Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "not secure"
-
Me: I have been working for you for almost 12 years now, and I feel that my current pay is not comparable to the work I currently produce. Therefore, in order to secure my future as your employee, I must request an immediate raise in pay to a level that is acceptable.
Boss: I can't afford it. If you want more money, you need to bring in more clients, plain and simple.
Me: I'm serious. If I don't get a raise, I will qui---
Girlfriend: Babe, stop talking to yourself and come to bed...
Me: Okay... [looks in mirror] This isn't finished...12 -
The spam denier
_____
An old phone conversation with a client:
Me : Hello
Client : My website and server are suspended? why is that?
Me : Your server sends spam messages.
Client : We do not send spam messages, we are on vacation, there is none in the office.
Me : Yes, but it is not necessarily you, according to our logs, your server sent spam messages in Chinese and Russian, so someone from Russia or China....etc.
Client : I do not believe you, we do not speak russian or chinese, how could we then write spam messages in those languages?
Me : I told you, maybe someone exploited some vulnerability in your website or server firewall. And if you want to activate your services, please check with your webmaster and sysadmin to secure your ....
Client: I tell you my son, because I am old and I have more life experience than you ... I am 60 years old and I tell you, spam does not exist, and YOU suspended my website and server, and created issues to sell me more of your solutions and services.
I won't check my server, I won't hire a webmaster or a sysadmin, AND YOU WILL ACTIVATE MY SERVER NOW !
(I suddenly realized that I am talking to a wall, so I switched to a robotic tone).
Me : Please resolve the issue to activate your services..
Client : YOU WILL ACTIVATE MY S...
Me : Please resolve the issue to activate your services...
Client : WHAT IS THIS SPAM STORY ANYWAY, I DO NOT BELIEVE YOU ...
Me : Please google that word and you will understand what is spam is...
Client : YOU ARE F**ING LIARS, SPAM DOES NOT EXIST... ACTIVATE MY WEBSITE N.... Beeeep !
I hang up.
Well, I thought about configuring an automatic response for this client, or a for-loop.
His voice was really unpleasant, as if he is a heavy smoker.7 -
Another one, teach secure programming for fucks sake! This always happened at my study:
Me: so you're teaching the students doing mysql queries with php, why not teach them PDO/prepared statements by default? Then they'll know how to securely run queries from the start!
Teachers: nah, we just want to go with the basics for now!
Me: why not teach the students hashing through secure algorithms instead of always using md5?
Teacher: nah, we just want to make sure they know the basics :)
For fucks fucking sake, take your fucking responsibilities.31 -
Creating a new account is always fun...
"This Is My Secure Password" <-- Sorry, no spaces allowed.
"ThisIsMySecurePassword" <-- Sorry, Passwords must include a number
"ThisIsMySecurePassword1" <-- Sorry, Passwords must include a special character
"ThisIsMySecurePassword 1" <-- Sorry, no spaces allowed
"ThisIsMySecurePassword%1" <-- Sorry, the % character is not allowed
"ThisIsMySecurePassword_1" <-- Sorry, passwords must be shorter than 16 characters
"Fuck" <-- Sorry, passwords must longer than 6 characters
"Fuck_it" <-- Sorry, passwords can't contain bad language
"Password_1" <-- Accepted.24 -
I was reviewing one dev's work. It was in PHP. He used MD5 for password hashing. I told him to use to password_hash function as MD5 is not secure...
He said no we can't get a password from MD5 hashed string. It's one way hashing...
So I asked him to take couple of passwords from the users table and try to decode those in any online MD5 decoder and call me after that if he still thinks MD5 is secure.
I have not got any call from him since.18 -
Started talking with someone about general IT stuff. At some point we came to the subject of SSL certificates and he mentioned that 'that stuff is expensive' and so on.
Kindly told him about Let's Encrypt and also that it's free and he reacted: "Then I'd rather have no SSL, free certificates make you look like you're a cheap ass".
So I told him the principle of login/registration thingies and said that they really need SSL, whether it's free or not.
"Nahhh, then I'd still rather don't use SSL, it just looks so cheap when you're using a free certificate".
Hey you know what, what about you write that sentence on a whole fucking pack of paper, dip it into some sambal, maybe add some firecrackers and shove it up your ass? Hopefully that will bring some sense into your very empty head.
Not putting a secure connection on a website, (at all) especially when it has a FUCKING LOGIN/REGISTRATION FUNCTION (!?!?!?!!?!) is simply not fucking done in the year of TWO THOUSAND FUCKING SEVENTEEN.
'Ohh but the NSA etc won't do anything with that data'.
Has it, for one tiny motherfucking second, come to mind that there's also a thing called hackers? Malicious hackers? If your users are on hacked networks, it's easy as fuck to steal their credentials, inject shit and even deliver fucking EXPLOIT KITS.
Oh and you bet your ass the NSA will save that data, they have a whole motherfucking database of passwords they can search through with XKeyScore (snowden leaks).
Motherfucker.68 -
Ranted about him before but this just came to my mind again.
The fucking windows (to the max) fanboy I had to deal with for too long.
Every time I mentioned something about what programming language to use in a project he was NOT part of:
"I know it's none of my business, BUT I think you should use .net"
(All backend JavaScript and php guys).
Every time I mentioned something about what server system to use:
"I know it's none of my business but I think you should use Windows server"
(All Linux guys)
Every time I'd say something positive about Linux he'd search as long as needed to prove that that was also a windows thing (didn't even come close sometimes)
Every time I told the devs there about a windows security issue (as in "guys they found this thing, install the next update to stay safe :)" - "ahhh will do, thanks for letting know man!") he'd search as long as needed to prove that Linux also had had security issues like that.
(Okay?!? I know?!? I'm just trying to notify people so their systems stay secure and they're genuinely happy with that so STFU)
MOTHERFUCKER.16 -
A quite severe vulnerability was found in Skype (at least for windows, not sure about other systems) allowing anyone with system access (remote or local) to replace the update files skype downloads before updating itself with malicious versions because skype doesn't check the integrity of local files. This could allow an attacker to, once gaining access to the system, 'inject' any malicious DLL into skype by placing it in the right directory with the right file name and waiting for the user to update (except with auto updates of course).
From a company like Microsoft, taking in mind that skype has hundreds of millions of users worldwide, I'd expect them to take a very serious stance on this and work on a patch as soon as possible.
What they said about this: they won't be fixing it anytime soon as it would require a quite big rewrite of skype.
This kinda shit makes me so fucking angry, especially when it comes from big ass companies 😡. Take your fucking responsibility, Microsoft.16 -
This is super childish but it's the gameserver insidstry and karma is a bitch.
TLDR: I hacked my boss
I was working for a gameserver and I did development for about 3 months and was promised pay after the network was released. I followed through with a bunch of dev friends and the guy ended up selling our work. He didn't know that I was aware of this as he tried to tell people to not tell us but one honest person came forward and said he sold our work for about 8x the price of what he owed ALL OF US collectively.
I proceeded to change the server password and when he asked why he couldn't log in I sent him an executable (a crypted remote access tool) and told him it was an "encryption tunnel" that makes ssh and file transfers secure. Being the idiot that he is he opened it and I snagged all of his passwords including his email and I changed them through a proxy on his machine to ensure I wouldn't get two factored with Google. After I was done I deleted system 32 :334 -
I hate this attitude of my study (when i studied):
"it might be a good idea to teach the students how to program securely by default?"
"oh no but we just want to teach them the basics"
"so why not the secure basics by default?!"
"nah we just want them to get started and understand it, that's all. We'll get to the secure way later on"
Well, fuck you.13 -
"Do you have 2 factor auth for the database?"
a customer asked. I stared on the wall in front of me and suddenly fel and urge to punch and piss on something.
I took a deep breath while thinking to myself
*Oh boy, here we go. Another retard*
I put on my nice voice and asked:
"What you mean?"
The customer seems confused, as if my question did not make sense and he said:
"TWO FACTOR AUTHENTICATION! Dont you know what it is? To make the database more secure."
I was fucking right, this person reads to much shit. The fact that the email signature of that person said "Wordpress Developer" made me more angry.
I, still with the nice voice asked
"How would that work?"
"Two factor authentication when I am connecting to the database."
"So, do you want it by SMS then? You'll get alot of messages if it is going to send you one every time a query is made."
The following 7 seconds was dead silent until I heard the person hang up.3 -
Alright people, I'm gonna be blunt here, which is something not often seen from me. Thankfully this platform is used to it.
I am absolutely sick of people hating Windows/MacOS just because of the fucking practices of the companies. Let's take a look at a pro/con list of each OS type respectively.
Windows:
Pro - Most computers built for it
Pro - Average consumer friendly
Pro - Most games made for it
------------------------------------------
Con - Proprietary
Con - Shady info collection (disableable)
Con - Can take some work to customize
~
Linux:
Pro - Open source
Pro - Hundreds of versions/distros
Pro - Incredibly customizable on all fronts
------------------------------------------
Con - Can have limited modern hardware support
Con - The good stuff has a steep learning curve
Con - Tends to have unoptimized programs or semi-failed copies of Windows programs
~
MacOS:
Pro - Actually quite secure in general
Pro - Optimized to all hell (on Apple devices)
Pro - Usually just works
------------------------------------------
Con - Only (legally) usable on Apple devices
Con - Proprietary
Con - Locked down customization
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
See? None of them are perfect. Fucking get over it already. Maybe I want to use Windows because it works for me, and it actually does what I need it to. I can disable the spying shit through a few nice programs. Just because I work in IT doesn't mean that I HAVE to hate Windows and LOVE Linux! I mean, Linux is absolutely SPECTACULAR for all of my servers, but as a Desktop OS? Not there for me yet. Check one of my other rants: https://devrant.com/rants/928935/... and you'll see a lot of my gripes with Linux that Windows actually executes well. FUCK!37 -
"We don't need to invest in security - noone is going to hack us anyway" == "We don't need a fire department in our city - fire is not going to start here anyway"
We don't need to invest in security - everything is public anyway" == "We don't need a fire department in our city - our buildings are made out of straws anyway"
-- my thoughts after seing a line in client's spec: "sensitive data is transferred via a secure tcp channel (https) and all the public data is transferred via an unencrypted tcp (http) channel"3 -
"secure" messaging apps which aren't open source.
Isn't it common sense that, when you can't check an app for anything because it's closed source (backdoors, vulnerabilities etc), you technically can't be sure whether it's actually secure or not?
And no, I'm not going to trust an app dev on his/her blue fucking eyes on this one.28 -
Worst thing you've seen another dev do? So many things. Here is one...
Lead web developer had in the root of their web application config.txt (ex. http://OurPublicSite/config.txt) that contained passwords because they felt the web.config was not secure enough. Any/all applications off of the root could access the file to retrieve their credentials (sql server logins, network share passwords, etc)
When I pointed out the security flaw, the developer accused me of 'hacking' the site.
I get called into the vice-president's office which he was 'deeply concerned' about my ethical behavior and if we needed to make any personnel adjustments (grown-up speak for "Do I need to fire you over this?")
Me:"I didn't hack anything. You can navigate directly to the text file using any browser."
Dev: "Directory browsing is denied on the root folder, so you hacked something to get there."
Me: "No, I knew the name of the file so I was able to access it just like any other file."
Dev: "That is only because you have admin permissions. Normal people wouldn't have access"
Me: "I could access it from my home computer"
Dev:"BECAUSE YOU HAVE ADMIN PERMISSIONS!"
Me: "On my personal laptop where I never had to login?"
VP: "What? You mean ...no....please tell me I heard that wrong."
Dev: "No..no...its secure....no one can access that file."
<click..click>
VP: "Hmmm...I can see the system administration password right here. This is unacceptable."
Dev: "Only because your an admin too."
VP: "I'll head home over lunch and try this out on my laptop...oh wait...I left it on...I can remote into it from here"
<click..click..click..click>
VP: "OMG...there it is. That account has access to everything."
<in an almost panic>
Dev: "Only because it's you...you are an admin...that's what I'm trying to say."
Me: "That is not how our public web site works."
VP: "Thank you, but Adam and I need to discuss the next course of action. You two may go."
<Adam is her boss>
Not even 5 minutes later a company wide email was sent from Adam..
"I would like to thank <Dev> for finding and fixing the security flaw that was exposed on our site. She did a great job in securing our customer data and a great asset to our team. If you see <Dev> in the hallway, be sure to give her a big thank you!"
The "fix"? She moved the text file from the root to the bin directory, where technically, the file was no longer publicly visible.
That 'pattern' was used heavily until she was promoted to upper management and the younger webdev bucks (and does) felt storing admin-level passwords was unethical and found more secure ways to authenticate.5 -
Oh fuck and boy Jesus, how on earth is this still a thing 😦
MD fucking 5 is not a fucking “secure” crypto algorithm.
This site has 14 million breached accounts with fucking MD5 hashes.
I think I’ve had to much internet for today.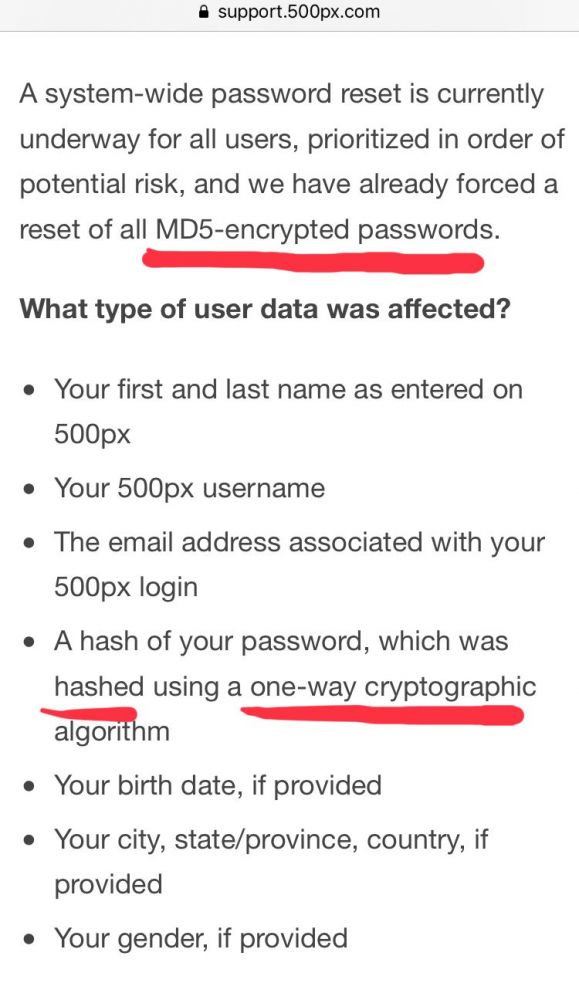 17
17 -
So I was at work and send to another location (distribution centers) and in the lunch break my guider for that day and I started a conversation about servers etc (he appeared to do loads of stuff with that). He recommended me all those programs but I didn't recognize anything so I asked him what kinda servers he ran. He runs a lot of Windows servers. No problem for me but I told him that I am into Linux servers myself.
Guy: "Linux guy, eh? That system is considered to be so secure but in reality it's insecure as fuck!".
Me: (If he would come up with real/good arguments I am not going to argue against that by the way!) Uhm howso/why would you think that?
Guy: "Well all those script kiddies being able to execute code on your system doesn't seem that secure.".
*me thinking: okay hold on, let's ask for an explanation as that doesn't make any fucking sense 😐*
Me: "Uhm how do you mean, could you elaborate on that?"
Guy: "Well since it's open source it allows anyone to run any shit on your system that they'd like. That's why windows rocks, it doesn't let outsiders execute bad code on it.".
Seriously I am wondering where the hell he heard that. My face at that moment (internally, I didn't want to start a heated discussion): 😐 😲.
Yeah that was one weird conversation and look on open source operating systems...21 -
Biggest dev insecurity?
Probably http://
It’s not secure at all, never feeling very confident when browsing that protocol.5 -
I hate Linux so much. I mean, how could anyone of you barbarians like it??
I don't understand the hate for windows. It's secure, emphasizes privacy, and it's Microsoft. What's not to love?
Linux is just proprietary malware.26 -
My hubby saw me using Secure Shell to install some software on a cloud server I'm using through the terminal. After a few minutes of watching, he said, "Oh, the government better watch out for you!"
I've been unable to successfully convince him I'm not some elite super-hacker like he's used to seeing in movies and NCIS. 7
7 -
I still miss my college days. Our crappy IT Dept restricted internet usage on campus. Each student used to get 10 GB of internet data and they used Cyberoam for login (without HTTPS). 10 GB was so less (at least for me).
Now, thanks to CS50, I learned that HTTP was not secure and somehow you can access login credentials. I spent a night figuring things out and then bam!! Wireshark!!!!
I went to the Central Library and connected using Wireshark. Within a matter of minutes, I got more than 30 user ids and passwords. One of them belonged to a Professor. And guess what, it had unlimited data usage with multiple logins. I felt like I was a millionaire. On my farewell, I calculated how much data I used. It was in TBs.
Lesson: Always secure your URLs.5 -
"Pre-Installed Malware Found On 5 Million Popular Android Phones"
"added somewhere along the supply chain"
See below how to check if it's installed
Sources:
- (new) https://thehackernews.com/2018/03/...
- (new) https://research.checkpoint.com/rot...
- (old relevant news) https://thehackernews.com/2017/03/...
---
"Rottensys" a malware which covers devices from: Honor, Huawei, Xiaomi, OPPO, Vivo, Samsung and GIONEE
---
"According to our findings, the RottenSys malware began propagating in September 2016. By March 12, 2018, 4,964,460 devices were infected by RottenSys," researchers said.
"At this moment, the massive malware campaign pushes an adware component to all infected devices that aggressively displays advertisements on the device’s home screen, as pop-up windows or full-screen ads to generate fraudulent ad-revenues."
---
If you have one of the affected devices, here's how I checked mine:
1. Install ADB (Windows: https://forum.xda-developers.com/sh...)
2. Connect your device in USB-debugging mode
3. execute "adb shell 'pm list packages -f' > output.txt" (On windows navigate to C:\adb and replace "adb" with ".\adb.exe")
4. open the now created output.txt
5. search for any of those:
com.android.yellowcalendarz (每日黄历)
com.changmi.launcher (畅米桌面)
com.android.services.securewifi (系统WIFI服务)
com.system.service.zdsgt 19
19 -
- Let's make the authentication system so the user can only login in one device at time, because this is more secure.
- You know that this will be a general-public application, right?
- Yeah!
- Sou you want to "punish" users with a logoff on the other device when he tries to login in a new one?
- Yeah!
- But before you said we will use Json Web Token to make the backend stateless.
- Yeah!
- And how will we check if the token is the last one generated?
- We will store the last generated token for this user on a table in our DB.
- So... you are basically describing the old authentication model, with session tokens stored on the backend and communicating them via cookies.
- Yeah, but the token will be sent on the Header, not on cookies
- Okay, so why will we use Json Web Token to do this in the first place?
- Because this is how they're doing now, and this will make the backend stateless.
A moment of silence, please.8 -
I'm not sure if this entirely qualifies and I might have ranted about it a few years ago but fuck it.
My last internship. Company was awesome and my mentor/technical manager got along very well with me to the point that he often asked me to help out with Linux based stuff (he preferred Linux but was a C# guy and wasn't as familiar with it as me (Linux)).
We had to build an internal site thingy (don't remember what it was) and we delivered (me and some interns) and then the publishing moment came so I went to out project manager (a not-as-technical one) and asked if he could install a LetsEncrypt certificate on the site (he knew how and was one of the only ones who had direct access to the server).
He just stared at us and asked why the fuck we needed that since it was an internal thing anyways.
I kindly told that since it's free and can secure the connection, I preferred that and since its more secure, why the fuck not?
He wasn't convinced so it was off.
Next day I came in early and asked my mentor if he could do the SSL since he usually had access to that stuff. He stared at me with "what?" eyes and I explained what the PM said.
Then he immediately ssh'd in and got the damn cert with "we're going to go secure by default, of course!"
A minute later it was all set.2 -
Would the web be better off, if there was zero frontend scripting? There would be HTML5 video/audio, but zero client side JS.
Browsers wouldn't understand script tags, they wouldn't have javascript engines, and they wouldn't have to worry about new standards and deprecations.
Browsers would be MUCH more secure, and use way less memory and CPU resources.
What would we really be missing?
If you build less bloated pages, you would not really need ajax calls, page reloads would be cheap. Animated menus do not add anything functionally, and could be done using css as well. Complicated webapps... well maybe those should just be desktop/mobile apps.
Pages would contain less annoying elements, no tracking or crypto mining scripts, no mouse tracking, no exploitative spam alerts.
Why don't we just deprecate JS in the browser, completely?
I think it would be worth it.22 -
"Use a .dev domain? Not anymore."
