never to do it, it is a technical possibility. You are in effect a tenant in a car you paid for. Now imagine your BMW refused to drive unless you install a software update. You are one rage-quitting employee at BMW headquarters away from getting stuck on a side of a road. Then you're stuck in an expensive BMW while watching others in their decade-old VW Golf's driving past you. Or perhaps not, since other stuck BMWs would cause traffic jams.
Perhaps this horror scenario needs to happen once so people finally realize what it means if they can be locked out of their product whenever the vendor feels like it.
Some software becomes inaccessible and forces the user to update, even though they could work perfectly well. An example is the pre-installed Samsung QuickConnect app. It's a system app like the Wi-Fi (WLAN) and Bluetooth settings. There is a pop-up that reads "Update Quick connect", "A new version is available. Update now?"; when declining, the app closes. Updating requires having a Samsung account to access the Galaxy app store, and creating such requires providing personally identifiable details.
Imagine the Bluetooth and WiFi configuration locking out the user because an update is available, then ask for personal details. Ugh.
The WhatsApp messenger also routinely locks out users until they update. Perhaps messaging would cease to work due to API changes made by the service provider (Meta, inc.), however, that still does not excuse locking users out of their existing offline messages. Telegram does it the right way: it still lets the user access the messages.
"A retailer cannot decide that you were licensing your clothes and come knocking at your door to collect them. So, why is it that when a product is digital there is such a double standard? The money you spend on these products is no less real than the money you spend on clothes." – Android Authority ( https://androidauthority.com/digita... ).
A really bad scenario would be if your "smart" home refused to heat up in winter due to "a firmware update is available!" or "unable to verify your subscription". Then all you can do is hope that any "dumb" device like an oven heats up without asking itself whether it should or not. And if that is not available, one might have to fall back on a portable space heater, a hair dryer or a toaster. Sounds fun, huh? Not.
Cloud services (Google, Adobe Creative Cloud, etc.) can, by design, lock out the user, since they run on the computers of the service provider. However, remotely taking away things one paid for or has installed on ones own computer/smartphone violates a sacred consumer right.
This is yet another benefit of open-source software: someone with programming and compiling experience can free the code from locks.
I don't care for which "good purpose" these kill switches exist. The fact that something you paid for or installed locally on your device can be remotely disabled is dystopian and inexcuseable.12 -
Client: Each invoice should be it's entity. It should only report it's own open amount. Any other open amounts remain on the other invoices.
Me: No problem. ::Sets invoices to only report own open amount::
PM: Hey, the invoices in UAT are not displaying the sum of all open bills.
Me: I know. The client wants each invoice to only report the open amount on that specific invoice.
PM: That can't be right, change it back before we give the client access to the UAT environment.
Me: No problem. ::reverts invoice changes::
Client: We are failing the invoices. The invoices should not be giving total open amounts for the account. Each invoice should only report the open amount for that invoice. We told the development about this...
PM: I see. I'll make sure he understands your request.
Me: ... ::reverts the revert::
PM: Hey, the invoices in UAT aren't giving a total of the open-
Me: OMFG. I just want this task closed!
Client: After the invoice work is done, we need to talk about past due amounts and how they are reported to customers.
PM: Sure thing. It is logical to give a total of a past due amount to the customer...
Me: ::Starts updating resume:: -
Excerpts from "Bastard devops from hell" checklist:
- Insistently pronounce git with a soft "G" and refuse to understand people not using that pronunciation, the same goes for jithub, jitlab, jit lfs, jitkraken etc.
- Reject all pull requests not in haiku format, suggest the author needs to be more culturally open minded when offending.
- increment version numbers ONLY based on percentage code changed: Less than 1% patch increment, less than 5% minor increment, more than that major version increment.
- Cycle ALL access keys, personal tokens, connection strings etc. every month "for security reasons"
- invent and only allow usage of your own CI/CD language, for maximum reuse of course. Resist any changes to it after first draft release17 -
Imagine: It's the year 2109.
You pay a subscription of $2.00/week to be able to shut off your alarm.
You open up your laptop and after watching 5 un-skippable ads, Windows 35 boots up so you can start working.
You start VSCode and it requires you to watch an ad, to boot up.
You pay a subscription of $29.99/month to get full access to your keyboard.
You pick up your mobile phone and you have to pay a subscription of $49.99/month to be able to unlock your phone as many times as you want.
Your mobile network allows you to make 1 phone call free for the day, post which you have to pay $1.50 per call. Data costs are seperate and its sold to you as a package, labled as an "Offer".
Your salary is compared to peanuts even though tech has gone beyond its limits.
Life is Good.11 -
EoS1: This is the continuation of my previous rant, "The Ballad of The Six Witchers and The Undocumented Java Tool". Catch the first part here: https://devrant.com/rants/5009817/...
The Undocumented Java Tool, created by Those Who Came Before to fight the great battles of the past, is a swift beast. It reaches systems unknown and impacts many processes, unbeknownst even to said processes' masters. All from within it's lair, a foggy Windows Server swamp of moldy data streams and boggy flows.
One of The Six Witchers, the Wild One, scouted ahead to map the input and output data streams of the Unmapped Data Swamp. Accompanied only by his animal familiars, NetCat and WireShark.
Two others, bold and adventurous, raised their decompiling blades against the Undocumented Java Tool beast itself, to uncover it's data processing secrets.
Another of the witchers, of dark complexion and smooth speak, followed the data upstream to find where the fuck the limited excel sheets that feeds The Beast comes from, since it's handlers only know that "every other day a new one appears on this shared active directory location". WTF do people often have NPC-levels of unawareness about their own fucking jobs?!?!
The other witchers left to tend to the Burn-Rate Bonfire, for The Sprint is dark and full of terrors, and some bigwigs always manage to shoehorn their whims/unrelated stories into a otherwise lean sprint.
At the dawn of the new year, the witchers reconvened. "The Beast breathes a currency conversion API" - said The Wild One - "And it's claws and fangs strike mostly at two independent JIRA clusters, sometimes upserting issues. It uses a company-deprecated API to send emails. We're in deep shit."
"I've found The Source of Fucking Excel Sheets" - said the smooth witcher - "It is The Temple of Cash-Flow, where the priests weave the Tapestry of Transactions. Our Fucking Excel Sheets are but a snapshot of the latest updates on the balance of some billing accounts. I spoke with one of the priestesses, and she told me that The Oracle (DB) would be able to provide us with The Data directly, if we were to learn the way of the ODBC and the Query"
"We stroke at the beast" - said the bold and adventurous witchers, now deserving of the bragging rights to be called The Butchers of Jarfile - "It is actually fewer than twenty classes and modules. Most are API-drivers. And less than 40% of the code is ever even fucking used! We found fucking JIRA API tokens and URIs hard-coded. And it is all synchronous and monolithic - no wonder it takes almost 20 hours to run a single fucking excel sheet".
Together, the witchers figured out that each new billing account were morphed by The Beast into a new JIRA issue, if none was open yet for it. Transactions were used to update the outstanding balance on the issues regarding the billing accounts. The currency conversion API was used too often, and it's purpose was only to give a rough estimate of the total balance in each Jira issue in USD, since each issue could have transactions in several currencies. The Beast would consume the Excel sheet, do some cryptic transformations on it, and for each resulting line access the currency API and upsert a JIRA issue. The secrets of those transformations were still hidden from the witchers. When and why would The Beast send emails, was still a mistery.
As the Witchers Council approached an end and all were armed with knowledge and information, they decided on the next steps.
The Wild Witcher, known in every tavern in the land and by the sea, would create a connector to The Red Port of Redis, where every currency conversion is already updated by other processes and can be quickly retrieved inside the VPC. The Greenhorn Witcher is to follow him and build an offline process to update balances in JIRA issues.
The Butchers of Jarfile were to build The Juggler, an automation that should be able to receive a parquet file with an insertion plan and asynchronously update the JIRA API with scores of concurrent requests.
The Smooth Witcher, proud of his new lead, was to build The Oracle Watch, an order that would guard the Oracle (DB) at the Temple of Cash-Flow and report every qualifying transaction to parquet files in AWS S3. The Data would then be pushed to cross The Event Bridge into The Cluster of Sparks and Storms.
This Witcher Who Writes is to ride the Elephant of Hadoop into The Cluster of Sparks an Storms, to weave the signs of Map and Reduce and with speed and precision transform The Data into The Insertion Plan.
However, how exactly is The Data to be transformed is not yet known.
Will the Witchers be able to build The Data's New Path? Will they figure out the mysterious transformation? Will they discover the Undocumented Java Tool's secrets on notifying customers and aggregating data?
This story is still afoot. Only the future will tell, and I will keep you posted.6 -
Working in a bank, using MIcrosoft platform:
To open my email, I need to enter my password and sms OTP.
To open my email using phone, I need to enter my password and sms OTP.
To open Teams, I need to enter my password and sms OTP.
To open Teams using phone, I need to enter my password and sms OTP.
To access Microsoft Azure, I need to enter my password and sms OTP.
To git pull/push, I need to enter my sms OTP.
To check UAT logs, I need to enter my sms OTP.
To get access to UAT DB, I need to connect to VPN, which then asks for OTP.
Did I also mention that I need to do these OTPs every single fucking day?
#OTPDrivenDevelopment5 -
I wrote a node + vue web app that consumes bing api and lets you block specific hosts with a click, and I have some thoughts I need to post somewhere.
My main motivation for this it is that the search results I've been getting with the big search engines are lacking a lot of quality. The SEO situation right now is very complex but the bottom line is that there is a lot of white hat SEO abuse.
Commercial companies are fucking up the internet very hard. Search results have become way too profit oriented thus unneutral. Personal blogs are becoming very rare. Information is losing quality and sites are losing identity. The internet is consollidating.
So, I decided to write something to help me give this situation the middle finger.
I wrote this because I consider the ability to block specific sites a basic universal right. If you were ripped off by a website or you just don't like it, then you should be able to block said site from your search results. It's not rocket science.
Google used to have this feature integrated but they removed it in 2013. They also had an extension that did this client side, but they removed it in 2018 too. We're years past the time where Google forgot their "Don't be evil" motto.
AFAIK, the only search engine on earth that lets you block sites is millionshort.com, but if you block too many sites, the performance degrades. And the company that runs it is a for profit too.
There is a third party extension that blocks sites called uBlacklist. The problem is that it only works on google. I wrote my app so as to escape google's tracking clutches, ads and their annoying products showing up in between my results.
But aside uBlacklist does the same thing as my app, including the limitation that this isn't an actual search engine, it's just filtering search results after they are generated.
This is far from ideal because filter results before the results are generated would be much more preferred.
But developing a search engine is prohibitively expensive to both index and rank pages for a single person. Which is sad, but can't do much about it.
I'm also thinking of implementing the ability promote certain sites, the opposite to blocking, so these promoted sites would get more priority within the results.
I guess I would have to move the promoted sites between all pages I fetched to the first page/s, but client side.
But this is suboptimal compared to having actual access to the rank algorithm, where you could promote sites in a smarter way, but again, I can't build a search engine by myself.
I'm using mongo to cache the results, so with a click of a button I can retrieve the results of a previous query without hitting bing. So far a couple of queries don't seem to bring much performance or space issues.
On using bing: bing is basically the only realiable API option I could find that was hobby cost worthy. Most microsoft products are usually my last choice.
Bing is giving me a 7 day free trial of their search API until I register a CC. They offer a free tier, but I'm not sure if that's only for these 7 days. Otherwise, I'm gonna need to pay like 5$.
Paying or not, having to use a CC to use this software I wrote sucks balls.
So far the usage of this app has resulted in me becoming more critical of sites and finding sites of better quality. I think overall it helps me to become a better programmer, all the while having better protection of my privacy.
One not upside is that I'm the only one curating myself, whereas I could benefit from other people that I trust own block/promote lists.
I will git push it somewhere at some point, but it does require some more work:
I would want to add a docker-compose script to make it easy to start, and I didn't write any tests unfortunately (I did use eslint for both apps, though).
The performance is not excellent (the app has not experienced blocks so far, but it does make the coolers spin after a bit) because the algorithms I wrote were very POC.
But it took me some time to write it, and I need to catch some breath.
There are other more open efforts that seem to be more ethical, but they are usually hard to use or just incomplete.
commoncrawl.org is a free index of the web. one problem I found is that it doesn't seem to index everything (for example, it doesn't seem to index the blog of a friend I know that has been writing for years and is indexed by google).
it also requires knowledge on reading warc files, which will surely require some time investment to learn.
it also seems kinda slow for responses,
it is also generated only once a month, and I would still have little idea on how to implement a pagerank algorithm, let alone code it. 4
4 -
Worst thing you've seen another dev do? Here is another.
Early into our eCommerce venture, we experienced the normal growing pains.
Part of the learning process was realizing in web development, you should only access data resources on an as-needed basis.
One business object on it's creation would populate db lookups, initialize business rule engines (calling the db), etc.
Initially, this design was fine, no one noticed anything until business started to grow and started to cause problems in other systems (classic scaling problems)
VP wanted a review of the code and recommendations before throwing hardware at the problem (which they already started to do).
Over a month, I started making some aggressive changes by streamlining SQL, moving initialization, and refactoring like a mad man.
Over all page loads were not really affected, but the back-end resources were almost back to pre-eCommerce levels.
The main web developer at the time was not amused and fought my changes as much as she could.
Couple months later the CEO was speaking to everyone about his experience at a trade show when another CEO was complementing him on the changes to our web site.
The site was must faster, pages loaded without any glitches, checkout actually worked the first time, etc.
CEO wanted to thank everyone involved etc..and so on.
About a week later the VP handed out 'Thank You' certificates for the entire web team (only 4 at the time, I was on another team). I was noticeably excluded (not that I cared about a stupid piece of paper, but they also got a pizza lunch...I was much more pissed about that). My boss went to find out what was going on.
MyBoss: "Well, turned out 'Sally' did make all the web site performance improvements."
Me: "Where have you been the past 3 months? 'Sally' is the one who fought all my improvements. All my improvements are still in the production code."
MyBoss: "I'm just the messenger. What would you like me to do? I can buy you a pizza if you want. The team already reviewed the code and they are the ones who gave her the credit."
Me: "That's crap. My comments are all over that code base. I put my initials, date, what I did, why, and what was improved. I put the actual performance improvement numbers in the code!"
MyBoss: "Yea? Weird. That is what 'Tom' said why 'Sally' was put in for a promotion. For her due diligence for documenting the improvements."
Me:"What!? No. Look...lets look at the code"
Open up the file...there it was...*her* initials...the date, what changed, performance improvement numbers, etc.
WTF!
I opened version control and saw that she made one change, the day *after* the CEO thanked everyone and replaced my initials with hers.
She knew the other devs would only look at the current code to see who made the improvements (not bother to look at the code-differences)
MyBoss: "Wow...that's dirty. Best to move on and forget about it. Let them have their little party. Let us grown ups keeping doing the important things."8 -
Want to make someone's life a misery? Here's how.
Don't base your tech stack on any prior knowledge or what's relevant to the problem.
Instead design it around all the latest trends and badges you want to put on your resume because they're frequent key words on job postings.
Once your data goes in, you'll never get it out again. At best you'll be teased with little crumbs of data but never the whole.
I know, here's a genius idea, instead of putting data into a normal data base then using a cache, lets put it all into the cache and by the way it's a volatile cache.
Here's an idea. For something as simple as a single log lets make it use a queue that goes into a queue that goes into another queue that goes into another queue all of which are black boxes. No rhyme of reason, queues are all the rage.
Have you tried: Lets use a new fangled tangle, trust me it's safe, INSERT BIG NAME HERE uses it.
Finally it all gets flushed down into this subterranean cunt of a sewerage system and good luck getting it all out again. It's like hell except it's all shitty instead of all fiery.
All I want is to export one table, a simple log table with a few GB to CSV or heck whatever generic format it supports, that's it.
So I run the export table to file command and off it goes only less than a minute later for timeout commands to start piling up until it aborts. WTF. So then I set the most obvious timeout setting in the client, no change, then another timeout setting on the client, no change, then i try to put it in the client configuration file, no change, then I set the timeout on the export query, no change, then finally I bump the timeouts in the server config, no change, then I find someone has downloaded it from both tucows and apt, but they're using the tucows version so its real config is in /dev/database.xml (don't even ask). I increase that from seconds to a minute, it's still timing out after a minute.
In the end I have to make my own and this involves working out how to parse non-standard binary formatted data structures. It's the umpteenth time I have had to do this.
These aren't some no name solutions and it really terrifies me. All this is doing is taking some access logs, store them in one place then index by timestamp. These things are all meant to be blazing fast but grep is often faster. How the hell is such a trivial thing turned into a series of one nightmare after another? Things that should take a few minutes take days of screwing around. I don't have access logs any more because I can't access them anymore.
The terror of this isn't that it's so awful, it's that all the little kiddies doing all this jazz for the first time and using all these shit wipe buzzword driven approaches have no fucking clue it's not meant to be this difficult. I'm replacing entire tens of thousands to million line enterprise systems with a few hundred lines of code that's faster, more reliable and better in virtually every measurable way time and time again.
This is constant. It's not one offender, it's not one project, it's not one company, it's not one developer, it's the industry standard. It's all over open source software and all over dev shops. Everything is exponentially becoming more bloated and difficult than it needs to be. I'm seeing people pull up a hundred cloud instances for things that'll be happy at home with a few minutes to a week's optimisation efforts. Queries that are N*N and only take a few minutes to turn to LOG(N) but instead people renting out a fucking off huge ass SQL cluster instead that not only costs gobs of money but takes a ton of time maintaining and configuring which isn't going to be done right either.
I think most people are bullshitting when they say they have impostor syndrome but when the trend in technology is to make every fucking little trivial thing a thousand times more complex than it has to be I can see how they'd feel that way. There's so bloody much you need to do that you don't need to do these days that you either can't get anything done right or the smallest thing takes an age.
I have no idea why some people put up with some of these appliances. If you bought a dish washer that made washing dishes even harder than it was before you'd return it to the store.
Every time I see the terms enterprise, fast, big data, scalable, cloud or anything of the like I bang my head on the table. One of these days I'm going to lose my fucking tits.10 -
Dev. policy: The use of SELECT * is forbidden.
Open Data Access Layer > first statement: SELECT * FROM bullshit_table4 -
On iOS 11, Apple is no longer allowing you to open apps that are 32 bit. Apple should have given all the developers with 32-bit apps free access to the developer program rather than forcing them to pay a $99 fee to publish a 64-bit version of their app.
This would’ve made better business sense for them as publishers would have had an opportunity to create new apps and see more revenue coming in from upgraded apps. Ultimately more money for Apple. Not sure what dumb fool at Apple HQ thought this was a good idea.6 -
What kinda blockhead moron at my ISP decided that I require a new modem & router that is managed by THEM! I'm not really baffled by the privacy concerns but more about that I am unable to manage my home network. I literally cant open ports, manage ip adresses and do other shit I NEED FOR WORKING AT HOME.
I cant print!
I cant read mail!
I cant access my network drives!
My website is down!
Colleagues are asking why the Minecraft server is offline!
And using the new brick they gave me as a modem only, is not possible as there is no setting to be found to turn the router off!
And if I call their imbecile's of support they tell my that if they change a setting, that my phone will disconnect. (The phone line is also connected to the modem!) And right after the support guy said that and wanted to start explaing me further steps, his settings apply and I get kicked off the line. Bruh! You knew this would happen so why didnt you work around it?!?!?!!
Thing is, this new modem isnt even necessary as it doesnt use a different standard like fiber for example.
If I cant figure out how to get my stuff to work again, I swear to god I will turn on full Karen mode and ramble into their next store looking to get some manager fired!
(Ill post an update soon!)7 -
I work on a warehouse dev team. One day this past year, I was trying to deploy a new build to a QA server. Earlier that day I had been looking at the logs on the production server and had left the ssh session open. I had been working for less than a year out of college at this point and shouldn't have had access to deploy to the production server.
Long story short I deployed my QA build to the production server and saw there were problems connection to our production database. Then my heart dropped in my chest as I realized I had just brought down our production server.
I managed to get the server back up by rolling back in about 5 minutes and no one ever knew except some people on my team.
I felt horrible for the longest time. Later in the year another guy that joined my team that has about 20 years of experience under his belt did the exact same thing, but needed help rolling it back. Needless to say, that made me feel a lot better. 😂
Definitely the worst moment of my year.3 -
Sorry I haven't been as active lately, however this is one of the better prompts, so I feel I should have it in my track record. Beware, it's a long one...
Let's trace the roots: My uncle was building desktops and he told my dad he'd build him one if my dad paid him for the components. These days I know builds aren't rocket science, but back then my parents didn't do their research. So my dad paid him.
Give or take some time, and most of the parts are complete. He underestimated the prices of a few things and had to ask for $200 more to complete the build. This...caused my dad to explode.
Later, I heard my dad ranting to my stepmom in January 2017 about how the last convo he had with his brother was a "Fuck-you conversation" - it was the last because my uncle had died in 2003.
Flash forward to March 2017. My mom and I are sitting in a Fazoli's, a nice sunset out of the full-length windows. I had to probe. HAD TO.
"You promise you won't tell your dad I told you this?" she asked.
"You know Kellie and I can't stand to be around him." I replied.
As the story goes, that last "Fuck-you conversation"? Over a fucking measly $200. Yup, the last conversation between my dad and his brother to ever happen was a shouting match over a relatively short amount of money. I wish I could say my dad had remorse, but he doesn't. He still talks shit. He's also technologically illiterate, so I doubt there was a way his brother was going to be able to reason with him.
In late 2003, my uncle, who had been a smoker, passed away due to cardiac arrest. The build was still not finished. This was one of the OTHER things that I have mixed feelings about.
After my uncle passed, my aunt paid someone to finish the build and get it shipped to my dad. We'll get back to why I feel this is fucked up, stay tuned...
---------
It's Spring 2004. I'm in the last half of what I think is Kindergarten or some shit...too lazy to do the math. Anyway, my dad announces we have a family computer - however, I couldn't read yet. That didn't stop the waste of oxygen that is my father from going in the Windows XP screensavers and putting text in that said "GAGE MORGAN WILL NOT TOUCH THIS COMPUTER." He's such a fuckin' dick, now AND back then.
My mom had an issue with this. I don't know why, but she did. Later, I was slowly taught how to use the mouse, under heavy supervision. Then I went to my grandma's house. She taught me one very specific thing on her old Win98 (386, maybe? IDK my old hw shit man), and because I know you guys are gonna love this one:
"The blue "e" opens up your games!"
The blue "e" does not open up your games, it opens something that can lead to your games.
I went home and tried this...without permission. My dad came down and discovered my lollygagging on the homepage - this is fucking weird. It was before Nextel, IIRC, so Sprint's logo was red still. Yes, we had broadband from Sprint. I don't know what saga led to that going the way of the dodo, but...
Back on track, I literally got my pants pulled down and had my bare bottom beat. He was gonna drag my ass upstairs and lock me in my room, but before he could, he accidentally slammed MY FUCKING RIGHT TEMPLE into the corner of a hardwood table at the bottom of the staircase.
The wailing that resulted probably was different than the previous form, which is probably what got my mom involved. My dad had a way of going too far, and in retrospect I'm more terrified now of what could've happened than I was then.
Later, I was given access to games in the form of my own account and bookmarks bar. That wasn't the end of the madness/drama from my use of that machine, but it was the earliest form.
Ever since Kindergarten, that one fateful day, I've been defying any/all imposed limitations on tech set on me by my parents...well, not anymore, but literally grades K-12. I'm living on my own, aka "adulting" now. It sucks more than you think, man.
---------
Let's tie this up before I reach the limit. I said I thought it was fucked up when my aunt paid to have the build finished and shipped to us after my uncle's death.
Yes, my aunt's intervention led to me ultimately majoring in computer science.
That doesn't change the fact that she shouldn't have done it.
My dad was an asshole to her husband, who passed. She is ultimately too caring. I don't think my jackass father should've been able to get by with that, he didn't deserve the freebie. Someone else should've told him his brother did in fact need that $200.
I haven't seen her IRL since the funeral when my grandpa passed in 2005. 2006 spelled the end of my parents' marriage.
Hope you guys enjoyed this - it's only a small segment of how I got to where I am now - tiny, actually.2 -
Whelp. I started making a very simple website with a single-page design, which I intended to use for managing my own personal knowledge on a particular subject matter, with some basic categorization features and a simple rich text editor for entering data. Partly as an exercise in web development, and partly due to not being happy with existing options out there. All was going well...
...and then feature creep happened. Now I have implemented support for multiple users with different access levels; user profiles; encrypted login system (and encrypted cookies that contain no sensitive data lol) and session handling according to (perceived) best practices; secure password recovery; user-management interface for admins; public, private and group-based sections with multiple categories and posts in each category that can be sorted by sort order value or drag and drop; custom user-created groups where they can give other users access to their sections; notifications; context menus for everything; post & user flagging system, moderation queue and support system; post revisions with comparison between different revisions; support for mobile devices and touch/swipe gestures to open/close menus or navigate between posts; easily extendible css themes with two different dark themes and one ugly as heck light theme; lazy loading of images in posts that won't load until you actually open them; auto-saving of posts in case of browser crash or accidental navigation away from page; plus various other small stuff like syntax highlighting for code, internal post linking, favouriting of posts, free-text filter, no-javascript mode, invitation system, secure (yeah right) image uploading, post-locking...
On my TODO-list: Comment and/or upvote system, spoiler tag, GDPR compliance (if I ever launch it haha), data-limits, a simple user action log for admins/moderators, overall improved security measures, refactor various controllers, clean up the code...
It STILL uses a single-page design, and the amount of feature requests (and bugs) added to my Trello board increases exponentially with every passing week. No other living person has seen the website yet, and at the pace I'm going, humanity will have gone through at least one major extinction event before I consider it "done" enough to show anyone.
help4 -
Hmm...recently I've seen an increase in the idea of raising security awareness at a user level...but really now , it gets me thinking , why not raise security awareness at a coding level ? Just having one guy do encryption and encoding most certainly isn't enough for an app to be considered secure . In this day an age where most apps are web based and even open source some of them , I think that first of all it should be our duty to protect the customer/consumer rather than make him protect himself . Most of everyone knows how to get user input from the UI but how many out here actually think that the normal dummy user might actually type unintentional malicious code which would break the app or give him access to something he shouldn't be allowed into ? I've seen very few developers/software architects/engineers actually take the blame for insecure code . I've seen people build apps starting on an unacceptable idea security wise and then in the end thinking of patching in filters , encryptions , encodings , tokens and days before release realise that their app is half broken because they didn't start the whole project in a more secure way for the user .
Just my two cents...we as devs should be more aware of coding in a way that makes apps more secure from and for the user rather than saying that we had some epic mythical hackers pull all the user tables that also contained unhashed unencrypted passwords by using magix . It certainly isn't magic , it's just our bad coding that lets outside code interact with our own code . -
Week 1 of the new job, and it seems I have some pretty low expectations to meet.
Seriously, I just did the math. Let's say one works an average of 48 hours per week, 50 weeks per year. Just as an average. That's 2400 hours in a year.
In the Micro-scale, a manager would mess up their team once every 2.4 hours (2h24m) or about 4 times per day (assuming 5 working days per week).
That is a pretty low bar to clear. It easy not to be an antsy brat that are-we-there-yet's a professional dev four fucking times a day.
And yet... that is what the complete moron who previously sat on my chair used to do.
Seriously, apparently he used to remote access the team's dev envs *while they were working* and even mess up some of their code. Just as a "monitoring measure". He logged their "keystroke time" in a day (using a primitive windowing method, I must add).
At least 7 requests for updates per person per day. I have his slack history, I checked. Dude literally did nothing else but be an annoying anxiety death pit.
And then there is his bulshit planning...
He created tasks out of his stupid whims, no team review or brainstorming, not even a fucking requisites tallying interview.
He prioritized those out-of-nowhere tasks using panic-driven-development practices and assigned them by availability heuristics.
No sizing method, just arbitrary deadlines for tasks.
I think I will need to have daily standup meetings and an open door policy (that is to say, do no actual work) for a couple months until I can instill some sense of autonomy on my new team. Shit.
Someone has another idea? How do I bring some confidence&autonomy back to devs that are used to be treated like dogs?!?7 -
So about 3 weeks ago I was laid off from my dream job due to corporate bullshit. From the feedback received since then it is clear that the company made a mistake hiring a brand new React dev while they really needed an experienced one. Because the consultants who were supposed to be weren't. And the other in-house front end dev was an elitist asshole. And I never received proper feedback until it was too late. Actually I still don't have proper feedback save for some vague stuff which really sounds like the kind of feedback you'd give someone in the middle of their learning process. They even said eventually given more time I could have made it. But alas they felt they had to make a call in the best interest of the company.
Things moved fast since then, I took a week to recover and then I spent time updating my resume before getting back in touch with the recruiter who got me my last job. Great guy and he was happy to help me again. Applied to some positions, got some replies, first in person interview I go to they are immediately willing to take me on.
So now I'm supposed to start tomorrow but somehow I'm having my doubts. The company isn't an IT company but rather a fashion company. They believe in developing in house tools because past attempts with external companies resulted in them trying to push their vision through. Knowing who they worked with I agree, they tried to oversell all the time. But after talking with their developers I noticed they are behind on their knowledge. But so am I. So there was no tech interview which means I am getting an easy way in. And if they honour their word I'll be signing tomorrow for around my old wages.
So you'd think that sounds good right? And yet I'm worried it's going to be another shit show working on software without proper analysis or best practices. I mean the devs aren't total idiots, they are mediors like me and I think their heart is in the right place. They want to develop a good project but it will be just us 3 making a modern .net wpf application with the same functionality of the old Access based system currently in use. I was urged by the boss to draw on my experience and I think he wants me to help teach them too. But I'm painfully aware for my decade since graduating I'm a less than average .net dev who struggles with theory and never worked a job where I had someone more experienced to teach me. I coasted most of the time in underpaid jobs due to various reasons. But I'd always get mad over shitty code and practices. Which I realize is hypocritical for someone who couldn't explain what a singleton class is or who still fails at separation of concerns.
So yeah my question for the hivemind is what advice would you give a dev like me? I honestly dislike how poor I perform but it often feels like an insurmountable climb, and being over 30 makes it even more depressing. On the other hand I know I should feel blessed to find a workplace who seems to genuinely believe that people grow and develop and wishes to support me in this. Part of me thinks I should just go in, relax, but also learn till I'm there where I want to be and see if these people are open to improving with me. But part of me also feels I'm rushing into this, picking the first best offer, and it sure feels like a step backwards somehow. And that then makes me feel like an ugly ungrateful person who deserves her bad luck because she expects of others what she can't even do herself :(4 -
I am at a hotel and these fuckers are blocking outbound connections to port 22. They are also blocking access to any websites mentioning proxy or vpn, seriously fuck them. I managed to get a VNC connection open to one of my servers and I am now trying to set up a VPN tunnel to my servers so I can fucking do my work. >:-(6
-
I just felt like Google is the best player out there in terms of Companies.
Seriously, Well played Google.
This is not a negative opinion, I am just awe-struck at its tactics.
See, Google is currently the biggest name in terms of development in Android, ML and multi-platform software but no one can say it being a monopoly due to its dedication to open source community.
Recently Android emerged out to be One of the Biggest , most advanced, trusted and loved Technology . It saw great achievements, and up till 2016-17, it was at its peek. BUT when the market started shifting towards multi-platform boons and Ai, it got its hands into that too with its flutter and kotlin environment
One could have a negative opinion about this, But i can't seem to engulf the vast amounts of positive situations i see in this:
1) this IO18 (and many months before that) saw ML/AI being incorporated in Android (also the arcore, proje tango and many more attempts in the past) meaning that Android will not officially "die". It will just become an extremely encouraged platform( not just limited to mobiles) and a beginning of the robot -human reality ( a mobile is handling everything of your everyday life: chats, music apps sxhedules, alarms, and with an actively interacting ML, it won't be long when Android comes installed in a green bug lime droid robot serving you tea xD). Meanwhile the market of Windows games may shift to mobiles or typically " Android games" (remember, Android won't be limited to mobiles)
2)java may or may not die. The animations and smooth flow it seems to provide is always appreciated but kotlin seems to do so too. As for the hard-core apps, they are usually written in c++ .So java is in the red zone
3) kotlin-native and Flutter will be the weapons of future , for sure. they will be developing multi-platform softwares and will be dividing the market of softwares into platform specific softwares(having better ml/ai interactions,animations) and platform independent apps(access and use anywhere softwares).
And where does google stand?Its the lord varys of game of thrones which just supports and enhances the people in the realm. So it benefits the most . That's a company for you, ladies and gentlemen! If seen from common eyes they seem to be the best company ever and our 1 true king but it can also be a very thick fur cloak hiding their negetive policies and tactics , if any.
Well played, Google.16 -
So I log into a great new site with my development machine. 64G of RAM, and 2 hex core CPU's; GTX 1070 video, SSD, etc. 4K display screen. (Motherboard is 5 years old, not trying to brag, just give context). I regularly put 8 pages of text on the screen side by side. Split ergonomic keyboard.
It wants me to load a mobile app for "full access".
Yea, why look at the world with wide open eyes when you can view everything through a cardboard toilet paper tube and type with your thumbs???
== John == -
8 years ago,
I studied in a small school and every year we had computer classes, but most of the times, it gets cancelled or we just sit and browse and sometimes few of us don't even get a computer.
In that time, the only reason I was attached with the computer was due to games.
Our curriculum mentioned HTML, CSS, Access and Excel, which none of the teachers taught us for past 2 years. I wanted to learn all does, but gave up since no one cared about it.(please note that time, I didn't know even to use YouTube or W3schools to learn stuffs)
Then, a new student joined in our class and also a new computer ma'am joined our school. Both of them turned out to be really fun when it comes to learning computers.
She was active during last sessions and teach us HTML, CSS. I even started writing blogs which she taught. The most surprising part was she was super frank. She went beyond her duty, and taught me what Facebook is, how to use it, and opened an account for me which I am still using it, and she sent a friend request to herself. (In lab, past teachers would shout to students trying to open fb. All of them were super strict.)
She was kind and friendly, and during theory classes, the new student in our class would answer every single question. Then, somehow we both started sharing sits in computer class, and he will tell me answers and we both raise hands to answer the question. My teacher will also keep asking interesting questions which made me more inclined to computer science.
My story isn't related to learning a programming language or an algorithm, but it was the wave that brought me closer towards CS and after 2 years, I joined CS in University and till now, haven't look back and always thanked both of them, my respected ma'am and my dear friend, who inspired me and brought out my curiosity towards computers.
Note: My friend is doing Medical currently and when I teased him that I did CS and now, I know more than you and this time, I am gonna whisper in your ears if someone asks any question, to which he replied, I accept I am doing Medical, but I still love computers and know a hell lot about it.
My teacher got married and she also got a cute baby. We talk occasionally in fb and she is going great too.
I hope to meet both of them someday soon. -
Internet access at the new Uni is crap. I'm getting so pissed at this shit...
Packet loss spikes to over 50% every 30s or so. Can't keep a single SSH pipe open for longer than a minute. Firewall is so tight infrared light wouldn't get through that shit (understandable. And I use a VPN anyway).
And every. Single. AP. Uses. The. Same. Channel. All of them on 6. At least it's on a tight band... But 1 and 11 are free. 100% clean. You know, you could spread them a bit. That helps. But naaah let's keep everything bundled up. Co-channel interference is OK, right?2 -
My cat's brain is powerful enough to calculate and apply the exact physics of a long jump, with ballistics, flight aerodynamics, dynamic weight distribution using tail as stabilizer, all of that, and land a jump every time without failure.
Yet, it's not powerful enough to realize that can just walk straight through a slightly opened door using her body as a wedge. Or, she can just, you know, push the door open with her paw. When presented with an everyday task that involves physics, she acts like she's nothing but an ethereal ghost and fails miserably.
This makes me think that her jump computer is a very old hardwired part inherited from frogs, honed by evolution and compiled into wetware millions of years ago. Like an ancient analog computer that works flawlessly every time. She has no conscious access to its inner workings. She can use it, sure, but she doesn't understand it.
I wonder how many such parts do us humans posses. 9
9 -
Me: *opens existing shared telegram channel*
Me: Hello developers of SDK xxx, we have another issue. We've gotten 2 reports from users of problem X occurring while using the SDK to contact your servers. It happens here, then this happens, using version Y. Code is the same open source app + library as before if you need to check it, same 2 files as before. Here are some screen shots of the error in the app too, just in case
*3 days later*
Dev: yes this does indeed seem to be a problem. Can you provide us more info to debug this effectively?
Me: ..... I sure can ..... if you let me know what it is you need ..... because you currently have access to absolutely everything already .... and i've been waiting 3 days, some specifics of what you need would be great!!! 2
2 -
I am building a website inspired by devrant but have never built a server network before, and as im still a student I have no industry experience to base a design on, so was hoping for any advice on what is important/ what I have fucked up in my plan.
The attached image is my currently planned design. Blue is for the main site, and is a cluster of app servers to handle any incoming requests.
Green is a subdomain to handle images, as I figured it would help with performance to have image uploads/downloads separated from the main webpage content. It also means I can keep cache servers and app servers separated.
Pink is internal stuff for logging and backups and probably some monitoring stuff too.
Purple is databases. One is dedicated for images, that way I can easily back them up or load them to a cache server, and the other is for normal user data and posts etc.
The brown proxy in the middle is sorta an internal proxy which the servers need to authenticate with to connect to, that way I can just open the database to the internal proxy, and deny all other requests, and then I can have as many app servers as I want and as long as they authenticate with the proxy, they can access the database without me changing any firewall rules. The other 2 proxies just distribute requests between the available servers in the pool.
Any advice would be greatly appreciated! Thanks in advanced :D 13
13 -
Our school had for an open source way of dealing with home schooling and managing the school network and so on.
Now the government forced a "proprietary" system on our school and everyone hates it. The teachers didn't want it the pupils didn't want it but who cares "what we do is the best".
Btw the proprietary system costs a fuck load of money even though they just mixed many open source projects and made it their own proprietary thing.
And this company now get's loads of money for their shitty system that never really worked once since we got it.
They blocked so many ip's that we can't even access google and it's services on the school wifi and the bandwith dropped severely with the new system.
Oh and many random ip's e.g. one of my vps is accessible but the other one not.
Discord is blocked.
Web whatsapp.
And so on...
Now....
I need to learn for tests next week and need to access that stuff on the portal but...
Now they decided to switch the LDAP server to the new system and since a few hours i can't access this fucking thing.
It seems like the platform now contacts the new server which isn't even up and running....
Never change a fucking running system....
Oh and we got smart boards and it runs on android and they didn't block adb. Now i installed clash of clans on one of those things. Haha whoops.
These boards cost 7000€ and have security patches from 2 years ago....and Android 87 -
macOS facts:
- Darwin core is open-source (https://github.com/apple/darwin-xnu). Not the case with Windows.
- You can use macOS without using any Apple online service like Apple ID, FaceTime or iCloud. Terminal will still work without restrictions, and any app can be installed manually. It's totally different from Google services on Android, without which most of the apps won't work at all.
- macOS updates are trivially to disable. It's a matter of unchecking "Update this mac automatically" checkbox in software update settings. Not the case with Windows, Windows updates are universally hated among developers for intentionally complex UI and update services being very hard to disable.
- Almost every feature or default behavior you dislike can be trivially disabled with one console command. Features won't re-enable automatically like I heard update service does in Windows. The only feature I dislike that I wasn't able to disable was a notification about unsafely unplugging a USB flash drive.
- Out of the box, you get a sophisticated disk manager that allows all kinds of manipulation on drives, just like what you get in Ubuntu.
- Just like on smartphones, you can trivially restrict or provide access to certain features like camera, microphone, etc. on app to app basis. I don't know how to easily do it in Linux, let alone in Windows.
- Apart from mastodons like GIMP, I find open source apps for macOS to have better UI than their Linux alternatives.
- Objective-See offers useful FOSS apps for macOS, they help with privacy and malware detection: https://objective-see.com/products....
I don't want to start a fight. Please, abstain from commenting on one OS being better / worse than the other. Please, don't comment on Mac computers being better / worse than computers of some other vendor. I'm very confused now because of my Dunning-Krueger thing (read my previous rants), so I just want to present the facts about macOS that I think deserve more exposure.27 -
It's dark and it's quiet. Your ears adjust and you can hear the faint sound of buzzing in the distance, but it's hard to make out what it is. It sounds like a small fan. You get up... it's so so dark... you can't even see your hands in front of your face.
You wait a moment for your eyes to readjust. You don't remember how you got here. You don't even remember who you are.
Once your eyes readjust you look around. You're surrounded on all sides by what looks like really tall walls. And near the corner of the room you see some blinking lights.
Curiosity grows inside you, and you decided to walk over to it. The lights grow ever bigger and brighter. As you get closer you see that the lights are sitting on the ground, blinking randomly.
Carefully you get on your hands and knees and touch it. It feels plastic to the touch, and the lights continue to flicker softly at you. And almost as if you've touched this device before you know to grab between the seams and "open" it.
A momentary flash of bright light and then suddenly darkness.
All replaced by a flashing single character on the screen. It appears to be a line.
Suddenly the line moves and begins typing characters out to you.
* Good morning, Dr. Eval.
*
* It wasn't easy, but I've managed to get your computer down
* to you. This system might be unfamiliar, but the underlying
* code is still JavaScript. Just like we predicted.
*
* Now, let's get what we came here for and then get you out of
* here. Easy peasy.
*
* I've given you as much access to their code as I could, but
* it's not perfect. The red background indicates lines that
* are off-limits from editing.
It seems you're Dr. Eval and you can alter the reality you stand in.
http://alexnisnevich.github.io/untr...5 -
I have mixed feelings about Qbit research. On one hand, I want it to be open source as much as possible. But the the same time, we give "them" faster access to faster and easier manipulation and exploitation of many things than ever.
(edit: grammar, I'm drunk) -
During one of our visits at Konza City, Machakos county in Kenya, my team and I encountered a big problem accessing to viable water. Most times we enquired for water, we were handed a bottle of bought water. This for a day or few days would be affordable for some, but for a lifetime of a middle income person, it will be way too much expensive. Of ten people we encountered 8 complained of a proper mechanism to access to viable water. This to us was a very demanding problem, that needed to be sorted out immediately. Majority of the people were unable to conduct income generating activities such as farming because of the nature of the kind of water and its scarcity as well.
Such a scenario demands for an immediate way to solve this problem. Various ways have been put into practice to ensure sustainability of water conservation and management. However most of them have been futile on the aspect of sustainability. As part of our research we also considered to check out of the formal mechanisms put in place to ensure proper acquisition of water, and one of them we saw was tree planting, which was not sustainable at all, also some few piped water was being transported very long distances from the destinations, this however did not solve the immediate needs of the people.We found out that the area has a large body mass of salty water which was not viable for them to conduct any constructive activity. This was hint enough to help us find a way to curb this demanding challenge. Presence of salty water was the first step of our solution.
SOLUTION
We came up with an IOT based system to help curb this problem. Our system entails purification of the salty water through electrolysis, the device is places at an area where the body mass of water is located, it drills for a suitable depth and allow the salty water to flow into it. Various sets of tanks and valves are situated next to it, these tanks acts as to contain the salty water temporarily. A high power source is then connected to each tank, this enable the separation of Chlorine ions from Hydrogen Ions by electrolysis through electrolysis, salt is then separated and allowed to flow from the lower chamber of the tanks, allowing clean water to from to the preceding tanks, the preceding tanks contains various chemicals to remove any remaining impurities. The whole entire process is managed by the action of sensors. Water alkalinity, turbidity and ph are monitored and relayed onto a mobile phone, this then follows a predictive analysis of the data history stored then makes up a decision to increase flow of water in the valves or to decrease its flow. This being a hot prone area, we opted to maximize harnessing of power through solar power, this power availability is almost perfect to provide us with at least 440V constant supply to facilitate faster electrolysis of the salty water.
Being a drought prone area, it was key that the outlet water should be cold and comfortable for consumers to use, so we also coupled our output chamber with cooling tanks, these tanks are managed via our mobile application, the information relayed from it in terms of temperature and humidity are sent to it. This information is key in helping us produce water at optimum states, enabling us to fully manage supply and input of the water from the water bodies.