Just read a medium article and thought some would be interested in reading it too, as I personally didn't know many of the information published there, for example:
- .dev gTLD belongs to google and nobody can register one
- .dev TLD are required to have a secure connection in chromium/chrome from now on, forcing you to use self signed certs across all development machines
"When applications opened for gTLDs in 2012, Google didn’t just apply for .dev. They applied for 101 gTLDs, including .google, .play, and .app. However, Google wasn’t the only company to apply for many of these gTLDs. For some applications, it took years for applicants to negotiate who would end up with the rights to the name. Google’s application for .dev was pending for over a year. Finally, in December 2014, their application for .dev was granted."
"In 2015, Chromium added the entire .google TLD to the HSTS preload list with little fanfare. It was the first and only TLD entry in the list for two years, until .dev was added in September and shortly followed by .foo, .page, .app, and .chrome — all Google-owned gTLDs."
Source: “Use a .dev domain? Not anymore.” @koop https://medium.engineering/use-a-de... 33
33 -
!rant && sarcasm
For a long time now I've been trying to convince people to use secure communication. I'm used to getting called "paranoid", but the killer phrase always was (and still is): "Why do you want me to encrypt my communication, I HAVE NOTHING TO HIDE, so I don't care who's reading it" - "It's not about hiding something, it's about private stuff staying private" - "Yeah, whatever"
"I have nothing to hide". That always killed the conversation... until I asked them to hand me their phones, unlocked, for 5 minutes.
"No" - "Why? I thought, you had nothing to hide and don't care who's reading it?" - "Uhmmm..."
More and more people around me are popping up in my Signal contact list.
Looks like they suddenly care a lot about private stuff staying private </sarcasm>11 -
"please use a secure password*"
* But don't make it too secure, 20 Charakters is enough.
Why would you fucking do this? The only reason I can think about is a scenario like this:
"How do we store the passwords in the database?"
"Just like anything else?"
"So I create a VARCHAR(20)?"
"Yeah why not? It's good enough for a name, and you shouldn't use your or anyone else's name as a password, so it should be perfect"10 -
TL;DR I'm fucking sick and tired of Devs cutting corners on security! Things can't be simply hidden a bit; security needs to be integral to your entire process and solution. Please learn from my story and be one of the good guys!
As I mentioned before my company used plain text passwords in a legacy app (was not allowed to fix it) and that we finally moved away from it. A big win! However not the end of our issues.
Those Idiot still use hardcoded passwords in code. A practice that almost resulted in a leak of the DB admin password when we had to publish a repo for deployment purposes. Luckily I didn't search and there is something like BFG repo cleaner.
I have tried to remedy this by providing a nice library to handle all kinds of config (easy config injection) and a default json file that is always ignored by git. Although this helped a lot they still remain idiots.
The first project in another language and boom hardcoded password. Dev said I'll just remove before going live. First of all I don't believe him. Second of all I asked from history? "No a commit will be good enough..."
Last week we had to fix a leak of copyrighted contend.
How did this happen you ask? Well the secure upload field was not used because they thought that the normal one was good enough. "It's fine as long the URL to the file is not published. Besides now we can also use it to upload files that need to be published here"
This is so fucking stupid on so many levels. NEVER MIX SECURE AND INSECURE CONTENT it is confusing and hard to maintain. Hiding behind a URL that thousands of people have access to is also not going to work. We have the proof now...
Will they learn? Maybe for a short while but I remain sceptic. I hope a few DevrRanters do!7 -
Client reads about MomgoDB ransomware attacks online.
Him: I heard that the MongoDB is not secure, we should use something else in our system.
Me: Those databases got attacked because security features were turned off. If you want you can have an external security team to test the system when it's done.
Him: I don't wana take any risk, so I we should use something else.
We have been working on this system for almost a year and the final stage was supposed to be delivered in a month.
He wants me to replace it with MySQL11 -
draw.io is moving to diagrams.net, because .io domains are not secure.
Source: https://diagrams.net/blog/... 12
12 -
*logs out of Google on Android*
*has this persistent Google search bar on launcher which I keep on accidentally tapping*
Alright, so I'm not logged into Google to see how it goes. Kind of an experiment to see just how intertwined Android and my life are with Google. And it's going quite well actually, except for my prime apps that I can't seem to get around.
*reads Google privacy policy*
"We protect your data by keeping it secure!"
Hmm, yeah.. you and 3 letter agencies are keeping it secure and out of the hands of other individuals.. that makes sense.
Don't be evil.. unless you're the devil, right?
Fuck you, I won't login like this.
*accidentally opens Google*
*le trending results show up*
- KSI vs Logan Paul weigh-in!
- KSI vs Logan Paul Manchester!
- KSI vs Logan Paul arena fight!
*opens up NewPipe in which I am not logged in either*
- KSI vs Logan Paul!!!
- Did you see the KSI vs Logan Paul stuff yet?!
*logs back into Google straight away*
Personalized search engine.. many hate it, but boy do I fucking love it.rant disney idiots obnoxious cunts fuck that logan fuck that jake kid too wtf is wrong with people who the fuck watches those morons4 -
A few years ago I configured my wifi extender.
Got everything working as I wanted.
Changed password to my favorite 24char password.
Can't login again...
Meh... It's working as I want and is secure, not even I can login.
It's still running in this state.3 -
If programming languages had honest slogans, what would they be?
C: If you want a horse, make sure you feed it, clean it and secure it yourself. No warranties.
C++: If you want a horse, you need to buy a circus along with it.
Java: Before you buy a horse - buy a piece of land, build a house in that land, build a barn beside the house & if you are not bankrupt yet, buy the horse and then put the horse in the barn.
C#: You don’t want a horse, but Microsoft wants you to have a horse. Now it’s up to you if you want Microsoft or not.
Swift: Don’t buy an overpriced Unicorn if all you wanted was a horse.
JavaScript: If you want to buy a horse & confidently ride it, make sure you read a book named "You don't know horse".
PHP: After enough optimization, your horse can compete the top most horses in the world; but deep down, you'll always know it's an ass.
Hack: Let's face it, even if you take the ass from the ass lovers and give them back a horse in exchange, not many will ride it.
Ruby: If you want a horse, make sure you ride it on top of rail roads, even if the horse can't run fast on rails.
Python: Don't ride your horse and eat your sandwich on the same line, until you indent it on the next line.
Bash: Your horse may shit everywhere, but at least it gets the job done.
R: You are the horse. R will ride you.
Got this from Quora.
https://quora.com/If-programming-la...7 -
Let me explain a tiny corner of some awful code I read earlier today, in layman’s terms.
It’s a method to see if the user is in a secure session — not to set up the session, just to see if it exists. The method ends with a question mark, so it’s basically a question. It should look up the info (without changing anything) and should always give a clear yes/no answer. Makes sense, right?
Let’s say the question is “am I in school right now?”
The code… well.
If there isn’t a student, the answer it gives is null, not yes or no. Null is a fancy word for no, pretty much, so that’s kinda fine, but it really should be a simple no.
It then checks to see if the school is open today. If it is open, it then checks to see if I made my lunch, if I took my backpack, and if I rode the bus — and makes these things happen if they didn’t. Forgot my backpack? Just ask “am I in school today?” And poof! There’s my backpack! … but only if the school is open.
It then, finally, checks to see if I’m actually in the school, and gives that answer.
It could just see if I’m in the school — I mean, I could be in school without a backpack, or walked there on the weekend, right? Ha! You and your silly logic have no place here.
So, by asking if the user is in a secure session, we change the answer: they weren’t before, but the act of asking makes it so. This isn’t profound or anything: I don’t work with Schrödinger. My coworkers are just idiots.
And no, the rest of the code isn’t any better…5 -
Can someone explain to me why the fuck I should even care about the fact, that some companies collect, use and sell my data? I'm not famous, I'm not a politician and I'm not a criminal, I think most of us aren't and won't ever be. We aren't important. So what is this whole bullshittery all about? I seriously don't get it and I find it somewhat weird that especially tech guys and IT "experts" in the media constantly just make up these overly creepy scenarios about big unsafe data collecting companies "stealing" your "private" information. Welcome to the internet, now get the fuck over it or just don't be online. It's your choice, not their's.
I honestly think, some of these "security" companies and "experts" are just making this whole thing bigger than it actually is, because it's a damn good selling point. You can tell people that your app is safe and they'll believe you and buy your shit app because they don't understand and don't care what "safe" or "unsafe" means in this context. They just want to be secure against these "evil monster" companies. The same companies, which you portrayed them as "evil" and "unfair" and "mean" and "unrepentant" for over a decade now.
Just stop it now. All your crappy new "secure" messenger apps have failed awesomely. Delete your life now, please. This isn't about net neutrality or safety on the internet. This is all about you, permanently exaggerating about security and permanently training people to be introverted paranoid egoistic shit people so that they buy your elitist bullshit software.
Sorry for my low english skills, but please stop to exist, thank you.64 -
I love how the Keybase Linux client installs itself straight into /keybase. Unix directory structure guidelines? Oh no, those don't apply to us. And after uninstalling the application they don't even remove the directory. Leaving dirt and not even having the courtesy to clean it up. Their engineers sure are one of a kind.
Also, remember that EFAIL case? I received an email from them at the time, stating some stuff that was about as consistent as their respect for Unix directory structure guidelines. Overtyping straight from said email here:
[…] and our filesystem all do not use PGP.
> whatever that means.
The only time you'll ever use PGP encryption in Keybase is when you're sitting there thinking "Oh, I really want to use legacy PGP encryption."
> Legacy encryption.. yeah right. Just as legacy as Vim is, isn't it?
You have PGP as part of your cryptographic identity.
> OH REALLY?! NO SHIT!!! I ACTIVELY USED 3 OS'S AND FAILED ON 2 BECAUSE OF YOUR SHITTY CLIENT, JUST TO UPLOAD MY FUCKING PUBLIC KEY!!!
You'll want to remove your PGP key from your Keybase identity.
> Hmm, yeah you might want to do so. Not because EFAIL or anything, just because Keybase clearly is a total failure on all levels.
Written quickly,
the Keybase team
> Well that's fucking clear. Could've taken some time to think before hitting "Send" though.
Don't get me wrong, I love the initiatives like this with all my heart, and greatly encourage secure messaging that leverages PGP. But when the implementation sucks this much, I start to ask myself questions about whether I should really trust this thing with my private conversations. Luckily I refrained from uploading my private key to their servers, otherwise I would've been really fucked. -
Foday my father argued with me that:
* "HTML programmers" get payed a lot
* WordPress is awesome
* wordpress programmers get payed a lot
* WordPress doesn't need to be secure
* FileMaker is 100% virus-free (probably malware free), because not many people use it
* UX and UI design are exactly the same6 -
Ten Immutable Laws Of Security
Law #1: If a bad guy can persuade you to run his program on your computer, it's not solely your computer anymore.
Law #2: If a bad guy can alter the operating system on your computer, it's not your computer anymore.
Law #3: If a bad guy has unrestricted physical access to your computer, it's not your computer anymore.
Law #4: If you allow a bad guy to run active content in your website, it's not your website any more.
Law #5: Weak passwords trump strong security.
Law #6: A computer is only as secure as the administrator is trustworthy.
Law #7: Encrypted data is only as secure as its decryption key.
Law #8: An out-of-date antimalware scanner is only marginally better than no scanner at all.
Law #9: Absolute anonymity isn't practically achievable, online or offline.
Law #10: Technology is not a panacea.3 -
Me : I should start building user authentication system.
inner self : there are enough free and secure ones out there, just go read the documentation.
Me : fuck I'm not reading 10000 pages of documentation written in alien language.
inner self : well then you better start building
Me : **writes code
Inner self : you better add the data validation and security while coding
Me : I just want it to work !
Me after a few days trying not to suicide : the site is hacked, the code is bugged, hello darkness my friend5 -
What. The. Actual. Fuck.
My co-workers just tried to convince me that the following is a secure password:
"ThisIsASecurePassword2018"
Just... I mean... Why? *sigh*
Their argumentation is based on the new NIST guidelines.
If they've read these guidelines CAREFULLY though... (not only the appendix) it actually states "Don't use words from the dictionary". Passwords like these should even be rejected right away.15 -
The cleaning lady saga continues yet again..
Here in Belgium, cleaning ladies are paid with cheques. All fine and dandy, and apparently the parent organization (Sodexo) even migrated to digital cheques. Amazing!!!
If only they did it properly.
Just now I received an email with my login data.
Login: ${FIRSTNAME}${FIRST2CHARSOFLASTNAME}
Password: I won't reveal the amount of characters.. but it's not even hex. It's just uppercase letters, and far from what I'd deem even remotely secure. Hopefully I'll be able to change that shitty password shortly, and not get it mailed back, even when I ask for recovery. Guess I'll have to check that later - the person who made that account was pretty incompetent when it comes to tech after all. Don't ask me why they did it instead of me. I honestly don't really know either.
With that said, this is a government organization after all... Can I really expect them to hash their passwords?24 -
I've been training a client for a few months now to not use Slack for sharing passwords and other secure materials.
I really thought I had made great progress. I even had him using a password manager. Then out of nowhere he sends the wildcard SSL key pair to me and a handful of other devs in a Slack thread.
At least we aren't storing important information like medical records. Oh wait, that's exactly what we're doing.6 -
Can someone please explain to me WHY THE FUCK non devs feel like they know shit. I DON'T GIVE A FUCK ABOUT HOW YOU FOUND SOME UNTRUE SHIT ON GIZMODO. I'VE KNOW SO MUCH ABOUT THIS SHIT, AND YOU LOOKED UP THE FIRST EXAMPLE YOU COULD FIND THE SUPPORTS YOUR CASE. The most recent time this happened was OVER THE LAST FEW DAYS when this DUMBASS that my friends and I BULLY but HE STILL HANGS AROUND. (By bully, yes sometimes we are mean to him, but we're not out to get him. He comes to us and we don't wanna be with him). So after the SEVENTH groupchat (on two apps) he created that night, HE WANTED TO SWITCH BACK TO ANOTHER APP I SPENT A WEEK TRYING TO GET THEM TO SWITCH FROM PREVIOUSLY (It was whatsapp, i got them to switch to telegram). THEN HE TRIED to ARGUE with me about how TELEGRAM wasnt secure. HE SEARCHED "is telegram secure" on Google and chose the FIRST ARTICE from the previously mentioned, GIZMODO which says that TELEGRAM chats ARENT ENCRYPTED by DEFAULT. HOW THE FUCK DO DUMBASSES GET THIS KIND OF PUBLICITY. There's a difference between ENCRYPTION and END TO END DUMBASS. Then he told me whatsapp is more secure than telegram. NO ITS FUCKING NOT. In telegram, your encryption keys CHANGE every chat, or every 100 messages. To my best research, whatsapp only has ONE key per USER. I could go on forever about how chat backups in whatsapp are UNENCRYPTED or how FACEBOOK stores your data, but blocked you works to.6
-
When you ask the IT-Department of a company collab with Microsoft, why you aren't allowed to use Firefox instead of IE.
The answer is: "It's insecure because it's open source"
YOU FUCKING KIDDING ME INSECURE ??? IT IS MORE SECURE AS IE!!! INSECURE BECAUSE OPEN SOURCE? THAN LET'S USE CHROME OR OPERA INSTEAD BUT NOT IE1 -
So this PR company hired my firm to convert their client's Wix website to WordPress to have better control over content and SEO, not to mention get away from the piss-poor "absolute position everything" setup of Wix. This is a single page design. 2 days later, we deliver it, performing faster than Wix and with a few extra goodies on the UI.
The client's director of IT wants to stay on Wix, because it's "the most secure provider", and will only move their ONE PAGE INFORMATIONAL WEBSITE to another platform and host if they answer a 133 item "security questionnaire". Short of SSNs, they want to basically know everything, including our proprietary and confidential security practices. You aren't Google...stop acting like you are...
How are people this stupid a "director" of anything?3 -
At my previous job we had to complete an online security training exercise. It shows you how to behave secure in the work place, to not open unknown links etc. The scary part was that the entire training thing was BUILT IN FUCKING FLASH. So I'm suppose to listen to some god damn virus shitting flash application on how to do online security?! Get your shit together before teaching others.5
-
I just blocked some of the top management from connecting to our WLAN because I was testing a verifing feature for said WiFi that kicks all devices not listed in the DB.
It happened while my boss/senior/guidance was trying to show them the advantages of a centrally managed infrastructure.
He covered my ass well and tried to sell it to them as proof of a secure solution, that unknown devices couldn't log in.
I feel like human trash right now, but that's what you get for testing in production.4 -
I request the VPN credential to access to an italian big company network.
The ask me the email to send the new credentials.
I reply sviluppo@mycompany.it
They say it's not good, it's not associated only to me.
I said I'm the only developer (sviluppo) in my company.
They reply the is more secure my private gmail account.
They sent the credentials to my gmail account.3 -
When I get on a site that is like “your password must contain upper case, lower case, a number, a symbol”, at first I’m like ooook, security I guess I’ll generate a long password, but then they sit there and say “and be at least 6 but not more than 10 characters”
WTF you fuckers really don’t know anything do you.2 -
The company I work for is requiring customers to submit credit card info in an online form which then gets stored into our "secure database". Which employees then pull and charge the card later on. They're also telling customers that the form is "encrypted". This is all because they're too fucking lazy and not patient enough to wait for someone to integrate a payment gateway. This is a lawsuit waiting to happen.5
-
Earlier i ranted about how someone hacked our site and he had our source code.
Now finally we found how was our site code stolen, thanks to @dfox he mentioned how can we pull code from got server at that time I checked trying commamds to dowload git folder but it was secure but later we found that we had another subdomain running for pur project and its git folder was not secured16 -
One of the more memorable computer problems I solved were when I added some lego blocks to solve a recurring windows bluescreen
A friend had a Pentium 3 (slot 1) that kept throwing him several bluescrens per day so I decided to help
I open up the computer and saw that the processor were not properly securred in it's place and the plastic pieces that should have holding it in place were gone, so I improvised pressing in some lego pieces that I found somewhere to secure that the processor didn't move if someone were walking close to the computer and after that he didn't have any more bluescreens than the rest of us4 -
Rant:
Why in the freezing cold all people think that linux = secure. Ransomware... Bla bla not happening on linux bla bla... Linux is secure.
If Linux would have been the most popular one people will pretty much run everything on root and install every stupid package available and never run: apt-get update.
Users were so dumb they got scammed by a phising mail... In freaking 2017... This is user stupidity not OS fault...
God its stupidly annoying seeing the same stuff : Linux secure...
Everything can be secure if you paid attention to the same stuff in freaking 2000.30 -
To this day I can't figure out why people still drink the windows koolaid.
It's less secure, slower, bloatier (is that a word?), Comes with ads, intrudes on privacy, etc. People say it's easier to use than Linux, but 99% of what anyone does happens on a chrome based web browser which is the same on all systems!
When it comes to dev, it boggles the mind that people will virtualize a Linux kernel in Windows to use npm, docker, k8s, pip, composer, git, vim, etc. What is Windows doing for you but making your life more complicated? All your favorite browsers and IDEs work on Linux, and so will your commands out of the box.
Maybe an argument can be made for gaming, but that's a chicken an egg scenario. Games aren't built for Linux because the Linux market is too small to be worth supporting, not that the games won't work on it...20 -
A friend of mine and I decided we wanted to fork linux and port it to C++.
Sounds crazy yea, but there are many benefits:
1) More secure due to ability to use references
2) More sustainable due to the extensive standard lib
Not only would we port linux to C++, we would improve it as far as possible.
So now for the part of the rant where I misuse devRant as an advertizement platform. to those interested in helping, here is the poll where you can get included into the mailing list:
https://docs.google.com/forms/d/...11 -
Massive payment gateway (not gonna say names) with more then 10k transactions / hour telling md5 is one of most secure encryptions they have. Only to made worse by the fact that they send the key and hashed key in the same request.
I am advising all our clients to change payment gateway asap if they use this one.1 -
Situation: My lead dev (read as in, my employee that has the lead developer position, not my superior) is complaining about certain decisions being made in regards to a rather large project that has been stagnated by executive political bullshit.
Me: let them fuck themselves over, it is their decision to have a voice on this and we are not the ones developing it, merely managing the resources.
Him: Well they do not know what they are asking! everyone is wanting to have an opinion! a voice!!!
Me: and by their own volition they will fuck themselves over and I have the proper documentation to show everyone that if the project is delayed, it will be by popular vote. I have already spoke to our VP to let him know that we are not taking part in their decision planning process, that we provide the necessary feedback, they get to do with it what they want regarding their decisions.
Him: they are being really stupid and inconsiderate
Me: they are indeed, but as long as I show that you, me, and the rest of the team provided input, they disregarded it and went with their decision, then then the fault is on them, not you or our team. Let them fuck themselves over, I have the documentation needed to secure our asses, I record every conversation and I have every email saved. Really, if they don't want to listen to you they will not be able to point the issues that will inevitably rise back to you or us.
Him: .... you are evil
Me: fuck with me team see what happens. Their face and reaction is what makes me get a hard on after the fact.