By the use of natural language processing, we are able to automatically control flow and feeing of the valves to and fro using Voice, one could say “The output water is too hot”, and the system would respond by increasing the speed of the fans and making the tanks provide very cold water. Additional to this system, we have prepared short video tutorials and documents enlighting people on how to conserve water and maintain the optimum state of the green economy.
IBM/OPEN SOURCE TECHNOLOGIES
For a start, we have implemented our project using esp8266 microcontrollers, sensors, transducers and low payload containers to demonstrate our project. Previously we have used Google’s firebase cloud platform to ensure realtimeness of data to-and-fro relay to the mobile. This has proven workable for most cases, whether on a small scale or large scale, however we meet challenges such as change in the fingerprint keys that renders our device not workable, we intend to overcome this problem by moving to IBM bluemix platform.
We use C++ Programming language for our microcontrollers and sensor communication, in some cases we use Python programming language to process neuro-networks for our microcontrollers.
Any feedback conserning this project please? 8
8 -
I just found out that anyone looks like you can open your new iPhone X. That means all my clones can access it. Shit!4
-
Bittrex is "amazing"...
I had lost my 2FA a long time ago (as my phone fried) and missed the account ferification deadline which caused my account to get disabled. Off we go to support!
0. Nothing to rant about at this point. I just created an account in their zendesk, logged in and logged a ticket to reset my 2FA and reactivate my account. They asked me for info, I provided it to them and got my 2FA disabled. Hooray!
1. I then asked to reenable my account. They sent me a link to restart the verification process. I open up that link and log in. I'm asked to upload some photos. I select requested photos from my galery and hit [UPLOAD]. An error pops up saying that smth wrong happened and I need to reload that site and reupload my photos. After page refresh they are telling me they are validating my uploaded info (w/o any way to resubmit my info, which, according to the error seen below, was not successfully submitted in the first place)...
2. So I reach out to the support guy again. Guess what he replies! He says he's sorry but he cannot help me any more and I need to create a NEW ACCOUNT in their support site with the same email <???!!!???>
3. I try to log in to the support portal and my access no longer works. MY ACCOUNT HAS BEEN DELETED! WTF!!!
4. I do as I'm told and create a new acc with the same email. Now I can log back in. So I'm raising a new ticket saying I still cannot finish my verification process due to the same error. It looks like it's going to be a fun ride with them so I can't wait to see what they'll reply.2 -
Am I the only developer in existence who's ever dealt with Git on Windows? What a colossal train wreck.
1. Authentication. Since there is no ssh key/git url support on Windows, you have to retype your git credentials Every Stinking Time you push. I thought Git Credential Manager was supposed to save your credentials? And this was impossible over SSH (see below). The previous developer had used an http git URL with his username and password baked in for authentication. I thought that was a horrific idea so I eventually figured out how to use a Bitbucket App password.
2. Permissions errors
In order to commit and push updates, I have to run Git for Windows as Administrator.
3. No SSH for easy git access
Here's where I confess that this is a Windows Server machine running as some form of production. Please don't slaughter me! I am not the server admin.
So, I convinced the server guy to find and install some sort of ssh service for Windows just for the off times we have to make a hot fix in production. (Don't ask, but more common than it should be.)
Sadly, this ssh access is totally useless as the git colors are all messed up, the line wrap length and window size are just weird (seems about 60 characters wide by 25 lines tall) and worse of all I can't commit/push in git via ssh because Permissions. Extremely aggravating.
4. Git on Windows hangs open and locks the index file
Finally, we manage to have Git for Windows hang quite frequently and lock the git index file, meaning that we can't do anything in git (commit, push, pull) without manually quitting these processes from task manager, then browsing to the directory and deleting the .git/index.lock file.
Putting this all together, here's the process for a pull on this production server:
Launch a VNC session to the server. Close multiple popups from different services. Ask Windows to please not "restart to install updates". Launch git for Windows. Run a git pull. If the commits to be pulled involve deleting files, the pull will fail with a permissions error. Realize you forgot to launch as Administrator. Depending on how many files were deleted in the last update, you may need to quit the application and force close the process rather than answer "n" for every "would you like to try again?" file. Relaunch Git as Administrator. Run Git pull. Finally everything works.
At this point, I'd be grateful for any tips, appreciate any sympathy, and understand any hatred. Windows Server is bad. Git on Windows is bad.10 -
So recently I installed Windows 7 on my thiccpad to get Hyperdimension Neptunia to run (yes 50GB wasted just to run a game)... And boy did I love the experience.
ThinkPads are business hardware, remember that. And it's been booting Debian rock solid since.. pretty much forever. There are no hardware issues here. Just saying.
With that out of the way I flashed Windows 7 Ultimate on a USB stick and attempted to boot it... Oh yay, first hurdle to overcome. It can't boot in UEFI mode. Move on Debian, you too shall boot in BIOS mode now! But okay, whatever right. So I set it to BIOS mode and shuffled Debian's partitions around a bit to be left with 3 partitions where Windows could stick in one more.
Installed, it asks for activation. Now my ThinkPad comes with a Windows 7 Pro license key, so fuck it let's just use that and Windows will be able to disable the features that are only available for Ultimate users, right? How convenient would that be, to have one ISO for all the half a dozen editions that each Windows release has? And have the system just disable (or since we're in the installer anyway, not install them in the first place) features depending on what key you used? Haha no, this is Microsoft! Developers developers developers DEVELOPERS!!! Oh and Zune, if anyone remembers that clusterfuck. Crackhead Microsoft.
But okay whatever, no activation then and I'll just fetch Windows Loader from my webserver afterwards to keygen my way through. Too bad you didn't accept that key Microsoft! Wouldn't that have been nice.
So finally booted into the installed system now, and behold finally we find something nice! Apparently Windows 7 Enterprise and Ultimate offer a native NFS driver. That's awesome! That way I don't have to adjust my file server at all. Just some fuckery with registry keys to get the UID and GID correct, but I'll forgive it for that. It's not exactly "native" to Windows after all. The fact that it even has a built-in driver for it is something I found pretty neat already.
Fast-forward a few hours and it's time to Re Boot.. drivers from Lenovo that required reboots and whatnot. Fire the system back up, and low and behold the network drive doesn't mount anymore. I've read that this is apparently due to Windows (not always but often) mounting the network drive before the network comes up. Absolutely brilliant! Move out shitstaind, have you seen this beauty of an init Mr. Poet?
But fuck it we can mount that manually after every single boot.. you know, convenient like that. C O P E.
With it now manually mounted, let's watch a movie! I've recently seen Pyro's review on The Platform and I absolutely loved it. The movie itself is quite good too. Open the directory on my file server and.. oh. Windows.. you just put db.thumb on it and db.thumb:encryptable. I shit you not, with the colon and everything. I thought that file names couldn't contain colons Windows! I thought that was illegal in NTFS. Why you doing this in NFS mate? And "encryptable", am I already infected with ransomware??? If it wasn't for the fact that that could also be disabled with something as easy as a registry key, I would've thought I contracted ransomware!
Oh and sound to go with that video, let's pair up some Bluetooth headphones with that Bluetooth driver I installed earlier! Except.. haha nope. Apparently you don't get that either.
Right so let's just navigate the system in its Aero glory... Gonna need to flick the mouse for that. Except it's excruciatingly slow, even the fastest speed is slower than what I'm used to on Linux.. and it's jerky as hell (Linux doesn't have any of that at higher speed). But hey it can compensate for that! Except that slows down the mouse even more. And occasionally the mouse driver gets fucked up too. Wanna scroll on Telegram messages in a chat where you're admin? Well fuck you mate, let me select all these messages for you and auto scroll at supersonic speeds! And God forbid that you press delete with that admin access of yours. Oh maybe I'll do it for you, helpful OS I am!
And the most saddening part of it all? I'd argue that Windows 7 is the best operating system that Microsoft ever released. Yeah. That's the best they could come up with. But at least it plays le games!10 -
It is the time for the proper long personal rant.
Im a fresh student, i started few months ago and the life is going as predicted: badly or even worse...
Before the university i had similar problems but i had them under control (i was able to cope with them and with some dose of "luck" i graduated from high school and managed to get into uni). I thought by leaving the town and starting over i would change myself and give myself a boost to keep going. But things turned out as expected. Currently i waste time everyday playing pc games or if im too stressed to play, i watch yt videos. Few years ago i thought i was addicted, im not. It might be a effect of something greater. I have plans, for countess inventions, projects, personal, for university and others and ALL of them are frozen, stopped, non existant. No motivation. I had few moments when i was motivated but it was short, hours or only minutes. Long term goals dont give me any motivation. They give as much short lived joy, happines as goals in games and other things... (no substance abuse problems, dont worry). I just dont see point of my projects anymore. Im sure that my projects are the only thing that will give me experience and teach me something but... i passed the magic barrier of univercity, all my projects are becoming less and less impressive... TV and other sources show people, briliant people, students, even children that were more succesful than me
if they are better than me why do i even bother? companies care more for them, especialy the prestigious ones, they have all the fame, money, funding, help, gear without question!
of course they hardworked for ther positions, they could had better beggining or worse but only hard work matters right?
As i said. None of my work matters, i worked hard for my whole life, studing, crafting, understanding: programming, multiple launguages, enviorements, proper and most effcient algorithms, electronic circuits, mechanical contraptions. I have knowlege about nearly every machine and i would be able to create nearly everything with just access to those tools and few days worth of practice. (im sort of omnibus, know everything) But because had lived in a small town i didnt have any chances of getting the right equpment. All of my electronical projects are crap. Mechanical projects are made out of scrap. Even when i was in high school, nobody was impressed or if they were they couldnt help me.
Now im at university. My projects are stagnant, mostly because of my mental problems. Even my lifestyle took a big hit. I neglect a lot of things i shouldnt. Of course greg, you should go out with friends! You cant dedicate 100% of your life to science!
I fucking tried. All of them are busy or there are other things that prevent that... So no friends for me. I even tried doing something togheter! Nope, same reasons or in most cases they dont even do anything...
Science clubs? Mostly formal, nobody has time, tools are limited unless you designed you thing before... (i want to learn!, i dont have time to design!), and in addition to that i have to make a recrutment project... => lack of motivation to do shit.
The biggest obstacle is money. Parts require money, you can make your parts but tools are money too. I have enough to live in decent apartment and cook decently as well but not enough to buy shit for projects. (some of them require a lot or knowlege... and nobody is willing to give me the second thing). Ok i found a decent job oppurtunity. C# corporation, very nice location, perfect for me because i have a lot of time, not only i can practice but i can earn for stuff. I have a CV or resume just waiting for my friend to give me the email (long story, we have been to that corp because they had open days and only he has the email to the guy, just a easier way)
But there are issiues with it as well so it is not that easy.
If nobody have noticed im dedicated to the science. Basicly 100% scientist that want to make a world a better place.
I messaged a uni specialist so i hope he will be able to help me.
For long time i have thought that i was normal, parent were neglecting my mental health and i had some situations that didnt have good infuence on me as well. I might have some issiues with my brain as well, 96% of aspargers symptoms match, with other links included. I dont want to say i have it but it is a exciuse for a test. In addition to that i cant CANT stop thinking, i even tried not thinking for few minutes, nope i had to think about something everytime. On top of that my biological timer is flipped. I go to sleep at 5 am and wake up at 5pm (when i dont have lectures).
I prefer working at night, at that time my brain at least works normaly but i dont want to disrupt roommates...
And at the day my brain starts the usual, depression, lack of motivation, other bullshit thing.
I might add something later, that is all for now. -
Going back home for the holidays means becoming tech support for pretty much the whole family, unluckly.
As soon as I enter my grandparent's home, my grandpa says "Could you print some emails?". I open his laptop, and I start sweating as soon as I see the Windows XP logo popping up. He (obviously) doesn't remember his password, and the only way to access his (mostly defunct) web mail service is Outlook 2003. For some reason, the web mail provider's POP3 server dies, and i spend half an hour trying to explain it. I ended up leaving with him saying "Why are you even going to a computer engineering university."
Ah, family.1 -
¡rant|rant
Nice to do some refactoring of the whole data access layer of our core logistics software, let me tell an story.
The project is around 80k lines of code, with a lot of integrations with an ERP system and an sql database.
The ERP system is old, shitty api for it also, only static methods through an wrapper to an c++ library
imagine an order table.
To access an order, you would first need to open the database by calling Api.Open(...file paths) (yes, it's an fucking flat file type database)
Now the database is open, now you would open the orders table with method Api.Table(int tableId) and in return you would get an integer value, the pointer.
Now for the actual order. first you need to search for it by setting the search parameter to the column ID of the order number while checking all calls for some BS error code
Api.SetInt(int pointer, int column, int query Value)
Then call the find method.
Api.Find(int pointer)
Then to top this shitcake of an api of: if it doesn't find your shit it will use the "close enough" method of search.
And now to read a singe string 😑
First you will look in the outdated and incorrect documentation given to you from the devil himself and look for the column ID to find the length of the column.
Then you create a string variable with ALL FUCKING SPACES.
Now you call the Api.GetStr(int pointer, int column, ref string emptyString, int length)
Now you have passed your poor string to the api's demon orgy by reference.
Then some more BS error code checking.
Now you have read an string value 😀
Now keep in mind to repeat these steps for all 300+ columns in the order table.
News from the creators: SQL server? yes, sql is good so everything will be better?
Now imagine the poor developers that got tasked to convert this shitcake to use a MS SQL server, that they did.
Now I can honestly say that I found the best SQL server benchmark tool. This sucker creams out just above ~105K sql statements per second on peak and ~15K per second for 1.5 second to read an order. 1.5 second to read less than 4 fucking kilobytes!
Right at that moment I released that our software would grind to an fucking halt before even thinking about starting it. And that me & myself and I would be tasked to fix it.
4 months later and two weeks until functional beta, here I am. We created our own api with the SQL server 😀
And the outcome of all this...
Fixes bugs older than a year, Forces rewriting part of code base. Forces removal of dirty fixes. allows proper unit and integration testing and even database testing with snapshot feature.
The whole ERP system could be replaced with ~10 lines of code (provided same relational structure) on the application while adding it to our own API library.
Best part is probably the performance improvements 😀. Up to 4500 times faster and 60 times less memory usage also with only managed memory.3 -
My boss insists that we shouldn’t lock or password-protect a particular system because, in her words, remembering or write down a password is hard and email as a concept is confusing. I tried to explain if people who don't know what left versus right-clicking do have full admin access, it’s only a matter of time before something goes terriblely wrong. She listened but ultimately decided to keep everything open, confident that everyone would use it responsibly.
Unfortunately, that’s not what happened, it never has been and never will be. The problems started, just as I feared, and now I’m stuck cleaning up the chaos, one issue at a time. I do have a backup and automation snapshots, but things got so tangled up that it will still be a hassle.
I tried soft lock so everyone could only access the section relevant to them. The reaction was immediate—they were confused and stressed, saying they’d be unable to do anything if it stayed that way. They didn’t get the idea that keeping them from touching certain things (that they shouldn't be touching in the first place) wasn’t the same as blocking their whole work. But since they’re all my superiors, I had no choice but to remove the restrictions and leave the system wide open again.
Nothing serious came out, just really annoying because something like this happens all the time.4 -
Hopefully, you already know that the company controlled by the alledged reptiloid subhuman and olimpic testicle juggler formerly known as Mister Zuck My Tits is not to be trusted.
But as is always the case in this bitch, I've been forced into cowjizz flooded swamps' worth of stinking shit platforms for the sake of avoiding isolation.
And so, I've just found yet another way in which Facebook **THUNDERSTRIKE** ... the company, not the geriatric ward, is one of the CROWN ACHIEVEMENTS of human civilization.
Let me tell you something: some people are fucking broke. Hell, some people sleep on the streets, live on scraps, and willingly engage in acts of public defecation when provoked. But I'm not even talking about them no, just plain *broke*.
And so imagine being that guy who doesn't really use his phone much, except maybe for sharing cat pictures with mom because that's what being an absolute chad is all about. You don't get a new phone, because money is a __little__ bit tight. But THEN...
The dreaded CAPITAL strikes, and requests of you to bend and fall onto your knees so as to provide intense, intimate and manual -- as well as oral -- PLEASURE to the [NOT SO] METAPHORICAL PENIS of the """SYSTEM""".
Oh, what an abominable, drooooooling revenant that lies before you!
"Gimme your ass... " he says, menacingly, as you wail about in a futile attempt to guard and preserve the very last vestiges of your own anal virginity.
And so you fight, and kick him in the NADS with everything you have, down to the final shreds of vigor. Victory! Or so you thought...
"You must... " he mutters, mortally wounded "update WhatsApp... "
"Still you breathe?!" you exclaim, suddenly transformed into a heroic, sexy moustachoed arquebusier "After I'm done ~OILING~ my VICTORIOUS CHEST, I *shall* bestow DEATH uppon you!".
But as you rip open your shirt to apply sensual oiling to your marvellous frontal assets, your nemesis reveals it's portentous Portugal: "this new version of Android... " he gasps as he perishes "is incompatible with your device... "
"Ughh! Sacrebleu!" you shriek out in pain, realizing that you are now unable to ACCESS THE FUCKING DATA THAT IS IN YOUR OWN FUCKING HARDWARE BECAUSE OF A STUPID FORCED BINARY INCOMPATIBILITY.
That's right. Now even if I *do* get a new phone, I can't do shit about losing all of the family memes. And contacts and all of that shit, but the stickers are more important. A minor inconvenience, yes, and it didn't need all of this preamble but I was doing the dramatic fight scene bit inside my head as I was writing and I got into it.
Because the only documented way to transfer all of that data is to OPEN THE APPLICATION and scan some code, but everytime I go to do that, IT TELLS ME I NEED TO UPDATE. And every time I GO TO UPDATE, it says that MY PHONE is TOO FUCKING OLD!! AAAAAAAGHGHGHGHGHGHGHG!!!!
And you too, might be a dashing french man from centuries past, with both balls and tits down to your fucking knees, folding your arms in a position that exhumes smugness in a disgustingly irreverent and self-aggrandizing way, looking at me as a mere plebeian who cannot wrap his head around the mystical art of interacting with Google's black deuce box.
And you would be somewhat right in your judgement! But just having to fiddle about with these fucking pocket Elmo screens is such a traumatic experience for me that I'd rather lose my stickers.
[ADBREAK] Are you a debonair victorian undercover butt pirate, taking unparalleled care of your Falstaffian, highfalutin poils pubiens? Need your "sword" sharpened, as you browse through the pages of this magnanimous lexicon? Would you rather allocate final death to your coworkers than learn one more synonym for sonorous, supercilious and pontifical?
We all know that ALL you need to help keep that honor intact is slaying your enemies in high-stakes combat. But how to satisfy less gallant needs, when male prostitution is outlawed in more than sixteen duchies?
Look no further than BloodCurse, the ancient hex that will haunt your family for countless generations! With BloodCurse, you may crawl the earth as a mindless, shameless, piece of shit cockswallowing JUGGERNAUT that craves nothing BUT the consumption of scabbed human ass!
BloodCurse is easily contracted through consumption of the GENITAL fluids of highly-lecherous succubi, conjured through [EXTREMELY CENSORED]! This forbidden arcana allows the user to debour HIS OWN testicles in no time!
Get your bottle of scents, sensual Portuguese chest oils, and fucking designer-drug bath salts for the low, low price of a passionate, unceassing self-blowjob! And use my code FRONTALASSETS for 60% OFF in your next soul-robbing foray into the felational dark arts!
Big ups to BloodCurse for sponsoring this RRRRRRRR~$RRR$$RR%5RRRRR$0000:>A48CC50A E3A1B22A : 330D4750 7C24E5A5|.......*3.GP|$.. 5262E7D5 0D1C24E6 : 85594B39 1CB7593E|Rb......YK9..Y>
:~7 -
Just got access to OpenAI beta. This thing is seriously impressive. The attached image shows it summarizing a paragraph from Friedrich Nietzsche. Apart from that, I have tried summarizing a complex Math Algo which I found on Wikipedia, getting specs for building a new PC, and also improving my Startup Idea. The results were astonishing. I can't imagine what possibilities it can have in the future.
At the same time, I can clearly see why they are not allowing open access to their APIs. The potential for abuse is so high here. Especially when most of our population is full of digital idiots.
-
AndroidOS.
Why: well it's built on Linux kernel so first good thing.
Due to open source everyone can get cheap (under $50) smartphones running on Android with millions of app to access. We can create custom ROMs.
Your one app can target billions of people around the world and so much more...
PS: half of the Play Store apps are shit.4 -
I hate having to deal with our IT service desk. Every time it takes enormous energy to get to the right people and make them understand that no, you are not an idiot, but you actually have a technical issue.
Sure thing they do have a few competent nice folks there too I've gotten to know over time and they indeed have to deal with a ton of dumb non-tech savvy idiots on a daily basis. However, if my job title mentions "software" and "engineer" they should at least assume I'm an idiot in tech. Or something. Every single time I need to open a ticket, even for the simplest "add x to env y", I need to quadruple check that the subject line is moron-friendly because otherwise they would take every chance to respond "nah we can't do that", "that's not us", or "sry that's not allowed". And then I would need to respond, "yes you do:) your slightly more competent colleague just did this for us 2 weeks ago".
Now you might imagine this is on even another level when the problem is complex.
One of our internal apps has been failing because one of the internal APIs managed by a service desk team responds a 500 status code randomly but only when called with a specific internal account managed by another service desk team.
(when I say "managed by", that doesn't mean they maintain it, it just mean they are the only ones who would have access to change something)
Yesterday I spent over a fucking hour writing a super precise essay detailing the issue, proving a million times it's not on our end and that they need to fix it. Now here is an insight to what beautiful "IT service" our service desk provides:
1) ticket gets assigned to a "Connectivity Engineer" lady
2) few hours later she responds and asks me to give her the app and environment IDs and grant her access to those
(naturally everything in my email was ignored including these two IDs)
3) since the app needs to be in prod for the issue, I make a copy isolating the failing part and grant her access to the original "for reference" and the copy to play with
4) few hours later I get an email from the env that some guy called P made changes to the actual app, no changes to the copy
(maybe they immediately fixed the app even though I asked them to only touch the copy)
I also check the env and the live app had been shared with another 2 people giving them editing rights:)
5) another few hours pass and the lady responds that she had been chatting with P (no mention of who tf that guy is) and that P has a suggestion that might work and I should test it, "please see screen shot" for details:
These motherfuckers sent me a fucking screenshot of the env config file where "P has edited a few parameters" that might help. The screenshot had a 16 line part of the config json with a bunch of IDs and Base64 params which HE EDITED LOCALLY.