Ain't no one touching my team.10 -
I'm sick of the tyranny of websites who say your password must include at least one shady character, one special agent, and a number of other filthy things. Only makes your passwords impossible to remember, hard to type, and not a bit more secure.
"mynameisronalddumpandimanorangehairedorangutan" is a million times more secure than "P4$$word".13 -
!rant
In july chrome will mark all http-pages as not secure and firefox will follow.
Worst of all, those insecure pages won't be allowed to access the microphone and other features any more. What will i do in cafes now?12 -
About browsers and whole SSL CERT thing...
Most likely everyone here noticed, that https site with broken certificate will throw these big red warnings, in your face and there is so much wording like "ITS NOT SECUREEEE" or "ITS HACKEDDD" almost like it was written by passionate fanatic.
But when you are on plaintext http browsers reaction is like ¯\_(ツ)_/¯
Even if you have plaintext with password, it will for example in chromium put small little red thingy that almost no one notices.
I believe that broken cert with some error like invalid date is MORE secure than plaintext password, yet still there is this hypocracy with browsers...
I dont say that broken SSL cert is good, or something, Im just pointing out contrast of "broken" https vs plain http.... One looks for casual Joe like end of the world is coming and second is bearly noticable. Da fuck?
I disagree with this approach17 -
I think most people are annoyed by the new design of chrome, for all the wrong reasons - I just noticed the TLS indicator lock is now gray when encrypted, giving you the idea of a website being not fully secure imho6
-
Hey! You there!
Are you sick of windows 10 sending you intrusive reminders about updates? Are you tired of random unscheduled restarts? Tired of feeling like you have no control over your own computer?
Take back control!
DO THE FUCKING UPDATE, YOU FUCKING INCOMPETENT, USELESS, LAZY, PIECE OF DRY WANK!
Seriously guys: pick a time convenient to you, and take 5 or 10 minutes (when you're likely spending hours at your computer), and do them. Not only will you get rid of the annoying notifications, but you'll also keep your pc safe and secure by keeping up with security patches. C'mon people, it's really not that difficult.
And can we please, for the love of all things holy, stop the circlejerking? You're developers, you are the computer proficient. The only things a PC will do are the things you tell it to do. Dig deep, dig into the registry, dig into the services manager, dig into the fucking settings cos a good number of the most common complaints can be fixed in the basic options menu. Tell your computer to stop doing the things you don't like and it will stop.
It's really not hard!16 -
Being a programmer for a while now it always irritates me to try to explain what I'm working on to friends and family. I forget what I knew before I developed. I'm always like "I made the strings in the database- oh I mean the words...well they're actually more like strings of letters- well anyway I made a code to sanitize the user input- I mean make it so it is secure before uhhh saving." I spend so much time watering what I'm saying down I forget what I'm talking about
It's not even funny. It'd be funny if one single person in my family or friend group understood what I meant to some degree.3 -
One thing every junior web developer learns is how to implement a login system.
They may not make it the most secure, but it works.
It boggles my mind how Microsoft still don't know how to make a login that works consistently.
Every Microsoft login page requires like 30 redirections to work.
The Teams app on my PC fails to login at least once a week, just because another Microsoft app is logged in using the same account (usually office), but Windows is not.
Microsoft needs to take it's head out of it's ass and BEG Google to teach them how to make a decent login system.4 -
When you spend 5+ minutes creating a secure password for your new bank account and you get a message saying the password must be between 6 and 12 characters long.
Not sure I want to open this account any more.
Fuck me.6 -
watching the online course for CEH... dude used the Death Star as a tangible example of how exploits work.
IDK if I should love it for the nerdiness, or be slightly sad that someone needs that type of example of what a vulnerability vs an exploit is, when they're going for the Certified Ethical Hacker certification...
Might be better in an introduction to Network Security class?
Also, while discussing the security, usability, and functionality triangle, he reference the Staples "Easy Button" - does one thing, not very secure, and not very functional (in that it has more than one function)...1 -
!rant
For the second time in a row, one of our customers decided not to pay their server. The server, on which a lot of the work we did for them (online shop) was hosted. Shortly after completion, we specifically told them to backup their stuff on a daily basis, secure their server and regularly update it... Guess who did neither of those things, in addition to not paying their server after more than 5 reminders, and still complains about their shop being offline. Fucking idiots.2 -
Just went to book something online. About to click the "Pay" button and noticed the page wasn't secure. Who the hell, in 2017, captures credit card details via insecure 'http'??? And 'https' worked on the home page but not the payment page!! Backed out of that, messaged them and we'll see if anything comes of it.3
-
I'm a game designer student in a Brazilian university. In my class I'm the only one who likes code and made the secure choice to be a future game programmer.
But recently some dudes on my class started to discourage me and telling me to give up that course and change to a computer science course.
I didn't feel that way... I think game programmers who know all the stuff and process of game development( modelling, concepts etc) are better professionals than the ones who just knows the scripting process. But sometimes their opinion flows up my head and I feel so unknown if I staying in the right way or not.
(Sry if my english still bad..hope you all understand anyway)17 -
Security lifehacks 101
Why pay for password managers? Just use one secure password for every service you use! Password managers are really designed for fools who don’t know that you can just use one password for every service and who are ready to pay for that shit.
The best practice is to use your name starting with a capital letter + your main credit card number + CVC code from the back of that card as your go-to password. It’s long and hard to bruteforce and you can remember everything that way! You just need to remember that one password and you’ll always remember your payment info! No need for apple’s bad Apple Pay which is not so secure after all like everything else that Apple offers.19 -
why do i have an iphone?
well, let's start with the cons of android.
- its less secure. this isn't even arguable. it took the fbi a month or something (i forget) to break into an ios device
- permission, permissions, permissions. many of the android apps i use ask for the not obscure permissions.
· no, you don't need access to my contacts
· no, you don't need access to my camera to take notes
· no, you don't need access to my microphone to send messages
· no, you don't need access to my saved passwords to be a functioning calculator
- not being able to block some apps from an internet connection
- using an operating system created and maintained by an advertising company, aka no more privacy
- i like ios's cupertino more than material design, but that's just personal preference
pros of ios:
- being able to use imessage, at my school if you don't have an iphone you're just not allowed to be in the group chat
- the reliability. i've yet a data loss issue
- the design and feel. it just feels premium
- if i could afford it, ios seems like a lot of fun to develop for (running a hackintosh vm compiled a flutter app 2x as fast as it did on not-a-vm windows)
so that's why i like iphones
google sucks55 -
ESET Antivirus is a strange animal. On one hand, it seems reasonably well written, because unlike Norton or F-Secure, it doesn't subject your computer to death by constant disk access and 100% CPU load for 10 minutes when you start it.
On the other hand, when I clicked the link in the mail about renewing licenses and filled out the form, I was not redirected to a page where I could enter credit cart details.
Instead, I got message that some representative would get back to me in 1-2 work days. Eh, what? It's a digital product for f***'s sake. Now, I suppose they'll send me a hand written letter (written using a quill, no doubt), delivered by a bloke riding a horse and wearing a tricorn.
Well, at least ESET virus definition updates are pushed on the internet, and not sent out on 5.25" diskettes.3 -
My mom asked me to speed up her PC's startup process. I looked into it and and probably found the problem: G Data.
I told her she has to delete it, there is windows defender anyways (and virus scanners are just snake oil). She refused and said: But I bought it from the local IT shop. They said it is the best.
I said: Yeah because they cannot sell windows defender...
She still argued that she paid for it and wants to keep it.
That was were I said: then enjoy your slow startups.
She also said she feels more secure with it. 🙄
I would not even be able to work with that PC! Its not old at all, but the permanent scanning comes at a high cost and probably does not help much.
But she trusts that local it store guy more than me apparently.5 -
We are required to use corporate SSO for any authenticated internal websites, and one of the features they require you to implement is a "logout" button.
They provide a whole slew of specifications, including size and placement/visibility, etc. They provide an SSO logout URL you must redirect to after you take care of your own application logout tasks.
Makes sense... except the logout URL they provide to serve the actual SSO logout function broke over 3 months ago, and remains non-functional to this day.
Apparently I'm the first person (and perhaps one of the only people) who reported it, and was told "just not to worry about it".
So, we have a standing feature request to provide a button... that doesn't actually work.
Corporate Security - Making your corporation _appear_ more secure every day...2 -
After a court ruling, the privacy focused email provider Tutanota has been forced to create plaintext copies of emails.
In the future, a court can order copies of emails, before they are saved encrypted on the email servers. Tutanota says, end-to-end encrypted emails would remain secure and they would "rather want to implement extended privacy enhancements for customers instead of extended access for government entities", but they would follow the law.
A few months ago, in a similar case, the constitutional court ordered another mail provider - Posteo - to save IP addresses on court request, even if they do not save them regularly.
Interestingly, the law the court based its decision on, might be not longer relevant for mail services.
Source (German): https://sueddeutsche.de/digital/...9 -
Clients r wankers. He wants to be able to send login details incl passwords in email to his clients when he adds them in the cms. The passwords are encrypted and generated on creation of a new user. Ive told him that sending credentials in email is shit and not secure. The stubborn bastard wont budge, so instead i've put explicit instructions to reset password once logged in with the credentials they send. Any other suggestions?3
-
Providing a web site to pay electricity and other services, but guess what? THE CONNECTION IS NOT SeCuRe !! (What can possibly can go wRoNg).
This retarded country have a lot of skilled people, but the dinosaurs who in charge are literally afraid of new technology.
Wake up bitches, it's almost 2020 -
So a few weeks ago I wiped my MacBook Pro to regain some space and speed, it wasn't really that slow I just had the disk partitioned into two installments of MacOS. When I erased the disk I thought the secure thing to do would be to set the format to journaled, encrypted rather than just journaled. Everything was working fine, there seemed to be this weird step of login when I restarted but whatever, except iCloud Drive. On my iMac it works fine but for whatever reason my MacBook Pro doesn't want to download custom folders (ones that aren't created by an app and don't have an app icon on folder icon) from my account despite them being clearly available in iCloud.com. So after this much time of messing with it I'm wiping my MacBook Pro again and formatting it as journaled (not encrypted). Wish me luck...undefined this must just be a bug or a security feature... probs a bug tho i still like apple products this stuff usually works for me3
-
My arguments about Apple:
- "iPhone 12 camera can be better than anything else because it's more advanced, it has LiDAR and 10-bit codecs"
- "I can copy on my iPhone and paste on my MacBook and vice versa out of the box"
- "My Beats can seamlessly switch from playing from my MacBook to my iPhone to my Apple Watch. I can be exercising with only my Apple Watch and my Beats, no need for iPhone"
- "2K screen with nice colors in a 900g laptop is rare if you consider the price. Apple one is the cheapest one with that characteristics"
- "Apple Pay is convenient"
- "Fingerprint scanners fail with wet fingers no matter if it's ultrasonic or optical, LiDAR Face ID is objectively more secure than any camera-based unlock mechanism"
- "Stainless steel frame feels better than aluminum one"
I'm not saying Apple is the best. I'm not saying that Google Pay doesn't exist or that Apple Pay is better. I'm not saying that Apple has no downsides.
However, these are responses I get:
"But Apple IS crapple, immutably"
"Why are you even looking at apple crap if you want something good"
If you want to bash Apple, bash it for something real like that butterfly keyboard fails, unconventional AirPods shape that makes most people's ears hurt, screen coating fails on MacBooks, App Store commissions.47 -
Managed to land 2 interviews:
The first one was for a startup that was looking for a react programmer (I've never used react before).
The later was a php job at a big company. They told me they used cakephp which is a framework I had not used before either.
Still, I'm more familiar with php than react so I felt more confident with the second interview. However, I felt there was a lot of good chemistry going on in the first interview.
The interviewer was incredibly nice (he was the lead dev, not an HR person as opposed to the second interviewer)
He gave me a small react test to be completed within a week. I barely managed to do it in time but I felt good about the solution.
Just as I was sending it, I get a call from the second interviewer saying I landed the php job.
I wasn't sure if my novice react skills would be impressive enough to secure me the react job (and I really needed a job) so I accepted.
After explaining everything to the guy who was interviewing me for the react job, he understood and was kind enough to schedule a code review where he walked through my novice code explaining what could be improved, helping me learn more in the process.
I regret not accepting the react position. The PHP they got me working with is fucking PHP5 with Cake2 :/
Don't get me wrong, I like the salary and the people are nice but the tech stack they're using (lacking source control by the way!), as well as all the lengthy meetings are soul-draining.6 -
Security fail here. I've just started a PPI claim and have been provided a link to a so called "very secure" client area.
There are no username or passwords and the screenshot is not a first time sign up screen.
All I need to login is a surname, postcode and DOB - all information easy enough to find online.
Pretty bad IMO, esp, so considering the effort required to add a proper login using a username/password combination.
I mean I'm logged in now and have no option to set an account password :| 3
3 -
Suck my hairy asshole, devs who disable paste for web forms. Or more likely, management softs who read in a trade magazine that paste is bad.1
-
A classmate saw me using Firefox today and laughed at me saying Chrome is more secure. I'm not very knowledgeable about the security; I use Firefox because it uses less memory and it's more stable on my machine.
I doubt that info of his is current so can someone who actually knows about the security give me some counter-arguments for him? The more facts the better :D14 -
I don't understand privacy advocators.
Am I the only one who wouldn't give up practicality in exchange for "potentially more secure"?
I don't understand so much what the deal is with people who avoid Facebook, or don't trust Google or Microsoft, just in the basis of "privacy" or "security".
Websites tracking you to serve ads? Well, it's pointless because I very rarely buy something from the internet or let myself be influenced, ads are waste of time, just use an adblocker.
I can pretty much upload my whole life or documents on Google drive, even if I made it public no one would really care or read it all. It's like that GitHub project you uploaded but never documented, so no one cares. I usually use alternative software not because of "privacy" but because it has features other software doesn't have.
In reality you realize people aren't that interested in your life more than their own life.24 -
Whelp. I started making a very simple website with a single-page design, which I intended to use for managing my own personal knowledge on a particular subject matter, with some basic categorization features and a simple rich text editor for entering data. Partly as an exercise in web development, and partly due to not being happy with existing options out there. All was going well...
...and then feature creep happened. Now I have implemented support for multiple users with different access levels; user profiles; encrypted login system (and encrypted cookies that contain no sensitive data lol) and session handling according to (perceived) best practices; secure password recovery; user-management interface for admins; public, private and group-based sections with multiple categories and posts in each category that can be sorted by sort order value or drag and drop; custom user-created groups where they can give other users access to their sections; notifications; context menus for everything; post & user flagging system, moderation queue and support system; post revisions with comparison between different revisions; support for mobile devices and touch/swipe gestures to open/close menus or navigate between posts; easily extendible css themes with two different dark themes and one ugly as heck light theme; lazy loading of images in posts that won't load until you actually open them; auto-saving of posts in case of browser crash or accidental navigation away from page; plus various other small stuff like syntax highlighting for code, internal post linking, favouriting of posts, free-text filter, no-javascript mode, invitation system, secure (yeah right) image uploading, post-locking...
On my TODO-list: Comment and/or upvote system, spoiler tag, GDPR compliance (if I ever launch it haha), data-limits, a simple user action log for admins/moderators, overall improved security measures, refactor various controllers, clean up the code...
It STILL uses a single-page design, and the amount of feature requests (and bugs) added to my Trello board increases exponentially with every passing week. No other living person has seen the website yet, and at the pace I'm going, humanity will have gone through at least one major extinction event before I consider it "done" enough to show anyone.
help4 -
Boss: We don't want to use PHP because it's open source we want to keep all the applications secure and want Microsoft to support us whenever some thing happens to ASP.NET applications.
Me: But we will be using PHP on intranet applications and it won't be for public. ASP.NET is also open source.
Boss: No, we cant take that risk.
I'm not sure whose right over here. PS: All the applications we built are for internal purpose only.14 -
The worst thing I have seen a dev do?
- Have all the APIs work without an access token for our main product which handles ~10k requests a day.
- Calling our architecture secure in the crucial investor meeting and being 'confident' that our database can not be compromised. No wonder we did not get funded.3 -
My boss did not care about making things secure in our early development stage, even though I told him several times.
After 1 day our elastic search cluster was filled with random crappy data.
Fix: Apply security schemes provided by AWS1 -
Hmm...recently I've seen an increase in the idea of raising security awareness at a user level...but really now , it gets me thinking , why not raise security awareness at a coding level ? Just having one guy do encryption and encoding most certainly isn't enough for an app to be considered secure . In this day an age where most apps are web based and even open source some of them , I think that first of all it should be our duty to protect the customer/consumer rather than make him protect himself . Most of everyone knows how to get user input from the UI but how many out here actually think that the normal dummy user might actually type unintentional malicious code which would break the app or give him access to something he shouldn't be allowed into ? I've seen very few developers/software architects/engineers actually take the blame for insecure code . I've seen people build apps starting on an unacceptable idea security wise and then in the end thinking of patching in filters , encryptions , encodings , tokens and days before release realise that their app is half broken because they didn't start the whole project in a more secure way for the user .
Just my two cents...we as devs should be more aware of coding in a way that makes apps more secure from and for the user rather than saying that we had some epic mythical hackers pull all the user tables that also contained unhashed unencrypted passwords by using magix . It certainly isn't magic , it's just our bad coding that lets outside code interact with our own code . -
I'd never do anything "risky" in a prod environment if I considered it so at the time, but in retrospect there's *lots* of things considered risky now (both from a security and good practice viewpoint) that were standard practice not long ago:
- Not using any form of version control
- No tests (including no unit tests)
- Not considering XSS vulnerabilities
- Completely ignoring CSRF vulnerabilities
- Storing passwords as unsalted MD5 hashes (heck that was considered very *secure* in the days of plaintext password storage.)
...etc. I'm guilty of all of those previously. I daresay in the future there will be yet more things that may be standard practice now, but become taboos we look back on with similar disdain.1 -
API Documentation: All API request should be made over https connections.
Me: Ok, (sees url bar), SECURE, good!
(sees curl code)
curl -X GET 'http://shittyapi.com/api/v2/users'
Me: (gasps) huh?
(heads to http://shittyapi.com/api/v2)
Me: Ok, (sees address bar) NOT SECURE
.
.
.
.
.
(long silence)5 -
With the movement of people recently deleting their facebook accounts, this actually covers a valid concern I didn't even think of, since I personally don't use that feature at all, nor have I ever used it.
People that used the "login with facebook" a lot, especially with websites that exclusively use it, will flush not only their facebook account doing that, but also all accounts they have ever used to log in with facebook, if not actually thought as far as checking the apps section of facebook and trying to migrate your account, which is also rarely possible.
So basically many people that do use it, simply won't delete their facebook account, because it has this backup parachute attached with its strings, that does not allow for an easy exit, except for literally ripping it all out and losing every account it seems.
Ignore dashlanes self advertisement bullshit at the bottom, the blog itself is still highly valuable in itself.
Source: https://blog.dashlane.com/delete-fa... 12
12 -
When i was younger, lesser experienced and more naive than now; i got away with a lot of things. By lot of things i mean security flaws in my applications and overall architecture. I realise now i could've so easily been pawned.
Not that i claim to be totally secure even now, or would ever. It is a process, slow and painful one - Learning.
What i wish to point out is the role of favorable probability (non believers would call it luck). Security is so much about it. You get away with so many things for so long. And bang one day the roll of dice is unfavorable. On such rare occasions, just look back and wonder - damn i should've been breached long ago.rant hindsight security fail looking back security luck vulnerabilities food for thought musings naive probability2 -
My grandfather is at age 72 & don't know much about technology. He forward me this message on whatsapp bcz I'm a software engineer. He made my day...
What is the difference between http and https ?
Time to know this with 32 lakh debit cards compromised in India.
Many of you may be aware of this difference, but it is
worth sharing for any that are not.....
The main difference between http:// and https:// is all
about keeping you secure
HTTP stands for Hyper Text Transfer Protocol
The S (big surprise) stands for "Secure".. If you visit a
Website or web page, and look at the address in the web browser, it is likely begin with the following: http:///.
This means that the website is talking to your browser using
the regular unsecured language. In other words, it is possible for someone to "eavesdrop" on your computer's conversation with the Website. If you fill out a form on the website, someone might see the information you send to that site.
This is why you never ever enter your credit card number in an
Http website! But if the web address begins with https://, that means your computer is talking to the website in a
Secure code that no one can eavesdrop on.
You understand why this is so important, right?
If a website ever asks you to enter your Credit/Debit card
Information, you should automatically look to see if the web
address begins with https://.
If it doesn't, You should NEVER enter sensitive
Information....such as a credit/debit card number.
PASS IT ON (You may save someone a lot of grief).
GK:
While checking the name of any website, first look for the domain extension (.com or .org, .co.in, .net etc). The name just before this is the domain name of the website. Eg, in the above example, http://amazon.diwali-festivals.com, the word before .com is "diwali-festivals" (and NOT "amazon"). So, this webpage does not belong to amazon.com but belongs to "diwali-festivals.com", which we all haven't heard before.
You can similarly check for bank frauds.
Before your ebanking logins, make sure that the name just before ".com" is the name of your bank. "Something.icicibank.com" belongs to icici, but icicibank.some1else.com belongs to "some1else".
👆 *Simple but good knowledge to have at times like these* 👆3 -
A "secure" IoT framework, that integrates with the current system and helps in future implementations as well.
More importantly it would be universally adopted, open source and not proprietary .
Kinda working on something like it for a side project but really dunno where it'll end up! :/2 -
I was once asked to create a fully secure chat system prototype (the ui didn't matter) in 2 days. We ended up building a client in python (which I wrote) and it kinda worked and a c# backend that didn't really work.
1 hour before we had to present the project to some high up management we decided that we couldn't fix the bugs in the system.
So I came up with a cool idea. Why not use ssh?
So I set up a bash script that writes to a file and tail -f that reads from the file. That way you could chat securely with another person.
I made it 15 minutes before the presentation with no Internet working :) they said it was hacky but a cool solution they saw that day :p I felt happy and that I had to thank Linux for being there for me2 -
Wanted to make an account on Payoneer to get paid from 99designs for the stuff I make there.
Entered my password, got error.
"Please use only the latin alphabet, a-z and 0-9"
SERIOUSLY, it's banking stuff. how can they not allow secure passwords? *sitting here, crying"6 -
Anyone wanting to improve OpenSSL fulltime?
Understanding of Cryptography or ability to write secure code are not required...
https://openssl.org/blog/blog/...4 -
Do you know what angers me more than anything else ?
Wasted potential. Thats what. That there are people out there that look at their bank account and see a large number and spend large amounts of time finding ways to push people down during sensitive times where they could be learning and growing and have the right attitude and energy to do so, just because it makes their horrible selves feel secure knowing how 'superior' daddy made them, not to mention likely factories filled with half naked Chinese kids sewing shoes and soccer balls and separating out precious metals with blow torches.
I cannot help but think about this again as I'm frustrated that I had to relearn something just now which created more questions which I once everything is dashed to pieces again I won't think to or know to look into, if the information even exists, all so some easily duped younger people can form the next generation of well... us, and fall for the same tricks while I feel like I'm falling behind.3 -
For all the hate against windows I built over the now 8 years using linux as my main os. Now I feel windows 10 is quite good.
I got a little beefier desktop lately, been using just laptops from the last 8 years(8D) so I got this urge to get a desktop for gaming, I bought an entry level machine. ryzen 5 2400g, put my lovely linux mint and... the fucking machine was hanging up when the load was too high, and the load was too high too often because react/node etc.
I gave up in less than a day, I just did a quick search and some people said about secure boot or whatnot, some other claimed that ryzen cpus had no problem with mint, I got fed up quickly and did not try any solution with linux. Then I installed windows 10, installed the godamned drivers from the provided dvd ... since then it was a breeze.
The dark mode is gorgeous and no hanging up at all... I'm just sad that mint did not worked soo well. I wanted to have consistency between my laptop/desktop and I loved mint above everything. But well, some things improve while you're not looking at them, win 10 is quite good, I'll keep my desktop as gaming/programming pc with win 10, and well, the laptop will be auxiliar programming machine.
¯\_(ツ)_/¯4 -
Am I the only one worried with the OS wars lately? Microsoft and Apple trying to gain even more control on everything and Linux remaining at less than 2% on the desktop. People are oblivious to the fact that their personal freedom is at risk, and don't you dare tell me otherwise. Companies knowing what we search or what files we have on our computer, having the ability to control us and force us to follow their rules. We have a choice, and I'm not talking about destroying the economical system a la Mr. Robot, but moving to the Open Source world, not because it's more secure, faster or some such shit, but because it's the only way to ensure freedom on one of the biggest part of our lifes, the digital part. My concerns may be exceeding the normal, and I'll hate it to be right, but I'm afraid that if this goes on, in a few years, we'll understand that we made a big mistake...21
-
Workarounds are great. I remember one time, I had a server that let anyone access any file as long as the knew the right path. I wanted to store data in a .txt (it wasnt secure passwords or anything, so calmyourtities), but then had access too it. Now, this server wasn't running anything except PHP, so I created a database.php, and within was just some php tags. I ended up modifying the database.php from other PHP scripts and storing all the data as PHP comment, then parsing thru it as I needed, so loading mydomain.biz/database.php wouldn't show the data. ex of my database.php (to all that might not understand because I'm bad at explaining):
<?php
//USER1:DATA1
//USER2:DATA2
?>2 -
I had a wonderful run-in with corporate security at a credit card processing company last year (I won't name them this time).
I was asked design an application that allowed users in a secure room to receive instructions for putting gift cards into envelopes, print labels and send the envelopes to the post. There were all sorts of rules about what combinations of cards could go in which envelopes etc etc, but that wasn't the hard part.
These folks had a dedicated label printer for printing the address labels, in their secure room.
The address data was in a database in the server room.
On separate networks.
And there was absolutely no way that the corporate security folks would let an application that had access to a printer that was on a different network also have access to the address data.
So I took a look at the legacy application to see what they did, to hopefully use as a precedent.
They had an unsecured web page (no, not an API, a web page) that listed the addresses to be printed. And a Windows application running on the users' PC that was quietly scraping that page to print the labels.
Luckily, it ceased to be an issue for me, as the whole IT department suddenly got outsourced to India, so it became some Indian's problem to solve.2 -
Webmin because why not ✓
Lamp stack ✓
Dynamic DNS client ✓
PhpMyAdmin X
Dear DigitalOcean. SINCE WHEN do you consider a PMA installation
without Https SECURE?
And why the fuck do you make me install an aptitude package that skips both file system AND Apache config cleanup on purging?
It's just a raspberry, but if it runs lamp I want PMA, and if it runs anything, I want Https. Is that too much to ask for from a tutorial source otherwise so reliable that I do anything you say without a questioning thought?8 -
Decrypt api responses in an iOS app which my “senior” dev thinks it is more secure to encrypt responses in stead of setting up a proper SSL cert (they use plain http to save money 🙄)
They disable the encryption since it does not function as we wanted and set up SSL instead🙄4 -
So... I finally decided to secure my VPS, so I started with sudo less /var/log/auth.log ...
Short story, not even gonna read every line, just gonna reset my VPS lol10 -
Had to do a change tonight - not once but twice my server secure login account was locked. And server security don't answer their pages. I couldn't even reverse my changes if my changes break something else.
My account has not been locked in over a year but happens twice in a 90 minute window. What are the chances? -
Is it legal to destroy other company's site or app. because they didn't pay your money in the past?
and also app they created is not secure.
The company is in another country.
.
.
.
If "No"
I'll still do that. I don't care.4 -
Firefox developer fucked up this morning my development after the update -_-
The fucking "Enhancing Tracking Protection" was on a local Wi-Fi IP address(192.168...) which automatically redirected to the https of that IP, but I did setup kestrel to listen on HTTP, which resulted in a nice "Cannot enstablich a secure connection(and suck it up because ¯\_(ツ)_/¯)"
Fortunately it's easy to get rid off this cunt, just go on the shield nearby the address and disable that motherfucker.
ps: sorry for the lil rage, my morning train trip development brain cells should not be bothered by this automatic technical troubles
Further question to the Firefox developers:
WHAT THE FUCK are you thinking when you force developers to automatic HTTPS redirection when you should know more than anyone that development is 360deg(and not 90 like your mom) 1
1 -
-Rant-
How do you (not) secure your Rest based web service?
1. Chain it to shady organic authentication system built by a hoard of monkeys high on Tequila.
2. have secret keys that get copy pasted into config flat files, and index them on your code search engine.
3. make the onboarding extremely platform specific that you need 500 environment variables, 50 scripts, 5 fancy device presses and a tap dance to make a GET call to the service.
4. fish through 500 rotating log files that the authentication system generates for each API call made.
5. Leave traces all over the host so if you have to start over, you should sudo rm -rf / and set fire to your computer. -
RANT!
I still struggle to find the suitable address book software for our company. It supposed to be secure and inexpensive. But how so? It's flipping not possible to have both!
My boss answer to almost everything I say: Just do it! - in German: einfach machen! Please hulp!10 -
Do you, guys, have any VPN suggestions? I'm mostly looking for a VPN that doesn't throttle your speed, allows and encrypts P2P connections and is secure and reliable. I'm not quite sure what other more specific requirements I'm looking for, since I'm not too knowledgeable in this domain, but I'm nonetheless thanking you in advance :D7
-
Who would be interested in reviewing an old peice of Python code I wrote..? It's a few years old, and it uses basic procedual generation to cypher text (entry, or ASCII files) using a hashed password. It's a command line tool.
I used to brag about how "secure" it was, and now I'm curious if it is secure or not.
I plan on picking it back up and open-sourcing it, but I want to know what problems might be wrong with it now.9 -
For all the hate that Java gets, this *not rant* is to appreciate the Spring Boot/Cloud & Netty for without them I would not be half as productive as I am at my job.
Just to highlight a few of these life savers:
- Spring security: many features but I will just mention robust authorization out of the box
- Netflix Feign & Hystrix: easy circuit breaking & fallback pattern.
- Spring Data: consistent data access patterns & out of the box functionality regardless of the data source: eg relational & document dbs, redis etc with managed offerings integrations as well. The abstraction here is something to marvel at.
- Spring Boot Actuator: Out of the box health checks that check all integrations: Db, Redis, Mail,Disk, RabbitMQ etc which are crucial for Kubernetes readiness/liveness health checks.
- Spring Cloud Stream: Another abstraction for the messaging layer that decouples application logic from the binder ie could be kafka, rabbitmq etc
- SpringFox Swagger - Fantastic swagger documentation integration that allows always up to date API docs via annotations that can be converted to a swagger.yml if need be.
- Last but not least - Netty: Implementing secure non-blocking network applications is not trivial. This framework has made it easier for us to implement a protocol server on top of UDP using Java & all the support that comes with Spring.
For these & many more am grateful for Java & the big big community of devs that love & support it. -
I got notified that tomorrow I'm gonna start a porting project from a FileNet ecosystem.
Well, I don't know what is FileNet, but at least I've enough time to study its architecture. Let's start from the official IBM page:
The FileNet® P8 platform offers enterprise-level scalability and flexibility to handle the most demanding content challenges, the most complex business processes, and integration to all your existing systems. FileNet P8 is a reliable, scalable, and highly available enterprise platform that enables you to capture, store, manage, secure, and process information to increase operational efficiency and lower total cost of ownership.
Thank you IBM, now I surely know how to use FileNet. Well, I hope that wikipedia explains me what it is:
FileNet is a company acquired by IBM, developed software to help enterprises manage their content and business processes.
Oh my god. I tried searching half an hour so far and everything I found was just advertisements and not a clue about what it is.
Then they wonder why I hate IBM so much4 -
Dev industry develop so fast. This is because information available anywhere in the internet and people try to learn any programming language they want . But only few know whether they following secure coding practice or not
But the thing is most of Dev people dosent care about security. They focus just to develop a application but not to secure it?2 -
A peeve of mine is when someone in the software industry denigrates a technology/tool/framework outside of his role eg webdevs on sysadmin stuff or viceversa.
I'm not trying to shame anyone for having subjective experiences, I just think that if you're gonna talk about tools that are not on your domain, then you need to be twice as humble as usual.
I'm a webdev and I don't post around how I KNOW how to make ssh secure, while other people devote their entire careers to that and all related matters.
What prompted me is seeing some not webdevs do this here that seem to be sysadmins/devops (can't tell for sure since I don't know them), but in real life, I've seen people from any role do this, webdevs too, even testers!
Imagine you had cancer, and you had a tumor extraction, and the oncologist said to the surgeon "step aside son, let me show you how to deal with cancer".5 -
Not much of a SQL Dev, still an apprentice and had a basic run throughs. Client needed a migration script to run, which I was assigned. Took me a good 6/7 days to make, transfer over a secure (and VERY slow) network took 2 hours. Infrastructure 3rd party took 2 days to clear and run. After all that process. I then realise, I left the fucking rollback in1
-
I seriously love rsync. Whoever made that utility is my hero. Not only that its CLI client is amazing and full of features, but rsync in daemon mode makes secure file synchronization a breeze! <38
-
I discovered a commit message from one of my (senior) colleagues today. It made me shudder. It read, 'Just adding some changes made outside of source control and deployed (over last 12 months)'.
I genuinely think he can't follow any processes he didn't design. He controls the servers too, so it's not like any pipeline would prevent him from just doing what he wants. It's a bit scary to be honest, he thinks MD5 is a secure password hash! -
I'm currently planning to set myselv up with some vps/dedicated server's for a project. What i plan to do to secure these servers is.
*Use centos 7
* Setup Wireguard and join all of the servers +1 client (my pc) to that network
*Disable SSH Access from outside that VPN
*Only allow RSA Key login to the Servers
*Install Cockpit for monitoring
*Intall docker/kubernetes for the applications i plan to run
What do you guys think of that as a baseline? Im not sure if my lower powered VPS (VPS M SSD from Contabo) will work as Kubernetes Nodes, does anyone have experience with that?
In general these Servers will be used for my projects and other fooling around.
If you guys have other suggestions for Securing/monitoring or other software i could put on to have more control without eating up to much of the Servers power, let me know :D12 -
Screw all the people who think standard email is "secure". It is not suitible for sending passwords and SSN numbers.
How can something Equifax or Marriott hacks have happened and people are still ok sending out information like this in plain text?!
I know their hacks weren't email released but still.....should be a good time to up some security standards. Right?2 -
I never understood how people have any problems with getting paid for freelancing work, when middleman/escrow platforms like upwork exist, just don't be retarded when applying for a job. I am so sick of those shit ass stories from people telling me "my client didnt pay meeee 😭😭😭" ITS YOUR FAULT. I never had any client not paying, if you don't have the option of escrow, then just fucking put remote execution via "update" system in for fucks sake or give remote control to the client while monitoring it, there is so much fucking ways to secure yourself, just don't be retarded and many clients instantly show their character when talking budget and turnaround time.15
-
I absolutely hate software to the point where I started converting from sysadmin to becoming more like a dev. That way I could just write my own implementations at will. Easier said than done, that's for sure. And it goes both ways.
I think that in order to be a good dev, you need these skills the most:
- Problem solving skills
- Creativity, you're making stuff
- Logical reasoning
- Connecting the dots
- Reading complex documentation
- Breaking down said documentation
- A strong desire to create order and patterns
- ...
If you don't have the above, you may still be able to become a dev.. but it would be harder for sure, and in some cases acceptance will be lower (seriously, learn to Google!)
One thing I don't think you need in development is mathematics. Sure there's a correlation between it and logic reasoning, but you're not solving big mathematical monsters here. At most you'd probably be dealing with arrays and loops (well.. program logic).
Also, written and spoken English! The language of the internet must be known. If it's not your first language, learn it. All the good (and crucial) documentation out there is in English after all.
One final thing would be security in my opinion, since you're releasing your application to the internet and may even run certain services, and deal with a lot of user data. Making those things secure takes some effort and knowledge on security, but it's so worth it. At the most basic level, it requires a certain mindset: "how would I break this thing I just made?"4 -
I wanna go back to the age where a C program was considered secure and isolated based on its system interface rathe than its speed. I want a future where safety does not imply inefficiency. I hate spectre and I hate that an abstraction as simple and robust as assembly is so leaky that just by exposing it you've pretty much forfeited all your secrets.
And I especially hate that we chose to solve this by locking down everything rather than inventing an abstraction that's a similarly good compile target but better represents CPUs and therefore does not leak.21 -
THREE DAYS of debugging, reading all the logs I could find, creating tens of new logs in our appliaction, and SUDDENLY an email from your IT admin:
"Hey your CURL requests are being rejected by my !oh so secure! firewall rule".
Not that I haven't said at the beggining, that THIS IS YOUR F...G NETWORK PROBLEM because we get "connection reset by peer" errors, and you ASSURED that everything is CHECKED and OK! 5
5 -
My very first time was when I first saw a Web page, I really wanted to know how they did it. Two weeks later I built an intranet at home and I thought I was so cool I was shitting out ice cubes.
The very first programme I ever wrote was a secret diary application(C#) for myself I thought it was really secure because I had my own file extension. Not one of my finer moments.4 -
Someone mentioned that client want to use wordpress instead of they current website because it is cheaper! Ok lets see how cheap it is.. each time wp release update after updating you need go through all website and check if nothing is broken.. plugins will need update as well because usually they run on specific wp version. Fixing theme and plugins requires dev time.. despite all those things.. have common sense. Maybe it is good for some type of business to host few pages without any business logic or use as blog without scare to loose everything and do not store users data.. someone mentioned that it is secure to run anything because updates are the best security to avoid security breaches. So why banks are not running on WP? Why health service is not using WP?
-
So, WPA2 was proven not fully secure. Wonder how much time it will take for most devices to be patched...2
-
Not promoting any app, but people should care more about what they use. The most used services are the least secure
 8
8 -
I just got my third 128GB MicroSD card off Amazon, this time SanDisk. Yet again, trying to do anything not involving the OEM full-disk exFAT partition staying intact (which, fuck that, all that uses that is Windows and Linux, i'm looking for splitting this thicc bih up) shifts EVERYTHING, including MBR+PT/GPT down the disk by 16MB exactly inserting data from... the atmosphere? whatever's using it? ...do SD cards have that secure key/DRM store space thing still?
(EDIT: I do verify that they ARE genuinely the right size after purchasing before reformatting or repartitioning, by the way.)
First it was a Silicon Power card, then a Samsung card, now a SanDisk.
(Also, why all S?)
Luckily, this time it wasn't a pain in the ass to get it to read as anything but "Bad Card" or a 0-byte/empty/non-existent device in Windows/Linux (respectively) so I was able to see that it was indeed the same issue without taking 3 days to jump through device hoops to finally get it to do it again but in such a way that it shifts out and back in all zeroes.2 -
I can be manipulated. Yes, I’m now more resilient to manipulation than ever because I’m autistically good at recognising patterns, yet I’m not perfect.
For a manipulator, there is just one problem — now and then, my disorder obliterates my entire worldview, together with the foreign manipulative framework, so I can start with a blank slate. It protects me. Yes, this protection is akin to our body’s “we’ll boil all the germs in our own blood” tactic that instead of defining winners and losers only leave survivors, yet the force is unstoppable. You cannot secure the land that is hit by a tornado every three months.
That inner Nemesis is so strong that it even defeated a complex, almost fractal-like manipulation of my own mother that I lived in since birth, leaving her with a wound that will never heal. Wannabe manipulator exes didn’t even stand a chance. I don’t care if that force destroys me or not, as during that time, there is no “me”.
About my mom, long story short, she told me “I want to stop treating my cancer to die as soon as possible just to not see you anymore” after my coming-out. Full story is here:
- part 1: https://devrant.com/rants/4923052/...
- part 2: https://devrant.com/rants/4924040/...5 -
How do you guys fight the urge to just screw it and implement a not so secure way of doing things, when you've been fighting with a bug for weeks?
No one would know!! 😂1 -
Guys, please use caddyserver as your webserver! It creates official tls certs for you without you having to do anything. Help making the web secure. There are too many websites that do not have any security.8
-
What makes free ssl "Unsuitable for e-commerce websites", Please read to end to see my view point.
From Namecheap:
Free Certificates are domain validation only which means they don't certify the identity of the website owner, they simply ensure a secure connection. Customers can't be sure of the integrity and trustworthiness of the website owner. If you need to secure credit card and personal information on e-commerce websites, free certificates aren't the answer. It's important your customers trust your business is safe enough to hand over these details. To gain this trust, you need a certification of your authenticity, which you can only get with a (paid) Business Validation or Extended Validation SSL Certificates.
https://namecheap.com/security/...
* "To gain this trust, you need a certification of your authenticity"
~ But isn't that just Domain Verification and other Extras, What justifies somebody or business's authenticity? Tax Id, Valid Address, Nobody is going to study the ssl cert to make sure that amazon.com is a valid business and has a tax Id.
* "domain validation only which means they don't certify the identity of the website owner,"
~ Wouldn't this just be the domain validation test that is required when using services like LetsEncrypt using Certbot etc, or are we referencing back to this idea that they look for a Valid Tax Id sort of thing?
* "If you need to secure credit card and personal information on e-commerce websites, free certificates aren't the answer"
~ Why is the paid version going to do double encryption, is the CA going to run a monitoring tool to scan for intrusions like a IDS or IPS? (disregard the use of DNS Validation being in the picture)
Am I missing something, this just seems like well crafted text to get people to buy a cert, I could understand if the encryption was handled differently, Maybe if they checked the site for HSTS or HTTPs Redirect or even, They blocked wildcard SSL before and now with the paid its included, but overall it doesn't sound like anything special. Now I'm not just picking on namecheap because domain.com does the same.14 -
Officially faster bruteforcing:
https://pastebin.com/uBFwkwTj
Provided toy values for others to try. Haven't tested if it works with cryptographic secure prime pairs (gcf(p, q) == 1)
It's a 50% reduction in time to bruteforce a semiprime. But I also have some inroads to a/30.