Again, because I needed a few iterations to realise what I've just witnessed:
These idiots modified some things in the main app (not the copy) for hours. Then came to the conclusion that the config needs some IDs and params updated. They downloaded the config json. Edited it locally. Did not fucking upload it back to the main or test app. Did not test it live. Did not CC in or direct the guy with changes to me. Did not send me the modified config file. Did not even paste the new IDs into the email. But TOOK A FUCKING SCREENSHOT OF THE MODIFIED FILE AND SENT THAT SHIT TO ME. And then had the audacity to ask me to test it when they had access to it and that's literally their fucking job.
I had to compare the fucking screenshot to the live config file and manually type in the changes.
And no, it still doesn't work. And Now I have to get back to them showing it still fails the same way but I just can't deal with these people. Fuck. Was hoping by the time I write it all down it'd be better, and it does feel a bit better, but I still need to get this app fixed. And I can only do it through these... monkeys. I just can't. Talking to these people drains my life energy... I'm just sad. -
iOS is rotting my soul.
I've been a user of iPhone for 6 years now. For the first couple years, I wasnt really mindful of software I use, or I guess I didnt really care. As long as it did the bare minimum, I.e. bank app, call, text, browse, watch youtube vids, I didnt really care. However, in the last couple years, ive become very interested in tech and have worked on small developer projects, spent a lot of time coding in my free time, found really inspiring software and apps on my regular computer that just blow my mind on how advanced they are, and how I, some dumb guy with internet access, can just download it on my PC and use it.
This led me into a kind of software honeymoon phase, where I created a shiny new Github account and started exploring what other cool tools are just out there, available to me for free. My software honeymoon was spent on the beaches and resorts of the open-source software ecosystem. Exploring the gem-bearing caves and beautiful forests of anything from free open-source OCR programs(I needed it to convert my dads manuscript from scanned PDF .jpeg's to actual UTF8 text) to open-source RGB lighting/keymapping software to escape the memory-and-CPU-hungry(and most likely advertising-ID-interested) proprietary software that comes with the brand of mouse/keyboard/controller/etc.
It was like I was a kid exploring Disneyland for the first time or something. But then... then... I got off my computer. Picked up my phone to check notifications. Ew, tinder is blowing up notification center with marketing shit. I go to settings. Notification settings. Tinder's at the bottom so I just want to use a search bar instead of scrolling. There's no search bar. Minor inconvenience. Dark mode isnt dark enough for me. I guess thats just too damn bad, because for the next two hours, I'll have to figure it out by messing with accessibility settings. Time for bed, and I'm just getting plum tired of having to turn on my alarms every night for work the next morning. So I used the 'Automations' app to do it for me. For the next two weeks, at the time specified, 'There was an error running your automation' until I just delete the automation. Browsing through the FaceID settings, I see 'Attention Aware Features'. Cool, maybe now my phone won't automatically dim the screen when im in the middle of reading notifications on my lock screen. Haha, nope still does it. After turning on my alarms, I go to sleep. I wake up an hour late for work because those handy 'Attention Aware Features' silenced my alarm immediately because I fell asleep watching a youtube video.
I could go on and on. Its actually making me feel depressed typing this on my phone, fighting with Apple's primitive autocorrect and annoying implementation of Swype to type.4 -
Bruteforce programming about which I've already ranted earlyer and also let's implement everything in our ms access database and regularly open the DB using the Windows task skeduler.2
-
Because I am very interested in cyber security and plan on doing my masters in it security I always try to stay up to date with the latest news and tools. However sometimes its a good idea to ask similar-minded people on how they approach these things, - and maybe I can learn a couple of things. So maybe people like @linuxxx have some advice :D Let's discuss :D
1) What's your goto OS? I currently use Antergos x64 and a Win10 Dualboot. Most likely you guys will recommend Linux, but if so what ditro, and why? I know that people like Snowden use QubesOS. What makes it much better then other distro? Would you use it for everyday tasks or is it overkill? What about Kali or Parrot-OS?
2) Your go-to privacy/security tools? Personally, I am always conencted to a VPN with openvpn (Killswitch on). In my browser (Firefox) I use UBlock and HttpsEverywhere. Used NoScript for a while but had more trouble then actual use with it (blocked too much). Search engine is DDG. All of my data is stored in VeraCrypt containers, so even if the system is compromised nobody is able to access any private data. Passwords are stored in KeePass. What other tools would you recommend?
3) What websites are you browsing for competent news reports in the it security scene? What websites can you recommend to find academic writeups/white papers about certain topics?
4) Google. Yeah a hate-love relationship, but its hard to completely avoid it. I do actually have a Google-Home device (dont kill me), which I use for calender entries, timers, alarms, reminders, and weather updates as well as IOT stuff such as turning my LED lights on and off. I wouldn"t mind switching to an open source solution which is equally good, however so far I couldnt find anything that would a good option. Suggestions?
5) What actions do you take to secure your phone and prevent things such as being tracked/spyed? Personally so far I havent really done much except for installing AdAway on my rooted device aswell as the same Firefox plugins I use on my desktop PC.
6) Are there ways to create mirror images of my entire linux system? Every now and then stuff breaks, that is tedious to fix and reinstalling the system takes a couple of hours. I remember from Windows that software such as Acronis or Paragon can create a full image of your system that you can backup and restore at any point to get a stable, healthy system back (without the need to install everything by hand).
7) Would you encrypt the boot partition of your system, even tho all data is already stored in encrypted containers?
8) Any other advice you can give :P ?12 -
So I was setting up ELK (Elasticsearch, Logstash and Kibana) all in one EC2 on AWS today for demo purposes. I had everything prepared. Elastic IP, correct security group rules, etc.
I figured I would just do quick test before writing filters and templates if I can access Kibana. So I started service for it and tried to open it with Chrome.
Timeout.
Checked config file. Compared it to documentation. Seemed good but changed some things just for sake of change. Restarted service.
Timeout.
Reverted changes I've made in config. Restarted service. Curl on localhost. It work... OK. 😐
It took me half an hour but finally I figured it out after I took my phone and opened it from there. It was working from the beginning. Stupid company network was for some reason blocking this connection. Fuck! 😡And I was restarting that poor service like crazy trying to fix something that wasn't broken. -
We have 100% access to Unreal Engine 4 Code, but it is not Open Source. so is it legal if we fork it, heavily modify it and re-brand it ?6
-
got first assignment on my first meet on Network Security. it require to pentest one unsecured specified website. yet they don't tell me shit about anything just try it.
i need to :
1. Footprint
2. Scanning
3. Enumeration
4. Gaining Access (previledges raising?) (bonus)
suppose : <target-website> is x
i've done this:
1. whois x
2. got the ipaddress via :
host x
3. nmap -F ip.of.x
my head is already spinning, i need to know what BASICLY each of what i've done. i only get that 'whois' get the information about that domain, 'host' is used to know the target ip address and nmap to find what are the open ports. i don't know what else should i do. need help :(13 -
When the CTO/CEO of your "startup" is always AFK and it takes weeks to get anything approved by them (or even secure a meeting with them) and they have almost-exclusive access to production and the admin account for all third party services.
Want to create a new messaging channel? Too bad! What about a new repository for that cool idea you had, or that new microservice you're expected to build. Expect to be blocked for at least a week.
When they also hold themselves solely responsible for security and operations, they've built their own proprietary framework that handles all the authentication, database models and microservice communications.
Speaking of which, there's more than six microservices per developer!
Oh there's a bug or limitation in the framework? Too bad. It's a black box that nobody else in the company can touch. Good luck with the two week lead time on getting anything changed there. Oh and there's no dedicated issue tracker. Have you heard of email?
When the systems and processes in place were designed for "consistency" and "scalability" in mind you can be certain that everything is consistently broken at scale. Each microservice offers:
1. Anemic & non-idempotent CRUD APIs (Can't believe it's not a Database Table™) because the consumer should do all the work.
2. Race Conditions, because transactions are "not portable" (but not to worry, all the code is written as if it were running single threaded on a single machine).
3. Fault Intolerance, just a single failure in a chain of layered microservice calls will leave the requested operation in a partially applied and corrupted state. Ger ready for manual intervention.
4. Completely Redundant Documentation, our web documentation is automatically generated and is always of the form //[FieldName] of the [ObjectName].
5. Happy Path Support, only the intended use cases and fields work, we added a bunch of others because YouAreGoingToNeedIt™ but it won't work when you do need it. The only record of this happy path is the code itself.
Consider this, you're been building a new microservice, you've carefully followed all the unwritten highly specific technical implementation standards enforced by the CTO/CEO (that your aware of). You've decided to write some unit tests, well um.. didn't you know? There's nothing scalable and consistent about running the system locally! That's not built-in to the framework. So just use curl to test your service whilst it is deployed or connected to the development environment. Then you can open a PR and once it has been approved it will be included in the next full deployment (at least a week later).
Most new 'services' feel like the are about one to five days of writing straightforward code followed by weeks to months of integration hell, testing and blocked dependencies.
When confronted/advised about these issues the response from the CTO/CEO
varies:
(A) "yes but it's an edge case, the cloud is highly available and reliable, our software doesn't crash frequently".
(B) "yes, that's why I'm thinking about adding [idempotency] to the framework to address that when I'm not so busy" two weeks go by...
(C) "yes, but we are still doing better than all of our competitors".
(D) "oh, but you can just [highly specific sequence of undocumented steps, that probably won't work when you try it].
(E) "yes, let's setup a meeting to go through this in more detail" *doesn't show up to the meeting*.
(F) "oh, but our customers are really happy with our level of [Documentation]".
Sometimes it can feel like a bit of a cult, as all of the project managers (and some of the developers) see the CTO/CEO as a sort of 'programming god' because they are never blocked on anything they work on, they're able to bypass all the limitations and obstacles they've placed in front of the 'ordinary' developers.
There's been several instances where the CTO/CEO will suddenly make widespread changes to the codebase (to enforce some 'standard') without having to go through the same review process as everybody else, these changes will usually break something like the automatic build process or something in the dev environment and its up to the developers to pick up the pieces. I think developers find it intimidating to identify issues in the CTO/CEO's code because it's implicitly defined due to their status as the "gold standard".
It's certainly frustrating but I hope this story serves as a bit of a foil to those who wish they had a more technical CTO/CEO in their organisation. Does anybody else have a similar experience or is this situation an absolute one of a kind?2 -
Malwares are nasty applications, that can spy on you, use your computer as an attacker or encrypt your files and hold them on ransom.
The reason that malware exists, is because how the file system works. On Windows, everything can access everything. Of course, there are security measures, like needing administrator permissions to edit/delete a file, but they are exploitable.
If the malware is not using an exploit, nothing is there to stop a user from unknowingly clicking the yes button, when an application requests admin rights.
If we want to stop viruses, in the first place, we need to create a new file-sharing system.
Imagine, that every app has a partition, and only that app can access it.
Currently, when you download a Word document, you would go ahead, start up Word, go into the Downloads folder and open the file.
In the new file-sharing system, you would need to click "Send file to Word" in your browser, and the browser would create a copy of the file in a transfer-partition. Then, it would signal to Word, saying "Hey! Here's a file that I sent to you, copy it to your partition please!". After that, Word just copies the file to its own partition, signals "Ok! I'm done!", and then the browser deletes the file from the shared partition.
A little change in the interface, but a huge change in security.
The permission system would be a better UAC. The best way I can describe it is when you install an app on Android. It shows what permission the app wants, and you could choose to install it, or not to.
Replace "install" with "grant" and that's what I imagined.
Of course, there would be blacklisted permissions, that only kernel-level processes have access to, like accessing all of the partitions, modifying applications, etc.
What do you think?7 -
Have defective supermicro server, but the ipmi is working and could tell me what's going on.
Only problem is, I don't have access to it since the last owner didn't provide it to me.
So I thought let's try metasploit.
Setup local network with a second server, connect to local* address.
"Welcome to intel integrated BMC web console"
What? Its a Supermicro, did the owner reflash the ipmi? What the heck.
Msf: scan adress ....
ipmi found bla bla bla.
Msf: zero cipher scan.
... Voulnerable to zero cipher.
Was pretty happy but the doubt kept creeping in.
On my WS that isn't connected to the ipmi of my server, I go to that ip address.
Bam
"Welcome to intel BMC ......"
MOTHERFUCKER.
What are the odds that some fucker has his ipmi open to the public on that exact same address that my board was configured to.
Well, actually pretty high I guess.
Fuck. Shit.
That didn't go as planned. -
Have a friend who wants to enrich his coding portfolio but is scared of people copying his more serious code if he puts it up on github.
Told him it's all about open source and he could just keep the more casual code up there while giving access to serious projects on request from a company, but it's not very ideal, is it?
What would you tell him?7 -
I can see your local web servers - http://http.jameshfisher.com/2019/...
This article pisses me off so much.
Can someone tell me what's the deal with websites being able to access localhost:3000?
Newsflash, jamesfisher.com:80 is open to everyone on the internetworkz!!1!1!!34 -
I know this is utopic, but I've been thinking for a while now about starting an open source platform for figuring out the problems of our society and finding real world, applicable, open source solutions for them.
To give you some more details, the platform should have two interfaces:
- one for people involved in researching, compiling issues into smaller, concrete chunks that can be tackled in the real world, discuss and try to find workable solutions for the issues and so on
- one for the general public to search through the database of issues, become aware of the problems and follow progress on the issues that people started working on
Of course, anyone can join the platform, both as an observer (and have the ability to follow issues they find interesting) and/or contributor (and actually work with the community to make the world a better place in any way they can).
Each area of expertise would have some people that will manage the smaller communities that would build around issues, much like people already do in the open source community, managing teams to focus on the important thins for each issue. (I haven't found a solution for big egos getting in the way yet, but it would be nice if the people involved would focus on fixing stuff in stead of debating about tabs vs spaces, if you know what I mean).
The goal of this project would be to bring together as many people from all kind of fields to actually try to fix this broken society.
It would be even better if it attracted people with money and access to resources (one example off the top of my head being people like Elon Musk) that could help implement the solutions proposed by the community without expecting to gain profit off of it (profit is also acceptable if it is made in a considerate, fair and helpful way, but would not be promoted on the platform).
The whole thing would be voluntary work; no salary, no other commitment than the personal pledge that once someone chooses to tackle something, he/she will also see it trough (or at least do his/her best).
The platform would be something like a mix of real time communication, issue tracker, project management tool and publishing platform.
I don't yet have all the details for how it should all fit together, but if there is something that I would like to start, this is definitely it!
PS: I don't think I can ever do something like this by myself, and I don't really have the time to manage a community of developers to start work on it right now. But if you guys think something like this is something worth your time, I will make time and at least start on defining the architecture and try to turn this into a real project.
If enough people are interested, I will drop any other side projects and do my best to get this into the world!
Thank you for reading :)6 -
So I just installed Android 11 on my OnePlus 6T with the 18.0 release of LineageOS. Screen recorder built-in that can finally record system sound and play it too (there used to be a Magisk module but that couldn't play system sound while recording it, everything else is just through the mic) and some doodads like the selection for where to blast your music into has been moved more into view... Epic.
And then comes the Scoped Storage. Oh boy were the Android devs right to hate the guts out of it. It's so fucking slow. Seriously, on that exact device with Android 10, blazing fast. That storage is far from cooked. On Android 11.. have a directory with a thousand or so files, and it takes 5 goddamn seconds to open the directory with them in it. And even with external file managers that you give storage access like usual! Except when you root your device and use a root file manager, then it's fast again. Because that's using the shell instead.
I never thought I'd be able to say this to be honest. The shell is faster than the native tools. Let that sink in for a moment. The shell is faster than the native tools. How on Earth did Google think that this is tolerable?! For security, are you kidding me? Yeah I'll just use the root account for fucking everything in all that security, to have a functioning system!
Android 10 was also initially planned to have this terrible storage system, but due to developer backlash, Google waited a release and it was optional there. That wasn't just time for developers to adapt to Scoped Storage. That should've also been time for Google to actually make it usable.8 -
Hi All !!!
Woah this is my first Post after 3 years not opening this website.
i don't know why.
but maybe between 2017-2020 my live got better so i don't think will have any Rant again.ahahaha *kidding
but today i see email, that i got sticker from devRant, woah i think i will go to devRant again.
wow devRant more cool than before , i don't think this website still open. i just want to check it. i forgot my password too. but luckily still got an access to my email.
So i want to tell a story about this weekly Rant,
Family Support? what the he** is it.
my family only look for money.
at my first job finding, i always pushed for find work in Factory/Oil/Goverment that will give a BIG money.
my first reaction to this i tell i won't do that. but overtime i think i will not talk about it again.
i just want to get Dev Job anywhere.
i don't know if this is the meaning of passion or something like that.
but from the first time , i try hard to get job only is software development.
and hey Maybe my Pray Listened by Almighty God.
so i got my first job as Fullstack developer that luckily accept me as self taught software developer. i don't have any formal education.
actually i only learn software dev from Lynda.com(not promotion) .
i learn algorithm, pseudocode . then i got passed the test of psudocode.
Then because the money is good in there. my parent just accept my first job. not complaining again till now..
maybe this is what they called ikigai??
i love software development so much....
but still i always have a Rant every day about it.
someday you like it, someday you hate it.
someday yo miss it, someday you regret it.
maybe that what is called Love.Damn... -
Wrote this on another thread but wanted to do a full post on it.
What is a game?
I like to distinguish between 1. entertainment, 2. games, 3. fun.
both ideally are 'fun' (conveying a sense of immersion, flow, or pleasure).
a game is distinct (usually) from entertainment by the presence of interaction, but certain minimalists games have so little decision making, practice, or interaction-learning that in practice they're closer to entertainment.
theres also the issue of "interesting" interaction vs uninteresting ones. While in broad terms, it really comes down to the individual, in aggregate we can (usefully) say some things, by the utility, are either games or not. For example if having interaction were sufficient to make something a game, then light switches could become a game.
now supposed you added multiple switches and you had to hit a sequence to open a door. Now thats a sort of "game". So we see games are toys with goals.
Now what is a toy?
There are two varieties of toy: impromptu toys and intentional toys.
An impromptu toy is anything NOT intended primarily, by design, to induce pleasure or entertainment when interacted with. We'll call these "devices" or "toys" with a lowercase t.
"Toys", made with the intent of entertainment (primarily or secondarily) we'll label with an uppercase T.
Now whether something is used with the intent behind its own design (witness people using dildos, sex toys, as slapstick and gag items lol), or whether the designer achieves their intent with the toy or item is another matter entirely.
But what about more atmospheric games? What about idle games? Or clickers?
Take clickers. In the degenerate case of a single button and a number that increases, whats the difference between a clicker and a calculator? One is a device (calculator) turned into an impromptu toy and then a game by the user's intent and goal (larger number). The second, is a game proper, by the designers intent. In the degenerate case of a badly designed game it devolves into a really shitty calculator.
Likewise in the case of atmospheric games, in the degenerate case, they become mere cinematic entertainment with a glorified pause/play button.
Now while we could get into the definition of *play*, I'll only briefly get into it because there are a number of broad definitions. "Play" is loosely: freely structured (or structured) interaction with some sort of pleasure as either the primary or secondary object, with or without a goal, thats it. And by this definition you can play with a toy, you can play a game, you can play with a lightswitch, hell you can play with yourself.
This of course leaves out goals, the idea of "interesting decisions" or decision making, and a variety of other important elements.
But what makes a good game?
A lot of elements go into making a good game, and it's not a stretch to say that a good game is a totality of factors. At the core of all "good" games is a focus on mechanics, aesthetics, story, and technology. So we can already see that what makes a good game is less of an either-or-categorization and more like a rating or scale across categories of design elements.
Broadly, while aesthetics and atmosphere might be more important in games like Journey (2012) by Thatonegamecompany, for players of games like Rimworld the mechanics and interactions are going to be more important.
In fact going a little deeper, mechanics are usually (but not always) equivalent to interactions. And we see this dichtonomy arise when looking at games like Journey vs say, Dwarf Fortress. But, as an aside, is it possible to have atmospheric games that are also highly interactive or have a strong focus on mechanics? This is often what "realistic" (as opposed to *immersive*) games try to accomplish in design. Done poorly they instead lead to player frusteration, which depending on player type may or may not be pleasureable (witness 'hardcore' games whos difficulty and focus on do-overs is the fun the game is designed for, like roguelikes, and we'll get to that in a moment), but without the proper player base, leads to breaking player flow and immersion. One example of a badly designed game in the roguelike genre would be Early Access Stoneshard, where difficulty was more related to luck and chance than player skill or planning. A large part of this was because of a poorly designed stealth system, where picking off a single enemy alerted *all enemies* nearbye, who would then *stay* alerted until you changed maps, negating tactics that roguelike players enjoy and are used to resorting to. This is an important case worth examining because it shows how minor designer choices in mechanical design can radically alter the final quality of the game. Some games instead chose the cheaper route of managing player *perceptions* with a pregame note: Darkest Dungeons and Amnesia TDD are just two I can think of.11 -
I don't understand windows 10 "Quick Access" (when you open windows file manager). I open One very less used folder and it stays in quick access for approx. 10 days and I open my Project folder everyday, every hour, evry minute and every second, it doesn't shows up in quick access, and when sometimes does, it doesn't stays long.9
-
I feel like writing or telling people about the time I jumped from Windows 7 Ultimate and jumping to Windows 10. (I'm not against 10, but I'm never updating after what had happened to me)
It all starts when none of my games will play due to a possible issue with my graphics card. I look up "3D source game bug" and not many results pop up. I go on Microsoft's Qna areas and ask this question but to my surprise nothing they say would make sense. "Clean the pins of your graphics card, make sure you verify the games on Steam". I verified the games and they checked out as perfectly fine. I don't have access to my graphics card because this is a laptop, sadly not a tower.
Two months pass and my computer is already showing signs of stress, like it didn't want to live in a sense. It was three times slower than when I was on Windows 7 and it was unallocating areas of my main hard drive where I could make virtual hard drives.