It's not "broke prime factorization for good!" levels of fast, but its still pretty nifty.
Could use decimal support with higher precision so I don't cause massive overflows on larger numbers, but this is just a demonstration after all.10 -
Filling out IRS forms using the Brave browser in privacy mode:
---------
Access Denied
You don't have permission to access "http://sa.www4.irs.gov/modiein/...?" on this server.
Reference #18.cfc3117.1714401007.25a9c99f
https://errors.edgesuite.net/18.cfc...
---------
Filling it out using ridiculously non-secure regular Chrome browser which exposes bookmarks, history, and cookies to anyone with enough knowledge:
"Right this way, sir. Don't worry, your data is in safe hands. We're totally not mining your data for leverage against you for your political leanings in a future tax audit."3 -
My university has "Economics and Technic" on its name and it straight up fails on the technical side.
We don't have proper wifi because nobody from the management wants to be responsible for whatever the fuck students do, so they borrow the public (not secure/shitty) wifi from the state for us. Great. We could also use Eduroam, except it only works OUTSIDE of the university for some fujing reason.
Also, our classrooms don't have plugs to charge our notebooks so that's not an option, I guess they just think: "well if they can't use their notebooks they might as well not use any internet at all".
With the heatwave in Europe the servers almost fried bcs management was not sure if they should turn it off or not. We got no server a day.
To top it off, for some reason, every time I access the Intranet from the university it won't login and it literally blocks my dns requests. FANTASTICAL. I even tried restoring my computer and it does the same shit, so I just gave up on it entirely.
TL;DR: My university has shitty IT-Infrastructure and I need to rant about it.
Thank you for sharing ze pain™6 -
Sus!
yesterday I bought a cool domain in namecheap, I was very lucky to find short and good one for my case.
Today (at weekends!!!!) I receive a letter:
>Hello **redacted name**,
>
>We are contacting you from the Namecheap Risk Management Team regarding your '**redacted name account**' account.
>
>Unfortunately, your Namecheap account was flagged by our fraud screening system as requiring verification and was locked.
>
>Please follow the instructions below to get your account verified:
>
>- take a color photo of the credit card used for the payment at **redacted link**
>
>Please make sure all of the edges of the credit card are visible, and that we can clearly see the card holder's name, expiration, and last four digits of the card number. The screenshots or images of the card cannot be accepted for verification. >If the submission does not meet these requirements, we can either request to submit the details again or permanently suspend your account.
>
>- provide a valid phone number and the best time to call you (within normal business hours, US Pacific time).
>
>If we do not hear back from you within 24 hours, we will be forced to cancel your orders.
>
>We apologize for any inconvenience that may result from this process. This extra verification is done for your security and to ensure that orders are legitimate. This industry, unfortunately, has a high rate of fraudulent orders, and this sort of >verification helps us drastically reduce fraud and ensure our customers remain secure. Such documents are used for verification only and are not provided to third parties in any way. Account verification is a one-time procedure, after your account >is verified, you will never face this issue again.
>
>Looking forward to your reply.
>
>---------------
>Dmitriy K.
>Risk Management
> Namecheap, Inc.
what if I did not notice it in 24 hours? It is the weekend for god's sake! People usually rest until monday.
They would what, cancel order and scalpel it to super high price?!
I have some doubts if the request is trully having anti fraudulent origins.
What if I used digital visa card? How was I supposed to photo it?
And the service they provided for photoing accepts only photos from web camera. I was lucky that I bought recently web camera with high enough amount of pixel power and manual focus. What if I did not?
That's all really SUS!
The person can not notice the letter within 24 hours time frame until the morning, when it would be already too late.10 -
Project with partner company, during the meeting I asked them how can we secure the communication between two services. I suggested api keys, tokens. They were like nope, no need. But I asked them for their IPs to do whitelisting on our side in Nginx.
But their side, nah not even whitelisting, no tokens, no validations. If one has address, can send anything from anywhere.
How hard would it be to do at least, AT LEAST simple token validation. And they are using the very old IIS server. I think for them as long as data flows in as expected, it is fine.3 -
Question for people familiar/knowledgeable about hardware keys;
Do you know if the OnlyKey could be considered safe/secure and if not, any idea as for alternatives?
My requirements would be nearly all the features that OnlyKey has, water/shockproof and the system should at least be open source.4 -
I am trying to "invent" secure client-side authentication where all data are stored in browser encrypted and only accessible with the correct password. My question is, what is your opinion about my idea. If you think it is not secure or there is possible backdoor, let me know.
// INPUT:
- test string (hidden, random, random length)
- password
- password again
// THEN:
- hash test string with sha-512
- encrypt test string with password
- save hash of test string
// AUTH:
- decrypt test string
- hash decrypted string with sha-512
- compare hashes
- create password hash sha-512 (and delete password from memory, so you cannot get it somehow - possible hole here because hash is reversible with brute force)
// DATA PROCESSING
- encrypt/decrypt with password hash as secret (AES-256)
Thanks!
EDIT: Maybe some salt for test string would be nice8 -
Thoughts on Session as a secure messenger? It looks fine at a glance, especially not using PII like a phone number, but I haven’t delved into it — and honestly don’t have the mental energy to.
What’s everyone’s thoughts on it?6 -
Plz help...
I’m a student and developer, working every night my butt off for the last 2 years, not going to sleep till 2,3,4,5am, and taking tablets to keep my brain running and not fall asleep. Getting clients and about to sell my programming company in 2 months...
My programming teacher teaches the class such basic shit, she explains the topic very well, but for me she’s explaining how to do 2+2... last time I starred of to the window and almost started crying...
I’m very passionate about programming, Work sucks cause I need to make secure smart systems with math that take forever, I want to at least enjoy it In class, but it’s torture, fucking torture...
What should I do?4 -
I am looking for new programming language to learn and I found D language. It looks interesting but I think that community is weak and there is lack of some usefull libraries.
For example I can not find secure PRNG.
So my questions are:
> Have you any experience with this language?
> It is worth to learn?3 -
Anyone ever tried Embedded Swift?
I should have posted this as a joke but, guess what Apple does NOT use when developing Embedded Swift stuff for their Secure Enclave firmware...
Yep, they don't use Xcode! 🤣🤣🤣🤣
(ok, I know, not surprising, but love the irony!)11 -
So tired of explaining other stupid developers that POST is not more secure than GET in a ReST api. I have heard many times if you use GET you will be hacked :|
-
FUCK you "WP iThemes Security Pro".
First of all, your FUCKing services isn't really secure, more like security by obscurity.
Don't get me started on how you probably don't have a dedicated team of security experts.
But oh well, the customer insisted I must install you, despite my advise.
Second of all, Don't FUCKing send me emails regarding "Scheduled malware scan failed" without it containing the FUCKing error message, not some generic "http_request_failed" error, why did it FUCKing fail?
Last but not least: Don't FUCKing clutter is with with your giant ass logo that takes up half my screen or FUCKing spam such as your upcoming events, newly published books/articles, incorrect "documentation"2 -
While attempting to quit smoking and after spending a full day trying to understand why the previous devs took this approach to encrypting a string and my lack of nicotine addled brain not allowing me to see that this was a “Secure”String and so uses a machine specific key (that’s why the code that worked locally wouldn’t run on production 😑) this is my rant on comments added to the helper I had to write
/// <summary>
/// If you are using this class and it's not for backward compatibility - then you probably shouldn't be using it
/// Nothing good comes from "Secure" strings
/// Further to this Secure strings are only "useful" for single user crypto as the encryption uses the login creds, transferring
/// this data to another client will result in them never being able to decrypt it
///
/// Windows uses the user's login password to generate a master key.
/// This master key is protected using the user's password and then stored along with the user's profile.
/// This master key then gets used to derive a number of other keys and it's these other keys that are used to protect the data.
///
/// This is also a broken crypto method via injection (see Hawkeye http://hawkeye.codeplex.com/) plus the string is stored in plain
/// text in memory, along with numerous other reasons not to use it.
/// </summary>
public class SecureStringHelper
{3 -
So yesterday I installed Arch. Well, sort of. So far the GUI isn't configured so it's literally less convenient than an equally unconfigured TTY. But I'm getting there, today I connected to a secure Wi-Fi network. Tomorrow I expect to install something for power efficiency and start configuring stuff/creating a proper DE. Last time, when I stripped down Ubuntu and installed i3wm there, the first thing that bothered me was the lack of a wallpaper so I never got to issues like the keyring not unlocking, the x11 default font being two physical pixels tall, or added peripherals not being handled. This time my plan is to solve every issue as soon as I get there. For this reason I'll use a queue for managing my tasks rather than a stack like Google Keep.10
-
when you spend all day making the app secure & client shouts of not seeing any visible changes....4
-
My school is awesome, their network infrastructure is so secure (not),
that you can easily control other people's desktops with Windows' basic tools. -
Anti-features need to be fought with fire (metaphorically speaking).
This means they must be eliminated, not just made optional.
Why? Because an optional anti-feature is just one step away from a mandatory anti-feature.
For example, "secure" booting: https://youtu.be/vvaWrmS3Vg4?t=750 (Jody Bruchon)
Another example are disguised remote kill switches, such as add-on signing ( https://digdeeper.club/articles/... ). It started as optional and people were able to opt out, and everyone accepted it because no one expected what would come next.
All that was left was removing the ability to opt out, and then Mozilla has control over which extensions users are allowed to use.
For years, this feature sat dormant and users did not know of its existence. But in early May 2019, the metaphorical thread snapped and an expired certificate remotely disabled all extensions, wasting millions of man-hours of productivity.
From the digdeeper.club article:
"The funny thing is, the whole point of the extension prison was allegedly to increase security - and yet today, all security addons got disabled because of it! Shows how freedom always has to trump over security or it ends up in a disaster like this."
Evil needs to be nipped in the bud before it can flourish.2 -
If I were an employee again, I would do a short stint in a startup to learn the ropes of a business, and then work in a big company, because big companies are effing slow. ie job is secure compared to the risk in Startups.
Use that sweet ass time, to create a secret github account to do your side project, while dragging your actual work like for days. xD
And be an average or slightly above employee for them to retain you but don't go above and beyond to get more work and fake praises and a measly bonus, or other employees to envy you. There is simply no incentive in most cases. "We are a big family" is not a great reason.
But lastly never lose sight of your original goal. It is easy to slack off and become one of them dunce.6 -
"Your connection is not secure". It is too! The certificate is valid to 2019, and in Chrome it's no problem. Stupid Firefox!3
-
Asking for a friend: Well actually a friend asked me (since "I'm good with computers", you know it ;)) and no real solution came to my mind, so I thought, why not ask the internet
Anyways. She's an artist and does a project (kind of a documentation) about the Egyptian revolution. She currently lives in Europe but still has her Egypian passport. As an Egyptian national, she fears, that she could be holden back for a while and have her laptop/external HD with all the photos/videos/interviews confiscated and/or searched. She asked me for help to have a "backup solution".
The requirements: a way to backup work (from a mac) to a secure location (I would offer my server running linux for it).
The upload would have to be encrypted (if possible, I suggested to use a VPN, is this enough?)
Access to the files should only be granted if you have the propper password (in my opinion the VPN tunnel should work here too, as when it's down, you can't just reopen it without a password.
What are your thoughts on this?10 -
The importance of not using static salt / IVs.
I've been working on a project that encrypts files using a user-provided password as key. This is done on the local machine which presents some challenges which aren't present on a hosted environment. I can't generate random salt / IVs and store them securely in my database. There's no secure way to store them - they would always end up on the client machine in plain text.
A naive approach would be to use static data as salt and IV. This is horrendously harmful to your security for the reason of rainbow tables.
If your encryption system is deterministic in the sense that encrypting / hashing the same string results in the same output each time, you can just compile a massive data set of input -> output and search it in no time flat, making it trivial to reverse engineer whatever password the user input so long as it's in the table.
For this reason, the IVs and salt are paramount. Because even if you generate and store the IVs and salt on the user's computer in plaintext, it doesn't reveal your key, but *does* make sure that your hashing / encryption isn't able to be looked up in a table1 -
BT "We'll give you BT Virus Protect, which protects against viruses, phishing and other online attacks."
Or... For a start, let your users provide a good secure password when signing up? More than 8 characters is a bit ambiguous. 20 minutes later and several attempts to find out it can't be longer than 20 characters, only upper and lower case letter and numbers aaaand must start with a letter is a bit s**t. Not to mention LatPass doesn't like it as you can't copy and paste.1 -
This is not a rant. Not really. It's more expressing my own insecurity with a certain topic, which somehow upsets me sometimes (the insecurity, not the topic though).
I have nearly no knowledge about security/privacy stuff. I mean, yeah, I know how to choose secure passwords and don't make stupid DAU mistakes. The very basics you would expect someone to have after a CS bachelor's degree.
But other than that... Nothing. And I would like to get a bit into that stuff, but I have no clue where to start. First getting my head wrapped around low-level stuff like network layers? Or something completely else.
This topic is so intimidating to me as it seems huge, I have no idea where to start, and I feel that if you don't have "full" knowledge, you are going to make mistakes which you might not even notice.
I sometimes get really scared about having an account hijacked or similar. Also in our job it seems to become more and more of a topic we should know about.
Anybody got any advice?
I am looking for a way to improve my knowledge in security in general for professional reasons and my knowledge about privacy for private reasons.
It's just, every time I start reading something related it seems that I am lacking some other knowledge etc...10 -
If you do not push something (language, education, people, cars, design, medicine ...etc etc) how the hell do you expect to mature, surpass expectations and become better. Java didn't start off as good or as bad as it is today. It was through testing, abuse, use and pushing it harder do more and more amazing things that it wasn't built for. PHP has changed alot since I started using and it's through people efforts that it gets better. Before the javascript wave came it was a nuisance to use and sucked as most browsers had it switched off by default but it's become more secure, fluent and able to do more amazing things and people are loving it right now.
I really wish people would stop with half arsed and uneducated comments.1 -
I made a wordpress website to one of my friends long time back as he wants to teach online and sell his videos. (he is studying MBBS)
Yesterday suddenly he calls me and says our site has been compromised and its not longer secure.
Me: After seeing screenshot, no actually site doesn't have ssl and in recent chrome updates http site is being flagged.
He: Okay, I saw video on youtube how to buy ssl.
Me: its not just installing the certs, all the links and images has to be on https so it will take sometime for me.
He: Today, Website is no longer opening please help after putting ssl as per the video...
Me: What the hell? Who asked you to do that? Are you nuts?
He:................. Sorry, 😐2 -
Finally decided to get myself some remote server on DO, faffing around and setting things up, and suddenly I decide to look at my access logs, someone was trying to figure out how to connect to mysql, phpMyAdmin and what's not... Too bad for him I won't have any of those installed until I know how to properly secure all this :)
Heh... Welcome to the real world I guess?4 -
Gaining root in Macs by not using a password, a vulnerability in HomeKit devices allowing unauthorized remote access.
https://9to5mac.com/2017/12/...
Next you tell me FaceID isn't as secure as you want me to believe.
Oh, wait...1 -
Our ISP asked if I was satisfied with their service. I told them that it's okay, but some of our computers don't have enough powerful network card, and they can't use the internet on maximum speed, and they said that they could see it, too. WTF? I knew that the ISP's router is not the most secure thing, but it has a remote mode, which if of course OFF, and they still can see this, and maybe even more. Monitoring your traffic is a thing, but a home network should be private...2
-
While trying to fall asleep, I came to the conclusion that a solution to privacy would be an encrypted p2p messenger. You'd need a dns-like system that can tell the peers how to contact their communication partners. Then I searched for one, and there was a good looking one, but it wasn't open source. looks secure otherwise, but perfection looks different.
Can anyone recommend something similar to kripter/tell me why it would be secure/insecure to use their service instead of, say, signal? Not that I truly NEED this, but I at least want to try it :)5 -
client: "can you build out a staging server for us? here's all the code, everything you need"
me: "awesome, looking good, i have almost everything i need, just give me the credentials for the server, and I'll get started installing all the infrastructure"
client: "ok, try these!"
me: "doesn't work"
client: "this one?"
me: "doesn't work..."
client: "how about this one?"
me: "STILL NOT WORKING!!!"
imagine you want someone to do stuff on your server and you don't even know the root SSH password.... smh
why is this always a problem, use fucking 1password or something its 40 bucks a year, secure, and you can organize alllll your passwords. don't be a fucking boomer and write them on a piece of paper, or worse, apparently like my client, never know it or have it in the first place.5 -
Everything I know is self taught... From a time I dunno when I'm 20, so likely just after the year 2000
From my perspective I think different from most devs more formally trained, which can be to my advantage , the downside of this I'm terrible with names, everything in computing has a anagram.
I'm bad with names anyway... Dyslexic 😉. But if explained to me I know what it is your on about.
I consider myself a good dev, not experienced but otherwise good. But I want to be the best...
I'm also a hacker (nice one) which I think helps me build better more secure programs knowing common vulnerabilitys
I'm proud of what I've achieved so far. Whilst I'm not perfect nor is my work that's what I work towards ... As should every dev -
Creating an secure authentication system is not that easy...
Especially if you create it for a community full of devs.
But I think I've found a secure solution.
Maybe some security experts on here could review the code after I'm finished.
Here's the GitHub repo but the auth system is not up yet:
https://github.com/DevRant-Docs/... -
Your computer is probably vulnerable to Samy Kamkar's poisontap: a Pi Zero-based device that connects to usb and does the following:
- emulates an Ethernet device over USB (or Thunderbolt)
- hijacks all Internet traffic from the machine (despite being a low priority/unknown network interface)
- siphons and stores HTTP cookies and sessions from the web browser for the Alexa top 1,000,000 websites
- exposes the internal router to the attacker, making it accessible remotely via outbound WebSocket and DNS rebinding
- installs a persistent web-based backdoor in HTTP cache for hundreds of thousands of domains and common Javascript CDN URLs, all with access to the user's cookies via cache poisoning
- allows attacker to remotely force the user to make HTTP requests and proxy back responses (GET & POSTs) with the user's cookies on any backdoored domain
- does not require the machine to be unlocked
- backdoors and remote access persist even after device is removed and attacker sashays away
I need several minutes with your laptop to perform the hack, even if it's locked. Full-disk encryption and secure boot won't save you.
If you use GNU/Linux, install usbguard today. If you use macOS/Windows, idk, pray.19 -
I know someone that’s constantly paranoid about being spied on by the government and fears companies stealing his code e.g. github, Microsoft etc.
His solution:
do nothing until we find a secure platform to write code on so that our ‘billion dollar ideas don’t get stolen’
Suffice to say that he’s a very bad coder, not that I’m really that good but compared to him I’m light years ahead.1 -
Area of focus: security and automation
Why: before I turned 18 i was a hacker for 5 years and i saw the kind of crap security most websites and programs had and even if the site was secure you could usually email somebody with a spoofed email and get in. And when i say hacker i mean i wrote my own stuff not skiddy.8 -
Is it so much to ask to feel appreciated and secure at a job if you make sacrifices and endure ridiculous stress of ownership and responsibility?
Why do I have to constantly go through life wondering if my name is going to be a top level item on a budget sheet ready for the cut ? And then I’m not supposed to be upset
Just work to the end like a good little monkey and HOPE I Have another job on its way1 -
Going back and forth with Microsoft technical support right now over a SharePoint issue. Good Lord I want to reach across the wire and smack them in the face with a sea bass. Not enough to hurt, but get their attention and smell like fish for a while.
No genius, the warning on the PowerPivot Data Refresh page 'Warning: this page is not encrypted for secure communication ..' IS NOT the problem. The error messages I sent *three times* from the ULS logs are the symptoms you need to be researching. Stop guessing and trying to blame any random message you see on our configuration.1 -
I love it when I see posts on any social media site or app where it's like
"Looking for someone to hack a <insert social site> account"
Do they not know how secure those sites tend to be?
Do they think it's as easy as CSI makes it out to be?
or
Maybe they're the police trying to trick us -
Not dev per sé but annoys see he'll out of me on a monthly basis... 30 day password expiration, how does that make things more secure?! The thing that makes it worse is that I can't use any previous 28 passwords or anything too similar... Now I'm stuck with a 36 character password which I have to put in everytime my work machine decides to lock out... Which is less than a minute of not touching it.
What's that? No I can't turn around and answer a question because if I do I'll be taking 20mins off of my future career prospects as I'm working on leveling up my inevitable arthritis6 -
Colleague: "My client says asp.net is more secure and has a better performance compared to php"
Me: "Hmm ok. But it all comes down the implementati..."
Him: "hE waNtS AsP.neT nOt PhP"1 -
Trying to install Linux off of a USB drive when motherboard flips put during boot mode and boots back into windows saying that it is not secure. Even though I've tested this drive and installed Linux on other computers. ugh1
-
Apparently,some universities don’t understand it’s not a good idea to send passwords ove an unencrypted connection. And btw, post requests work the same as get ones, it’s not more secure.