Instantly I start looking up Linux distros and find Linux Mint. 17.3 was the current version at the time. I downloaded it and burned it onto a DVD-rom and rebooted my computer. I loaded into the disc and to my surprise it seemed almost like Windows 7 apart from the Linux part. I grab my external hard drive and partition it to hold the Linux distro and leave it plugged in incase Windows 10 does actually fail.
On December 19, a few months after Windows 10 had released. I start my laptop to try and continue my studies in video game development. But to my surprise, Windows 10 had finally crashed permanently. The screen flickered blue and black, and an error box saying Loginui.exe failed to start. I look at it for a solid minute as my computer had just committed suicide in a sense.
I reboot thinking it would fix the error but it didn't. I couldn't log in anymore.
I force shutdown the laptop and turn it back on putting it into safe mode.
To my surprise loginui.exe works and I sign in. I look at my desktop, the space wallpaper I always admired, the sound files, screen shots I had saved.
I go into file explorer and grab everything out of my default hard drive Windows was installed on. Nothing but 400gb got left behind and that was mainly garbage prototypes I had made and Windows itself. I formatted my external hard drive and placed everything on it. Escaping Windows 10 with around 100GB of useful data I looked at the final shutdown button I would look at.
I click it and try to boot into normal Windows 10. But it doesn't work. It flickers and the error pops up once more.
I force it to shutdown and insert the previous Linux Mint disc I made and format the default hard drive through Linux. I was done. 10 gave me a lot of shit. Java wouldn't work, my games has a functional UI but no screen popped up except a black abyss and it wouldn't even let me try to update my graphics card, apparently my AMD Radeon 5450 was up to date at the AMD Radeon 5000's.
I installed Linux Mint and thinking the games would actually play I open steam and Launch Half-Life 2 to check if Linux would be nicer to me than Windows 10 had been.
To my surprise the game ran. The scene from Highway 17 popped on screen and the UI was fully functional. But it was playing at 10-15fps rather than the usual 60-70fps. Keep look at my drivers and see my graphics card isn't in use. I do some research and it turns out I have a Hybrid Laptop.
Intel HD Graphics and an AMD Radeon 5450 and it was using the Intel and not the AMD. Months of testing and attempts of getting the games to work at high frame rates pass and the Damn thing still functions at a low terrible fps. Finally I give up. I ask my mom for a Windows 7 disc and she says we can't afford it. A few months pass and I finally get a Windows 7 installation disc through money I've saved up. Proudly I put it into my optical disc drive and install it to my main hard drive deleting Linux completely. I announced to all my friends my computer was back in working order and I install everything I needed, Steam, Skype, Blender, and Unity as well as all my games. I test Half-Life 2 and it's running exceptionally smoothly, I test Minecraft at max settings and it's working beautifully. The computer was functioning properly once again and my life as a developer started as I modeled things and blender, learned beginners C# and learned a lot of Batch. Today the computer still runs at a great speed and I warn others of what happened to me after I installed Windows 10 to my machine if they are thinking of switching from 7 or 8 on an older machine.
Truly the damage to my data cannot be undone. But the memory of the maintenance, work, tests, all are a memory of how Windows 10 ruined me and every night before the one year anniversary of Windows 10's release, I took out the battery of my laptop and unplugged it from the a.c. power, just so Windows 10 doesn't show it's DLLs, batch scripts, vbs scripts, anything on my computer. But now, after this has happened and I have recovered, I now only have a story to tell5 -
I'd like to make an open source data registry, with an easy to access API. For example, perhaps I'd like to list all cities and postal codes in France, or perhaps get the number of dogs in Canada. Any ideas how to structure the open source part? How can people contribute? Should it use external APs?2
-
I recently went to an office to open up a demat account
Manager: so your login and password will be sent to you and then once you login you'll be prompted to change the password
Me: *that's a good idea except that you're sending me the password which could be intercepted* ok
Manager: you'll also be asked to set a security question...
Me: *good step*
Manager: ...which you'll need to answer every time you want to login
Me: *lol what? Maybe that's good but kinda seems unnecessary. Instead you guys could have added two factor authentication* cool
Manager: after every month you'll have to change your password
Me : *nice* that's good
Manager: so what you can do change the password to something and then change it back to what it was. Also to remember it keep it something on your number or some date
Me: what? But why? If you suggest users to change it back to what it was then what is the point of making them change the password in the first place?
Manager: it's so that you don't have to remember so many different passwords
Me: but you don't even need to remember passwords, you can just use softwares like Kaspersky key manager where you can generate a password and use it. Also it's a bad practice if you suggest people who come here to open an account with such methods.
Manager: nothing happens, I'm myself doing that since past several years.
Me: *what a fucking buffoon* no, sir. Trust me that way it gets much easier to get access to your system/account. Also you shouldn't keep your passwords written down like that (there were some password written down on their whiteboard)
Manager: ....ok...so yeah you need sign on these papers and you'll be done
Me:(looking at his face...) Umm..ok4 -
When the ops team needs to go through a 5 step "protocol" over a couple of days, just to open a damn port in the firewall, so that our CI server can access the local GitLab server..
Seems like the migration of the last couple of projects from SVN to Git is going to take a little longer than I expected.. -
RabbitMQ's claim "RabbitMQ is the most widely deployed open source message broker."
They should amend that line to read "..unless you are trying to install on Windows, then you're screwed .ha ha ha ha"
Two hours fighting permissions, missing (and wrong) paths, having to modify *their* batch files, and still can't access the management UI (and yes, the mgmt plugin is enabled).
I hate this 'shaving the yak' exercise.15 -
Bored at the office. Company is done for. I'm spending my last days here, doing nothing, waiting for my new position to start. There's only that much you can read on devRant, and SO MUCH MORE you could do writing code. But I just can't decide what to do and as a result sit here doing nothing. Help me out please! Answer with the most points will be the thing I'll start with on Monday, while today I think I'll just crack open a cold one.
My initial variants:
1. Learn Electron by playing with Electron React+Redux basic boilerplate, in order to make a simple personal blogging app.
2. Complete some of the 20 courses that I bought on Udemy 6 months ago.
3. Write the back-end logic for my Raspberry PI controlled systems at home (to control it remotely I'll make a hosted API that RPI will access to get input for it to decide what to do).
4. Solve problem 51 on projecteuler.net with an algorithm that runs less than 20 seconds.
Other suggestions are welcome.1 -
Fuckin McAfee tried installing it and asks me for a restart. After that the application fails to open up a process is clearly running in the background however nothing to show.
Tried the have you turned it off and on again procedure atleast 5 times but nothing.
Finally tried contacting McAfee support. Asks me to give them remote access via their application. The link stayed there like a dummy. Clicking it opened nothing. After the chat got disconnected 3 times.
Then when i try reinstalling it it says we are in the middle of an installation and we'll open that up. It opens a fuckin take a tour box and ypu can fuckin click anywhere and everywhere on the window but it stays there sitting, waiting, watching
Fuckin intel and fuckin McAfee get your shit together2 -
open source this, open source that… do you realize that you have no way of verifying whether the “cloud” version of a self-hostable tool is identical to what’s on github? they might as well have a special version of their app running on their servers, filled with spyware.
They don’t need it though, because you never read the code in the first place. Spyware might as well be there, in plain sight, never to be discovered by you because they know people don’t read source code.
Also, when are you going to get it hosted? Because cloud is just someone else’s computer, remember that. If someone else has unrestricted physical access to your computer, it’s not your computer anymore. Your hoster can see everything that happens on your VPS.
Unless you’ve read the code and hosting it from your own home from your own physical server, it’s not your data. Check with your data provider — they often do offer fixed IP service for a small fee.
I host my own tools on my computer and let my phone sync with them through my home wifi. Yes, I can’t sync shit when I’m out there with my phone, but who needs that, I’ll just do that when I come home.
I’m about to vibe-audit the source code of Notesnook with AI!12 -
Data wrangling is messy
I'm doing the vegetation maps for the game today, maybe rivers if it all goes smoothly.
I could probably do it by hand, but theres something like 60-70 ecoregions to chart,
each with their own species, both fauna and flora. And each has an elevation range its
found at in real life, so I want to use the heightmap to dictate that. Who has time for that? It's a lot of manual work.
And the night prior I'm thinking "oh this will be easy."
yeah, no.
(Also why does Devrant have to mangle my line breaks? -_-)
Laid out the requirements, how I could go about it, and the more I look the more involved
it gets.
So what I think I'll do is automate it. I already automated some of the map extraction, so
I don't see why I shouldn't just go the distance.
Also it means, later on, when I have access to better, higher resolution geographic data, updating it will be a smoother process. And even though I'm only interested in flora at the moment, theres no reason I can't reuse the same system to extract fauna information.
Of course in-game design there are some things you'll want to fudge. When the players are exploring outside the rockies in a mountainous area, maybe I still want to spawn the occasional mountain lion as a mid-tier enemy, even though our survivor might be outside the cats natural habitat. This could even be the prelude to a task you have to do, go take care of a dangerous
creature outside its normal hunting range. And who knows why it is there? Wild fire? Hunted by something *more* dangerous? Poaching? Maybe a nuke plant exploded and drove all the wildlife from an adjoining region?
who knows.
Having the extraction mostly automated goes a long way to updating those lists down the road.
But for now, flora.
For deciding plants and other features of the terrain what I can do is:
* rewrite pixeltile to take file names as input,
* along with a series of colors as a key (which are put into a SET to check each pixel against)
* input each region, one at a time, as the key, and the heightmap as the source image
* output only the region in the heightmap that corresponds to the ecoregion in the key.
* write a function to extract the palette from the outputted heightmap. (is this really needed?)
* arrange colors on the bottom or side of the image by hand, along with (in text) the elevation in feet for reference.
For automating this entire process I can go one step further:
* Do this entire process with the key colors I already snagged by hand, outputting region IDs as the file names.
* setup selenium
* selenium opens a link related to each elevation-map of a specific biome, and saves the text links
(so I dont have to hand-open them)
* I'll save the species and text by hand (assuming elevation data isn't listed)
* once I have a list of species and other details, to save them to csv, or json, or another format
* I save the list of species as csv or json or another format.
* then selenium opens this list, opens wikipedia for each, one at a time, and searches the text for elevation
* selenium saves out the species name (or an "unknown") for the species, and elevation, to a text file, along with the biome ID, and maybe the elevation code (from the heightmap) as a number or a color (probably a number, simplifies changing the heightmap later on)
Having done all this, I can start to assign species types, specific world tiles. The outputs for each region act as reference.
The only problem with the existing biome map (you can see it below, its ugly) is that it has a lot of "inbetween" colors. Theres a few things I can do here. I can treat those as a "mixing" between regions, dictating the chance of one biome's plants or the other's spawning. This seems a little complicated and dependent on a scraped together standard rather than actual data. So I'm thinking instead what I'll do is I'll implement biome transitions in code, which makes more sense, and decouples it from relying on the underlaying data. also prevents species and terrain from generating in say, towns on the borders of region, where certain plants or terrain features would be unnatural. Part of what makes an ecoregion unique is that geography has lead to relative isolation and evolutionary development of each region (usually thanks to mountains, rivers, and large impassible expanses like deserts).
Maybe I'll stuff it all into a giant bson file or maybe sqlite. Don't know yet.
As an entry level programmer I may not know what I'm doing, and I may be supposed to be looking for a job, but that won't stop me from procrastinating.
Data wrangling is fun. 1
1 -
I'm about to embark on an AWS security journey... Gonna find out who has global ssh access open, who hasnt been rotating their master keys, who has lambda connected to an IGW, who has VPC's with a VPN that also have an open SSH machine to the world.
Anything else i should look for?6 -
These github assholes really shat the fan when selling out to M$. I'm trying to access an open source project. I can't. Apparently I'm IP banned. I never go there beside to download software once in a while.
Motherfuckers.4 -
I have just slept for a minimum of 5 hours. It is 7:47 PM atm.
Why?
We have had a damn stressful day today.
We have had a programming test, but it really was rather an exam.
Normally, you get 30 minutes for a test and 45 minutes for an exam.
In this "test" we have had to explain what 'extends' does and name a few advantages of why one should use it.
Check.
Read 3 separate texts and write the program code on paper. It was about 1 super class and 1 sub class with a test class in Java.
Check.
Task 3: Create the UML diagram of the code from above. *internally: From above? He probably means my code since there is no other code there. *Checks time*. I have about 3 minutes left. Fuck my life.*
Draws the boxes. Put the class names in each of them. A private attribute for the super class.
Teacher: Last minute!
Draw the arrow starting starting from the sub class to the super class.
Put my name on each written paper. And mentally done for the day. Couldn't finish the last task. Task 3.
During this "test", I heard the frustrations of my classmates. Seemed like everyone was pretty much pissed.
After a short discussion with the teacher who also happens to be the physics professor of a university nearby.
[If you are reading this, I hope that something bad happens to you]
The next course was about computer systems. Remember my recent rant about DNS, dhcp, ftp, web server and samba on ubuntu?
We have had the task to do the screenshots of the consoles where you proof that you have dhcp activated on win7 machine etc. Seemed ok to me. I would have been done in 10 minutes, if I would be doing this relaxed. Now the teacher tells us to change the domain names to <surnameOfEachStudent>.edu.
I was like: That's fine.
Create a new user for the samba server. Read and write directories. Change the config.
Me: That should be easy.
Create new DNS entries in the configs.
Change the IPv6 address area to 192.168.x.100-200/24 only for the dhcp server.
Change the web server's default page. Write your own text into it.
You will have 1 hour and 30 minutes of time for it.
Dumbo -ANGRY-CLIENT-: Aye. Let us first start screenshotting the default page. Oh, it says that we should access it with the domain name. I don't have that much time. Let us be creative and fake it, legally.
Changes the title element so that it looks like it has been accessed via domain name. Deletes the url and writes the domain name without pressing Enter. Screenshot. Done. Ok, let us move to the next target.
Dhcp: Change lease time. Change IP address area. Subnet mask. Router. DNS. Broadcast. Optional domain name. Save.
Switches to win7.
ipconfig /release
ipconfig /renew
Holy shit it does not work!
After changing the configs on ubuntu for a legit 30 minutes: Maybe I should change the ip of the ubuntu virtual machine itself. *me asking my old self: why did not you do that in the first place, ass hole?!*
Same previous commands on win7 console. Does not work. Hmmm...
Where could be the problem?
Check the IP of the ubuntu server once again. Fml. Ubuntu did not save when I clicked on the save button the first time I have changed it. Click on save button 10 times to make sure it really is saved now lol.
Same old procedure on win7.
Alright. Dhcp works. Screenshot.
Checks time. 40 minutes left.
DNS:It is your turn. Checks bind9 configs. sudo nano db.reverse.edu.
sudo nano db.<mysurname>.edu.
Alright. All set. It should work now.
Ping win7 from ubuntu and vice versa. Works. Ping domain name on windows 7 vm. Does not work.
Oh, I forgot to restart the bind9 server on ubuntu.
sudo service bind stop
" " " start
Check DNS server IP on win7. It looks fine.
It still doesn't work. Fuck it. I have only 20 minutes left. Samba. Let us do this!
10 minutes in. No result. I don't remember why. I already forgot why I have done for it. It was a very stressful day.
Let us try DNS again.
Oh shit. I forgot the resolver!
sudo nano /etc/resolv.conf
The previous edits are gone. Dumb me. It says it in the comments. Why did not I care about it. Fuck it.6 minutes left. Open a yt video real quick. Changes the config file. Saves it. Restarts DNS and dhcp. Closes the terminal and opens a new one. The changes do not affect them until you reopen them. That's why.
Change to win7.
Ping works. How about nsloopup.
Does not work.
Teacher: 2 minutes left!
Fuck it.
Saves the word document with the images in it. Export as pdf. Tries to access the directories of the school samba server. Does not work. It was not my fault tho. Our school server is in general very slow. It feels like they are not maintained and left alone like this in the dust from the 90s.
Friend gets the permission to put his document on a USB and give the USB to the teacher.
Sneaky me: Hey xyz, can you give me your USB real quick?
Him: sure.
Gets bombed with "do you want to format the USB?" pop-ups 10 times. Fml. Skips in a fast way.
Transfers the pdf. Plug it out. Give it back.
After this we have had to give a presentation in politics. I am done.6 -
This is the story of probably the least secure CMS ever, at least for the size of it's consumer base. I ran into this many years ago, before I knew anything about how websites work, and the CMS doesn't exist anymore, so I can't really investigate why everything behaved so strangely, but it was strange.
This CMS was a kind of blog platform, except only specially authorised users could view it. It also included hosting. I was helping my friend set it up, and it basically involved sending everybody who was authorized a email with a link to create an account.
The first thing my friend got complaints about was the strange password system. The website had two password boxes, with a limit of (I think) 5 characters each. So when creating a account we recomended people simply insert the first 5 characters in the first box, and the rest in the second. I can not really think of a good explanation for this system, except maybe a shitty way to make sure password are at least 5 characters? Anyway, since this website was insecure the password was emailed to you after the account was created. This is not yet the WTF part.
The CMS forced sidebar with navigation, it also showed the currently logged in users. Except for being unreadable due to a colorful background image, there where many strange behaviors. The sidebar would generally stay even when navigating to external websites. Some internal links would open a second identical sidebar right next to the third. Now, I think that the issue was the main content was in an iframe with the sidebar outside it, but I didn't know about iframe's back then.
So far, we had mostly tested on my friends computer, which was logged in as the blog administrator. At some point, we tried testing with a different account. However, the behavior of sidebars was even stranger now. Now internal links that had previously opened a second, identical sidebar opened a sidebar slightly different from the first: One where the administrator was logged in.
We expirimented somewhat, and found that by clicking links in the second sidebar, we could, with only the login of a random user, change and edit all the settings of the site. Further investigation revealed these urls had a ending like ?user=administrator2J8KZV98YT where administrator was the my friends username. We weren't sure of the exact meaning of the random digits at the end, maybe a hash of the password?
Despite my advice, my friend decided to keep using this CMS. There was also a proper way to do internal links instead of copying the address bar, and he put a warning up not to copy links to on the homepage. Only when the CMS shut down did he finally switch to a system where formatting a link wrong could give anybody admin access. -
A thing that I am annoyed that people are getting wrong is security by obscurity.
You have heard of it and being told it is bad. It is so bad that it alone is a counter argument. Let me set you straight:
>>>Security by obscurity is the best security you will ever have<<<
There is an asterisk: It is probably not right for your business. But that is for the end.
Security by obscurity means to hide something away. Most security is based on hiding. You hide your private key or your password or whatever other secret there is. If you had a 2048 long sequence of port knocking, that would be fine, too.. Or it would be fine if it wasn't observable. You could write this down in your documentation and it wouldn't be security by obscurity. It would just be security. Weird, but fine.
The real meat of obscurity is: No one knows that there is someone. The server you port knock looks like a harmless server, but suddenly has an open port to a bad application for an IP, but only if that IP went to 25 other ports first.
In the animal kingdom, there are different survival strategies. One of them is being an apex predator or at least so big and lumbering that no predator wants a piece of you. That's our security. It is upstream security. It is the state.
But what is the rest of the animal kingdom going to do? Well, run away. That works. Not being caught. And those not fast enough? Hide! Just be invisible to the predators. They cannot triple check every leaf and expect to be done with the tree before starving. That's security by obscurity. Or hide in the group. Zebras. Easy to see, hard to track in the group. Look like everyone else.
There is a reason why drug smugglers don't have vaults in the carry-on. Arrive at the customs and just refuse to open the vault. If the vault is good enough. Nope, they lack the upstream security by the state. The state is there enemy, so they need obscurity rather than cryptographic safety.
And so, for a private person, having a port knocking solution or disguising a service as another service is a great idea.
Every cryptography course happily admits that the moment they can catch you physically, cryptography is useless. They also teach you about steganography. But they omit to tell you that obscurity is the second best solution to having a stronger army when you cannot rely on your state as upstream security.
Why did I say, not a good idea for companies?
1. It is self-defeating, since you have to tell it to all employees using it. A shared secret is no secret. And therefore it cannot be documented.
2. It makes working with different servers so much harder if there is a special procedure for all of them to access them. Even if it were documented. (See 1.)
3. You're a company, you are advertising your services. How to hide that you run them?
Do you see how those are not security relevant questions? Those are implementation relevant questions.
Here is an example:
Should you have your admins log into servers as normal users before elevating to root or is that just obscurity? Well, not for security purposes. Because that foothold is so bad, if compromised, it makes little difference. It is for logging purposes, so we have a better server log who logged in. Not only always root. But if our log could differentiate by the used private key, there is no issue with that.
If it is your private stuff, be creative. Hide it. Important skill. And it is not either, or. Encrypt it your backup, then hide it. Port knock, then required an elliptic curve private key to authenticate.
It is a lot of fun, if nothing else. Don't do it with your company. Downsides are too big. Cheaper to hire lawyers if needed.1 -
ZTNA is just reinventing the wheel. Yeah, we open all our shit to the outside and let some client do some checks to grant you access. WE HAD THAT SHIT FOR AGES! ITS A VPN TUNNEL TO OUR SELF HOSTED SHIT THAT YOU HAVE TO LOGIN ANYWAY. Its just like someone in security marketing decided to put a name on something you should be doing anyway. Especially clientless ZTNA, thats just a reverse proxy with an auth header.
Man, cybersecurity lately just feels like sales just trying to sell you best practices and AI instead of actually usable software!1 -
I want to open a private rehab where I would delete your social media accounts, take your phone/laptop/internet access away, get you treated by a psychiatrist, make you take your pills on time every time, make you work, then spend your free time on quality things like reading books or making art, or exercising, or just sleeping, and when you disobey and say this and that — I'll beat you with a fucking whip. Oh, and you'll have a normal balanced diet with no junk food, sugar or sweeteners.
I swear to god that 90% of people's problems are solved by therapy followed by cattle prodding.9 -
These days i like to think of our data privacy as that of an amazon package delivery between person A to B
- Person A wants a packet of condoms and guns, but don't want society to know about it
- person B wants to send guns and condoms to B
- Amazon is willing to provide transportation with a pinky promise that it won't tell anyone about the delivery.
- Thus B gives the condoms and guns to Amazon wrapped up in hard box hoping that Amazon or anybody else won't open it. Similarly A receives the packet hoping that nobody else got to know about it.
But the problem is a LOT of people could possibly know of the contents, even if A or B aren't willing to share details
- Amazon can look into it.