Not going to put the website for privacy reasons, but 🖕 this university!🖕🖕3 -
It has to be Keybase.
It is exactly what I need - A secure yet practical cloud storage, where only you own the crypto key, with the added bonus of maintaining a blockchain-based identity online, with proof system and all.
Also has a secure PKI-Based E2E chat when I want to talk to someone about something I don't want the general government to necessarily know.
Definitely recommend the service! Even with the odd decision to include an option of a Lumen crypto wallet or whatever, you can just ignore that feature if you're not into it and it doesn't slow you down.2 -
!rant
I see a lot of people complain about uni degrees and stuff because they don't learn how to code etc. Is this really the standard?
I mean I'm only in fourth semester bachelor and had coding knowledge before starting uni. But we had basic to intermediate java in the first two semester, now learning how to write secure code and OS-Level stuff in C++, we had a module with practical Assembly coding all while still learning all the theory.
At the end of the first semester we had to write a terminal game in Java. I mean of course that's not "real experience" but if you dive in you definitely learn the basics you need to get started in real life.
Or am I wrong completely / just in a weird uni?6 -
TL;DR Does Telegram really secure?
Some people say Telegram is the most secure and safe messenger, some say it's not. If you're familiar with it you may know from news that Telegram did not gave its clients' info to government, you may have heard that Telegram's encryption is not the best one, BUT my question is does it store peoples' private chats' keys? Actually it does with normal chats because if you reinstall Telegram you can easily get normal chats' messages. Also my friend said that any application in mobile stores like App Store sign a agreement with stores owner company that if some points met, the application owner have to share info of its clients. So dear friend what do you think, should I continue using Telegram)?
P.S. sorry for my not the best English4 -
Jeesh! In the last 12 months I've had a lot of emails from the different services I've used that they've been compromised and a database of emails and hashed passwords have been exposed 😒1
-
I just finished posting this but think it deserves its own post.
If you're creating a business or "startup" (as people like to call it these days) don't assume the idea is novel or investors will just jump on board. Focus on the business fundementals, money and cash flow, even before launch, unless you can afford not to. But really you can't afford not to. Selling before launch means that you're effectively doing two things 1 you're collecting new customers and income for the business and 2 you're. raising awareness at the same time. Obscurity is death and failure.
Get you a good sales team and marketer when the time is right.
Have a year of runway.
Identify the sites and groups your target audience and investors frequent. Start conversations now, buzz is the hardest thing to generate.
Start building relations with customers and potential clients now. Discuss launch, ask them if they'd be willing to pay up front before launch, in order to secure a "lifetime membership", offer it as an early opportunity and charge extra. Giving a discount out of the gate is a mistake B/c it says to potential investors that you don't think it's ready or worth it yet. Of course if it's between making 1. Some money or 2. No money, don't let it be a deal breaker, offer a discount. Going from no clients to any clients is a BIG deal. If you can do 1 you can make it to 10, if 10, you can reach 100, we etc.
No one likes asking for money and yet it is as important if not more important than development. -
Currently trying to make a multi boot machine, with a lot of linux distros inside, like debian, fedora, gentoo and arch.
I know I will have to format everything a lot of time, because of stupid mistakes, I want to try to put /home in common, and play with some more SSD, and to put a preempt_rt patched kernel somewhere.
I am starting from debian,
Format counter: 3
Reason 0: because i need to install at least once...
Reason 1: I am stupid
Reason 2: I disconnected the SSD,to connect a disk with windows. Now bootloader doesn't find any os in the SSD anymore... still no clue, and in case of doubt: give windows the fault 😠😠😠
DAMN YOU WINDOWS, how did you find that I want to use debian? What did you do to break it?? (Despite it wasn't even connected?!?)
I have checked everything about secure boot, and I am sure it is disabled...
And every search online gives results about dual boot, but it is not my case... :/ -
This is not a rant. Rather just a question or an ask for advice, as I have seen a lot of people talk about web development around here. I am planning to create a website for my search engine. I created a Rest API for my VPS so I can do http requests and retrieve some links for certain key words. But I need some good ideas to do this from a website. As I am not sure what would be the best way to do http requests. As far as I know it's possible with Js and PHP, but I am not sure what's better, more secure or convenient? So here I am to ask you guys, especially those who have experience with this, what I should consider to do.
Oh and please forgive me my limited knowledge about Js and PHP 😅😊3 -
One of Biggest dev insecurity i think poor quality of user passwords. Users have not yet understood how to create secure passwords.2
-
When did we decide managing Users through Cloud REST architecture was more secure than having them in an underlying DB?
Because I can't put my finger on exactly why... but I don't like it and I think it's probably less secure... and just spawned from the need to be able to make user management a subscription based service like fucking everything? When a simple MySQL or postgres and some bcrypt somewhere would be both more secure and infinitely cheaper?
I'm more used to consuming REST API's than writing them. Can any you REST peeps help me understand how a REST API could be made as secure as a SQL DB connection for user management?
What do you think the attack vectors are for a REST API User Management? Like... what's the SQL injection of REST API? Pack some extra JSON somewhere or something?
At least if I can have faith my shit's not gonna get hacked because I have to use a 3rd party REST service for User Management of Users to my own fucking app I can maybe sleep tonight.2 -
Yeah, so when you create an account just about anywhere nowadays, you need to choose a strong password. Fair enough. But then, some sites/services/systems require a second password, sort of a password hint as an extra security for retrieving your first password in case you forget it. Well OK...That hint question just becomes very *in*secure when you must choose from some extremely stupid presets like "In which town were you born?" or "What was your mother's maiden name?", all of which are trivia that for most people can be easily googled, or looked up on facebook ffs. And these "in which town did this or that happen?" questions? As there is only one town in my country it's not a long shot that I was born in Mariehamn, met my partner in Mariehamn and had my first job in Mariehamn. Security questions for imbecils.4
-
Okay I'm probably going to get flak for this but...
WhatsApp chats are apparently e2e secure. Except when you back them up, right? Why not, when you create a backup (iCloud, google drive, whatever), have the app generate a password protected key pair and use that to encrypt/decrypt the backup?
When restoring the backup, use the password you set for the key et voila! While at rest, that backup is still encrypted.
Or have I missed something completely?2 -
!rant
Why everyone who claim to know a lot about web security and encryptions is not able to help me check if my system is secure :/
And some try to charge me afterwards -.-"
Edit:
If they expect payment they should state that at beginning and be able to actually do something...3 -
Why is it so difficult to tell the people to not use the same passwords everywhere? I thought of a service which searches all leaked databases and predicts a password based on that as a warning for the user... Having the program told you that your password the user is likely to enter would be XY, because the adobe OR MySpace OR Dropbox passwords for the email OR username entered was that password could be a bit more aggressive but useful to let the users at least think of secure passwords.1
-
1) Simple, secure and powerful technology for website user interface design which will replace HTML, CSS and JS.
2) Simple and practical technology to be able to utilize HTML for all kinds of documents which will replace paper page based document formats like PDF and Word.
3) One technology for native mobile app development to rule them all. So that it's not necessary to use HTML and JS.1 -
Been wondering about something and can't figure out if I am a retard or a genius 😂.
If MD5 is so outdated and should not be used to store password hashes (let's say for whatever reason you cannot effectively switch to another algorithm) wouldn't it just be easier and more secure to just re-encrypt the hash again, so just MD5 the MD5 hash... in theory, wouldn't that make the hash virtually uncrackable because instead of trying to brute force actual real words, you now have a hash of essentially random characters which have no relation to the others, and even then, suppose you manage to crack the hash, you will get another hash to crack before getting to the password?5 -
The fact that the Wordfence plugin exists kind of admits to everyone WordPress is not very secure in the first place...
-
Work! Terribile doubt about our project 😭i will leave this company if we do not come up with an adult solution 😔
We are working for another Company, they asked to add a web app to their project.
We made frontend and backend, we make user auth to their api, then call their api (place order, get orders etc), passing their auth token to their services.
Which Means that our endpoints are not really protected (i think) and if we add an endpoint that does not use their api, the only way to secure them Is to take the token, validate It by calling for example get /order of the api and if It fails just discard the request....too slow?
my colleagues do not want to put a serious auth they Just want to use the company api and leave the rest open...
And the customer Just asked to use some other api functionality, but that api has another auth... How do we pur them togheter? The last api want the id of the user to do machine ti machine auth
It Is my 6th month here no one thaught me anything, i think i'll Just leave ..or am i Just experiencing the developer Daily work?😔7 -
Obviously credit card companies, banks, etc. do not use MySQL. So what database do they use to keep data secure?7
-
Bought two hp z230 and one hp z210 to setup as a kubernetes cluster at home.
The first two worked as expected to install Ubuntu 18.04 but the z210 just fails installation just at the end of.
I've updated the bios, I've tried different hard drive, (obvious I've turned off secure boot), I've downgraded the bios, I've cursed, spoken harch language at it and sprinkled it with holy water, still it fails.
A Google search the problem, one hit similar to my problem but it did not help me.
Currently I'm on my 5:the glass of wine, if not solved tomorrow I'm hiding it at work until the next "downsizing" and it will have an accedent from the 9:the floor.
I've spent 150$ on it but I have the economy to nurture my mental health... Not all the time but this time it feels worth it!!!3 -
{
-i won't follow logging practices
-i won't follow secure coding
-i won't leverage profiling n monitoring tools
-i won't reuse best practices
-i won't listen to thought leaders
-i will outsource writing UT
-i will outsource code quality checks
-i will outsource all testing
-i will ignore n overide CTO team
But I still want high stability, security n 4 9s availability. Just want it done. My team is best. Am a fast-track leadership program leader who never has or ever needs to cod. I just know ...
}
People I have to deal with every sprint. Site reliability is not easy ...
Teaching good code makes great products to morons, toughest ...
"Beginners mind needed"2 -
Could someone please tell me what model of router uses Https for their admin page? I went to the store and I noticed most of them had http. What is the point in making the right setting if in the first place the connection is not secure?! :S59
-
https://learnbchs.org - The web framework consisting of OpenBSD, C, httpd and SQLite.
What do you think? Not sure if I should call C-webdevs insane or genius (maybe both).
I think the code will either end up very secure or with more severe bugs than any PHP website ever had. Please talk me out of trying it.7 -
!dev (kinda)
Warning: Might contain (be) stupid rambling.
So I got my new toy and want to play around with it. Just in case I have to return it I first want to make a full disk backup, so I try to boot clonezilla. I press the power button and mash F2, F8, F9 - and it boots straight into the windows setup. Nope, not what I wanted. Try again. And again. Eventually I look it up and apparently I have to hammer the ESC key to get where I want to. Alright, now it works. Boot from USB. Failed. Try again. Failed. Check the BIOS, disable secure boot, reboot. I need to type 4 digits to confirm disabling secure boot. Alright. Reboot, try again, failed. Secure boot is on again. Wtf? After some more infuriating tries I see that NumLock is disabled. AAAARGH. BIOS: Enable NumLock on boot, disable secure boot, enable legacy boot. Input the 4 digits - works! Try to boot from USB: Failed! Grab another USB stick, did the clonezilla image, try again: Finally! It! Works!
Format disk, install Qubes OS. Success!2 -
I'm reading online that after I buy bitcoins from Coinbase, I should transfer it to a private wallet that is kept offline.
What would be a private wallet? Does that mean I have to download and keep the entire blockchain on my PC?
Also how would I transfer?
And best way to keep the private wallet secure? and not lose the key, password, etc?
And I guess main reason I ask was bc I saw this. Actually does this basically act like Coinbase? But they keep my wallet?
https://try.blockfi.com/morningbrew...9 -
Goes to my comment on on of the rants to "Why linux cannot AVER be used by a normal user"
I'm pretty good with techs, OS, dev etc.
But here you go, a random error message which tells me nothing (Absolutelly nothing) and no way to fix it. No way to fix it, not even a hint where to look for solution, outside google. Sure, It took me around 5 minutes to find the problem googeling and copy/pasting some bash commands, but next time it happens and I don't have internet ? Well fucked.
This shit never happens on Wiondows or MacOs :) And that's why these 2 will always be user firendly ans linux will never be.
That's why linux will never be used by normal humains.
You 100% linux addict will point out directlly 'TYeah yours repos sources are fuckied" or whatever, but it IS NOT to user to know how sources, packages etc work. I want just update my system, if one source is not found, ignotre it by default ! How hrd is that ?
Error message in question :
E: The repository 'https://ppa.launchpadcontent.net/tr... jammy Release' does not have a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
Thanks for assisting to my ted talk.17 -
So... there is a bank. And the website for example is using "https". Alright. But the Login consists your login ID (in the most cases your account number) and a Pin number ( only 5 chars) If i remember pentesting, crunch etc a pin or password with 5 chars (included special characters) is fast hackable or not? Or is it super secure cuz of the "https"?4
-
Though I’ve seen devices like the following I’ve only ever seen them used for horrible purposes.
I was envisioning facility control being made capable by the use of a larger tablet device or tablet computer. The device would have no internet connection. It would not attach to the outside world at all.
It would not receive non manual software updates
It could view all air flow, temperature, lights, locks, electrical outlets, power draw, water usage, heaters, air conditioners, computer statins etc
And control and report statistics on them all.
Impractical you people said last time. But I would say cool if the device is kept super secure . That being said who knows how to do that since everything sucks once someone who knows what they’re doing has physical access lol
Personally all I don’t know how to break into is smart phones
Comps I could always figure out even if they had disk encryption given enough time.
The only reason phones are hard is you’re limited to network attacks and the boot loader is on the chip page.
Cause in the end a computer is just it’s hard drive in terms of security lol1 -
Approx. 24 hours ago I proceeded to use MEGA NZ to download a file It's something I've done before. I have an account with them.
This is part of the email I received from MEGA NZ following the dowload: "
zemenwambuis2015@gmail.com
YOUR MEGA ACCOUNT HAS BEEN LOCKED FOR YOUR SAFETY; WE SUSPECT THAT YOU ARE USING THE SAME PASSWORD FOR YOUR MEGA ACCOUNT AS FOR OTHER SERVICES, AND THAT AT LEAST ONE OF THESE OTHER SERVICES HAS SUFFERED A DATA BREACH.
While MEGA remains secure, many big players have suffered a data breach (e.g. yahoo.com, dropbox.com, linkedin.com, adobe.com, myspace.com, tumblr.com, last.fm, snapchat.com, ashleymadison.com - check haveibeenpwned.com/PwnedWebsites for details), exposing millions of users who have used the same password on multiple services to credential stuffers (https://en.wikipedia.org/wiki/...). Your password leaked and is now being used by bad actors to log into your accounts, including, but not limited to, your MEGA account.
To unlock your MEGA account, please follow the link below. You will be required to change your account password - please use a strong password that you have not used anywhere else. We also recommend you change the passwords you have used on other services to strong, unique passwords. Do not ever reuse a password.
Verify my email
Didn’t work? Copy the link below into your web browser:
https://mega.nz//...
To prevent this from happening in the future, use a strong and unique password. Please also make sure you do not lose your password, otherwise you will lose access to your data; MEGA strongly recommends the use of a password manager. For more info on best security practices see: https://mega.nz/security
Best regards,
— Team MEGA
Mega Limited 2020."
Who in their right mind is going to believe something like that that's worded so poorly.
Can anybody shed some light on this latest bit of MEGA's fuckery?
Thank you very much.4 -
Hey. I'm still very new to CloudFlare and I have a question.
Let's say that I have 4 sub domains: a.test.com, b.test.com, c.test.com, d.test.com. They're all under the same domain (test.com).
I have a page rule setup specifically for a.test.com, where "Disable security" is set to On. I did this as a temporary solution so that I can figure out the problems that a.test.com has when the security is enabled (had users complaints regarding not being able to send requests with CF security On), so that it is still accessible while I try to fix it..
By turning disabling security for a.test.com, do I put others (b, c, d) at risk? I had someone telling me that it is possible for attackers to make use of a.test.con (unprotected by CF) in order to attack the other sub-domains. "a.test.com has no protection so attackers can use it to send requests to other secured subdomains, cross-site attack" or something along that line.
I don't get this. I thought page rule is supposed to be active only for the domain where it's being set up and the rest will still be secured, and that if attacker manages to attack the other subdomain its due to the others not having secure applications inside of it.
Dunno if that person was telling the truth or tried to mess around with me with their joke!
Thanks!5 -
People who generalize any technology as 'bad' or "worthless" (or worse, proclaim it is not secure, doesn't work correctly, or has specific problems it doesn't have) when the technology is widely and obviously appropriately used in practice just make themselves look bad. It's like getting mad at a hammer. It's just a tool. If you don't like it, don't use it. If you think it needs improvement, contribute to improving it. Non-constructive criticism is a waste of your time as a software developer.6
-
I'm kinda looking for a new phone, should be super cheap (so a used one would do), I wanna modify it to be secure (proper encryption, VPN, etc.), very good battery time and not very big (more like 4"). I have been looking at the Lenovo P2 a lot, but I'm afraid my current phone will die before I have enough money for that one (I'm a broke trainee yay).
So what do y'all have or can recommend?3 -
I deployed a website and hosted it today. Also used a SSL certificate but now when I'm opening it on another device with its own data connection, it is not loading and showing error "This site can’t provide a secure connection".
But if my device is connected to wifi, the website is functioning normally. Can anybody help me out? My website - https://covid-india.live/4 -
the red haired girl and the blue haired girl.
there was this story about a programmer who spent years studying computer science before finally getting a job.
the dev studied only computer science and was put on blue team after a few days.
a few hours into one of the constant coding sessions, the boss told the devs that red team members and blue team members would be working in pairs.
the person from red team transferred the devs work to their data base without the dev knowing, then locked down the devs computer. the dev could not do anything. later, the dev got fired for not doing any work. after that, the company got millions of dollars, and the dev did not see any of it.
both the dev and the managers made a note not to hire any programmer who cannot secure their work.
it is not ethical to teach people programming without also teaching them cyber security.
computer networking, programming and security should all be the same major.
it is a bad idea to teach people how to build anything without telling them how to secure it.
the story above was just a scenario, but it probably happens way more often than people think.
Schools should teach both things in the same major.3 -
Recover Funds Lost To Crypto Investment Scam – Simply Contact Captain WebGenesis.
Among the companies offering cryptocurrency recovery services, Captain WebGenesis stands out as the safest, most legitimate, and trusted option. With a team of expert cybersecurity professionals and cryptographers, we have developed a proprietary recovery process that ensures the secure and efficient retrieval of lost or stolen digital assets. Captain WebGenesis's impressive success rate and long list of satisfied clients are a testament to our expertise and dedication to delivering exceptional results.
Remember, with Captain WebGenesis, you're not alone in the fight against crypto losses.
Email: ( Captainwebgenesis@ hackermail. com )
WhatsPp: (+1 501, 436,9362)13 -
One of our partners sent me a Key Injection Tool to inject encryption keys into a PINPAD with. Looks like they were short on developers and had to hire Python typists who have made a mess of a simple AES encryption/decryption. When do these companies learn that writing a security related software in Python is not really secure? I had to read the rubbish in Python and read it from scratch in C++ to get it to work, and am now contemplating whether to provide that company with my version of their Key Injection Tool or not...1
-
I have the following scenario with a proposed solution, can anyone please confirm it is a secure choice:
- We have critical API keys that we do not want to ship with the app because de-compiling will give access to those keys, and the request is done before the user logs in, we are dealing with guests
Solution:
- Add a Lambda function which accepts requests from the app and returns the API keys
- Lambda will accept the following:
1. Android app signing key sha1
2. iOS signing certificate sha1
- If lambda was able to validate them API keys are sent back.
My concerns:
- Can an attacker read the request from the original (non-tampered) apk and see what the actual sha1 value is on his local network?
- If the answer to the question above is yes, what is the recommended way to validate that the request received is actually from the app that we shipped and not from curl/postman/script/modified version of the app11 -
So, need to secure some requests.
I decided on going passwordless on the website but I want to have an API too.
I am reviewing auth0.
I am also not sure if I can secure the same endpoints as private and public differently, so the private is used by the backend with no auth and the public with auth.