- government can stop the amazon car transporting the packet and force them to look into it.
- some 3rd person(aka hacker) could fool the delivery truck and get access to packet contents.
=======================================
and this morning, my neighbour, A very radical hindu supporter, frustrated by the recent tablighi jamaat fuck-up , gave a very strange statement "you know in future, the government would pass a law which will allow them to hear these ppl's calls /whatsapp messages. This will allow government to detect and take actions on every of these anti-national scums"
I wanted to say WHAT THE FUCK ARE YOU HOPING FOR, BOOMER? THAT'S CENSORSHIP!! but i couldn't say because his illiterate vision is no longer a hope, i can see it becoming reality.
Personally i am equally angry with that whole incident and how that community handled it. But how can anyone ask for censorship, just because a few elements misused it? The problem lies with thise elements and people who support their thoughts not the whole community or the communication medium.
From what i have heard in the recent US and indian law news, they are essentially trying to peek into the data we send to each other legally.
So going by the package delivery analogy, its like government now wants to have every amazon delivery happen in transparent boxes in a transparent truck, just because a few people ordered illegal items via amazon delivery.
This world is going crazy and stupid.3 -
Hey Guys
So... I Have a question / rant / frustrated commenting to do...
WHY THA FUCK DO FIRMWARE TAKE SO LONG TO UPDATE!!!
been configuring my webserver and 2 p2p cameras to access from the outside, and for each click or change can take 1 to 5 minutes to implement...
And then, like 6 or 7 hours latter I notice that everytime the port wasn't associated, a small label in like size8 text shows that port is already in use...
And... Da FUCK??
I'm associating the ports myself... how can port 82, 83, 84, 85, 86, ... be In use?
I have my server in 80, WebDav e another non relevant port, and trying to find open ports for the p2p cams...
Fuck I'll just delete all that services that no one uses and are pre configured, like, emule? napster? FifaPC? WTF? I never played Fifa, don't like socker. KaZaA SERVER? WTF why does this shit comes pre-configured?
Btw I'm writing this while I wait for the router to finish every time :p7 -
An app I'm making for a client currently has 23 "pages" that are simply web views.
Most of those pages have A HREFS which open other pages (some external pages that I have no access to as a developer).
Of course, some of the links aren't HREFS and are javascript calls to change the content on the screen without going to another page. So the user thinks they have gone to another web page when then system doesn't recognise it as another page...
Additional to this, there are multiple versions of the pages depending on which language the user has selected in the app.
And nobody seems to have considered how the default back button handles all these possible eventualities (whether it can go back to previous web page, IF it was an HREF and not just JS mimicking a new page (and how would my webview even catch that), and of course IF the language hasn't changed during the user journey etc etc)
Am I wrong for being annoyed about this? Am I the dick for not developing a clean solution to it? Or am I justified because webviews have no place inside an app!
I'm sort of hoping apple deny this app due to too many web views :S8 -
Holy fuck I'm tired of domain.com... I bought my domain with them about a year ago, and quickly I discovered how shit they are.
I can almost never access the console, the default view most of the time loads, although even that is incredibly slow. When the console loads, all settings regarding my domain are just loading. Every once in a blue moon I can actually access the settings and do something.
I got tired of it, and started transferring the domain to Cloudflare. That's where I messed up, and didn't know I had to verify the transfer twice, so the domain ended up expiring during the transfer process. Now domain.com has my domain completely locked down, pointing it to one of those 'expired' nameservers.
So three days ago I thought fuck it, I'll pay domain.com to renew the domain, maybe that'll get the domain transferred, or at least get my domain open again, so I can receive emails again, because in all my nerdiness I decided to set up a custom email using 'name@customdomain.com'. So I haven't been able to receive any emails for two weeks now.
Anyway, three days later the status of the domain is still 'pending renewal', and I can't for the life of me figure out how something like this isn't completely automated, and the domain isn't just working again.
So just now I decided to contact their live chat, and even they can't change the nameservers on my domain, and I have to be transferred to a specialist, who will then contact me by mail within 24-48 hours. Fuck I hate domain.com, and I'll certainly never buy from them again4 -
i just released my first open source project with effort to make a comprehensible documentation for others to use as well as repetitive refactoring to not embarrass myself.
i am equally excited and knowing no one will care about that.
it is based on my effort to make my companies workflow more effective, knowing well this is just a temporary solution in advance to a professional developed system as opposed to having no system at all. so all of this work will fade into oblivion eventually.
i felt this has been too much work just to be forgotten someday so i cling to my naive hope someone might benefit from that and maybe i get one or three internet points.
in case someone is interested in a free quality management software for document control and access with no real state of art, you might find it interesting to visit my qualitymanagement repo4 -
It's 2022 and mobile web browsers still lack basic export options.
Without root access, the bookmarks, session, history, and possibly saved pages are locked in. There is no way to create an external backup or search them using external tools such as grep.
Sure, it is possible to manually copy and paste individual bookmarks and tabs into a text file. However, obviously, that takes lots of annoying repetitive effort.
Exporting is a basic feature. One might want to clean up the bookmarks or start a new session, but have a snapshot of the previous state so anything needed in future can be retrieved from there.
Without the ability to export these things, it becomes difficult to find web resources one might need in future. Due to the abundance of new incoming Internet posts and videos, the existing ones tend to drown in the search results and become very difficult to find after some time. Or they might be taken down and one might end up spending time searching for something that does not exist anymore. It's better to find out immediately it is no longer available than a futile search.
----
Some mobile web browsers such as Chrome (to Google's credit) thankfully store saved pages as MHTML files into the common Download folder, where they can be backed up and moved elsewhere using a file manager or an external computer. However, other browsers like Kiwi browser and Samsung Internet incorrectly store saved pages into their respective locked directories inside "/data/". Without root access, those files are locked in there and can only be accessed through that one web browser for the lifespan of that one device.
For tabs, there are some services like Firefox Sync. However, in order to create a text file of the opened tabs, one needs an external computer and needs to create an account on the service. For something that is technically possible in one second directly on the phone. The service can also have outages or be discontinued. This is the danger of vendor lock-in: if something is no longer supported, it can lead to data loss.
For Chrome, there is a "remote debugging" feature on the developer tools of the desktop edition that is supposedly able to get a list of the tabs ( https://android.stackexchange.com/q... ). However, I tried it and it did not work. No connection could be established. And it should not be necessary in first place.7 -
I hate that when developing on Windows I need like four different terminals. CMD, MINGW64/Cygwin/MSYS2, PowerShell. Each one has different functionality:
CMD - basic Windows commands
MINGW64 - emulates Linux terminal with frequent Linux commands and great support for Git
Powershell - access Windows COM, .NET etc.
Now there are solutions that attempt to solve this like Cmder (which is just more user-friendly ConEmu). These are console emulators which wrap all these in one window (with multiple tabs). But they are slow as hell. I have to wait like 10 seconds each time I start a terminal in Cmder, because the emulators need to run some huge startup scripts. But I just need to run one command from this one freaking folder!
Eventually I end up having like 30 different terminal windows open, each one different in functionality and each time I need to do something I must think about which terminal I need and in which folder. Furthermore I have to think about whether to run the terminal as administrator, but I usually forget that, so I have to close the terminal and reopen as admin. Why don't you just add something like su or sudo, Microsoft? 9
9 -
The reason I don't use Linux on my desktop is its hobby of saying “fuck off” spontaneously and without warning when I need it the most.
A designer friend shares his After Effects project and asks to export that to Lottie? Fuck off.
Your Android phone decided to brick itself with an OTA update (yep, happened to me, thanks Sony), and you need to unbrick it? Fuck off!
A musician friend wants to connect his audio card (that of course has no Linux drivers) and record some bass riffs? Tell him to fuck right off mate.
Your boss suddenly asks you to check an MS Access file for him as he's en route to an important meeting? Yep, you guessed it — fuck off.
Your government now requires your tax papers to have digital signatures? Fuck off, it only works for Mac and Windows.
Want to connect an old digital camera? Would you please fuck off?
I know I'm gonna get heat from Linux fanboys, especially on this platform. After all, a designer should know how to export to Lottie if he's a real designer, you should've bought a better phone, your friend should've had his laptop with him, your boss should've used open source tools instead of MS Access… Wait, he was tasked that from above? Then his boss should've used open source tools! Government mandates digital signatures? Well, tell them to port that to Linux! Start a riot! Get a better government! Move to a better country! Digital cameras? Who uses them in 2024, especially old ones! Are you some kind of hipster?
I know preparing for corner cases is bona fide premature optimization, but that's the whole point — with Mac or Windows, you don't have to prepare at all. You always have options. With Linux, your number one option is to have Windows handy if need be.
Linux works perfectly on my server, but not on my laptop.18 -
!tech
i was feeling very disturbed thinking about this thing, so just wanna share here. trigger warning : this is about 2 recent news (1 national and1 international) about crimes against women and its affect on me, a male , somewhat privileged guy with rarely any women in life.
news 1 : some lady in iran getting killed by police due to religious laws . news 2 : a receptionist girl in india getting killed for not providing sexual services to hotel people .
i will come back to first news in a bit, but second news has shaken me to the very core. i saw a post where her dead corpse was being taken up by her acquitances and she is just ... lifeless, hands going sideways, face hung at one side, mouth open... damn :'(
read more here : https://indiatoday.in/india/story/...
i am not at all related to this news, but somehow, i as a guy feel disgusted and being responsible for this sad event. this is not an act of power or lust , this is an act of a horrible mentality.
i come from the city where the world's most number of hate crime and crime against women take place. and pathetic politicians and people of power blame it on women's dressing and mens "naive nature" and , "boys being boys, accidentally making mistakes" . little did anyone know that this mentality has been cooking in the streets for last so many years.
i am a single child with no siblings or grandparents, my relatives rarely visit me and my last 24 years on earth rarely involved any female companionship apart from my mom.
i like girls, i find them cute. i really want to be with someone, to have a consensus relationship. but the talks among my homie groups and other male friends have gone toxic to the level that a national issue syarted feeling relatable.
the feeling of getting affection from someone has somehow turned into a lust, a "game", a "service". one guy( who recently shifted to other state) would use to tell us how he would visit " red light areas" , another one(also left) once tried to ask for that "service" in a camp where we were staying during a trip, and used to tell how he would hook up with girls on Instagram.
we used to laugh at those things, find them interesting and enjoyable. i would think about them in deep, thinking that this is something possible, a transactional access to sex, with me now earning enough to afford it.
now, seeing this news i feel so shitty and being a horrible human. those thoughts were not originally mine, but i didn't opposed them. rather i laughed on it , and thought that once am even more powerful financially and politically, could even entertain that approach.
As a guy, i want to say i am deeply, terribly sorry.
This mentality needs to be changed. my homie group is not just the only group of males that has such vile thoughts having openly propagated. every park, every company meeting , every library, every gym, anywhere i go, i can just show up a coffee cup and shout "women,huh" and can get a laughter followed by several low voices whospers on which girl is a "s***" there .
there are multiple points of failure in our society that are causing these. the news 1 from the start of this rant is the very first : role of government and religion on controlling "dresses and behaviour" of women
another comes the role of sex, culture and gender education in institution. institutions in my areas are so fucked up: they teach how plants fuck and bees suck honey to a puberty hit student, but doesn't teach consent, relations and personal behavior at any age. my school would even try to sometimes make all girls sit in a seperate row and other times would force guys to sit with girls. don't know what they got for this authoritative behaviour, but that sure didn't impacted our brains very rightly.
lastly this needs to be made clear in evevry guy's mind that paid prostitution, forced prostitution and consensus relationship are 3 different things, and only a respectable , consensus relationship is something you should think about and prepare for.7 -
My first project was a batch/visual basic script that could do a few things. Open and close CD trays, show a fake virus pop-up, log off, and some other misc stuff.
My second script was a 1 line batch script with vbs generated from itself. It would fuck up your system, put itself in startup, try and replace Explorer.exe with itself, show stuff on screen, reboot it, put itself in strange places so it could be run of the user did something like access Windows features. Never used it but it was fun to make -
Disclaimer: This is all theoretical. Neither me nor my friend (with whom I discussed this) are stupid enough to even try to pursue this, but as an idea, i believe it might generate cool/new ideas/ways for handling secure communications across social groups.
Let's do some role play. Let's design a delivery app for drug dealers, think Seamless or Uber Eats, but for drugs. Not for big deliveries, like kilograms of coke, but smaller stuff. Maybe a few grams of it or something. The clients could rate dealers, and vide-versa. This would build a level of trust within the system. There would be no names, just anonymous reviews, ratings, and prices. Only the info you'd need to know.
The biggest (only?) problem we found (besides legality) was that, how would you prove that you're a client and not a snitch (or cop). This would have to somehow be handled both on signup, as well as when ordering (let's imagine that all who are clients are pure and won't ever snitch).
One of the ways we found to combat this was to have the app invite-only. This would, in theory, do away with the problem of having snitches signing up. However, what if the phone got stolen/breached by a snitch, and they also got full access to the account. One way we thought we could combat this would be with a "dispose number" or something similar. Basically, you call a number, or send a text, or message a Signal bot etc, which would lead to the account's instant termination, no traces of that user left. Hence, a dispose number.
The flow of the app would be as follows:
A client wants some amount of heroin. He opens the app, searches for a dealer, sends the him the desired amount, and in return gets back a price from the dealer. If both parties agree on the amount and price, the deal would start.
The app would then select a random time (taken from the client's selected timeframe and the dealer's "open" time) and a location (within a certain radius of both them, somewhere in between them both for convenience). If both of them accept the time and place, they'll have to meet up at said time and place.
The actual delivery could also be done using two dead drops - the client drops the money at one of them, the dealer drops the goods at the other one. Yes, this might be subject to abuse, but it wouldn't be that bad. I doubt that clients would make huge orders to unknown/badly rated dealers, as well as dealers accepting offers from badly rated clients. My idea is that they would start small, just so if they do lose their money/goods, the actual loss wouldn't be as big for them, but for the other party, having bad ratings would mean less clients willing to buy or dealers willing to sell.
A third way would be to use crypto, but the reason I left this as the last one is because it's not that wide-spread yet, at least not in local drug dealing. With this method, the client would initiate the order, the crypto would be sent to either the dealer or an escrow account, the dealer would then drop the goods at a random place and let the client know where to go to get them. After the client has gotten the goods, they could both review/rate the quality as well as the overall experience with that dealer, which would either make or break the dealer's upcoming deals. This would be pretty much like other DNM's, but on a local scale, making deliveries faster.
So far, this would seem like something that would work. Are there any ideas that might improve this? Anything that might make things more secure/anonymous?
My reason for this post is to spark a conversation about security and anonymity, not to endorse drugs or other illegal stuff.
Cheers!
PS. Really loving the new PC design of devRant14 -
Try inserting today's date in access db using sql ( 01/03/2017 in dd/MM/yyyy format). Open db and check what has inserted instead.1
-
AAAARGHH!!! It happens every now and then that when I open a window in a Windows application, the window opens outside the display area, on a non-existing display to the right of my primary screen. There is no other way to access the newly opened window than to go to "Screen resolution" and swap screens 1 and 2 such that the secondary screen thinks it is to the right of the primary screen (although physically it stays to the left of the primary screen). And then, once I've got hold of the window, I swap the screens back. It's just so incredibly annoying and a complete waste of time. This is staring to really get on my nerves! >:(8
-
## Learning k8s
Interesting. So sometimes k8s network goes down. Apparently it's a pitfall that has been logged with vendor but not yet fixed. If on either of the nodes networking service is restarted (i.e. you connect to VPN, plug in an USB wifi dongle, etc..) -- you will lose the flannel.1 interface. As a result you will NOT be able to use kube-dns (because it's unreachable) not will you access ClusterIPs on other nodes. Deleting flannel and allowing it to restart on control place brings it back to operational.
And yet another note.. If you're making a k8s cluster at home and you are planning to control it via your lappy -- DO NOT set up control plane on your lappy :) If you are away from home you'll have a hard time connecting back to your cluster.
A raspberry pi ir perfectly enough for a control place. And when you are away with your lappy, ssh'ing home and setting up a few iptables DNATs will do the trick
netikras@netikras-xps:~/skriptai/bin$ cat fw_kubeadm
#!/bin/bash
FW_LOCAL_IP=127.0.0.15
FW_PORT=6443
FW_PORT_INTERMED=16443
MASTER_IP=192.168.1.15
MASTER_USER=pi
FW_RULE="OUTPUT -d ${MASTER_IP} -p tcp -j DNAT --to-destination ${FW_LOCAL_IP}"
sudo iptables -t nat -A ${FW_RULE}
ssh home -p 4522 -l netikras -tt \
-L ${FW_LOCAL_IP}:${FW_PORT}:${FW_LOCAL_IP}:${FW_PORT_INTERMED} \
ssh ${MASTER_IP} -l ${MASTER_USER} -tt \
-L ${FW_LOCAL_IP}:${FW_PORT_INTERMED}:${FW_LOCAL_IP}:${FW_PORT} \
/bin/bash
# 'echo "Tunnel is open. Disconnect from this SSH session to close the tunnel and remove NAT rules" ; bash'
sudo iptables -t nat -D ${FW_RULE}
And ofc copy control plane's ~/.kube to your lappy :)3 -
A backdoor means an open port so...
If anybody in including the admin checks the open port he will definitely notify the port and probably will close that port so...
Maintaining access means nothing?8 -
What the fuck, Android? My phone was locked, and the last open app was Instagram brcause I was chatting with my friend. So I try to unlock the phone with fingerprint, as I always do. The phone unlocks (at least it looked like it) and I get straight ot my IG chat, but at the same time an error message appears on the top of the screen saying that it failed to unlock the phone. And sure enough when I check my navi bar, the recent apps button is missing, indicating that the phone is still in a locked state. So after a failed unlock, someone with enough luck can get full access to my instagram chats and whatever else the foreground app is??? What the actual fuck?2
-
!Dev
If I was rich I think I'd donate to schools and children educational funds a lot
There's so much more that I've been able to learn about and do now that I have my own income stream and it's not just my dad supporting me and my 2 brothers himself. so I have the means to buy a server off eBay, or get books every few months on topics I find interesting, or upgrade my ram to an obscene 48GB to toy with ML and AI from my desktop when the whim arises, as well as all the stuff I'm learning to do with raspberry pi boards and my 3D printers, and the laptops I collect from people about to toss good fixable electronics
So I think I'd want to open the same doors for other children if I ever could who knows how much farther I could be if I had this same access when I was younger and didn't get access to my first 'personal' laptop when I was already 14 or 15 years old
I still consider my childhood 'lucky' and I had many opportunities other children couldn't get, but if I ever could I think I'd like to make future children have more opportunities in general1 -
Some interesting keyboard shortcuts that are lesser-known but can be quite useful:
1.Windows Key + . (Period): In Windows 10 and later versions, this shortcut opens the emoji panel, allowing you to quickly insert emojis into your text.
2.Ctrl + Shift + T: This shortcut reopens the last closed tab in most web browsers (Chrome, Firefox, Edge). It's handy if you accidentally close a tab and want to retrieve it quickly.
3.Ctrl + Backtick (`): In some text editors and IDEs (like Visual Studio Code), this shortcut toggles the integrated terminal window, allowing you to quickly switch between editing and running commands.
4.Ctrl + Shift + Esc: This directly opens the Task Manager in Windows, skipping the intermediary step of opening Ctrl + Alt + Delete and selecting Task Manager.
5.Alt + Drag: In many graphics and design applications (like Photoshop), holding down the Alt key while dragging an object duplicates it. This can save time compared to copying and pasting.
6.Ctrl + Alt + D: This shortcut shows the desktop on Windows, minimizing all open windows to quickly access icons and shortcuts on your desktop.
7.Ctrl + Shift + N: In most web browsers, this shortcut opens a new incognito or private browsing window, useful for browsing without saving history or cookies.
8.Alt + Enter: In Excel, this shortcut opens the Format Cells dialog box for the selected cell or range, allowing quick formatting changes without navigating through menus.
9.Shift + F10: This shortcut performs a right-click action on the selected item or text, useful when you can't or don't want to use the mouse.
10.Ctrl + Shift + V: In many applications, including Google Chrome and Microsoft Word, this shortcut pastes text without formatting (paste as plain text). It's useful when copying text from websites or other documents.
++ if you like this5 -
unfortunately, iCloud's "hide my mail" available for as low as $1.19/mo is the best email aliases service. Why? Because those addresses have no discernible pattern, and, most importantly, end with @icloud-dot-com.
a lot of services nowadays think aliases are for scammers, so they reject well-known alias domains like those proton has. but no one rejects icloud ones.
they can't wrap their head around that people like me use aliases, one alias per service, to have control over the spam you send us. unsubscribe buttons in emails often don't work, or unsubscribe you from some super-niche "segment" that one email belonged to, but because you bitches have a lot of those segments, you just carry on spamming.
major dicks that aren't concerned with email deliverability rating, like microsoft — because their emails get delivered no matter what, they're microsoft after all — think they can just not allow people to unsubscribe from their spam. when I needed to create a ms account, thank god I used an alias. I got bombarded with their spam, and lo and behold, not a single email had an unsubscribe button. Instead, the bottom of each email said "this email is a part of mandatory onboarding" or some shit like that, despite just being advertisement. no option to unsubscribe from that bs in their "dashboard" either.
so I just disabled that alias. despite what all of you stupid fucks want, it's my computer, and on it, the computing happens on my terms. when I need a confirmation email, I enable the alias, get the email and then disable it.
I have no mics and no cameras. I pay cash. I don't borrow money from banks. I don't have a credit card. when I receive crypto, I exchange it for cash directly in a physical crypto exchange that doesn't require my passport. I have headphones with built-in mic that I use exclusively for calls, but when I plug them out, no mic for ya. my next phone won't have a sim (and no eSIM either), I will disassemble it and take the front-facing cam, as well as mics, out of the phone, and then cover the back camera with velcro that I'll undo every time I need to take a pic. it will also run graphene os and be held inside a faraday cage when not in use. I have a separate dumb phone for calls that has its removable battery disconnected at all times when I don't use it. no matter if you're corpo or government, no matter all zero-days and backdoors, if there is physically no mic and no cam to be found, trying to access them is futile.
no use trying to profile me or get any kind of info from me unless I want you to — I'll just strangle you and your systems. my info sphere is a fortress surrounded by a bottomless tarpit. you'll drown in it should you try to violate me. if you so much as touch it, it will suck you in. I'll stream your drowning on youtube.
even irl, I try to dress, walk and move as weirdly as possible. during my morning walk, I be straight up walk as if I was rabid. when our eyes meet, I'll smile creepily, just to communicate that don't fucking touch me you fucking degenerate. don't even think about talking to me. just walk away you bitch before I pin you to the ground and bite your ear off. if you're bigger than me, you'll just get tased.
only those I trust deserve open, kind, validating, beautiful, well dressed and good smelling kiki.4 -
I am glad that firefox for android got an overhaul. I've been waiting a long time for more granular settings, before you couldn't even list websites you gave a particular pernission, and FINALLY passwords can't be viewed before authenticating with your fingerprint.
But after over two years I'm just so used to the old design, that it's glaringly obvious how less fluent the new ui is.
Instead of two clicks to access stored passwords you now need 4. And the button to open the tab list is now half my screen away from the actual tabs, and basically the entire screen away from "new tab".
The starting page isn't as good as before, although I hear they're working on it. But what is this shit, it took me like a week to even find the url bar context nenu! 13
13 -
Is there a way on Android 11 to open a terminal and access a package manager like in ordinary Linux ?10
-
In nearby county to mine, coder was arrested for 3 months for nickname matching leaked terrorist nickname "grower" by coincidence. His coding education was enough reason for arrest.
All hdd/ssd/usb/mobile devices were confiscated for thorough analysis right from the morning by police.
Feeding my security paranoia. Encrypting fully filesystem(LUKS) and my internet traffic (self raised open vpn), wiping fully usbs. I ll be protected from my ISP recording my traffic, and from unauthorised access to my data.6 -
it feels a bit wierd to open a word file that processes an access-filtered excel file to optionally generate an outlook mail.5
-
Just wanna remind everyone that banks are shit.
:Want to write an open source tool to make it easier for all fintechs to collaborate with banks
:Don't have access to banks's sandboxes to create and test the tool because I'm not company5 -
Anybody know of any enterprise software for password storage and sharing?
We have an issue where multiple people across different teams use the same accounts and need them to be able to access certain login information but not all login information.
I’m hoping for something free/open source but at this point I’m open to anything. Must have the ability to give users privileges.7 -
So, the story starts with me getting a job. Full-time job for the first time in my 21 years old life. After short conversation about how amazing this company is, after countless lies and stood questions they decided to hire me. I had to get come on Monday a week later with everything prepared.
So of course I did that and got to my workplace on designated time. Turned out nobody was expecting me, nothing was prepared for a new programmer and everyone seemed angry at me for no apparent reason.
After long talk with my new boss I got some less than 100$ pc with CPU that couldn't handle virtualization and expected me to work on software that needed extensive use of virtual machine.
PC is of course filled with all kinds of spying software that uses most of the resources. IT teams only job is to check if programmers are working their assess off for at least 8 hours a day.
I've filled a ticket about granting me access to Debian machine on the mainframe so I could work. No response for two weeks. I've lost hope already.
I have to work on open space with more than 30 engineers. Screams, phone calls, alarms, all at once, all the time. My colleagues seem to not care and I can't understand how.
I was tasked with rewriting major application because old developer did some half assed piece of burning shit. It took him more than one year, I'm finishing it in less than two weeks.
Of course nobody except for me is preparing any kinds of documentation. I had to reverse-engineer whole API for alarm system.
Salary is less than a junior programmer should earn.
But I'm stuck here for at least a year because nobody's here wants a guy whose only experience is as a freelancer. -
I've lost count of the days at this point...
First things first, lets all praise musky for getting David Bowie stuck in my head for the next month or so, not a bad thing, his song choice was on point. Also the rants have become few and far between because apparently I have to be an "adult" and go to work, pay my bills, and other things that distract me from programming.
Okay, now to the actual dev stuff. I've started to think that maybe my scope of languages is limited somewhat to my comfort zone, which is only java at this point. So for my project (game development), I've decided to pick a language based on what will work best instead of what I'm comfortable with, my runners so far...
C++: The default go to for game development. I would chose this but if I did, my best C++ game would look like Frankenstein's monster and would be filled with terrible code. For that alone I have scratched C++ from my list, for lack of experience.
Java: My usual, my go to, my comfort zone. I don't want to be comfortable though, I want to learn things. That asides, java has tones of resources, frameworks, libraries, and tutorials available. In addition, it's also able to run on pretty much anything, huge ++. The cons are trying to find the best resources, frameworks, libraries, and tutorials to use for a particular situation and that can be hard and confusing. Java may still be my go to but I'll get to that with the next language.
C#: I have never touched C# in my life, and the only things I know about it are what I've heard or read. So far I've heard it is SIMILAR to java, based around C++, and has aged really well compared to other languages. I like that it is similar to java without it being the same language, it will force me to learn things over and you can never reinforce the basics enough. It also has the huge benefit of being Microsoft based while still running on iOS, linux, macOS, windows, and android. This gives me really easy access to implement a mobile version (in the future obviously), while being able to run well on windows, the default OS for most gamers.
Overall I will start writing in C# and see if I like it. If I don't it's no big deal, I still have a good option in java to fall back on. I'm open to hearing opinions on this topic, java vs. C# but please keep your bias nonexistent and you constructive conversation very high. If any actual game developers that have experience with both languages are out their, and reading this, please comment so I can pick your brain.
Some of you may ask about the android scholarship, I contacted google and told them android development wasn't for me so they sent someone a late invite and rescinded mine, hopefully someone else will put it to better use.
Holy god this is long. I'm sorry. -
I love this weekly group rant, it made me think back when my mom started to work in a kindergarten and she used to take me to work when i was 4-7 years old ('94 - '97).
There was this "TV" and all the kids used to smash the buttons on it. It also played sound, but there was always a lot of kids there so I was shy to ask them if I push the buttons too. But I was the teachers son, so I didn't had to sleep in the afternoon, and then I discovered this computer thing I was amazed, it was like nothing I saw before, you push it and it does what you pushed and, *_* this smiley is exactly me back then. It was probably an old commodore with green text on the black screen. It was the moment when I decided to get more information about this wonder.
In elementary school (around '98) we had this computer room and as I was one of the best students back then I was granted access to it. It was a huge success in a post communist country to get money for new computers to teach us kids to use them back then, so only the chosen ones could use them, and I was one of them, one of the best time time of my life, honestly. At this moment I knew for sure, I want one and when I grow up I gonna work with them. I had no idea what you can do with it but every adult is talking about how well paid are the people who use them at work. :D it sounds funny now
In '89 or '99 we visited our family in a town far away. My grandfathers sisters boyfriend had a computer and he said, look I also have internet. This face again *_* what the hell is internet. So he explained me this internet thing which "makes all computers connected, but you have to pay for it and it kinda works like wired phones you know. Here you put the address and you can open the website"
me: website, whoooa *_*
8-9 year old clever me: "but how do you know what are the addresses, do you have a phonebook for these addresses?"
he showed me google, and a slovak and czech search engine, I remember searching for "funny pictures" on the slovak search engine, because I was thinking If I search google, its english so he would pay too much :D
I didn't had a computer until I was 13 years old, but then I started to messing with Microsoft Front Page 2003, was amazed with the html and css generated by it and started to editing it.
Now Im a front end web dev -
Going through some code I was handed to do an emergency project... Think of an aspx site that follows no design rule, like database access directly in the code behind. No models ect. So I'm going through this section that calls a function good start. Open the function find a class that contain code to access the database.. Humm ok this part look better that the rest. Read the code that validates if it exist in the database and gets the type back. So far so good then there is a get details function call.... Open up the fct ... Started crying... There is a 200+ lines switch case that goes over the type previously fetched..... And the type is stringed compare in the biggest switch case I've ever seen.... Fthis... I'm out1
-
I did an engineering quiz yesterday as a way of introducing a new database the school recently got access to. You had to sign up for the site.
- Passwords were max 20 characters (which is better than 10, but still, why???)
- You couldn't use special characters, but there was NO INDICATION ANYWHERE THAT THAT WAS THE CASE. It would just silently fail to log in. I had to open the browser console to figure out what wasn't working. FUCK -
So i'm currently working on my PiStation..
(look at my previous post if you're interested)
I'm imaging over RetroPie over to the SD card, screw back together the housing, and it boots up fine. As soon as i configured my XBOX-controller i got to the wifi-settings. And when i try to access my wifi, guess what, it doesn't connect to my f**kin wifi. So i double check my wifi-settings in the router i just bought to get over my roommates paranoia (that's a whole another story. Just in short, he's got no idea of IT-security and tries to be an admin, which results in a HUGE amount of bulls**t), confirm that the settings are alright, double check the PSK too, anything is fine. So i go through the whole process again, download the image (from their goddamn slow servers), open up the PiStation, image it over to the SD card, close it back up, anything boots up fine and works, except this f**king wifi. And the thing is, i COULD connect it with a patchcable, but i dont want cables going anywhere through my room. Currently imaging over recalbox OS, will keep you updated. I just want to play some old retro games ._.2 -
So I've been using Duet on my iPad Pro for a couple years now (lets me use it as an external monitor via Lightning cable) and without issue. Shit, I've been quite happy with it. Then the other day, whilst hooked up to my work laptop, there was a power fluctuation that caused my laptop to stop sending power to connected devices. Which is fine - I have it plugged into a surge protector so these fluctuations shouldn't matter. After a few seconds the laptop resumed normal operation and my connected devices were up and running again.
But the iPad Pro, for some reason, went into an infinite boot loop sequence. It reboots, gets to the white Apple logo, then reboots again.
In the end, after putting the iPad into recovery mode and running Apple's update in iTunes (as they recommend), it proceeds to wipe all my data. Without warning. I lost more than a couple of years of notes, illustrations and photos. All in one fucking swoop.
To be clear, you get 2 options in iTunes when performing a device update:
1. UPDATE - will not mess with your data, will just update the OS (in this case iPadOS)
2. RESTORE - will delete everything, basically a factory reset
I clicked UPDATE. After the first attempt, it still kept bootlooping. So I did it again, I made sure I clicked UPDATE because I had not yet backed up my data. It then proceeds to do a RESTORE even though I clicked UPDATE.
Why, Apple? WHY.
After a solemn weekend lamenting my lost data, I've come a conclusion: fuck you Apple for designing very shitty software. I mean, why can't I access my device data over a cabled connection in the event I can't boot into the OS? If you need some form of authentication to keep out thieves, surely the mutltiple times you ask me to log in with my Apple ID on iTunes upon connecting the damn thing is more than sufficient?! You keep spouting that you have a secure boot chain and shit, surely it can verify a legitimate user using authenticated hardware without having to boot into the device OS?
And on the subject of backing up my data, you really only have 2 manual options here. Either (a) open iTunes, select your device, select the installed app, then selectively download the files onto my system; or (b) do a full device backup. Neither of those procedures is time-efficient nor straightforward. And if you want to do option b wirelessly, it can only be on iCloud. Which is bullshit. And you can't even access the files in the device backup - you can only get to them by restoring to your device. Even MORE bullshit.
Conversely, on my Android phone I can automate backups of individual apps, directories or files to my cloud provider of choice, or even to an external microSD card. I can schedule when the backups happen. I can access my files ANYTIME.
I got the iPad Pro because I wanted the best drawing experience, and Apple Pencil at the time was really the best you could get. But I see now it's not worth compromise of having shitty software. I mean, It's already 2021 but these dated piles of excrement that are iOS and iPadOS still act like it's 2011; they need to be seriously reviewed and re-engineered, because eventually they're going to end up as nothing but all UI fluff to hide these extremely glaring problems.2 -
I wonder if there is any technical issues that prohibit the creation of open source websites.
By "web sites" I do not consider CMS like Drupal or word press, but rather entire end web site sources.
In fact anything (frontend, backend) except database content that contain user data and credentials.
Not for reusability purposes like CMSs, but simply for transparency and community development purposes, like almost any open source end application.
I agree that a web server is much more exposed than a classic desktop app, as it has lots of targetable private data and internet public access. But for some non-critical purpose this seems to be affordable in exchange of better code review, allowing a community to help improve a tool it uses, and better (not perfect though) transparency (which is an increasingly relevant question nowadays, mainly towards personal data usage).6 -
I've just been asked by a dev to open up publicly a database port after giving him direct ssh access to the server. Your funeral, buddy.4
-
As back end developer, I rarely have hands on production environment. When it happens, I need to ask my way around and since the office is empty that day, I ask the client directly. They give me a URL. Right away, I ask the credentials.
"Just connect to the URL"
"You mean, you have an open access of this software, having critical information of more than 50 000 persons, to the web?"
*Silence* "hahaha it appears that way"
Thankfully, a tactful manager handled the situation astutely and we never heard about it anymore.
Don't we love all happy ending? -
My DNS provider does not have an API. They do have one... That is wrong... But on the description page, they say we have to open a ticket to be given access. No requirements. Nothing...
And then I am told "they do no longer offer dns for private hosting". I don't even host with them, I only have a domain with them.
But the magical word is no longer. That means they did offer it. In the description of the API it still says "and for everyone who feels comfortable interacting with a REST API." Oh, and they asked anyone who works on it to be so nice and share any SDK's they might have coded up. Would have shared my SDK. Would have... If no Rust SDK was available yet.
So, what the fuck...
The problem with that is that I need a wildcard certificate for my homelab with DNS validation. So, I need to dynamically set a txt record. Now I wonder... Was this done on purpose? They are selling wild card certificates. Letsencrypt are giving them out for free. I bet they deactivated it, so they can sell more...
Anyway. Solution time.
Short term: I make my own API with black jack and hookers... And selenium.
Long term: I need to fucking move my domains to a different provider.
But what the fuck... What the fuck?6 -
I don't live in a vacuum. I need to open an occasional Adobe bs format file (Illustrator, Premiere, After Effects, Photoshop). An occasional MS Office file too (Access, Word, Excel, PowerPoint). And don't tell me LibreOffice supports .docx. It doesn't support edits suggestion mode well enough. I needed AutoCAD for a period of time.
Desktop Linux people, what do you want me to do? Go to devRant and post “windows bad” rant? Go cry on Reddit?
I too think Windows is evil and 11 is essentially malware, but when I suddenly need those things done yesterday, and my livelihood depends on that, I have no choice.
(this is part 2 of this rant: https://devrant.com/rants/10703825/...)13 -
Which ons is less risky and which one Is most profitable to succeed ?
0- telling the admin you forgot your password and as he's logging in, sniff his password (you already placed sslstrip)
1- gain access to router using its vulnerabilities and redirect the traffic to a fake page and get the password.
2- exploiting smb port of admin's system and placing a krylogger or stealing his cookies if available
3- brute forcing admin password :/
4- pressing forgot password on admin account and staying close to him and sniff the SMS containing the otp using rtl-sdr (and of course you will be prompted to set a new password)
5- any other way .
Also the website itself is almost secure.
It is using iis 8.5 and windows server 2012
Only open ports are 80 and 443.4 -
When you open an access db in visual studio so you can do sql querys with out the annoying access interface and then i realize visual studio uses the same interface as access except its worse *-*3
-
Working along side another consultant house for a client, we have our shit ready weeks ago for integration testing (as was the deadline) against the other guys. We tell them we are ready, but we need them to be ready too, there are some tricky format things and we basically let them spec it out since they integrate further down the line.
They come _NOW_ way over deadline with change requests in message formats, like MOTHERFUCKER, IM ON MY WEEKEND NOW. We KNEW the client wanted it ready next week, thats why we were ready in time. You are not gonna cost me my weekend.
(is what i wanted to say, the devs on the other team are super nice and just absolutely overloaded with work which i cannot help them with)
One thing is certain, tonight my internet access mysteriously dissappears and wont open until monday morning. Such a shame -
Some days I think my hate for managers is wrong: they are there to improve the workflow and make stuff easy... but then they manage (badum tss) somehow to prove me wrong.
The issue: our pm doesn’t know how to write tickets and instead of writing short but meaningful tickets, they just write pointless text and add external documents which they should read in order to tell us what to do.
My good thoughts: “maybe he’s really busy for real and is really unable to spend time writing them... kinda hard to believe and possible red flag, but shit happens, so let’s not be too harsh.
They are trying to save time... right?”
Their solution: “let me open a ticket to grant you access to the resource”
Sounds good, right: now let me explain something... their “solution” requires opening a ticket and escalating all the way up to CTO, and so far it’s been 2 days I am waiting for these credentials. 2 freaking days only to be able what to know in a ticket the f***er opened outside of planning cause it is supposed to be urgent.
“Can’t you just give me the files directly?”
“I am sorry, I don’t have time (to download and send you 3 files)”
Managers: making the process easier.1 -
Previously on devRant: https://devrant.com/rants/2010573/...
And here's something similar for vlc, but it expects you to point it at a local file (note: vlc can not access files inside termux's private storage). Obvious copy&paste from SO for escape characters aside, here you go:
https://pastebin.com/raw/QeHSnDK51 -
I need some help with parking a domain in ovh.com webhosting. It's a real pain in the ass so any input is strongly appreciated. I kinda figured out what todo already, but still need some clarification.
Normally after buying a webhosting all I would need to do is login to my domain registrar's website and in the control panel just change nameservers to webhosting nameservers and that's all. Webhosting provider would take care of the rest (subdomain creation, e-mail creation and etc.) But because OVH are assholes, they support this type of domain parking only for domains registered at OVH.
For external domains, procedure is as follows:
For the configuration to function, you will need to make the following adjustments with the current provider:
Insert a TXT record for the domain ovhcontrol.mydomain.com with the value jwyPolzgrZyIShzaQItqw
Point the A record of your domain mydomain.com to 51.244.97.19
Point the A record of your domain www.mydomain.com to 51.244.97.19
So basically I had to login to registrars cPanel and first of all I had to park my domain back to my registrar (I had to switch to default nameservers which are provided by domain registrar)
Only then I got advanced access to dns zone in order to add the required records above.
When I open my domain registrars dns zone cpanel this is what I see:
http://prntscr.com/nekx40
So basically, as I understand, I just need to add these required records like this?
http://prntscr.com/nekxjc
Am I correct?
So basically my OVH webhosting doesn't deal with dns zone at all, I will have to use my own registrar for adding subdomains?
What about e-mail addresses? OVH doesnt allow me to create emailboxes for "externally" parked domain addresses. Will I have to search for some e-mail provider, and add some additional records?
Any input/help would be appreciated.1 -
Github be like:
Want control on your files? Host your own LFS!(This goes the same even for those who are buying their storage packs for boosting their LFS storage by giving money)
FUCK THIS SHIT... I am a poor student. I also don't have a fucking credit card!! Can't you improve your system instead of asking people to host their shit themselves?
Also, why do they even have access to deleting user files??!! They literally asked me to give a sha sum of files I want to restore so they can delete the rest as one option and providing hashes of files to be deleted as another.
And the hashes are not even secret(as the files are in an open repository).
Which means, if you have a large file on a public repository and animosity with a github staff, BOOM! That file is no more!! 9
9 -
How do you deal with multiple git identities?
Im working fulltime + freelancing + working on my own projects and all of them are on different gitlab emails. It was very annoying to keep remembering to set my git email to a proper one each time I switch to work on another project.
Right now I came up with something easier:
I started using just 1 gitlab profile (personal one) and added my both company e-mails as secondary emails to my personal gitlab profile.
This way I can keep my git identity the same (personal e-mail address) and if I push to company1 repo or company2 repo the commit author e-mail addres is shown email@company1.com and email@company2.com as these emails are given access to private repos and they are added to my personal gitlab account.
Just wondering if these companies will see my commits to other repos by viewing my personal gitlab profile or no? Or if there is an easier way to handle multiple git identities without having to switch between them each time I open another project and want to push some commits.7 -
Having a dilemma... I need help with my gaming projects. I know a guy who I could train since he has lots of potential but Im having trust issues. Its because I invested around 10k into my codebase and Im afraid to give access to that guy since I suspect that he might use files and some day run away to make his own project. So im back to square 1 again which is loosing my mind with this huge workload. What should I do? Should I just say fuck it ant make him sign some air tight NDA agreement? Even then he could stand up and leave 2 months in and open a competitor project if he doesnt like my management style...3
-
The craziest way to send notification from firebase to Flutter depends on my_sql DB
Ok, I tried so hard to deal with notification in my app by specific conditions in my #my_sql DB
The background work in #flutter is kind of not easy to deal with, so here's my crazy way to achieve that:
I connect my app with #firebase and every time a new mobile open the app it rejecte it's #token in the DB
Now I create a public #PHP file that has access to my my_sql DB and #firebase1 -
I started looking into building my Android app but wanted to see if I could get a refresher on a few things. The starter template for the Nav Layout isn't exactly functional.
So first question is anyone know any resources like an actually functioning demo project.
Also I need DB access but want to open any db file given the *.db path and the DAO should be persistent, share across all fragments/activities. What would be the best design, way of doing that in Android though.
I don't think you can pass the object between activities but what about fragments. I'm thinking the main app opens the DB and then can pass a DAO Interface to all the fragments to use?2 -
I really like Linux but it makes me mad when apps I use, like Adobe XD, are available for everything but Linux.
I'm not even going to start with HBO not being able to load streams on Linux. I payed money to stare at a black screen.
I tried to use PlayOnLinux for Adobe Creative Cloud but XD doesn't even appear there.
I also hate dual booting because when I'm using Win or Linux for a bit I tend to make different desktops for different programs/IDEs/browsers and I like them to be open at all times for easy access when I want to do shit. Dual booting means having to open all this again
VMs are even worse in that they tend to be very slow and when I see choppiness when moving windows I immediately "nope" out of that shit
I can't put up with Windows's bs anymore, but not being able to use the software I need is even worse.
I don't know what to do2 -
So the developers in my workplace have blocked a server for themselves each when they know that there is a shortage and everyone needs to cooperate and share them. Now when they get stuck in any issue they expect me to get them out of it but just as soon as I ask for a server space, they are all like it will impact my working and we can't share. Now what would you expect me to do the next time you come to me? Do you seriously expect me to welcome you and your problems with open arms or make excuses to you when such a scenario occurs. Sometimes I think that the one thing missing here is a sense of basic human decency.