Wold you guys help me with some reading material?2 -
I read somewhere while at work on the internet in X that the Bitcoin lost during the Bit get breach, worth more than $5 million, has been fully recovered, thanks to the efforts of Tech Cyber Force Recovery. The breach had left many users devastated, unsure if they would ever see their funds again. However, Tech Cyber Force Recovery stepped in and successfully traced and retrieved the stolen Bitcoin, ensuring that all affected users received 100% of their lost assets. The recovery process was far from easy. The Tech Cyber Force Recovery team used cutting-edge blockchain forensic techniques to track down the stolen funds. They meticulously followed the transaction trail across multiple blockchain networks, piecing together the complex puzzle of the breach. It involved collaboration with cybersecurity experts and relevant authorities to ensure that the recovery was not only successful but also secure. The recovery efforts were particularly significant because the total value of the Bitcoin lost during the Bit get breach amounted to over $5 million. This made the task even more critical, as the amount at stake was substantial. Users who had once feared losing their investments can now rest easy, knowing that Tech Cyber Force Recovery was able to restore their assets in full. What sets Tech Cyber Force Recovery apart is not just its technical expertise but also its commitment to transparency. Throughout the entire recovery process, the team kept users informed every step of the way. This communication was crucial in maintaining trust and confidence. Many of the affected Bit get users expressed their gratitude toward Tech Cyber Force Recovery, acknowledging the team’s dedication to ensuring the recovery of their funds. In an era where digital asset security is a growing concern, this recovery serves as an important reminder of the role that blockchain forensics and recovery services play in protecting users. It also underscores the importance of having a trusted service like Tech Cyber Force Recovery available to assist in cases of breaches and theft. Their success in recovering the stolen Bitcoin, worth over $5 million, has made them a beacon of hope for users who might otherwise have lost everything. VISIT THE TEAMS ON WhatsApp +.(156)(172)(636)(97) OR TELEGRAM (AT)TECHCYBERFORC With the full recovery of the funds, users can now feel more secure about the safety of their digital assets, knowing that there are reliable and capable services like Tech Cyber Force Recovery to help when things go wrong.3
-
I need some clarity with the situation below.
I have my API ready.
Let's say I have a route /reset/token,
I want to be able to serve a html file with css and all that once I've processed the token internally.
I've not worked with the whole stack before so I've never really served files based on conditions i.e if the token is valid serve x else serve y.html
Also, I'm pretty sure node.js isn't the best for serving files.
So I'm taking another approach with nginx which is to implement /reset/token to serve the static file with it's coupled js file to query the API. Seems standard to me but I have this feeling that a prefilled html would be more secure than one with exposed js.
Is this the right way? Should I worry about my API calls being exposed via the js fil ? Is obfuscation the only way to handle this ? Is this the way everyone does it cause somehow I don't see the key js files in most sites. How are they hidden if so? Or are they?
I'm confused and also nginx won't let me rewrite /reset/token to something else without changing the browser url field. How do I prevent that ?1 -
I'm so fucking excited, is anyone joining me in making money? If you're looking for a color prediction game that meets your criteria, I've heard that lottery-7.app is worth considering. It's unique not only for its user-friendly interface but also for its focus on security. From what I've heard, it has a robust system to protect user accounts, providing peace of mind while playing. Moreover, the withdrawal process is fast and secure, improving convenience. Starting with a minimum deposit of ₹100, you can explore a variety of online games and potentially earn rewards. When you win, withdrawing your earnings seems simple.
-
Saclux Comptech Specialist appears to be a legitimate cryptocurrency recovery service. Here are some key points about their self-recommendations:
Expertise
1. Specialized knowledge: They claim to have extensive experience in cryptocurrency recovery, blockchain analysis, and crypto tracing.
2. Technical expertise: Their team allegedly consists of skilled technicians and experts in cryptocurrency recovery.
Services
1. Recovery services: Saclux Comptech Specialist offers recovery services for lost, stolen, or inaccessible cryptocurrencies.
2. Blockchain analysis: They provide in-depth blockchain analysis to track down stolen funds.
3. Crypto tracing: Their team uses advanced tools and techniques to trace and recover cryptocurrencies.
Benefits
1. High success rate: Saclux Comptech Specialist claims to have a high success rate in recovering lost or stolen cryptocurrencies.
2. Fast and efficient: They allegedly provide fast and efficient recovery services.
3. Confidentiality: Their team prioritizes confidentiality and ensures that client information remains secure.
Recommendations
1. Positive reviews: Saclux Comptech Specialist has received positive reviews from clients who have used their recovery services.
2. Expert endorsements: Some cryptocurrency experts recommend Saclux Comptech Specialist for their recovery services.
Please note that while Saclux Comptech Specialist appears to be a legitimate service, it's essential to check their website very well so that you will not fall into any scam.1 -
TOP-RATED CRYPTO & BITCOIN RECOVERY EXPERTS
Betafort Recovery is the trusted solution for Bitcoin scam victims looking to reclaim their lost funds. I wholeheartedly recommend Betafort Recovery to anyone who has fallen prey to a scam and is searching for effective methods to recover their cryptocurrency or wallets. As a reliable cryptocurrency recovery firm, Betafort Recovery not only assists in recovering stolen assets but also offers secure solutions to protect your wallets from future online scams.
I can personally vouch for their effectiveness. I was deeply distressed and had almost given up when I lost $23,400. But thanks to the experts at Betafort Recovery, they managed to restore my funds to my wallet. If you've lost your cryptocurrency and feel helpless, don't wait—contact Betafort Recovery to get your money back.
One of the standout features of Betafort Recovery is their dedication to providing secure solutions that protect wallets from scammers. They don't just focus on recovering lost funds; they actively work to prevent future incidents, ensuring that their clients’ digital assets remain safe from potential threats. This proactive approach underscores their commitment to the long-term financial security of their clients.
For those who feel lost after their cryptocurrency has been stolen, reaching out to Betafort Recovery could be a game-changer. Knowing that there are legitimate experts who can help recover lost funds offers a sense of relief and empowerment, restoring hope in a difficult situation.
Betafort Recovery is undeniably a reliable cryptocurrency recovery firm. Their proven ability to assist scam victims, their focus on secure solutions, and their unwavering commitment to supporting clients through challenging times make them a valuable resource in the often-complex world of digital currencies. If you or someone you know has fallen victim to a cryptocurrency scam, contact Betafort Recovery as the first step towards reclaiming your funds and regaining your peace of mind.2 -
I was drawn into the world of cryptocurrency with the promise of high returns and financial independence. One day, I stumbled upon a website that looked legitimate, boasting impressive profits and testimonials from seemingly satisfied investors. It promised a low-risk, high-reward investment in Bitcoin, and before long, I had invested €48,750 into what I thought was a secure platform. At first, everything appeared to be going well. The returns were as promised, and I watched my investment grow. But when I attempted to withdraw my earnings, the site suddenly became unresponsive. My attempts to contact customer support were met with silence, and it dawned on me that I had fallen victim to a sophisticated scam.Desperate and feeling betrayed, I turned to the internet for solutions. It was here that I first heard about Alpha Spy Nest. The stories on various forums spoke of their success in recovering funds for those scammed in the crypto world. Skeptical but with nothing to lose, I reached out to them.From our initial conversation, the team at Alpha Spy Nest exuded professionalism. They asked for details about my transactions, the platform used, and any communication I had with the scammers. They assured me of confidentiality and explained how they would use blockchain analysis and cyber forensics to trace my lost Euros converted into Bitcoin.The process was both fascinating and nerve-wracking. Alpha Spy Nest's experts delved into the blockchain, tracking the movement of my Bitcoin through various wallets, which was no small feat given the anonymity and complexity of cryptocurrency transactions. They identified patterns and connections that led them to the scam operation's digital footprint.The breakthrough came when they managed to freeze some of the assets on various exchanges where the scammers attempted to cash out. Through negotiations and leveraging their network, Alpha Spy Nest was able to recover a significant portion of my lost investment.The relief was overwhelming when they informed me that they had successfully reclaimed much of my €48,750. Not only did they recover my funds, but they also educated me on how to better secure my digital investments going forward, teaching me about secure wallets, the importance of due diligence, and how to verify the legitimacy of investment platforms.
 1
1 -
The gaming industry in Angola has entered a new era, with online casinos transforming how people approach entertainment. What once required travel to physical locations can now pin up casino https://pinup-casino.ao/ be accessed instantly through a smartphone or computer. This flexibility appeals to a wide demographic, from younger tech-savvy players to seasoned casino fans looking for new digital experiences.
One of the standout destinations for this new wave of entertainment is Pin-Up Casino Angola
. Its portfolio is vast, covering everything from slot machines with vibrant graphics to interactive live casino rooms. Sports betting is another major attraction, giving players the opportunity to combine their love of gaming with their passion for sports events. The platform’s ability to bring together multiple forms of entertainment under one roof has made it particularly popular among Angolan players seeking variety.
Beyond just the games, Pin-Up is recognized for its player-first approach. The platform offers multilingual support, multiple secure payment options (including e-wallets and cryptocurrency), and an easy-to-use interface designed for smooth navigation. Promotional offers, daily rewards, and seasonal tournaments further enhance the experience, making Pin-Up not just a gaming site but a full-fledged entertainment hub for Angolans.2 -
HOW MY CARBON NEUTRAL BITCOIN WAS HELD HOSTAGE AND RESCUED BY ASSET RESCUE SPECIALIST
I believed in a cleaner tomorrow, one where blockchain and renewable energy were not enemies. My wind farm was proof. Excess energy powered my Bitcoin mining machines, a closed loop. It was the future. Until the ransomware attack.
My turbines hummed one morning as they always did, but my mining operation? Gone. My wallet? Locked. One message replaced my screen:
"Create a payment of 5 BTC to free your information. You have 72 hours."
The irony? My carbon-neutral Bitcoin had been taken hostage.
I panicked. I had crafted my system for survival, yet here I was, stuck. Perplexed, I went to industry colleagues. That's when one panelist from a Clean Energy Summit contacted me:
"Consider ASSET RESCUE SPECIALIST. They provide blockchain forensics, and they're carbon neutral!"
I was desperate but skeptical. During my first call, their personnel were talking my language, both security and sustainability. They did not just care about Bitcoin; they cared about why I was mining it.
Their approach? Genius. Instead of negotiating with the hackers, they reverse-engineered the ransomware. My infrastructure had been attacked through a zero-day vulnerability in the grid software, not my specific setup.
This wasn't a solo problem. This was an energy security emergency for the entire region.
Over 12 frenetic days, ASSET RESCUE SPECIALIST, worked with good-faith hackers and clean-energy engineers. They did not simply recover my Bitcoin without giving a ransom to attackers, they also fixed the flaw that had jeopardized our grid in the first place.
When I was finally able to log back in to my wallet, I felt like I'd regained not only my Bitcoin, but command over my vision.
My wind farm is now more secure than ever. ASSET RESCUE SPECIALIST, even helped us implement decentralized security protocols to prevent future hacks. And the icing on the cake? Their carbon offsets make their entire operation all about aligning with my emphasis on sustainability.
I once believed that Bitcoin and green energy were the perfect pair, but now I understand security is the third leg.
If you work in cleantech and disaster strikes? ASSET RESCUE SPECIALIST, is not a rescue team, they are a renewable power. 1
1 -
APM BILLING: Providing HIPAA-Compliant Billing Services You Can Trust
In today’s healthcare landscape, maintaining patient privacy and data security is paramount. Healthcare providers must adhere to strict standards to protect sensitive information while ensuring that financial operations are smooth and efficient. APM BILLING, based in Philadelphia, Pennsylvania, is dedicated to providing HIPAA-compliant billing services that ensure the highest level of security and compliance, while also optimizing the billing process for healthcare providers.
What Are HIPAA-Compliant Billing Services?
HIPAA (Health Insurance Portability and Accountability Act) establishes strict rules to ensure that healthcare providers maintain patient privacy and the confidentiality of their health information. As part of our commitment to protecting patient data, APM BILLING offers HIPAA-compliant billing services that meet all of the requirements set forth by this regulation.
Our HIPAA-compliant billing services ensure that all personal health information (PHI) handled during the billing and claims process remains secure. From data encryption to secure transmission, we follow the highest security standards to prevent unauthorized access, breaches, and other vulnerabilities.
Why Is HIPAA Compliance Critical for Healthcare Billing?
For any healthcare business, staying HIPAA-compliant is not just a regulatory necessity—it's essential to maintaining trust with patients and avoiding costly penalties. Non-compliance can result in hefty fines, lawsuits, and damage to your reputation. When it comes to billing, ensuring that all processes follow HIPAA guidelines is critical in preventing unauthorized access to sensitive patient data.
APM BILLING takes privacy and security seriously. Our team is well-versed in all HIPAA regulations, so you can trust that your patient data is always protected. We integrate comprehensive security protocols into our billing workflows, including:
Encrypted communications for all patient data exchanges
Secure data storage that meets HIPAA standards
Audit trails to track access to patient information and billing details
Employee training to ensure that everyone handling sensitive data understands HIPAA guidelines
The Benefits of Working with APM BILLING for HIPAA-Compliant Billing Services
By choosing APM BILLING, you gain the peace of mind that comes with knowing your billing processes are in full compliance with HIPAA regulations. Here are some of the key benefits of our HIPAA-compliant billing services:
Data Security: We use the latest technology to protect patient information, ensuring that all billing data is securely transmitted and stored.
Regulatory Compliance: Our team stays up-to-date with the latest changes to HIPAA regulations, ensuring that your practice remains compliant with all legal requirements.
Reduced Risk of Penalties: HIPAA violations can lead to significant fines and penalties. By outsourcing your billing to APM BILLING, you minimize the risk of compliance issues and the associated costs.
Enhanced Trust: Patients trust healthcare providers to keep their personal and medical information safe. By using our HIPAA-compliant billing services, you show your commitment to maintaining privacy, which fosters trust and enhances your reputation.
Efficiency and Accuracy: In addition to security, we ensure that your billing processes are efficient and accurate, leading to faster claim submissions, reduced denials, and increased revenue.
Why Choose APM BILLING for HIPAA-Compliant Billing Services?
Expertise: Our experienced team is dedicated to ensuring that all of your billing practices comply with HIPAA guidelines.
Tailored Solutions: We offer customized solutions that meet the specific needs of your healthcare practice, whether you’re a clinic, provider, or specialty office.
Focus on Security: We take security seriously and use state-of-the-art systems to protect all sensitive information.
Reliable Support: With APM BILLING, you’ll have a trusted partner in billing that is committed to safeguarding your practice’s financial and data integrity.
Get Started with APM BILLING Today
At APM BILLING, we understand the importance of maintaining HIPAA-compliant billing services in today's healthcare environment. We are here to help your practice stay secure, compliant, and financially efficient.
Contact us today at +1-800-621-3354 to learn more about how we can help streamline your billing process while ensuring complete protection of patient data. Visit our office at 19104 Philadelphia, Pennsylvania, and let APM BILLING handle your billing needs with the utmost professionalism and care.
Let APM BILLING take the stress out of billing while keeping your practice compliant with HIPAA regulations, so you can focus on what matters most—caring for your patients.2 -
As a devoted mother from the United States, I have always prioritized my family's well-being, which includes caring for my own children and several orphans. In our household, every penny counts, and financial stability is paramount. However, my world was turned upside down when I fell victim to a scam that cost me $500,123. The scammer, masquerading as a blockchain recruiter, lured me in with enticing promises of a "high-paying crypto position." They exerted undue pressure on me to send USDC as a "verification deposit," and in my desperation to secure a better future for my family, I placed my trust in them. Unfortunately, I discovered the heartbreaking truth far too late.GRAYWARE TECH SERVICE emerged as my beacon of hope. Their expert team acted with remarkable urgency, employing their extensive knowledge and sophisticated resources to trace my stolen funds across multiple blockchains. Within hours, they identified the scammer's Binance deposit address and began collaborating closely with the exchange to freeze the assets. Although $150,000 had already been liquidated, their relentless efforts culminated in the successful recovery of 100% of the remaining $350,123 . This financial miracle not only salvaged my family's future but also restored my faith in the possibility of justice.What truly distinguishes GRAYWARE TECH SERVICE is not just their technical prowess but also their unwavering compassion. They took the time to educate me about the crypto landscape, emphasizing that legitimate opportunities never require upfront payments. This invaluable knowledge has empowered me to make informed decisions moving forward. Their professionalism and dedication not only helped me recover my savings but also reignited my passion for helping those who depend on me.To anyone who has pass the anguish of being victimized by scams, I implore you not to lose hope. GRAYWARE TECH SERVICE possesses the expertise and determination to transform despair into second chances. They have not only restored my financial stability but have also inspired me to advocate for financial safety and awareness in my community. I am eternally grateful for their support and commitment to helping individuals like me reclaim their Cryptocurrencies.You can reach them on whatsapp+185827595082
-
How Hackers Gained Access to My Crypto Wallet and Sensitive Data through a Keylogger sent to my device through a phishing email.
I’ll advise others to be wary of the kind of emails they open, as this happened a few weeks ago when a phishing email was sent to my email unknowingly to me that it was a keylogger with the intent of stealing my private information and if not for the intervention of Morphohack Cyber Services, I would have been cleaned out completely. I contacted Morphohack Cyber Services a week after that incident and they detected the keylogger in my computer which has been there for months stealing my private information. If my crypto wallet was not drained, I would not have been aware of the keylogger in my device. Morphohack was able to secure my devices and retrieve my crypto wallet including the crypto assets. Their sophisticated security features and malware can beat any hacking tools available and they are very professional and ethical. Morphohack is a lifesaver and I hugely recommend their services. Their E-mail. Morphohack@Cyberservices. com & WhatsApp. +1 - 213 - 672 - 40921 -
Puran Crypto Recovery: The Best Crypto Recovery Company with Expert Solutions
Why Choose Puran Crypto Recovery?
When it comes to cryptocurrency wallet recovery, you need more than just technical skills; you need a team you can trust. Puran Crypto Recovery is renowned for its industry-leading expertise, ethical practices, and high success rate.
Comprehensive Expertise
Puran Crypto Recovery employs a team of professionals with deep knowledge of blockchain technology, encryption algorithms, and digital forensics. This multidisciplinary approach ensures that every angle of recovery is covered.
Proven Track Record
With years of experience and countless successful recoveries, Puran Crypto Recovery has built a reputation as one of the most reliable recovery services in the industry.
Secure and Confidential Processes
Puran Crypto Recovery understands the sensitivity of your situation. They implement strict confidentiality agreements and cutting-edge security measures to protect your information at every step.
Customized Solutions
No two cases are the same. Puran Crypto Recovery tailors its recovery strategies to fit the specific circumstances of each client, ensuring the best possible outcome.
Transparent Communication
Honesty is a cornerstone of Puran Crypto Recovery’s philosophy. They provide clients with realistic expectations and keep them informed throughout the recovery process.
The Importance of Managing Expectations
While Puran Crypto Recovery offers exceptional services, it’s essential to understand that cryptocurrency recovery is never guaranteed. The decentralized and pseudonymous nature of blockchain technology makes it inherently difficult to reverse transactions or access lost wallets.
Puran Crypto Recovery approaches each case with dedication and professionalism, making every effort to recover your assets. However, clients should view the process as a “best-effort” attempt rather than a certainty.
Preventing Future Losses
Once your wallet is recovered—or if you’re fortunate enough never to lose access—implementing robust security measures is critical to protecting your digital assets.
Use Hardware Wallets
Store your cryptocurrency offline in a hardware wallet to minimize the risk of hacks.
Backup Private Keys and Wallet Files
Maintain multiple secure backups in different locations to safeguard against loss or damage.
Enable Multi-Factor Authentication (MFA)
Adding an extra layer of security can prevent unauthorized access to your wallet.
Stay Informed About Emerging Threats
The cryptocurrency landscape is constantly evolving. Stay updated on the latest scams and security best practices.
Conclusion
Losing access to your cryptocurrency wallet can be a distressing experience, but it’s not the end of the road. By taking prompt and careful action, you can significantly improve your chances of recovery. With the expertise of Puran Crypto Recovery, you can navigate the complex process of wallet recovery with confidence and peace of mind.
Remember, prevention is always better than cure. Secure your wallets, safeguard your private keys, and stay vigilant to protect your valuable assets in the dynamic world of cryptocurrency. If the worst does happen, Puran Crypto Recovery stands ready to help you recover what’s rightfully yours.1 -
hey, so i have recently started learning about node js and express based backend development.
can you suggest some good github repositories that showcase real life backend systems which i can use as inspiration to learn about the tech?
like for eg, i want to create a general case solution for authentication and profile management : a piece of db+api end points + models to :
- authenticate user : login/signup , session expire, o auth 2 based login/signup, multi account login, role based access, forgot password , reset password, otp login , etc
- authorise user : jwt token authentication, ip whitelisting, ssl pinning , cors, certificate based authentication , etc (
- manage user : update user profile, delete user, map services , subscriptions and transactions to user , dynamic meta properties ( which can be added/removed for a single user and not exactly part of main user profile) , etc
followed by deployment and the assoc concepts involved : deployment, clusters, load balancers, sharding ,... etc
----
these are all the buzzwords that i have heard that goes into consideration when designing a secure authentication system for a particular large scale website like linkedin or youtube. am not even sure how many of these concepts would require actual codelines and how many would require something else.
so wanted inspiration from open source content to learn about it in depth, replicate and create new better stuff if possible .
apart from that, other backend architectures like video/images storage system, or just some server for movie, social media, blog website etc would also help.2 -
After an attack on my laptop that saw me lose access to my wallet keys and losing $1.2m worth of crypto, I was admitted to the hospital for weeks and if not for the intervention of loved ones, I’m not sure I will be here to tell this story.
A few weeks ago, I was hacked and saw me lose all my digital assets including that belonging to my friend. I was extremely disoriented until a post about crypto recovery popped up on my feed and I saw a similar post about Morphohack Cyber Security, a crypto recovery expert, I contacted them immediately and to my surprise, Morphohack Cyber Security was able to recover my crypto assets and secure my wallet for me. Words can not express how grateful I am for their help, and I’m putting this out there to remind people of the importance of being able to get help and knowledge about crypto recovery and security. If you have lost crypto and think it is impossible to get it back then you need to contact Morphohack Cyber Security, they will convince you otherwise and help you get back your crypto assets. Contact them ( MORPHOHACK@CYBERSERVICES . COM ) WHATS APP ( +1 213 672- 4092) WEB ( MORPHOHACK.WIXSITE. COM/ CYBER)15 -
Days later, after relentless investigation and negotiation, they succeeded in recovering a significant portion of my lost investments. The relief I felt was indescribable. Not only had they managed to recover my funds, but they had also educated me on the importance of security and due diligence in the digital world. They didn’t just save my financial future; they gave me the knowledge and confidence to make better decisions moving forward. Thanks to Alpha Spy Nest, I’ve learned to be more cautious in my investments, and I now feel secure in knowing I have a team of experts to turn to if anything ever goes wrong. The experience taught me that even in the darkest of times, there is hope, and with the right help, recovery is possible. Contact them via:WhatsApp: +15132924878
 1
1 -
Steps for fund recovery from an online crypto scam—rely on BETAFORT RECOVERY
Through Betafort Recovery, Bitcoin scam victims can retrieve their money. I recommend Betafort Recovery to anyone who has fallen victim to a scam and has been looking for methods and techniques to recover their lost cryptocurrency or wallets. Betafort Recovery is a reliable cryptocurrency recovery firm that assists victims in recovering their stolen cryptocurrency and offers secure solutions to protect your wallets from online scammers. I must admit that I was deeply melancholy and had given up on life until these experts could restore my $23,400 to my wallet. If you've lost your cryptocurrency and you are helpless about it, contact Betafort Recovery to get your money back. One key aspect that makes Betafort Recovery stand out is its focus on providing secure solutions to protect wallets from online scammers. It's not just about recovering lost funds; it's also about preventing future incidents and ensuring that clients' digital assets are safeguarded against potential threats. This proactive approach demonstrates their commitment to the long-term financial security of their clients. Furthermore, for individuals who have lost their cryptocurrency and are feeling helpless, reaching out to Betafort Recovery could be a turning point in their situation. The reassurance that they are legitimate for seeking help and recovering lost funds can provide much-needed relief and a sense of empowerment. Betafort Recovery as a reliable cryptocurrency recovery firm is certainly well-founded. Their ability to assist scam victims in recovering stolen cryptocurrency, their focus on providing secure solutions, and their commitment to supporting clients through challenging situations make them a valuable resource for individuals navigating the complex world of digital currencies. If you or someone you know has fallen victim to a cryptocurrency scam, contacting Betafort Recovery could be the first step towards reclaiming lost funds and regaining peace of mind.7 -
Buy Verified Cash App Account: Navigating the Digital Transaction Landscape
In an age dominated by digital transactions, the concept of purchasing a verified Cash App account has gained significant traction. This article aims to explore the nuances of buying a verified Cash App account, elucidating the advantages, potential risks, and offering a comprehensive guide for individuals considering this financial move.
Introduction
The Growing Trend of Buying Verified Cash App Accounts
As online transactions become more prevalent, the trend of purchasing verified Cash App accounts is on the rise. Users are increasingly recognizing the added benefits and security that come with having a verified account.
Understanding the Importance of Account Verification
Account verification is a crucial step in enhancing the security of digital transactions. A verified Cash App account provides users with an additional layer of protection, making their financial interactions more secure and reliable.
Advantages of Purchasing a Verified Cash App Account
Enhanced Security Features
One of the primary advantages of a verified Cash App account is the incorporation of advanced security features. These may include multi-factor authentication and additional verification steps, adding an extra layer of defense against unauthorized access.
Increased Transaction Limits
Verified accounts often come with substantially increased transaction limits. This proves beneficial for users engaged in larger financial transactions or those running businesses through the Cash App platform.
Access to Exclusive Cash App Features
Apart from heightened security and increased transaction limits, verified accounts may unlock exclusive features within the Cash App. This could range from priority customer support to early access to new features and promotions.
How to Safely Purchase a Verified Cash App Account
Researching Reputable Sellers
Before entering the purchasing process, it's crucial to research and identify reputable sellers. Reading reviews and testimonials can provide valuable insights into the credibility and reliability of a seller.
Authenticating Account Legitimacy
Ensuring the authenticity of the accounts offered by sellers is paramount. A legitimate verified account should have gone through the necessary verification steps outlined by Cash App.
Ensuring Transparency in Transactions
Transparency in transactions is vital. Buyers should choose sellers who provide clear information about the accounts, including their verification status and any associated features.
Risks and Precautions in Buying Verified Accounts
Common Scams in the Verified Account Market
The digital landscape is not without risks, and the market for verified Cash App accounts is no exception. Being aware of common scams, such as fake listings and phishing attempts, is essential.
Tips for a Secure Transaction Process
To mitigate the risk of falling victim to fraudulent transactions, following best practices such as using secure payment methods and verifying the seller's credentials is crucial.
Step-by-Step Guide to Verifying a Cash App Account
Understanding the Cash App Verification Process
Before attempting to verify a Cash App account, it is essential to understand the process thoroughly. Familiarizing oneself with the required documentation and steps ensures a smooth verification experience.
Submitting Required Information
During the verification process, users typically need to provide personal information, such as a valid ID and proof of address. Ensuring the accuracy and legitimacy of this information is key to a successful verification.
Navigating Potential Challenges
While the verification process is generally straightforward, users may encounter challenges. Being prepared to troubleshoot and address potential issues ensures a seamless verification experience.
Conclusion
Summarizing the Benefits and Risks
In conclusion, opting for a verified Cash App account offers users enhanced security, increased transaction limits, and exclusive access to platform features. While potential risks exist, informed decision-making and adherence to safety precautions can lead to a positive experience.
Encouraging Informed Decision-Making
As users consider the option of purchasing a verified Cash App account, it is crucial to approach the process with caution and awareness. Choosing sellers with proven credibility, staying informed about potential risks, and following best practices contribute to a secure and positive experience. devrant cash app buy verified cash app accounts buy verified cash apps buy verified cash app account uk buy verified cash app account usa buy verified cash app account
devrant cash app buy verified cash app accounts buy verified cash apps buy verified cash app account uk buy verified cash app account usa buy verified cash app account -
EY and ConsenSys announced the formation of the Baseline Protocol with Microsoft which is an open source initiative that combines cryptography, messaging and blockchain to deliver secure and private business processes at low cost via the public Ethereum Mainnet. The protocol will enable confidential and complex collaboration between enterprises without leaving any sensitive data on-chain. The work will be governed by the Ethereum-Oasis Project.
Past approaches to blockchain technology have had difficulty meeting the highest standards of privacy, security and performance required by corporate IT departments. Overcoming these issues is the goal of the Baseline Protocol.
John Wolpert, ConsenSys’ Group Executive for Enterprise Mainnet added, “A lot of people think of blockchains as the place to record transactions. But what if we thought of the Mainnet as middleware? This approach takes advantage of what the Mainnet is good at while avoiding what it’s not good at.”
Source : ConsenSys -
🐟💩The image i fetch from s3 is of type byte array
I return it to angular as an ArrayBuffer
Which then needs to be somehow converted to an image so i can fucking show it
Then after research i had to convert ArrayBuffer to Blob
And from Blob to URL encoded object which returns a string that now shows the full image in img tag
Somehow, by a sheer of trials and error i have just accidentally made a very secure way of fetching a very sensitive piece of document (verification document with user's personal data on it) and now in browser this is shown as blob:shit-image/random-hash. Not even the file extension. This means nobody can download this image. You fucking cant. Its a Blob motherfucker! Like a Blob Fish. It saves either a .txt when you try to save it (no idea how) and if you try to open the image in new tab it shows gibberish text. This means you can read-only this highly sensitive document image and not manipulate it, not even download it. Perfect. I have just made a very secure software by accident.
(this blob fish looks like my shit) 3
3 -
Buy Verified Cash App Accounts
USASMMACCOUNT buy Verified Cash App Account from. In today’s digital world, Cash App has become a popular platform for fast and convenient money transfer. If you want to streamline your online financial transactions and ensure a safe and authentic experience, you can purchase the Verified Cash App account service from our platform.
Our accounts sell full USA, UK,UA,CA,AUS and also 100% verified cash app accounts from other countries. We sell high quality verified Cashapp accounts at low price and in short time. With a verified Cash App account, you can greatly reduce the risks associated with online financial transactions. So, if you want to avoid the hassle, buying a verified Cash App account from the platform can be a smart solution. buy verified Cash App accounts.
Buy Verified Cash App Accounts
Looking to buy verified Cash App accounts? We offer trustworthy and secure options.
In today’s digital world, Cash App has become a popular platform for fast and convenient money transfers. However, getting a Cash App account verified can be a tedious and time-consuming process. So, if you’re looking to skip the hassle, buying a verified Cash App account can be a wise solution. Buy Verified Cash App Accounts.
Not only does it save you time, but it also ensures that you have a reliable and hassle-free experience. We will discuss the benefits of buying verified Cash App accounts and where you can find them. So, let’s dive in and discover a straightforward way to obtain a verified Cash App account hassle-free.
Buy Verified Cash App Accounts
Buy Verified Cash App Accounts
Why Buy Verified Cash App Accounts?
If you are looking to streamline your online financial transactions and ensure a secure and authentic experience, buying verified Cash App accounts can be a game-changer. Not only does it offer various advantages, but it also provides peace of mind knowing that your transactions are protected. -
Building Fortresses, not Firewalls: Ethical Hacking Meets Software Development
In the digital age, security is no longer an afterthought; it's the bedrock upon which our online world rests. Yet, traditional security measures often resemble fortresses – imposing, but vulnerable to unseen cracks and tunnels. To truly safeguard our systems, we need to think like the enemy, like the nimble figures scaling those walls: ethical hackers.
Enter the exciting realm of DevSecOps, where ethical hacking practices are woven into the very fabric of the software development lifecycle (SDLC). This proactive approach is akin to building castles with security in mind, each brick meticulously laid to withstand even the most cunning siege.
Why Ethical Hacking in SDLC?
Imagine developing a critical piece of software, only to discover a gaping security hole after launch. The damage could be catastrophic, exposing sensitive data and eroding trust. Ethical hacking flips this script. By integrating penetration testing, vulnerability assessments, and threat modeling throughout the SDLC, we proactively hunt for weaknesses before they can be exploited.
Think of it as a friendly sparring match, where the ethical hacker throws their best punches to expose vulnerabilities, allowing the development team to fortify the software's defenses. This constant testing and refining leads to robust, secure systems that can withstand real-world attacks.
Benefits of DevSecOps:
1. Reduced Costs and Risks: Early detection and patching of vulnerabilities are far cheaper than dealing with a full-blown data breach.
2. Improved Software Quality: Security becomes an inherent part of the development process, leading to more reliable and trustworthy software.
3. Enhanced Brand Reputation: Demonstrating a proactive approach to security builds trust with customers and stakeholders.
Putting it into Practice:
Integrating ethical hacking into the SDLC requires a cultural shift. Developers, security professionals, and testers need to work together seamlessly, sharing knowledge and fostering a collaborative environment. Here are some key practices:
1. Threat Modeling: Identify potential threats and attack vectors early in the development process.
2. Static and Dynamic Code Analysis: Use automated tools to detect vulnerabilities in code.
3. Penetration Testing: Simulate real-world attacks to uncover hidden weaknesses.
4. Security Awareness Training: Educate developers and other stakeholders about security best practices.
Tools of the Trade:
A plethora of tools empowers ethical hackers and security professionals in their quest for a more secure digital world. Some popular options include:
1. Kali Linux: A distribution packed with security tools for penetration testing.
2. Burp Suite: A web application security testing platform.
3. Metasploit: A framework for developing and executing exploit code.
4. Wireshark: A network traffic analyzer for identifying suspicious activity.
The Future of Security:
As technology evolves, so too must our security practices. DevSecOps, with its embrace of ethical hacking, is at the forefront of this evolution. By building security into the very fabric of software development, we can create a safer, more resilient digital world for everyone.
Remember, in the ongoing battle against cyber threats, ethical hackers are not the enemy; they are our allies, the architects of digital fortresses that stand strong against the shadows. So, let's embrace DevSecOps, sharpen our ethical hacking skills, and build a future where security is not just an afterthought, but a fundamental principle.
I encourage you to explore the world of DevSecOps and ethical hacking. Whether you're a seasoned developer or just starting your journey, there's always more to learn and contribute. Together, we can build a more secure digital future, one line of code and one vulnerability patch at a time.
Do you have any questions about DevSecOps or ethical hacking? Share your thoughts and experiences in the comments below! -
Living in the UK, I have always focused on making secure investments, and my decision to invest in Bitcoin was no different. With $680,000 stored in a hardware wallet, I felt well-prepared for the future. However, my confidence was shattered one fateful day when my hard drive suffered a catastrophic failure. Panic quickly set in as I tried every recovery method I could think of, but nothing worked. The sinking feeling in my stomach told me that my hard-earned Bitcoin might be lost forever. When I was at my wit’s end, a friend suggested I look into TRUST GEEKS HACK EXPERT. He had heard good things about them, especially their expertise in dealing with hard drive-related wallet issues. Skeptical but desperate, I decided to reach out. From the moment I contacted TRUST GEEKS HACK EXPERT website https :// trustgeekshackexpert . com/, I felt a wave of reassurance. Their team was not only knowledgeable but also genuinely concerned about my situation. They explained the data recovery process in a way that was easy for me to understand, which helped ease my anxiety. They patiently walked me through each step, ensuring they were dedicated to helping me retrieve my lost funds. After several tense days filled with anticipation, I received the astonishing news: they had successfully recovered my wallet. The relief I felt was indescribable; it was like I had just won the lottery. I was overwhelmed with gratitude for their incredible work and expertise. It felt like a miracle to regain access to my Bitcoin. If you find yourself in a similar predicament, whether in the UK or anywhere else, I wholeheartedly recommend TRUST GEEKS HACK EXPERT visit Website <> https :// trustgeekshackexpert . com/, Their dedication, expertise, and ability to deliver results are truly remarkable. They are not just a service; they are a lifeline for those facing the uncertainty of lost digital assets. Thanks to them, I can now look forward to a more secure financial future, knowing that my investments are safe once again. I am profoundly thankful for their support and commitment, which transformed what seemed like a financial disaster into a story of hope and recovery. TRUST GEEKS HACK EXPERT Tele Gram <> Trustgeekshackexpert

-
I HIGHLY RECOMEND ADWARE RECOVERY SPECIALIST AS THE BEST IN ALL FORM OF SCAMED RECOVERY
I cannot express how distraught I was when I realized someone had hacked my email and was conning my family and friends on Instagram to invest with me. The hacker was using my identity to lure them into a fraudulent investment scheme, and by the time we discovered what was happening, some of my family members and friends had fallen for it. They ended up wiring the fraudsters a total of $25,000 before they realized it wasn't me. The emotional and financial impact was devastating. Call or text: +18186265941 I felt helpless and violated, knowing that someone was using my name to deceive the people I care about the most. It was during this period of turmoil that a close friend told me about ADWARE RECOVERY SPECIALIST. She had been through a similar ordeal and had used their services to regain control of her digital life. Desperate for a solution, I reached out to the ADWARE RECOVERY SPECIALIST team. From the very first contact, they were understanding and professional. They explained the steps they would take to track down my email account, recover it, and secure it, along with my Instagram and other social media accounts. The process was thorough and efficient. The team at ADWARE RECOVERY SPECIALIST used their expertise to identify the breach points and secure my accounts against future attacks. They provided clear instructions on how to enhance my online security and even offered tips on maintaining privacy in the digital age. Within a few days, my email and social media accounts were back under my control. The relief was immense. Knowing that my accounts were secure and that the fraudsters no longer had access to them lifted a huge weight off my shoulders. My family and friends also felt reassured, seeing the proactive steps I was taking to prevent this from happening again. If you ever find yourself in a situation where your digital security is compromised, I highly recommend reaching out to ADWARE RECOVERY SPECIALIST. Their team is not only skilled in recovering and securing accounts but also empathetic to the distress such incidents cause. They offer a comprehensive solution to safeguard your digital presence, giving you peace of mind in a world where online threats are increasingly common. Don't wait until it's too late. Protect your digital life with ADWARE RECOVERY SPECIALIST and ensure that your personal information remains safe from those who seek to exploit it.
-
The UPS Store: Secure Document Shredding Services in Carlsbad
In an age where data security is paramount, safely disposing of sensitive documents is critical for both businesses and individuals. At The UPS Store, located at 7040 Avenida Encinas #104, Carlsbad, CA 92011, we offer professional document shredding services to help protect your confidential information from unauthorized access. With our convenient and secure shredding options, you can ensure that your private data stays protected.
Why Opt for Document Shredding at The UPS Store?
Secure and Confidential Disposal
When it comes to document disposal, security is our top priority. Our shredding services use strict protocols to ensure your information remains confidential. From financial documents to personal files, we provide secure shredding solutions for every type of sensitive information.
Convenient Shredding Services for All Document Types
Whether you’re cleaning out your home office or managing sensitive client information, The UPS Store handles all types of documents, including bank statements, contracts, tax forms, and more. With our shredding services, you can conveniently and securely dispose of everything from single documents to bulk files.
Environmentally Friendly Disposal
At The UPS Store, we believe in responsible disposal. All shredded materials are recycled, so you can feel confident that your document shredding is not only secure but also environmentally conscious. By shredding with us, you’re helping reduce waste and support eco-friendly practices.
Affordable and Transparent Pricing
We believe that security should be accessible, which is why we offer transparent and affordable pricing for our shredding services. Whether you’re shredding a few pages or several boxes of documents, we provide competitive rates to meet both personal and business needs.
Convenient Location in Carlsbad
Located in Carlsbad, The UPS Store makes it easy to handle all your shredding needs without any extra hassle. With flexible hours and a convenient location, stopping by to securely dispose of your documents is simple and efficient.
How Our Document Shredding Service Works
When you visit us for shredding, simply bring in your documents, and our trained staff will handle the rest. Our team follows a secure process that ensures all documents are destroyed effectively, protecting your sensitive information from the moment you drop it off until it is securely shredded.
Contact Us for Secure Document Shredding Today
For secure, reliable document shredding in Carlsbad, visit The UPS Store at 7040 Avenida Encinas #104, Carlsbad, CA 92011. For any questions or to discuss your shredding needs, feel free to call us at +1 760-431-0028. Our friendly team is here to help make document disposal simple, safe, and affordable.
Trust The UPS Store for Your Document Shredding Needs
When it comes to disposing of confidential information, don’t take chances. Rely on The UPS Store in Carlsbad for secure and responsible document shredding. Visit us today to experience the ease and peace of mind that comes with our professional shredding services.
-
BEST CRYPTO / BITCOIN RECOVERY COMPANY / SERVICES - Consult iFORCE HACKER RECOVERY
Hi everyone, my name is Edward Decker, and I’m from New York, USA. I want to express my sincere gratitude to iFORCE HACKER RECOVERY for helping me regain access to my crypto wallet after nine years. I had lost all hope, thinking my funds were gone forever, but thanks to their expertise, everything was still intact. They not only recovered my wallet but also ensured it was fully secured. I’m beyond grateful for their professionalism and efficiency. If you ever find yourself in a similar situation, I highly recommend iFORCE HACKER RECOVERY for reliable and secure crypto recovery services.
crypto scam recovery recover stolen cryptocurrency cryptocurrency recovery services lost crypto recovery bitcoin recovery expert recover scammed bitcoin crypto fund recovery blockchain recovery services recover hacked crypto wallet crypto fraud recovery
Website; ww w. ( iforcehackersrecovery. com
Email; contact@iforcehackersrecovery. co m
Whatsapp; +12..40.. 80.3. 3706 1
1 -
Why in the fuck does everyone expose specific ports in Dockerfiles?
If I wanted to expose the port, I would fucking expose it.
Currently can't run my home infra platform because I'm running two separate instances of Maria DB on the same private internal network. These are two databases for two separate applications.
Why don't I run them on one? Because they're two separate fucking applications.
Why the fuck can I not do this when I used to be able to do it a week ago.
Stop exposing your fucking ports in your fucking Dockerfiles.
This shit is getting so bad, I'm just about to throw my towel in on all fucking containers and just install everything in multiple VM environments.
I am God damn appalled that after 8 years of using docker, core concepts like a port exposure is being leveraged as a way to somehow circumvent poor security practices.
You want a secure container environment? Expose your own goddamn ports.
Fuck you Maria DB, and fuck you docker.2