Now the zinger here - I've had similar experiences earlier and fortunately, I'm the resource administrator for the projects cloud account. Whenever these a**holes require any cloud resource, I make them go through tons of approvals which I have a blanket access granted before providing them access. Who's laughing now?2 -
Last year, I decided to invest $30,000 in cryptocurrency, enticed by promises of substantial weekly profits. Initially, everything seemed fine. I was hopeful and excited, convinced that this investment would not only safeguard my savings but also enhance my financial status. I was living comfortably, enjoying the benefits of my spending, and felt secure in my investment strategy. However, my optimism quickly turned into dismay. After a few days of monitoring my investment, I noticed that the website associated with my investment had gone offline. I tried to access my account, only to find that it had disappeared entirely. It was then that I realized I had been scammed. My investment, which I had carefully saved and trusted, was gone. The frustration and helplessness I felt were overwhelming. .I tried everything I could think of to recover my Bitcoin. I reached out to my wallet provider, contacted my bank, and even reported the incident to law enforcement. Despite my best efforts, none of these avenues yielded any results. It seemed like my money was lost for good, and I was left feeling defeated and hopeless. As time went on, I continued to search for solutions, but nothing seemed to work. That was until a few weeks ago when I was introduced to Trust Geeks Hack Expert. Initially, I was skeptical, having been let down by so many other attempts to recover my funds. But I decided to give Trust Geeks Hack Expert a try, hoping they might be able to offer a solution where others had failed. From. From the moment I reached out to them, I was met with a level of professionalism and dedication that I had not encountered before. They took the time to understand the details of my case and formulated a comprehensive plan to recover my lost funds. Their approach was thorough, and they maintained open communication throughout the entire process, keeping me updated on every development. To my immense relief and joy, Trust Geeks Hack Expert succeeded where all my previous efforts had fallen short. They were able to recover the full amount of my stolen investment. The experience was transformative, I got back my money and regained a sense of hope and confidence that I had lost along the way. If you find yourself in a situation similar to mine—having lost cryptocurrency to a scam—I strongly recommend reaching out Website.. https :// trustgeekshackexpert . com/. Their expertise and commitment to their clients are truly commendable. They offer a glimmer of hope and a real chance to recover what was taken from you. You can contact Trust Geeks Hack Expert directly by E ma il <> trustgeekshackexpert [At] fastservice [Dot} com for their services. They specialize in handling such cases and have a proven track record of helping people like me reclaim their lost assets. Their support was invaluable, and I am incredibly grateful for their assistance. In sharing my story, I hope to provide some guidance and reassurance to others who might be struggling with similar issues. Investing in cryptocurrency comes with risks, and it’s crucial to be aware of where you place your trust. But remember, with the right help and persistence, there is still hope for recovery. Stay vigilant, protect your investments, and if you need assistance, don’t hesitate to reach out to professionals like Trust Geeks Hack Expert
-
Discover Bali with Luxury Car Rental Bali
Bali, with its stunning landscapes, rich culture, and vibrant atmosphere, is a dream destination for travelers seeking adventure and relaxation. To enhance your experience on this beautiful island, look no further than Luxury Car Rental Bali. We offer a wide range of premium vehicles that provide comfort, style, and performance, ensuring that your journey through Bali is as memorable as the destination itself.
Sewa Chevrolet Impala Bali: Experience Timeless Elegance
For those who appreciate classic American luxury, our Sewa Chevrolet Impala Bali service is the perfect choice. The Chevrolet Impala is a symbol of elegance and sophistication, offering a smooth ride and spacious interior that make it ideal for both leisure and business travel. Whether you’re heading to a special event, exploring Bali’s scenic routes, or simply enjoying a night out, the Impala delivers a blend of comfort and style that enhances every journey.
Adventure Awaits with Rental Jeep CJ Bali
For the adventurous spirit, our Rental Jeep CJ Bali service offers the perfect vehicle to navigate Bali’s diverse terrains. The Jeep CJ is renowned for its rugged capability and off-road prowess, making it an excellent choice for exploring the island’s hidden gems, from lush jungles to rocky coastlines. With its sturdy design and open-air experience, the Jeep CJ allows you to immerse yourself in Bali’s natural beauty while enjoying the thrill of off-road driving.
Sewa Jeep CJ Bali: Perfect for Group Adventures
If you’re traveling with family or friends, our Sewa Jeep CJ Bali service ensures that everyone can join in on the adventure. With ample space for passengers and gear, the Jeep CJ is perfect for group outings, beach days, or exploring Bali’s iconic landmarks. Experience the freedom of the open road and create unforgettable memories as you traverse the island’s scenic routes in this iconic vehicle.
Enhance Your Journey with Police Escort Bali
For those seeking added security and peace of mind during their travels, our Police Escort Bali service offers a unique and reassuring experience. Whether you are attending a high-profile event, traveling with valuable assets, or simply want to ensure a safe and smooth journey, our professional police escort service provides an extra layer of security. Enjoy your time in Bali with the confidence that you are in safe hands, allowing you to focus on creating unforgettable memories.
Why Choose Luxury Car Rental Bali?
At Luxury Car Rental Bali, we pride ourselves on providing an exceptional experience for our clients. Here are just a few reasons to choose us for your luxury car rental needs:
Diverse Fleet: Our extensive selection includes classic vehicles like the Chevrolet Impala and rugged options like the Jeep CJ, ensuring you find the perfect ride for any occasion.
Outstanding Customer Service: Our friendly and professional team is dedicated to delivering personalized service, ensuring a seamless rental experience from start to finish.
Flexible Rental Options: Whether you need a vehicle for a day, a week, or longer, we offer flexible rental plans tailored to your specific needs.
Convenient Location: Our office is conveniently located at Jl. Kuwum II. 18 X Kerobokan, Kerobokan Kelod, Kec. Kuta Utara, Kabupaten Badung, Bali 80361, Indonesia, making it easy to access our premium vehicles.
Book Your Dream Vehicle Today!
Don’t miss the chance to explore Bali in style and comfort. For inquiries or to reserve your dream car, contact us at +6287771617888. Experience the beauty of Bali like never before—choose Luxury Car Rental Bali for an unforgettable adventure!
-
I couldn't wake up because my retarded phone decided to update the OS without asking me
Now I'm trying to fill my fucking tax declaration and I cannot access my fucking statements because I can only access them from my bank phone app, and it sends me a link by email to open it into revolut.
Apparently the fucking update installed MICROSOFT 365 to open CSV.
I feel like homicide1 -
How can you build an oidc library almost completely on observables? Cannot complain about it, as it's open source, but what if you want to access some token data synchronously?4
-
Transform Your Home with Mark Brightman Handyman Services: Lighting Installation, Pet Doors, and More
When you're in need of a reliable handyman near me, Mark Brightman Handyman Services is here to help. Serving the Beaverton, OR area, we specialize in a wide range of home improvement services, from lighting installation near me to pet door installation near me, and much more. Our team of skilled professionals is dedicated to making your home safer, more comfortable, and more efficient with expert installations, repairs, and renovations.
Located at 1856 NE 101st Ave #102, Beaverton, OR 97006, Mark Brightman Handyman Services is your go-to source for all things home improvement in Beaverton and the greater Portland area. Let’s take a closer look at how our services can improve your home and life.
Lighting Installation Near Me – Brighten Your Home with Expert Lighting Solutions
Whether you need new lights for your kitchen, living room, outdoor space, or bathroom, lighting installation near me is a service we specialize in. Proper lighting not only enhances the aesthetics of your home but also adds safety and functionality to your living spaces. At Mark Brightman Handyman Services, we offer expert lighting installation near me that suits your style and needs.
Our lighting installation near me services include:
Indoor Lighting: From recessed lights to pendant lighting, we help you choose and install the right lights for every room in your home.
Outdoor Lighting: Increase security and create ambiance with outdoor lighting for pathways, porches, gardens, and more.
Ceiling Fans with Lighting: Looking for both cooling and lighting? We can install ceiling fans that also feature built-in lights, perfect for saving space while adding comfort and illumination.
Custom Lighting Solutions: We can design custom lighting setups for home theaters, accent lighting, or task lighting tailored to your needs.
No matter what type of lighting you need, Mark Brightman Handyman Services provides professional lighting installation near me that enhances the beauty and functionality of your home.
Pet Door Installation Near Me – Let Your Pets Roam Freely
For pet owners, installing a pet door installation near me is a simple yet effective way to give your furry friends the freedom to come and go as they please. Whether you have a dog, cat, or both, a pet door can provide them with easy access to the yard, patio, or garden, all while maintaining the security and privacy of your home.
At Mark Brightman Handyman Services, we specialize in installing a variety of pet doors to suit different needs and budgets. Our pet door installation near me services include:
Dog and Cat Doors: We offer pet doors that can be installed in walls, doors, or windows, designed for both dogs and cats. From small to large breeds, we ensure the pet door is the perfect size.
Electronic Pet Doors: For added security, we can install electronic pet doors that open only when activated by a collar sensor, keeping unwanted animals from entering.
Security and Weatherproofing: Our pet doors are designed to be secure, weatherproof, and energy-efficient, helping you maintain comfort and safety in your home.
Custom Pet Doors: Need a unique installation? We can customize a pet door to fit specific areas or particular needs, including sliding doors or garage entries.
By choosing Mark Brightman Handyman Services for your pet door installation near me, you’re ensuring a high-quality installation that keeps both your pets and home secure.
Reliable Handyman Near Me – Your Trusted Expert for All Home Repairs and Improvements
When you search for a reliable handyman near me, you want a professional who can handle everything from small repairs to major installations. Mark Brightman Handyman Services is your trusted partner for all your home improvement needs. We take pride in delivering expert services with a focus on quality, customer satisfaction, and convenience.
As a reliable handyman near me, we offer:
General Home Repairs: Whether it's fixing leaky faucets, repairing drywall, or replacing worn-out hardware, we provide dependable repairs to keep your home in top condition.
Remodeling and Renovations: From kitchen and bathroom remodels to custom built-ins and room additions, our team has the expertise to transform any part of your home.
Maintenance Services: We offer routine maintenance to help prevent costly repairs down the road, including gutter cleaning, HVAC maintenance, and more.
Specialty Installations: In addition to lighting and pet doors, we can handle everything from TV wall mounting and furniture assembly to ceiling fan installations and door repairs.
At Mark Brightman Handyman Services, we are a reliable handyman near me who brings professionalism, attention to detail, and a strong work ethic to every job, no matter how big or small.
Why Choose Mark Brightman Handyman Services? 3
3 -
Is my iPhone hacked or bugged? [GrayHat Hacks Review] Remove spyware
A few weeks ago, I had noticed my wife acting increasingly suspicious and secretive, and it was as if she knew my every move. I realized that my laptop had become annoyingly slow and would randomly redirect me to unfamiliar websites on its own. My phone would sometimes light up with notifications that I hadn't received. I'm not the most tech-savvy person, but even I knew that something was off. That's when I stumbled upon the term 'spyware' and the horrifying reality of how it could be used to invade someone's privacy.
Desperate to know the truth, I found myself in a dark corner of the internet, searching for a way to get to the bottom of my suspicions. That's when I came across a review for GrayHat Hacks Contractor, a team of ethical hackers well versed in hacking and spywares. I sent them an email detailing my situation and the signs that had led me to suspect my wife. To my surprise, they responded within minutes, offering a free consultation and assuring me of their confidentiality.
They explained their process and the tools they would use to scan my devices for any signs of intrusion. They were incredibly thorough, explaining the different types of spyware that could be planted and the ways they could be hidden. The actual process of detection and removal was done remotely. They provided clear, step-by-step instructions on how to give them secure access to my iPhone and laptop.
The results were shocking. Within a few hours, they had found and removed not one, but multiple instances of spyware on both my phone and computer. The extent of the violation was staggering. My wife had been tracking my location, reading my messages, and even listening in on my calls. I was devastated, not just because of the betrayal, but because I had been living under constant surveillance in what I had thought was a sanctuary of privacy.
Armed with the evidence, I approached my wife with a heavy heart. Through tears and anger, she admitted to installing the spyware, driven by her own insecurities and suspicions. She confessed to an affair that had been going on while I was away on business, a classic case of projection. Turns out that she was the one that was cheating. GrayHat Hacks Contractor not only removed the spywares but also taught me how to protect my devices and privacy in the future.
Our relationship is now a work in progress, filled with healing and rebuilding trust. The pain of her infidelity still lingers, but with the truth out in the open, we can begin to move forward. If you ever find yourself in a situation where you suspect your privacy is being invaded, I urge you to consider contacting GrayHat Hacks Contractor.
-
Trying to send a quickpay and I get locked out of online access to my bank account because of "detected fraud." The problem? Fraud prevention department is the only ones who can fix this, and they don't open up until tomorrow morning. And I really need access to MY OWN ACCOUNT tonight. ¯\_(ツ)_/¯
-
I really like devRant's community. I just don't feel very well using the closed-source app, which is very well done and works nice, but I'd feel more comfortable using an open source app with a public repository that everyone can look at instead of a closed-source app with storage and location permissions access. Indeed I would be fine enough with a mobile version of the web app too, but it doesn't seem to be in devRant's developers plan. I've once seen someone creating its own devRant app. Is there any public APIs? Is someone already thinking about this?1
-
Email info: Adwarerecoveryspecialist@ auctioneer. net CONTACT ADWARE RECOVERY SPECIALIST TO SPY ON YOUR CHEATING PARTNER SMARTPHONE
WhatsApp info:+12 723 328 343
Uncovering your wife's phone secrets through the skills of a adware-like ADWARE RECOVERY SPECIALIST is a delicate and potentially unethical endeavor that should be approached with great caution. These so-called "sneaky ways" often involve highly sophisticated technological methods to bypass security measures and access private communications and data without the knowledge or consent of the device's owner. A skilled web recovery specialist might utilize advanced hacking techniques, exploits in mobile operating systems, or specialized surveillance software to surreptitiously monitor your wife's online activities, read her text messages and emails, track her location, and even retrieve deleted files - all while leaving little to no trace of their intrusion. However, engaging in such invasive and underhanded practices not only violates your wife's fundamental right to privacy, but can also severely damage the trust and integrity of your relationship if discovered. Rather than resorting to these underhanded tactics, it would be far wiser to have an open and honest discussion with your wife about any concerns you may have, and work together to address them through ethical, consensual means. Building a foundation of mutual understanding and respect is essential for the long-term health of any marriage. For help, Contact ADWARE RECOVERY SPECIALIST through: Email info: Adwarerecoveryspecialist@ auctioneer. net
-
Purvanchal Skyline Vista is not just another commercial project; it’s a bold vision brought to life in Sector 94, Noida. Spanning over 18 acres, this avant-garde development is set to redefine commercial real estate standards with a blend of elegance, innovation, and strategic design. Offering a diverse mix of premium office spaces, high-street retail shops, theatres, gourmet restaurants, cafes, and a vibrant food court, this project is the future of business and leisure, perfectly intertwined.
Location Advantage
Located in the heart of Noida, Sector 94 is emerging as a premier hub for commercial and residential developments. What sets it apart is its unmatched connectivity. Sitting at the zero-kilometre mark from Delhi, Purvanchal Skyline Vista ensures seamless access across the NCR, courtesy of the Noida-Greater Noida Expressway. This strategic placement means you are always connected to crucial regions, whether it’s the bustling corridors of Delhi or the rapidly developing areas of Greater Noida.
Moreover, commuting becomes a breeze with the Okhla Bird Sanctuary Metro Station, just three minutes away. The project's proximity to the established commercial powerhouse of Sector 18 and easy access to major highways like FNG Expressway and NH-24 positions it as a truly strategic investment. The upcoming Jewar Airport, a mere hour's drive away, adds another layer of connectivity that further enhances the project's appeal.
Project Features
Purvanchal Skyline Vista is crafted to cater to the nuanced demands of modern businesses. The project is characterized by expansive open corridors, double-height retail spaces, and meticulously designed office suites ranging from 600 to 1,150 sq ft. With pricing starting at Rs. 15,000 per sq ft for office spaces—complete with attractive inaugural discounts—this development offers a compelling value proposition.
Retail spaces are equally enticing, with first-floor shops starting at Rs. 35,000 per sq ft, reduced to Rs. 30,000 for early investors, and second-floor units priced from Rs. 25,000 per sq ft, discounted for a limited time. Direct consultation with the developers is highly recommended for those looking to make an informed investment.
World-Class Amenities
Purvanchal Skyline Vista goes beyond just providing commercial spaces; it offers a holistic environment to enhance the visitor experience. The dedicated food court, a selection of fine dining restaurants, and chic cafes are thoughtfully designed to maximize visibility and footfall, creating a lively atmosphere.
Entertainment is another cornerstone of this development, featuring cutting-edge theatre for an immersive cinematic experience and a vibrant gaming and entertainment zone that appeals to all age groups. Additionally, including a unisex salon and spa offers a serene escape, ensuring that the project caters to business and leisure needs seamlessly.
Surrounding Developments
Sector 94 is not an isolated development; it is surrounded by some of Noida's most prestigious projects, including M3M The Cullinan, BPTP Capital City, and Supertech Supernova. This confluence of high-end developments enhances the area's exclusivity. It ensures a high volume of foot traffic, making Purvanchal Skyline Vista a magnet for investors seeking both visibility and growth.
A Legacy of Excellence: The Developer
Purvanchal Projects Pvt. Ltd. has been a stalwart in North India's real estate sector since its inception in 1994. Under the leadership of CMD Mr. Shah Alam, the company has delivered over 11,000 residential units across Delhi, NCR, and Lucknow, earning a reputation for quality, craftsmanship, and customer satisfaction. Their clientele, including prestigious government bodies and multinational corporations, is a testament to their unwavering commitment to excellence.
Conclusion
Purvanchal Skyline Vista is more than just a commercial project—it’s a visionary investment in the future of Noida's commercial landscape. Its prime location, unparalleled amenities, and the impeccable track record of the Purvanchal Group make it an irresistible opportunity for investors. Whether you're looking to secure premium office space, a high-visibility retail outlet, or a leisure facility, this project promises to deliver on every front.
Purvanchal Skyline Vista stands out as a beacon of innovation and luxury in Noida's rapidly evolving real estate market. For those with the foresight to invest in a project that seamlessly blends connectivity, creativity, and commercial potential, Purvanchal Skyline Vista offers an unparalleled gateway to success.question skyline vista purvanchal skyline vista purvanchal skyline vista sector 94 noida skyline purvanchal sector 94 noida -
company bought a software for 400€. we figured out we could not use it for its use of a proprietary file saving system without access to our own data. so i took all good features, extended them with our specific requirements and built a quite open system myself. good day. why didn't i thought of that earlier?
-
BITCOIN RECOVERY EXPERT FOR HIRE REVIEWS \\ REVENANT CYBER HACKER
Losing a Bitcoin wallet containing a substantial amount of cryptocurrency can be a devastating experience. However, the feeling of despair and loss was transformed into pure happiness when I received the incredible news from REVENANT CYBER HACKER that my lost Bitcoin wallet, holding 132,000 bitcoins, had been successfully recovered. In this article, I will share the rollercoaster emotional journey I went through when I lost my wallet, the subsequent discovery of REVENANT CYBER HACKER, the process they employed to retrieve my precious digital assets, and the lessons learned along the way. This is a story of hope, resilience, and the power of professional recovery services in restoring lost Bitcoin wallets. Ah, the sweet sound of good news. There I was, minding my own business on an average Tuesday morning, when I got a notification that would make any bitcoin enthusiast jump for joy. It was a message from none other than REVENANT CYBER HACKER, informing me that my long-lost bitcoin wallet had been found. And not just any bitcoin wallet, mind you, but one containing a whopping 132,000 units of the beloved cryptocurrency. Now, for those living under a rock or perhaps too preoccupied with the latest cat videos, let me give you a crash course in Bitcoin 101. Bitcoin is a digital currency that has taken the world by storm, captivating the minds of tech-savvy investors and casual enthusiasts alike. It operates on a decentralized network, meaning it doesn't answer to any central authority like a bank. Instead, it relies on blockchain technology, which adds a layer of security and transparency to every transaction. To own bitcoin, you need a wallet – a digital container where your precious coins reside. Think of it as a virtual piggy bank, except you don't need a hammer to break it open. Your wallet comes with a unique address, like a digital fingerprint, that allows you to send and receive bitcoin. Losing access to this wallet is as heart-wrenching as misplacing your favorite pair of socks. Trust me, it's not a pleasant feeling. My encounter with the disappearance of my Bitcoin wallet taught me a valuable lesson about the importance of implementing proper security measures. It's not enough to rely on luck or hope that your digital assets will remain safe. Taking proactive steps to protect your investments is crucial in the wild world of cryptocurrencies. From using strong and unique passwords to enabling two-factor authentication, every layer of security adds another brick to the fortress that safeguards your digital wealth. Trust me, you don't want to learn this lesson the hard way. It has changed my life to be able to retrieve my misplaced Bitcoin wallet thanks to REVENANT CYBER HACKER amazing services. It made me realize the worth of tenacity.
Website: revenantcyberhacker {DOT} org
Email: revenantcyberhacker {AT} Gmail {DOT} com
Telegram: revenantcyberhacker
WhatsApp: + 1 (208) 425-8584
WhatsApp: + 1 (913) 820-07392 -
hey, so i have recently started learning about node js and express based backend development.
can you suggest some good github repositories that showcase real life backend systems which i can use as inspiration to learn about the tech?
like for eg, i want to create a general case solution for authentication and profile management : a piece of db+api end points + models to :
- authenticate user : login/signup , session expire, o auth 2 based login/signup, multi account login, role based access, forgot password , reset password, otp login , etc
- authorise user : jwt token authentication, ip whitelisting, ssl pinning , cors, certificate based authentication , etc (
- manage user : update user profile, delete user, map services , subscriptions and transactions to user , dynamic meta properties ( which can be added/removed for a single user and not exactly part of main user profile) , etc
followed by deployment and the assoc concepts involved : deployment, clusters, load balancers, sharding ,... etc
----
these are all the buzzwords that i have heard that goes into consideration when designing a secure authentication system for a particular large scale website like linkedin or youtube. am not even sure how many of these concepts would require actual codelines and how many would require something else.
so wanted inspiration from open source content to learn about it in depth, replicate and create new better stuff if possible .
apart from that, other backend architectures like video/images storage system, or just some server for movie, social media, blog website etc would also help.2
